Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

We spend over 30 percent of our lifetimes sleeping—yet it never seems like enough, does it? Distractions ranging from work issues to personal relationships keep our minds racing well after they should be shutting down for the night, and the onset of smartphones has only added to this problem with the instant information and easy entertainment that they offer.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...
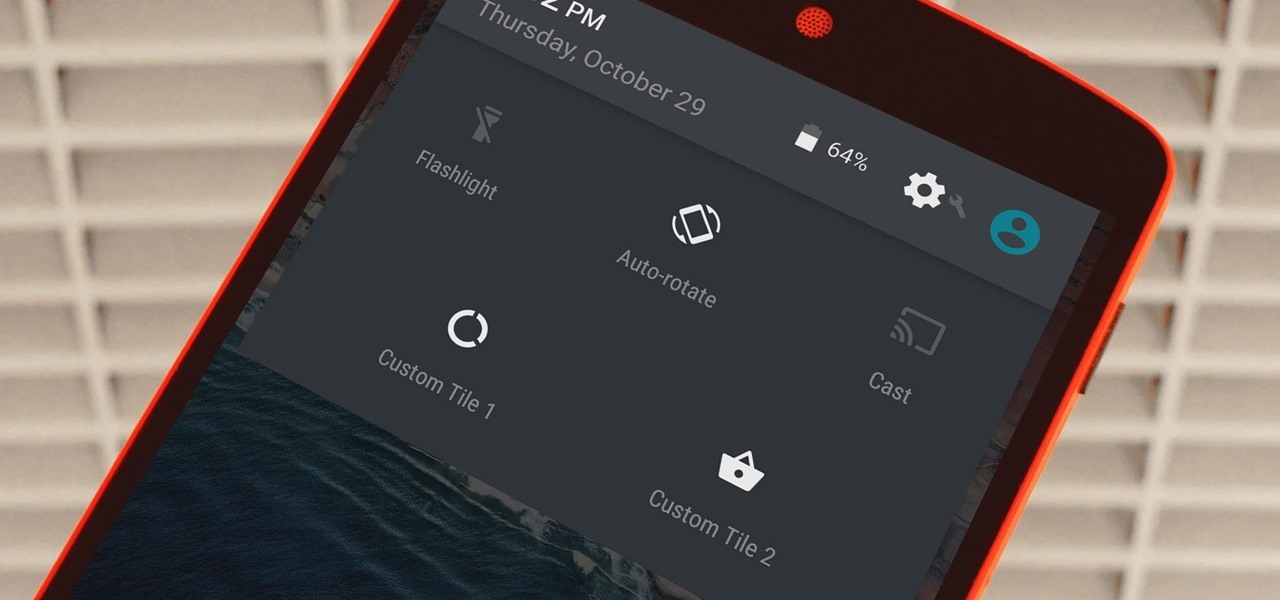
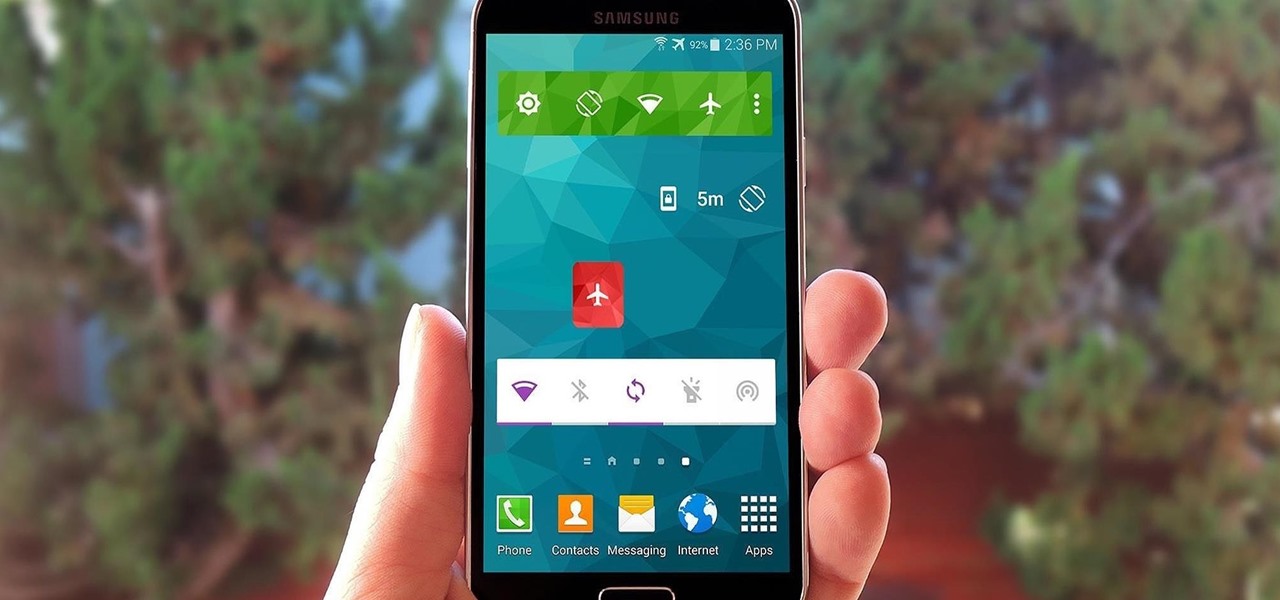
Android's Quick Settings menu is quite handy—just swipe down with two fingers from the top of your screen and you're ready to toggle several different system settings on or off. It got even better with Android 6.0 Marshmallow, since you can even use the hidden System UI Tuner to rearrange and remove your Quick Settings tiles now.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

