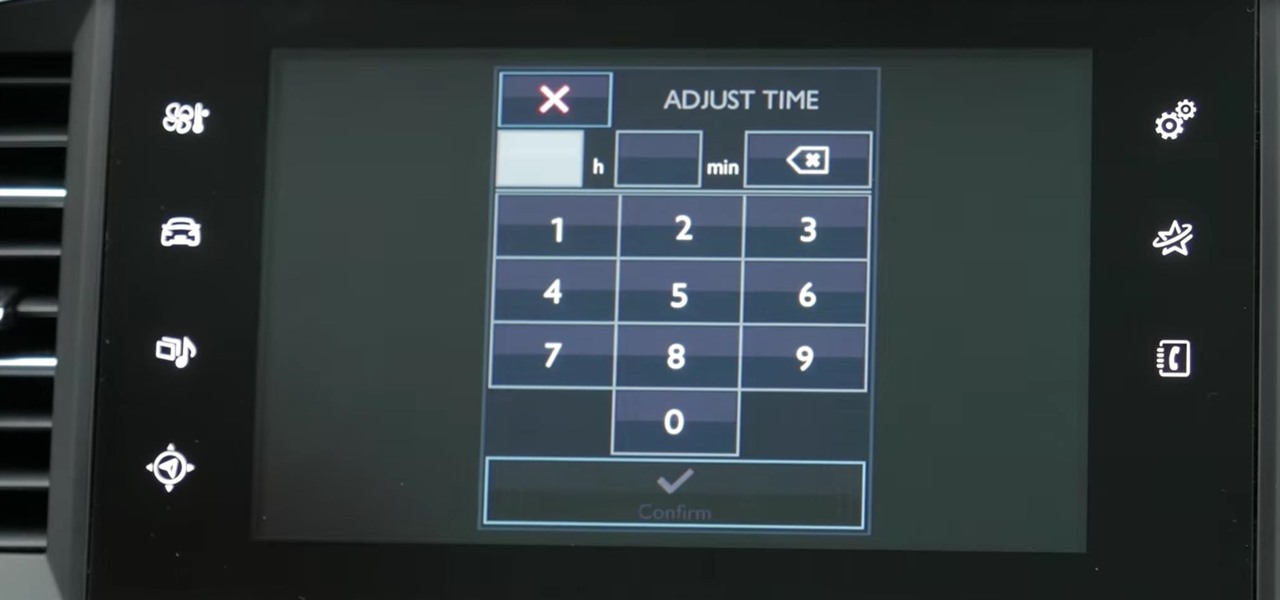
How To: Adjust Date and Time in Peugeot 308
My Next Car how to video series - how to set up the date and time in Peugeot 308 iCockpit (2015, 2016 and 2017 Europe model). This function is accessible in the touch screen i-Cockpit.


My Next Car how to video series - how to set up the date and time in Peugeot 308 iCockpit (2015, 2016 and 2017 Europe model). This function is accessible in the touch screen i-Cockpit.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Fashionably cool and awesome, this marvelous French Twist hair Style is as simple to make as it is elegant and stylish to flaunt. Just in few easy and accessible steps, this urbane style makes your appearance special and any outing memorable. Step 1: Comb Your Hair Neatly to Remove Any Tangles and Make Them Smooth. Step 2: Hold the Hair Together Like a Pony and Twist Them Till the Middle of the Pony and Make a Roll as Shown. Step 3: Once You Have Secured the Roll, Cover It with Surrounding Ha...

Smartphone users these days can get bombarded with texts and emails every hour. Online retailers sending you coupons to get you to buy stuff. Girlfriends asking where you are. Service providers reminding you to pay your bills on time.

Captioning your YouTube videos not only makes them more acessable for the hearing impaired, but they also make the contents of your video more accessible to YouTube. Once YouTube knows exactly what is being said it your video you will be more likely to rank when people search for related words or phrases.

Today, books in PDF are quickly accessible on the Internet, whether free or paid. You can easily read them on your computer or mobile device, but some still enjoy a printed version they can hold in their hands. Printing PDF volumes is a quick and easy task, but the only problem is binding them into a sturdy book, especially when they're pretty thick.

In photography, creating a double or multiple exposure photo involves combining two different images to make one single image. This technique has been used in film photography by exposing a piece of film twice to two different images. The second image becomes superimposed onto the first image, creating various effects that may mirror one another or seem ghostly.

