If you're new to Ubuntu Linux and, for whatever reason, not so very keen on Ubuntu's default email client, Evolution, then you might like to try Mozilla Thunderbird. In this tutorial, you'll how learn how to go about setting up an email account in Thunderbird. Take a look.

Benny from askbenny.cn teaches some Mandarin Chinese words and phrases to use when opening a bank account.

Looking for a quick primer on how to create a new email account on a BlackBerry phone running version 6 of the BlackBerry OS? This clip will teach you everything you'll need to know. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this official video guide from the folks at Blackberry. For detailed information, including step-by-step instructions, take a look.
In this tutorial, we learn how to use the left handed column options in Gmail. First, log into your Gmail account, then click on your different emails. Open an e-mail by clicking on it, then click reply to respond to it. You can also save this, and it will save to your account. If you want to delete a message, simply select it and click on the delete button. It will now be moved to your trash, where you can keep it, or you can delete that, which will remove it forever. If you want to write an...
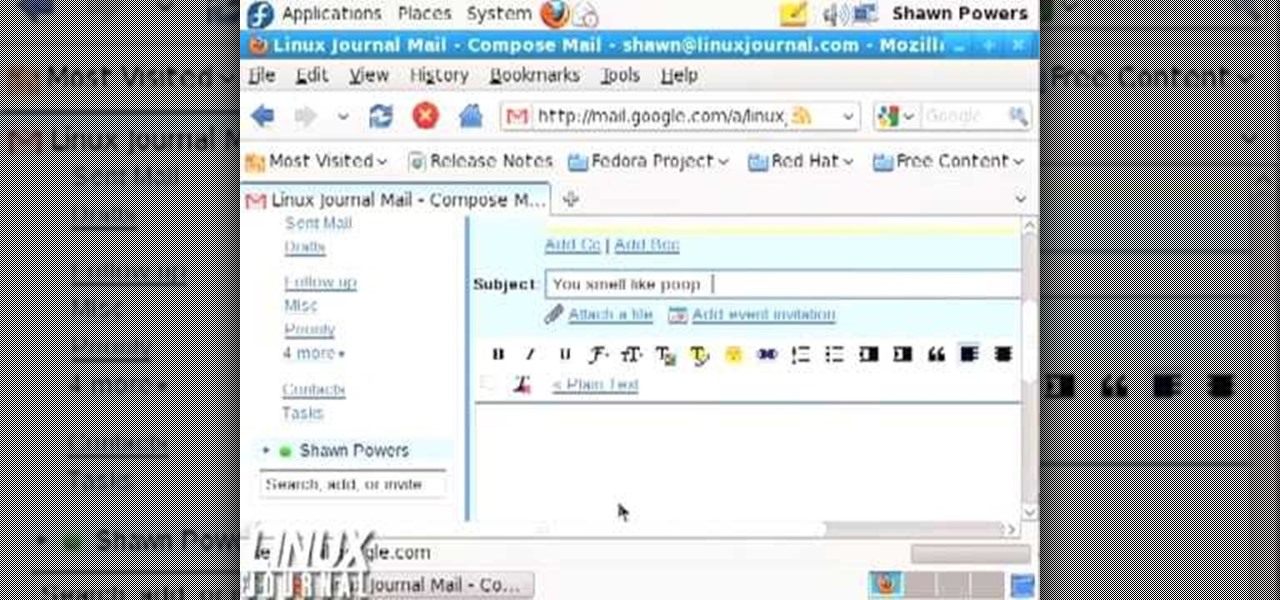
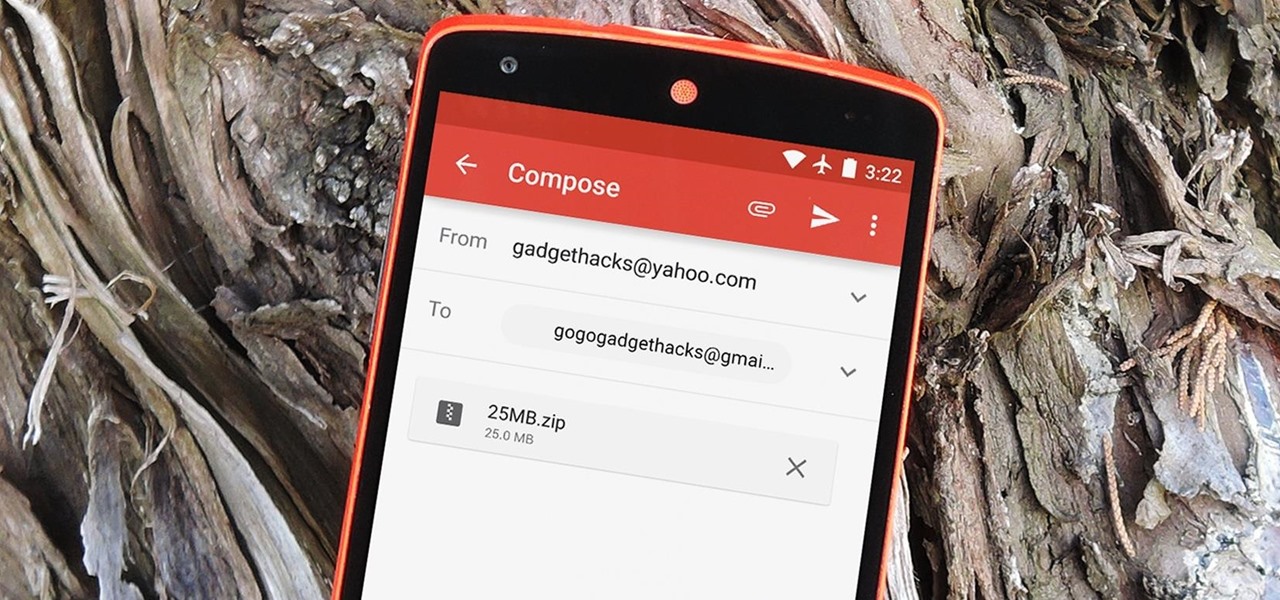
In this video tutorial, viewers learn how to unsend emails with the help of Google. Users will need a Google email account. Begin by logging into your Gmail account and click on Settings. Then click on the Labs tab under Settings and scroll down the page until you see "Undo Send". Now click on Enable and click on Save Changes. Now when users send an email, they can undo the email by clicking on Undo once they have sent the mail. Users will only have 5 seconds to undo an email after it has bee...
One way to keep your budget in line is with MoneyWell. This video tutorial for beginner users teaches you the ins and outs of setting up credit cards accounts, and how to manage them.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