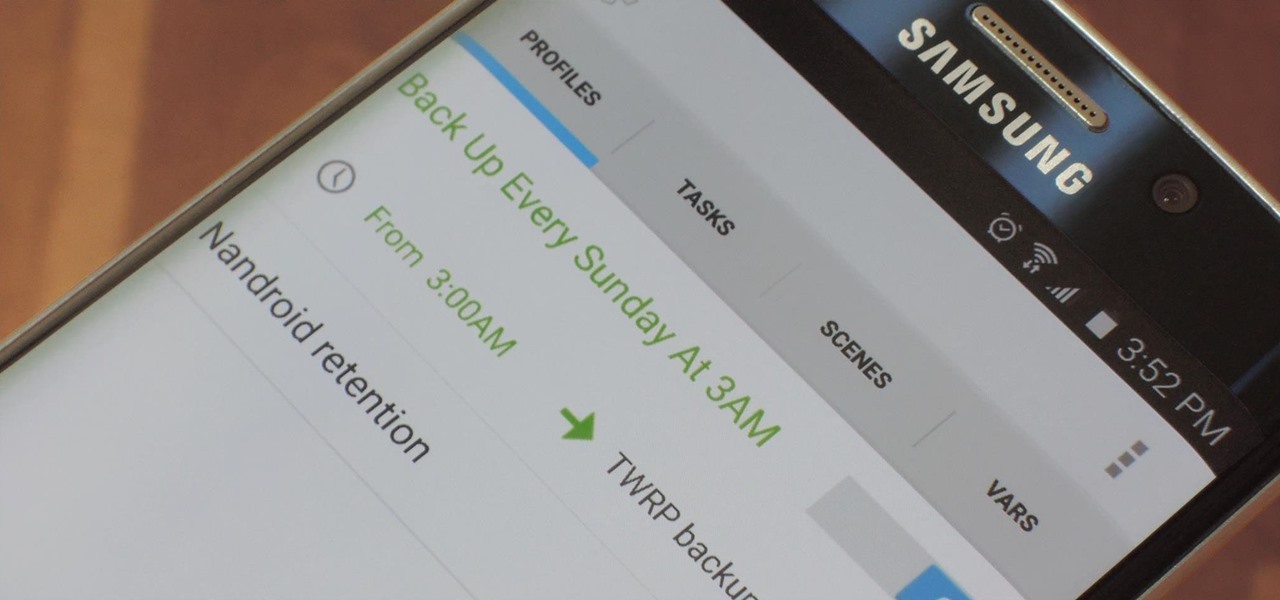
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

