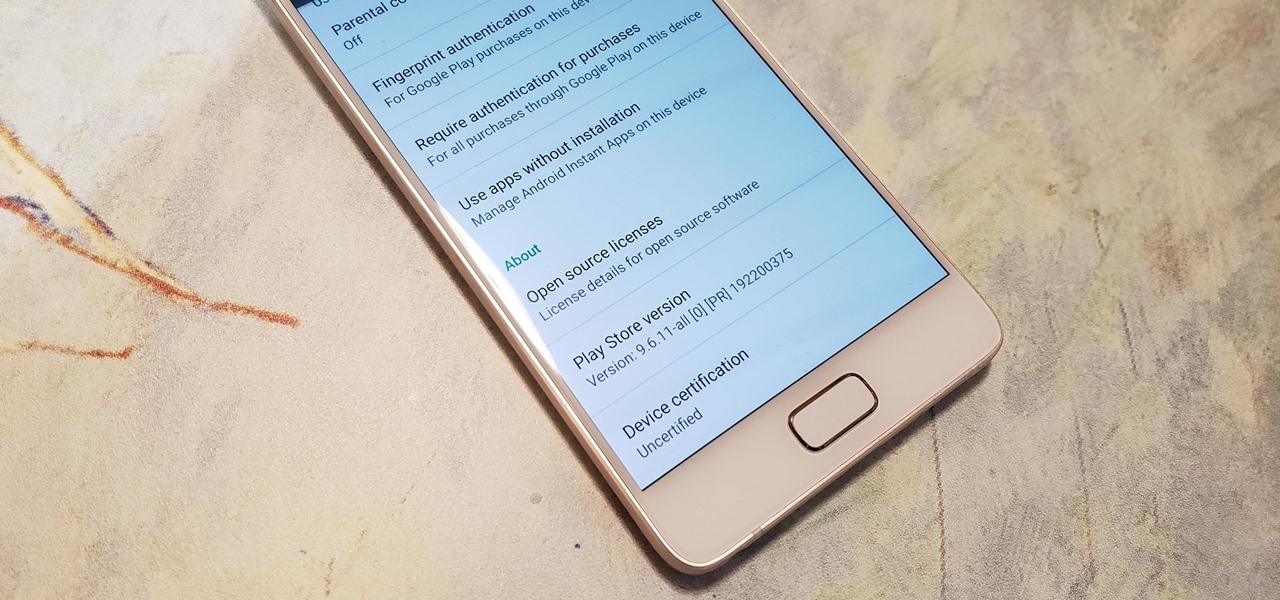
Google has started blocking certain devices from accessing the Google Play Store and other Google services. This is part of an effort to clamp down on OEMs that skirt its certification requirements, but now millions of phones have been uncertified to download or update Google apps. Fortunately, there are a few workarounds.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

With Huawei's recent emergence as the second largest OEM in the world, the company was poised to finally make a big push into the US market. Instead, their efforts were derailed by an unlikely foe, the US government. As a result, American customers will miss out on the newly-released Huawei P20.

Over the past week, we've had a number of important launches take place in the Android community. Samsung is in the middle of their rollout of the Galaxy S9, with preorders in the US shipping this week. Google also rolled out the first Android P developer preview last week. While these may seem unrelated, there are actually a number of Android P features inspired by Samsung software.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

MoviePass may be popular with filmgoers on a budget, but it might not be with those of you who are concerned about your privacy, since MoviePass may be logging your location data even when you don't expect the app to do so.

With the S9 and S9+ upon us, you maybe wondering if it's time to retire your aging Galaxy and either sell it or do a trade-in to get Samsung's latest flagship. Before you do, however, it's important to make sure that all its components — most notably the sensors — are working fully in order to avoid potential headaches.

Most of us have probably used a GIF at least once or twice to respond to a message, and that's why a lot of messaging services and keyboards have GIF search tools readily available to use. Now, Google wants to take GIF responses to a more personal level, by allowing you to create your own selfies GIFs to instantly sent to family and friends.

Apple's Mail app for iOS isn't a bad email client by any means. However, it just doesn't cut it for iPhone users that want a more intelligent and advanced email solution. If you're in the market for an app like that, Spark is absolutely your best bet.

