Apple just released the fourth public beta for iOS 14 today, Thursday, Aug. 6. This update comes two days after the company released iOS 14 developer beta 4, 15 days after Apple seeded developers the third dev beta, and two weeks after the release of public beta 3.

Apple just released the fourth developer beta for iOS 14 today, Tuesday, Aug. 4. This update comes 13 days after Apple seeded developers the third dev beta, and 12 days after public testers got their hands on public beta 3.

Watch this how to video to learn Tibetan sound healing techniques. Use these five guided practices for clearing obstacles, accessing positive qualities, and uncovering your inner wisdom.

After jailbreaking your iPhone 3G or iPod Touch, you can use WinSCP (a Windows ftp program) and OpenSSH (an app avilable through Cydia) to put IPA files on your Apple device using a Windows computer. This video walks you through the process of accessing a root directory to make your iPod or iPhone IPA-compatible.

The LG KF700 Virgo is designed to maximize convenience, enjoyment and productivity, LG’s advanced UI brings new meaning to the word convenience. The KF700 is the only place to get hands-on experience with the magic of its touch as you control your mobile life with simple gestures.
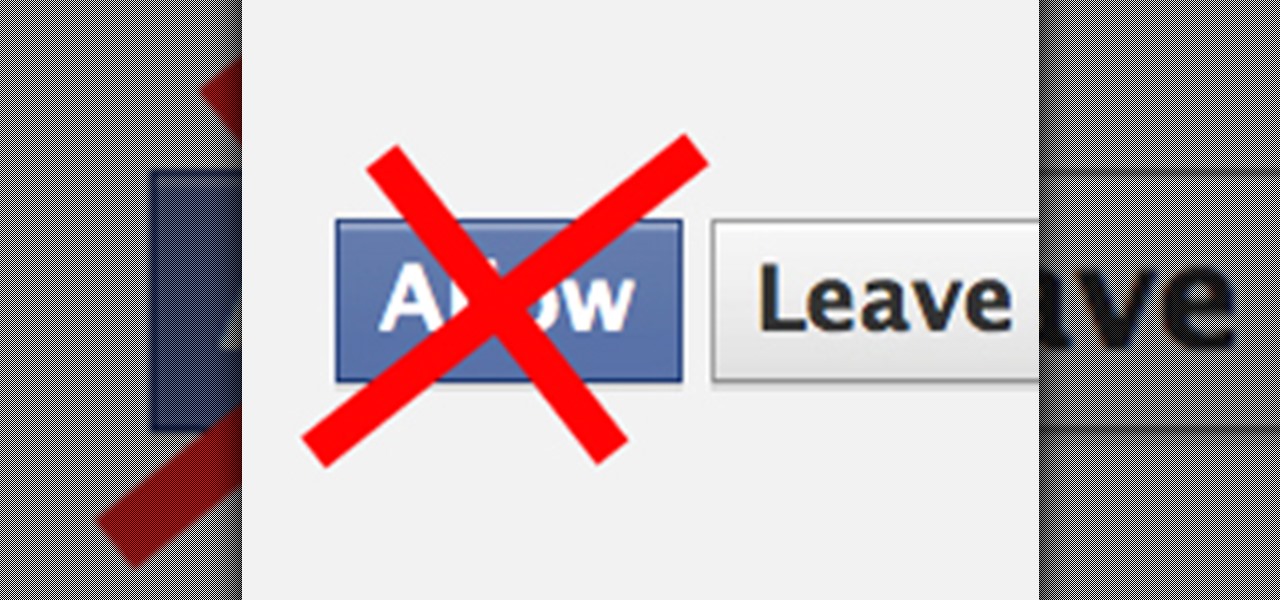
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.

Don't want one of your Facebook "friends" knowing your status updates? Prefer to keep a few of those "friends" out of your photo albums? Would you like to prevent a few "friends" from accessing your address?

Facebook is powerful and affluential, even when it comes down to its applications. But some applications are just downright annoying! With the new layout and other changes affecting Facebook recently, you can take ease in the fact that blocking and unblocking Facebook applications is still as easy as before.