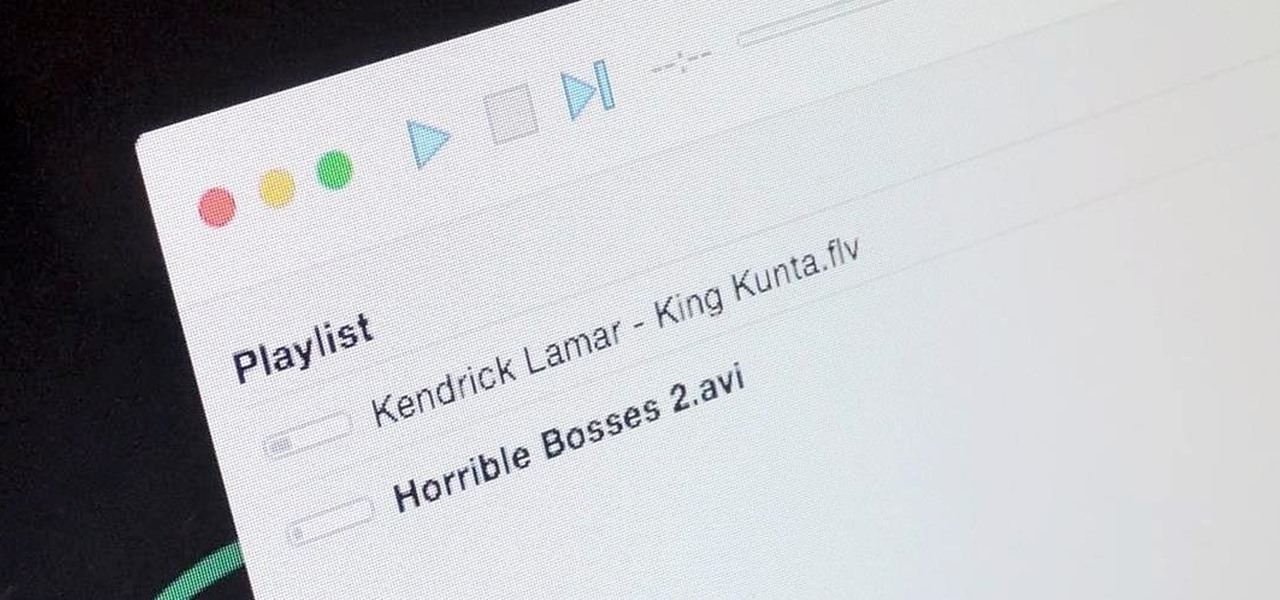
It's a breeze to send videos and music from your phone straight to your TV with an Apple TV or Chromecast, but these devices don't support all file types. While MP4 videos and MP3 music files are the norm these days, I still have a ton of AVI and FLV files that I'd like to watch on a big screen.

Reddit, the self-proclaimed "front page of the internet," continues to take a big bite of my free time each and every day, as well as millions of its other users'. The clicking and scrolling through page after page never gets old, but you could speed things up with a few browser extensions and double your Reddit knowledge in half the time. Here are my favorite extensions you can try out for the Chrome, Firefox, and Safari web browsers.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

When you finally turn the privileged age of 21 in the U.S. (or 18 in most other countries), the first thing you'll probably do is sprint to the nearest pub, order a drink, and revel in your new freedom. Congratulations, you've survived two decades on Earth, you've earned that drink.