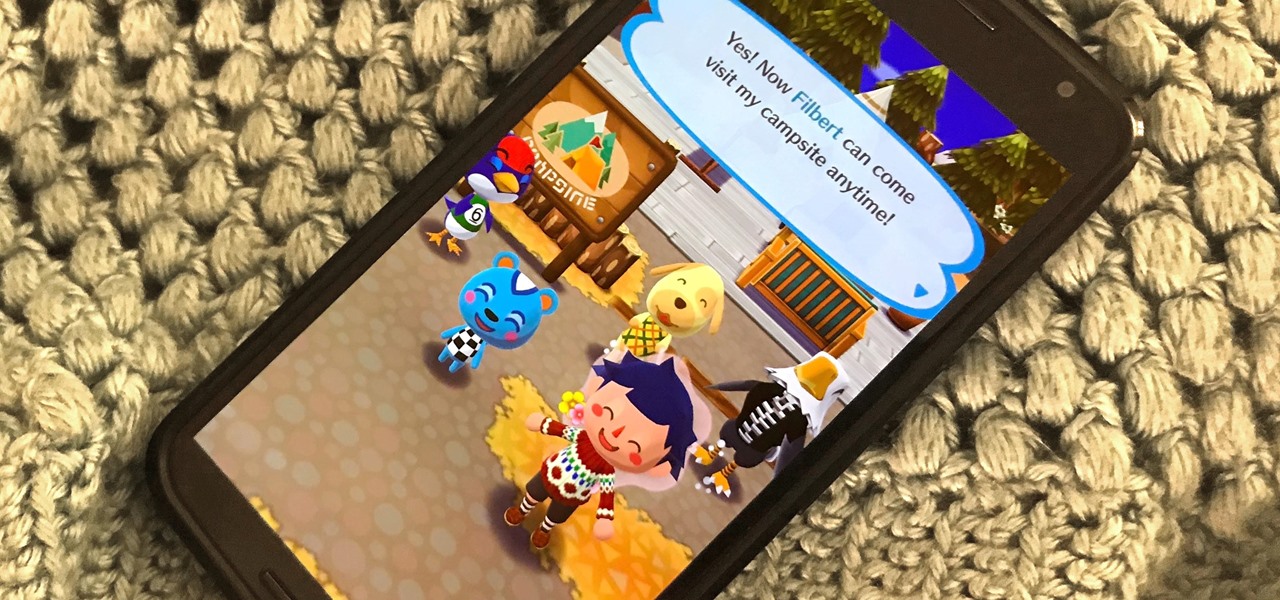
Friendship has always been a staple of Animal Crossing games, and Animal Crossing: Pocket Camp makes no exceptions. Check out this guide if you're interested in how to maximize time with your furry friends.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

A tethered version of the Vuzix M300 smart glasses, developed to pair with wearable computers from Toshiba Corporation, is expected to be available by the first quarter 2018, if not sooner.

Now that iOS 11 is official, everyone can enjoy all of the great new features available, but there are certainly a few bad seeds in there that you'll probably find annoying. Luckily, a lot of these disagreeable quirks can be changed for the better.