Despite the controversy over Scrabble Trickster across the word world, Mattel's modern take on the classic crossword board game is out in stores— but not in the United States. It's only available in and around the UK, but you can snag your copy just in time for Christmas from Amazon UK. You can also visit the official Scrabble Trickster website. I imagine this is going to be a hot item in the United Kingdom this holiday season, but as for me— it's the one Scrabble game I refuse to add to my c...

Despite all the tragic stories you hear on the news, you'll probably never be involved in a shooting. But you never know. Nobody thinks it’s going to happen to them – until it does. Be prepared to survive a shooting rampage, just in case.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

It's a common misconception that iPhones are impervious to cyberattacks and "more secure" than Android. And when an iPhone does get hacked, it's nearly impossible to tell that it happened.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Samsung uses their own SamsungOne font for their Galaxy lineup. But if you're coming from an iPhone or another Android device, you might not love it. With the help of this mod, however, you're sure to find a font that's right for you.

Producing professional video can be expensive and time-consuming. Green screens are cumbersome and require a lot of space, whereas dialing in the perfect lighting comes with its own challenges. For people working on a budget and space constraints, achieving the ideal background can be a nightmare.

You've just picked up your new Samsung Galaxy S20, S20+, or S20 Ultra — but wait. After you turn it on and restore your data, there a few apps you should install to get the most out of your updated phone. Installing these eight apps right away will help maximize your experience from the very beginning.
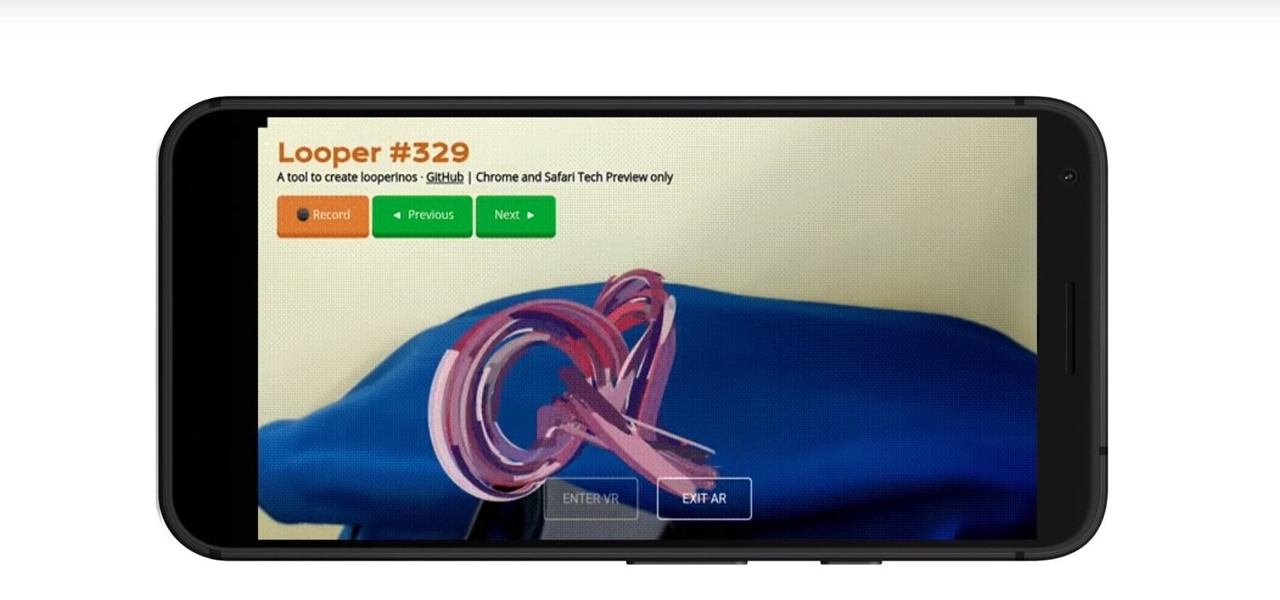
Web-based mobile augmented reality technology continues to gain momentum as Google is set to expand the standard for immersive web content to AR.