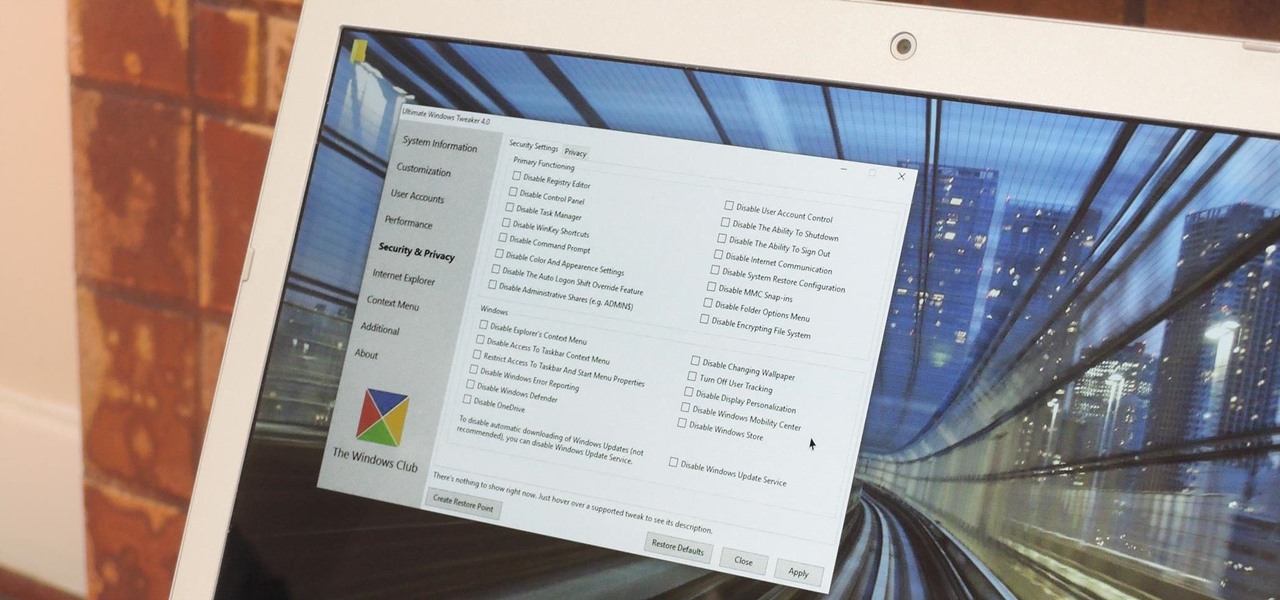
Every time Windows gets a significant update, the vast majority of existing tweaking utilities become obsolete. For every option that you fine-tuned with one of these tools on Windows 7 or 8, there's a change in the registry or system settings that cause your tweaks to now point to a dead end. This was definitely the case with Windows 10, since there were so many sweeping changes that very few existing options carried over.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

If your PC setup includes a mouse and keyboard, you'll be happy to know that most of the touchscreen-first features of Windows 8 have gone by the wayside in Windows 10. Where it once required awkward gestures to access key features, Windows now recognizes when you're using a traditional desktop or laptop, then responds by making sure that all features can be easily discovered with clickable buttons and menu entries.

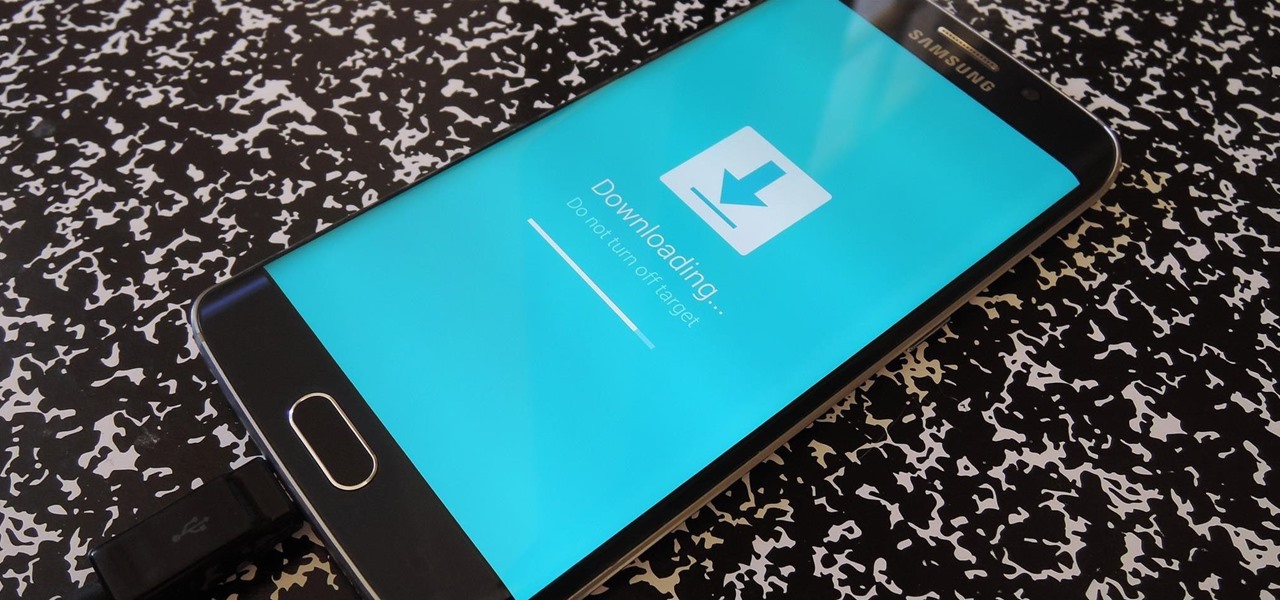
In the past, updating a rooted Samsung Galaxy device has always involved the complicated process of downloading the proper firmware for your variant, installing device drivers, then sideloading the update with Odin.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Exclusive to the Samsung Galaxy S6 Edge, "Information stream" is a screen feature that lets you see quick, at-a-glance information with a simple swipe while the screen is off. It also supports plug-ins, or additional streams of information that can come from third-party sources. So developers are starting to come up with nifty little add-ons for Information stream, and the team at 3C has some cool new system feeds that might come in handy.