Have you ever wondered how to create an invisible folder? I mean an invisible folder, not a hidden folder. Nowadays, we are facing lots and lots of problems requiring us to keep our data safe and secure. There are millions of hackers all around the world that are trying to steal our information whenever we get onto the internet. Even some of our friends are trying to lay their hands on our personal and confidential information.

What is DansGuardian? Schools, offices and universities often tend to use a software like DansGuardian to prevent people from accessing certain websites - websites like Youtube, Facebook, Myspace, and so on. However, if you ever find yourself in a situation where you need to access a blocked website... it's possible! As a matter of fact, it's quite easy.

The mouse is the primary tool most people use for accessing their computer and the vast stores of information on the Internet. Wouldn't it be funny if instead of allowing you to click icons on the computer screen, your mouse just lit up and made noises when you pressed it buttons? Well now you can prank a friend's optical mouse and make it so. This video will show you how to do it using only a mouse, simple tools, and a light-up, noisemaking keychain cow toy. Prank an optical mouse by replaci...

Some people (including myself) are seeing a "Hold" button instead of the "FaceTime" button when calling people on our new iPhone 4. It turns out this problem comes from a bug where Apple disables FaceTime on the iPhone 4 if you restored from an iPhone 3G.

Installing the Software Download the PC/Mac client from Dropbox for your computer. When installing the software you will also be prompted to create an account. Please do so at this point. This account gives you free access to 2 gigabytes (gb) of cloud storage that can be accessed from any PC/Mac or Dropbox Enabled Device.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

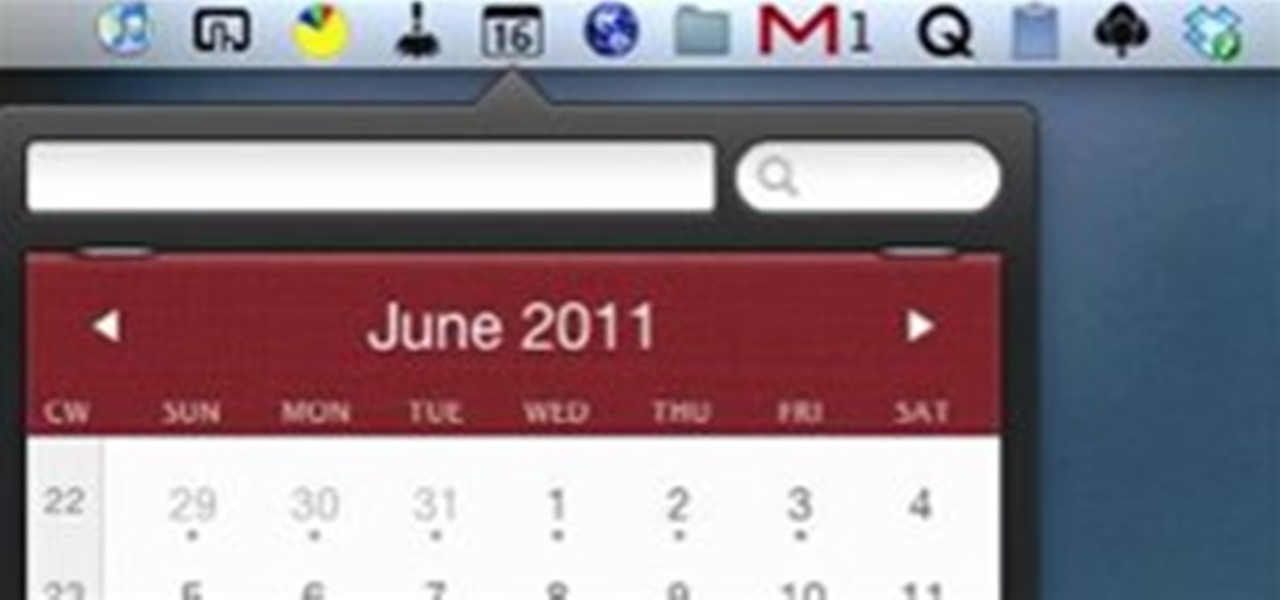
If you‘re new to Mac, you may not realize that the Dock is not the only place you can access applications and folders. The menu bar of your desktop can also hold a dozen or more applications and plug-ins for easy access to lots of content on your computer.