After jumping to the head of the class of augmented reality journalism in 2019, USA Today is continuing to push the medium forward in 2020.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.
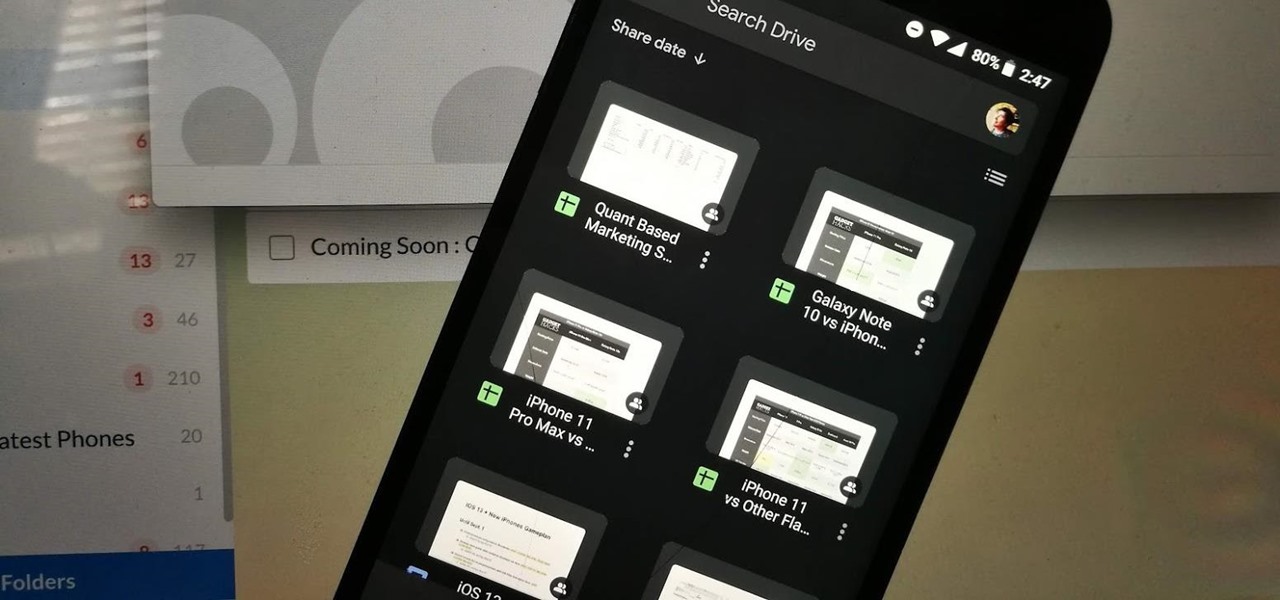
Lots of Google apps are getting dark mode. Google Drive has had it on Android 10 for a few months. But it hasn't been accessible to all Android users until now. With the latest update, there's a manual dark mode switch you can turn on regardless of what OS version you have.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

If you need some help expressing how you feel to your mom for Mother's Day, Snapchat and Facebook are here with some augmented reality help.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.
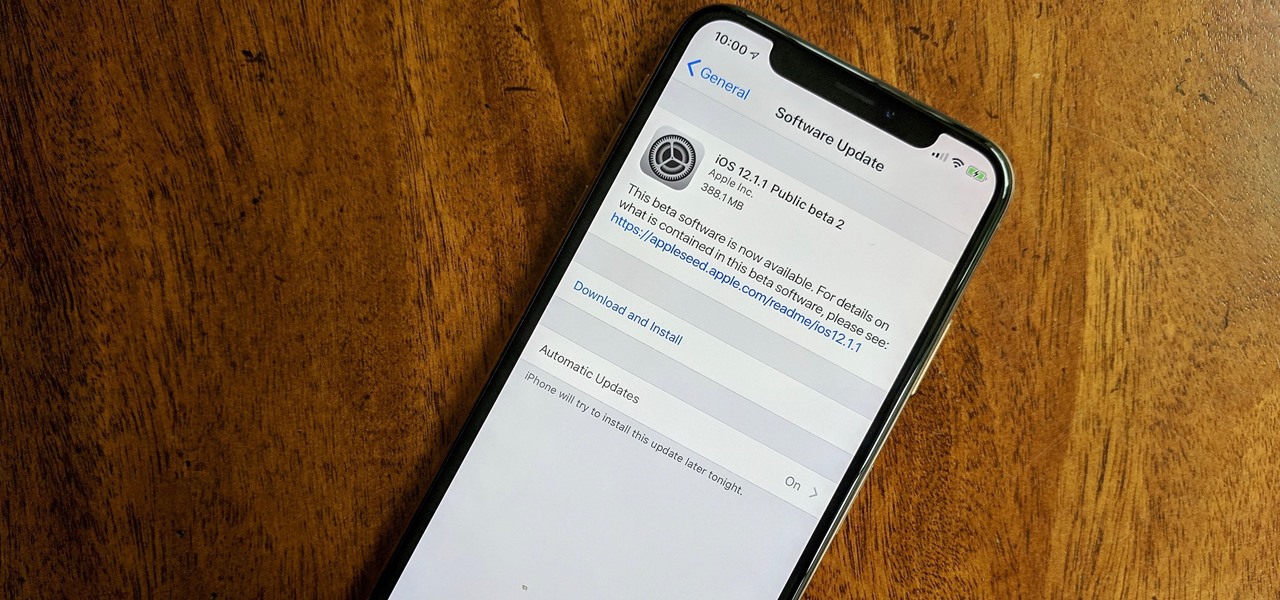
Registered iOS developers received their first taste of 12.1.1 dev beta 2 on Wednesday, Nov. 7, and public beta testers received the iOS 12.1.1 public beta 2 shortly thereafter.