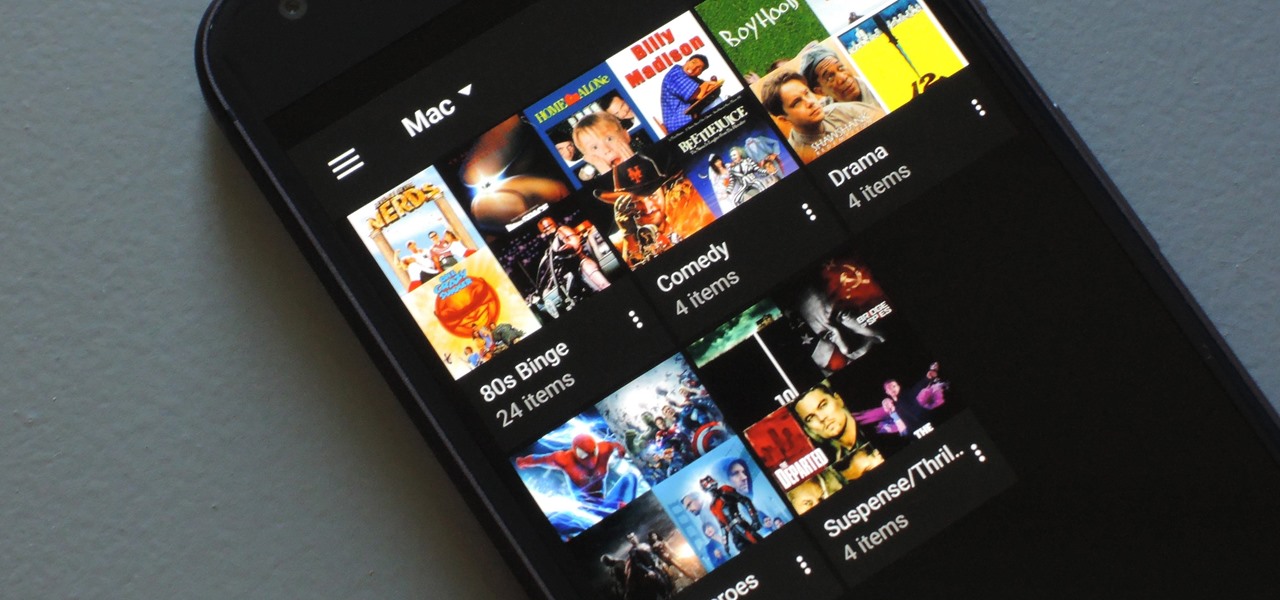
If you have a large media library, you should definitely have the Plex server installed on your computer. If you do, you can just install Plex for Android or iPhone, then you'll have access to all of your music, movies, and TV shows anywhere.

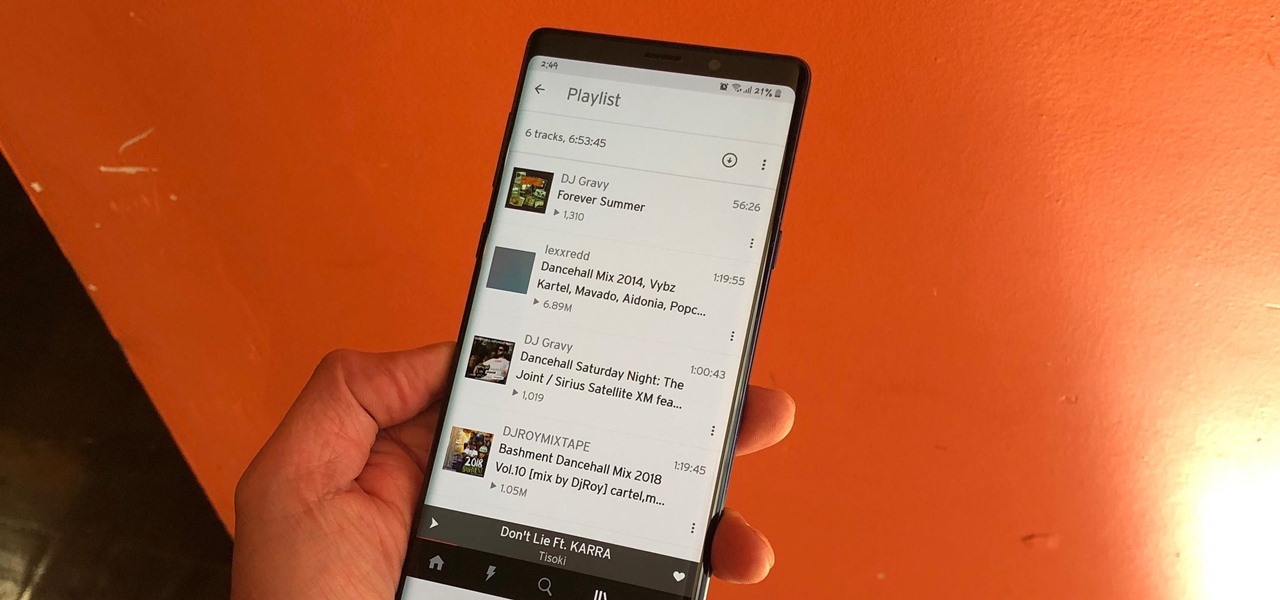
The nice part about creating a song playlist is that it's essentially like your own customized album. You can organize all your different music tastes into one large collection or separate them into each of their own genres.