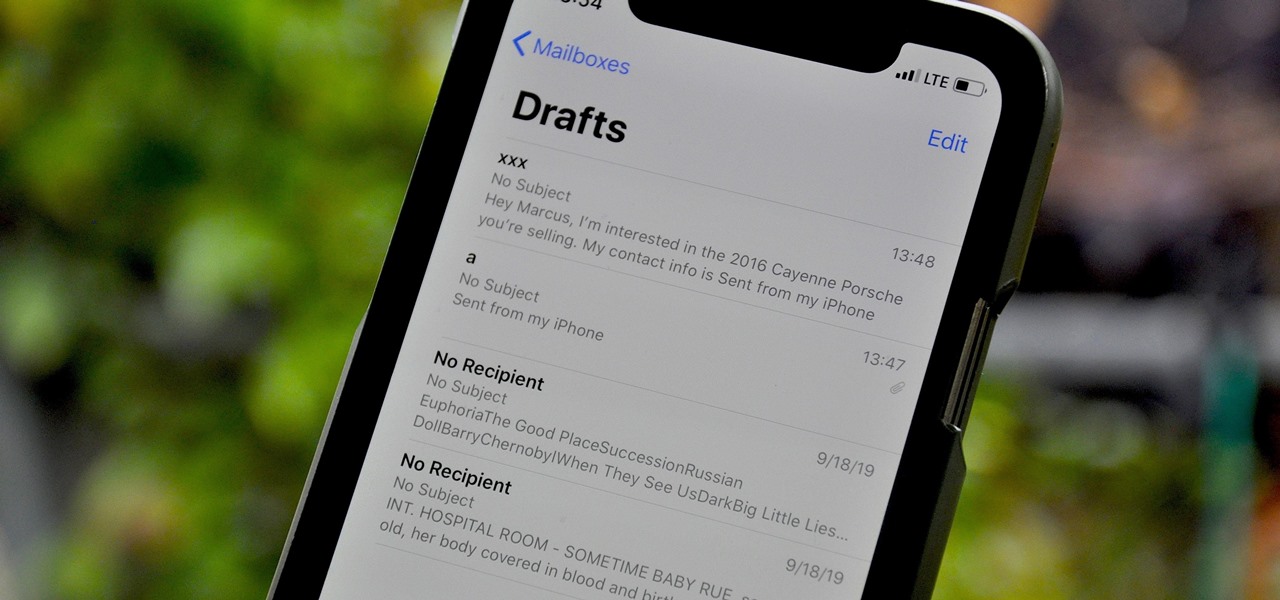
All of your partially written, unsent emails live in your "Drafts" folders, in limbo until the day they are sent off or deleted. In Apple's Mail for iPhone, you can access all drafts from all accounts in a combined "All Drafts" folder from the app's main Mailboxes list — but only if you added it manually. But there's an even better way to access all of your drafts in Apple Mail in iOS; it's just not obvious.