Snapchat continues to deepen its roster of clients adopting its Shoppable AR Lens, with clothing giant Levi's and Disney becoming the latest brands to try on the e-commerce platform for size.

The day has finally come. About eight months after unveiling Magic Leap One: Creator Edition, on Wednesday, Magic Leap made the device available for order through a reservation page on its website.

If you find yourself on the run from the Empire, you no longer need a droid to send a holographic distress message, you just need an iPhone X and the HoloBack app.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Usually, when the public gets to see and hear Microsoft's Alex Kipman expound on the future of immersive computing, it's because the company has a new product to show off. But on Tuesday, April 24, Kipman was in the spotlight for an entirely different reason: an award nomination.

While much of the technical specifications of the Magic Leap One: Creator Edition still remain a mystery, some clues to its internals are hidden among the guides in the now freely-accessible Creator Portal.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Facebook may have shamelessly copied Snapchat and its camera effects for faces (as well as its World Lenses), but it might beat its social media competitor to virtual body augmentation.
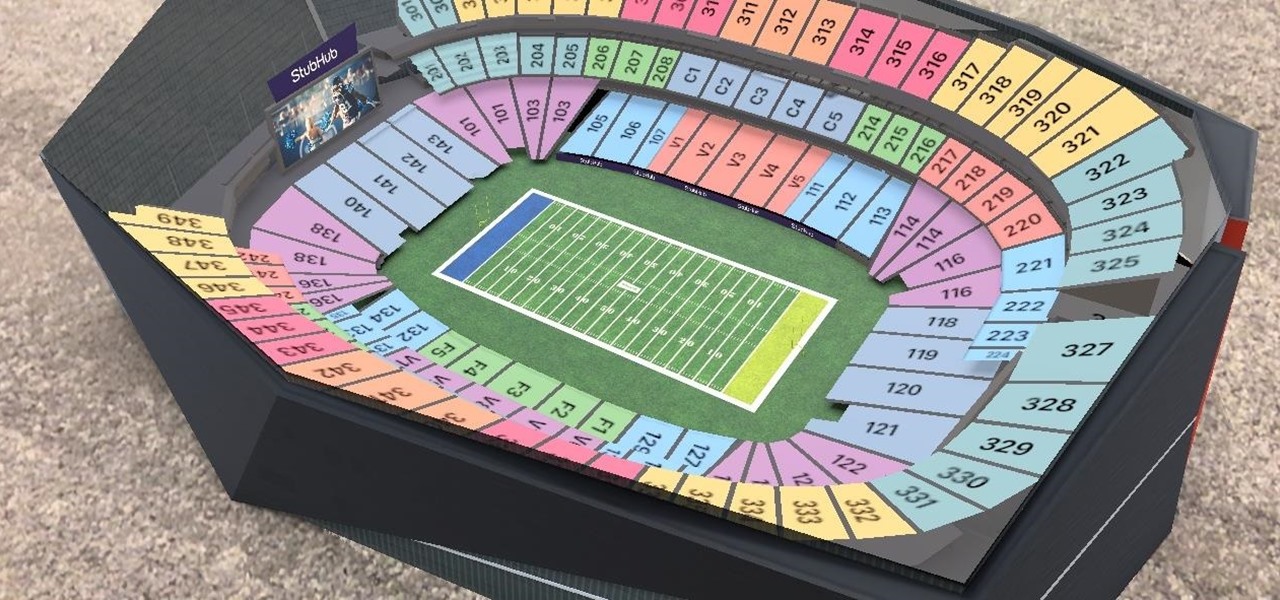
While the Minnesota Vikings have a realistic chance to become the first team to play in a Super Bowl on their home field, there will still be fans attending Super Bowl LII who will be in unfamiliar surroundings.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.