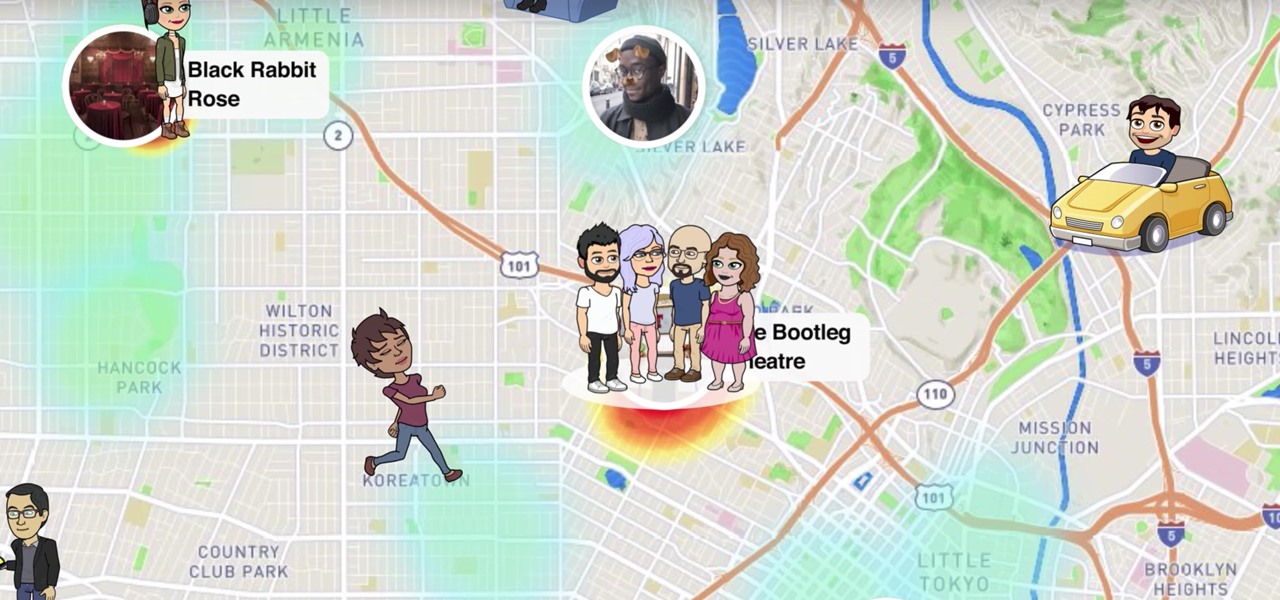
Snapchat recently updated their Android and iPhone apps with a new feature called Snap Map which lets you share your current location with other Snapchatters, as well as see their current locations. It may sound like an interesting new feature, but sharing your exact location with all of your Snapchat followers is dangerous, to say the least. Luckily, it's easy to turn this feature off.

If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

The problem with HIV is that it attacks and kills the very cells of the immune system that are supposed to protect us from infections — white blood cells. But a new technique, developed by scientists at The Scripps Research Institute (TSRI) in La Jolla, California, offers a distinct HIV-killing advantage.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

It has become hard to decipher where your digital imprint ends and your true self begins in today's tech-dominated world. Scrolling through news feeds and endless updates is not conducive to a good night's sleep, nor does it help you lead a well-balanced life.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

Amazon thinks that by simply removing an app from their Appstore, that they will stop users from accessing it. But with Android OS powering their Fire TV Stick and Fire TV, there really isn't anything they can do to prevent us from sideloading an APK onto the streaming media devices.

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

Microsoft has invested years and countless man-hours in an effort to get their cloud storage service on par with competitors like Dropbox and Google Drive, who have long resided at the top of this market. Their hard work has definitely paid off, as OneDrive (formerly SkyDrive) has finally reached a point in its development where it can stand toe to toe with any comparable service in almost any measurable regard.