CMU’s Biorobotics Laboratory modular snake robot slithers in all sorts of different ways. Check out the three videos in the gallery below.

Update: Based on comments from Adam Novak, this article has been updated to better reflect how the video memory range works. You can check out his working emulator (written in c) here.
Creativity is a very important aspect of keeping a balanced mind. The more balanced your mind is, the more able it will be to perform the tasks you ask of it. And don’t think “creativity” has to be writing a novel or painting a masterpiece. The brain (and ‘spirit’) can benefit from simple and small adventures in non-linear thought and action.

Do you need proxy access, but cannot have it for some reason? The most common perpetrator behind the issue is the network you're trying to access the pages from. Some networks will block websites, then go as far as filtering out all of the web queries for terms like "proxy" because it can get around their filter. Quick web proxies can be used for tons of other things, though.

Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and the aircrack-ng software suite, the software has become unusable.

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.
Collapse At Hand Ever since the beginning of the financial crisis and quantitative easing, the question has been before us: How can the Federal Reserve maintain zero interest rates for banks and negative real interest rates for savers and bond holders when the US government is adding $1.5 trillion to the national debt every year via its budget deficits? Not long ago the Fed announced that it was going to continue this policy for another 2 or 3 years. Indeed, the Fed is locked into the policy.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

Go to http://yourguitarsage.com/ to find out how to order my ebook containing charts for over 170 tunes and constantly updating.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...

UPDATE: Minecraft 1.9.5 Has Been Leaked! Get it Here. You heard right. This one is hot off the presses! Last night, Notch promised a 1.9 Version 3 Update and here it is!

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Over the past few years, I have downloaded several third-party web browsers for the iPhone, iPod touch and iPad, and the one I have found most advanced and feature rich is Atomic Web. While many mobile browsers have their unique features, Atomic Web could well be considered the professional browser for advanced web users. With each version of the app, the developer has included features that make navigating the browser more user friendly and useful for bookmarking, managing and saving website...

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

What Hand Do I Read - And Why ?This is the first tumbling block for some budding palmists, so let me give you some real begginning tips.

Ever wanted to display text in Minecraft? It's actually not overly difficult. In this tutorial, I will endeavor to guide you through the process between storing and displaying text from memory. To do this, we will examine two different methods of displaying and storing text in memory.

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.

Google+ has managed to double their user count from three months ago, now standing at over 90 million Google+ accounts created. But how did it get so many so quick? By tricking people who are signing up for Gmail or a regular Google account into setting up a Google+ account, too.

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

By now, most of you have updated to the new Xbox look. Just as expected, it's got some great new features. The dashboard looks great and Bing integration is awesome, but I'm very unhappy about the new Netflix interface. It's awkward, slow, and half of the items don't even load correctly. I can't even play some movies. And the instant play feature is kind of annoying. When I first chose a video, I was hoping when it instantly started playing that it was a trailer, à la Zune. Alas, no.

Formerly ipchains, iptables is a script-based firewall that's included with both Mac and Linux operating systems. In my opinion, it's the best firewall in existence. The only downfall is that it's complicated for some people to use due to its script-based nature. But this should be disregarded, as firewalls are nearly the entire security of your computer.

If you want your Kindle to connect to the internet, you have to install the latest update for Kindle devices (not the Kindle Fire) by today. Amazon released a statement urging Kindle users to install a "critical software update" by March 22nd to maintain the Kindle's internet capability, which includes accessing and downloading Kindle books from the online store or any other internet-required service.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

Spending five days with the game is enough to know it's not to my liking. Is it a horrible MMO? Yes, yes it is. There are better Free to Play MMOs launched years ago that are better than this. As a fan of the Final Fantasy series (I am currently playing and liking Final Fantasy 13), this MMO is so bad that at some point I couldn't justify the awful environment, game play, and interface.