If you've got a desktop computer, I can almost guarantee that you've got a widescreen monitor set up in landscape mode. It's how just about everyone uses their monitor these days, including myself. Except that it's not always the best way of working.

Android version 5.0 Lollipop introduced a ton of changes to the OS—and of course with new features, there's always a new set of bugs. One of the biggest bugs of all was a massive memory leak caused by the new screen-off animation, which loaded its assets into memory but never cleared them away.

In the era of smartphones and cloud-based computing, it almost seems irresponsible to keep a stash of paper documents. Not only is a physical paper printout environmentally impractical, it's also a lot harder to organize and keep track of than a digital file stored on a hard drive.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

If you were around when the Nintendo Wii first launched, you remember how revolutionary the device was at the time. When I first encountered one, I was amazed at the simplicity of its controls, namely the fact that the Wii Remote (aka Wiimote) just felt like such a natural way to play a game.

If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.

HTC's Sense UI is generally regarded as one of the best manufacturer-skinned versions of Android. This is mainly due to the subtle and classy styling of the interface, as well as some unique features that are added in here and there.

We all fall sleep in different ways. Some may require absolute silence, others need white noise, and some enjoy listening to a song or two to help bring on the sleep. If you're in the latter group, like I am, there's a problem. Fall asleep before the music stops, and a loud song may jolt you awake in the middle of the night. With an iPhone, however, that issue can be avoided with a little setup.

Widget toggles, or "power toggles" as they're often called, have been around for quite a while. They serve their purpose nicely as an easy way to add switches to your home screen or notification area for functions that don't come with the stock software on your device.

Welcome back, my greenhorn hackers!

Android Lollipop's new Material Design interface does its best to strike a delicate balance between intuitiveness, usability, and aesthetics. For some folks, though, the use of a lighter color palette throughout the interface disrupts this balance.

There's a common bug that affects many Samsung Galaxy S5 users, myself included. The software that drives the fingerprint sensor can randomly fail to load, leaving you without one of the most unique features of your beloved smartphone.

The Nexus 6 uses an Ambient Display notification system that was heavily inspired by the Active Display feature on the Moto X. Essentially, the device shows a black-and-white version of the lock screen whenever you receive a new notification or pick the phone up. This is all made possible by the N6's AMOLED display that doesn't have to waste any battery to power black pixels on the screen.

Stock Android is a great experience, and it's probably one of the biggest reasons that people purchase a Nexus device over other Android phones. Without carrier or manufacturer modifications to the core software, the entire user interface feels a lot more clean and snappy, and this also means that developers encounter fewer compatibility issues when creating flashable ZIPs and custom ROMs.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Apple's iPhone 6 packs a powerful 4.7-inch Retina HD display with 1334-by-750 resolution, and it's so incredible in person that it almost looks fake. However, as awesome at this display is, it can always be better.

App-locking apps have been around for a while, but none have had quite the panache of developer Fazil Kunhamed's latest offering, Oops! AppLock. While others use a PIN or password to restrict access to apps that are installed on Android, AppLock uses a stealthy volume button combo.