I'm often reluctant to use a home screen launcher other than the stock one on my Android. Once you're well acclimated with something, complacency sets in, welcoming change with much resistance. Well, my friends, I have seen the error of my ways...

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

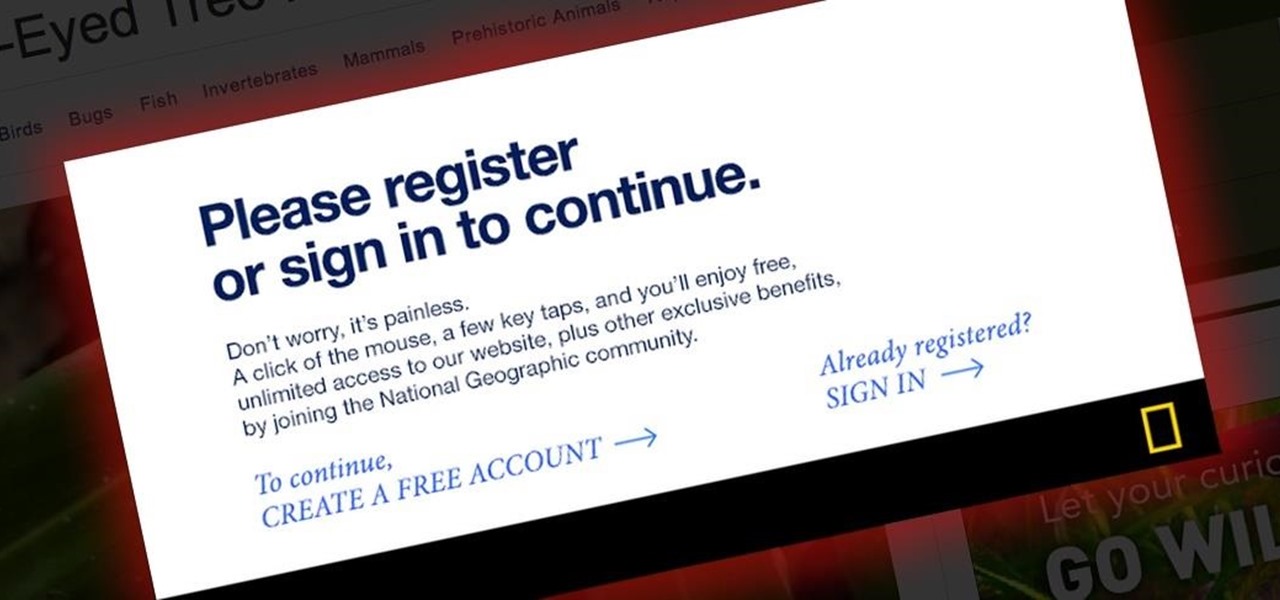
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

If you're as bad at locking your Nexus up as I am, you have the "slide" option set for your screen lock. It may not be the most secure option, but it's definitely the easiest way to unlock your device while being able to utilize lock screen widgets.

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

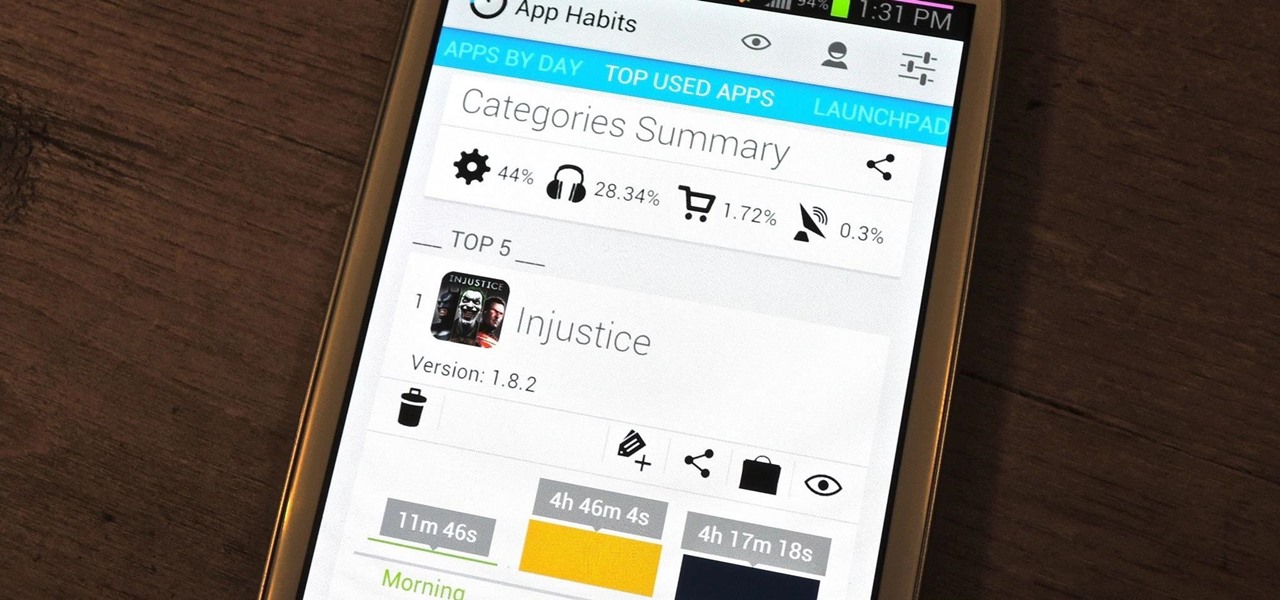
In today's dog-eat-dog world, every minute matters. Whether you're in school or working for the Man, a huge amount of your day is consumed by tasks, assignments, and other kinds of work. Then there's the time you spend playing video games, watching TV, or screwing around on your Samsung Galaxy S3.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

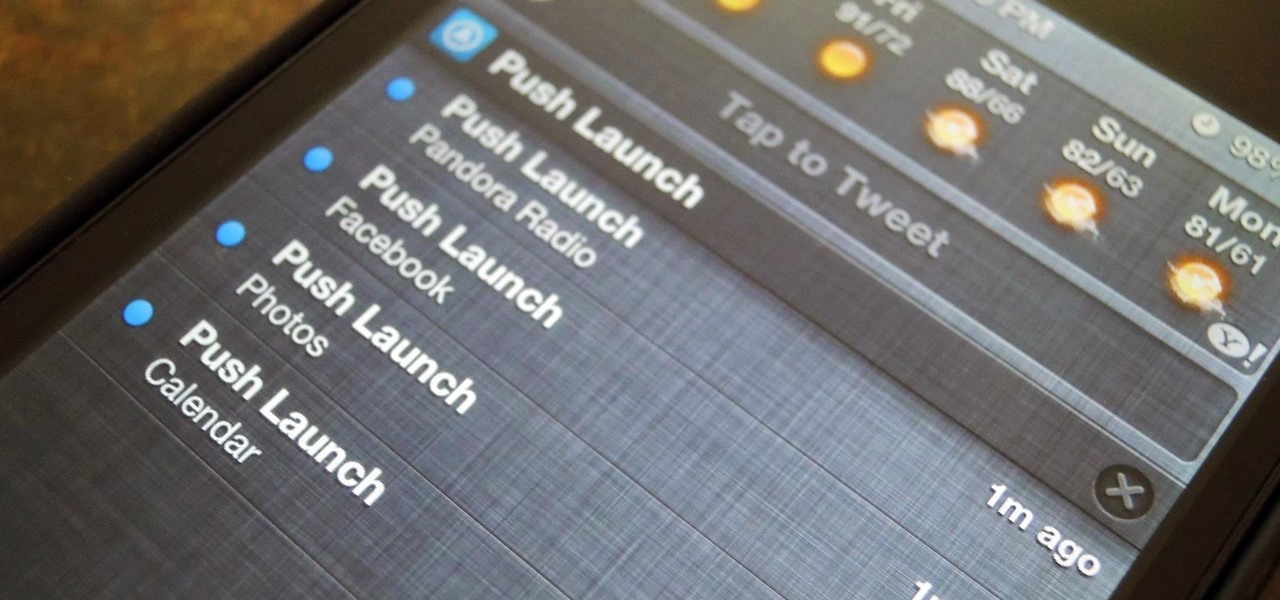
The shortest distance between two points is a straight line, but the shortest way to launch an app on an iPhone can be a much more complicated process.