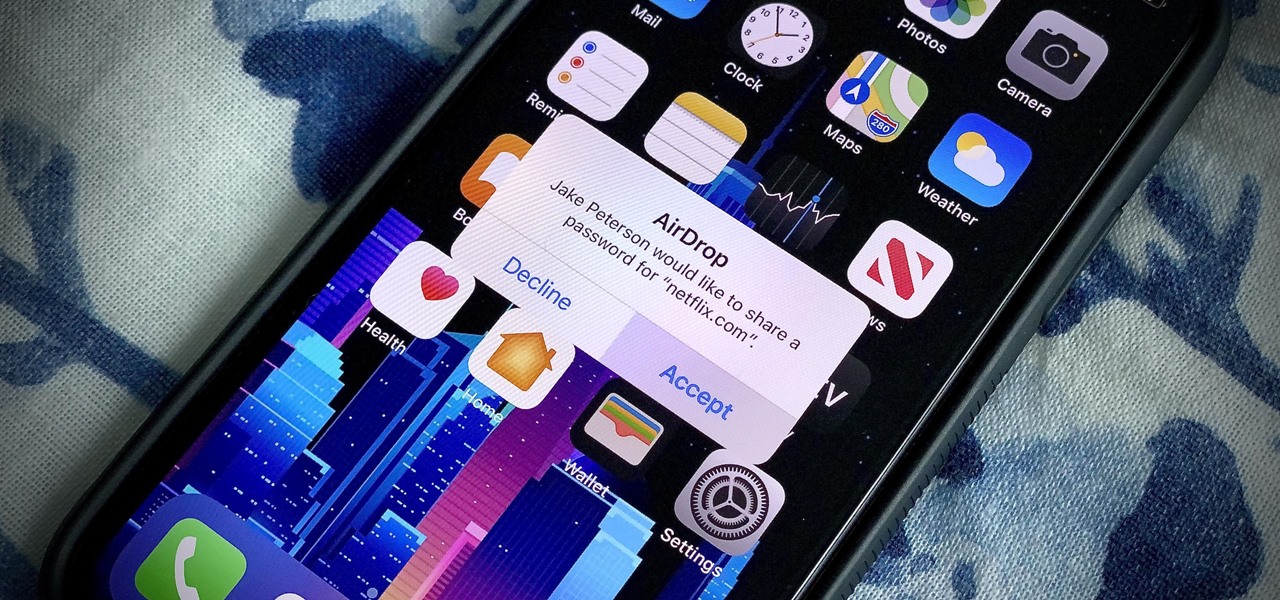
In iOS 11, Apple made it easier for you to share passwords with friends. Back then, it was just Wi-Fi passwords, which made sense. "What's the Wi-Fi?" gets old after a while. But now, whether you're running iOS 12 or 13, you can share any password you want with any iPhone around, all with one of iOS' best features: AirDrop.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

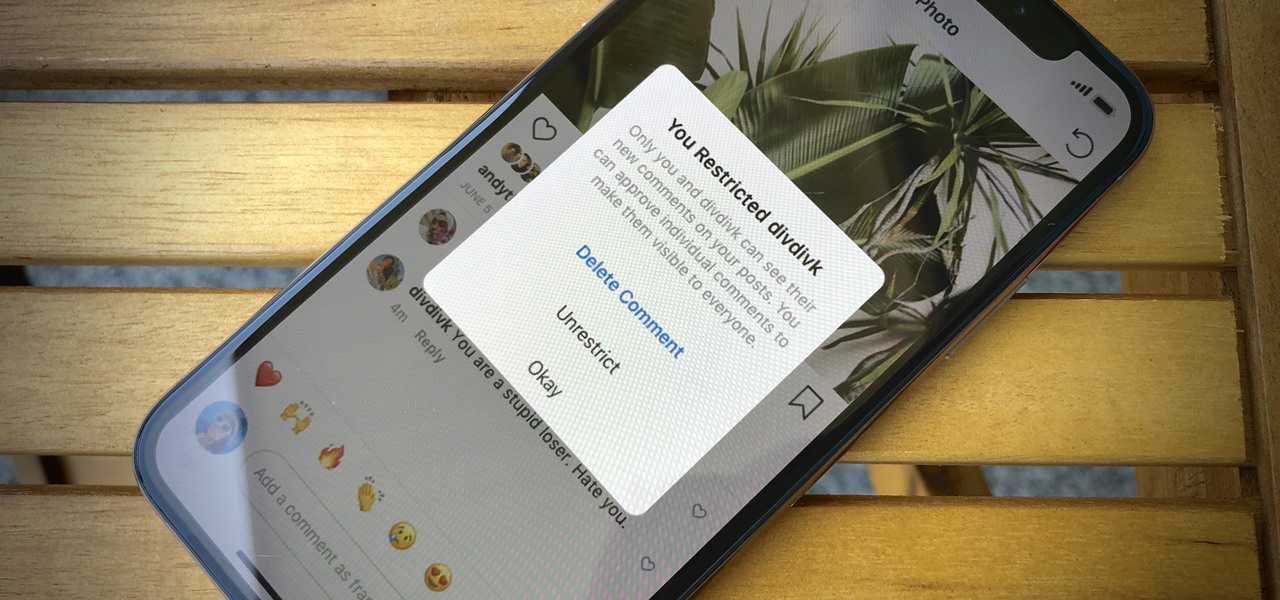
In general, the internet can be a cruel place, and Instagram is no exception. Most of the time, the platform is a fantastic way to share and view unique and creative content, to reach an audience of both fans and friends. People can step out of line and harass or bully others on posts to the detriment of the entire community. However, this type of commenting won't be sustainable for much longer.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Many apps, including Facebook, Twitter, and Facebook, do not let you download videos, even if they are living on your own account. Saving these videos usually requires a third-party app or screen recorder, which is inconvenient and can result in loss of quality. However, TikTok, the newish popular short-form video platform, makes it easy to download videos — even if they're not yours.

Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.

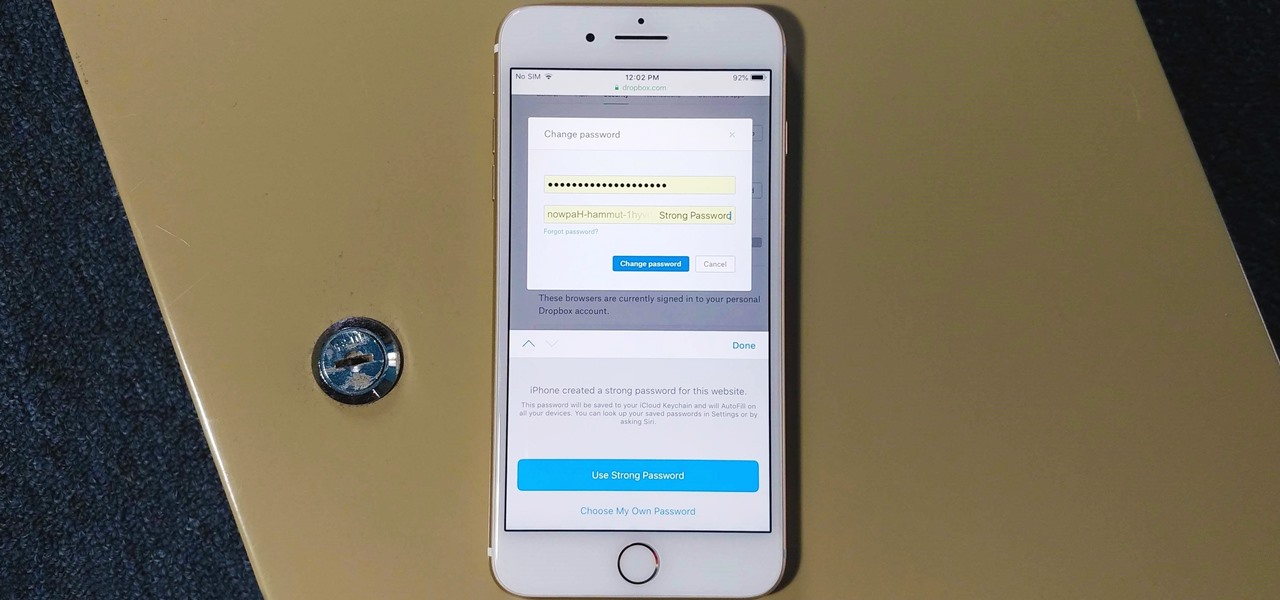
The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

Netflix currently lets parents block content based on maturity rating, but it isn't a perfect system. Not all titles rated PG-13 are equal, for instance. That's why it's good news that Netflix is adding more controls for parents, by allowing account holders to bar individual movies and TV shows they deem inappropriate.

Hashtags are the backbone of Instagram. They connect photos from users all around the world and give visibility to users who don't have many followers. Now, Instagram has added more functionality to this indispensable tool, and this new feature lets you follow hashtags in your main feed right alongside all the pics and videos you see already from people or companies you follow.

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

Making a custom location on Instagram is one of the best ways to generate traffic to your account. It gives you that extra uniqueness when it comes to standing out amongst other companies. It also allows people to check in at the same location, further promoting your account across other platforms.

Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Windows 10 runs on laptops, desktops, tablets, and even phones—but even though the operating system should scale accordingly, fonts and icons aren't always perfectly sized for every screen. Luckily, though, there's a handy new menu for adjusting the size of your screen's contents, which you can use to make everything bigger or smaller to match your preferences.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

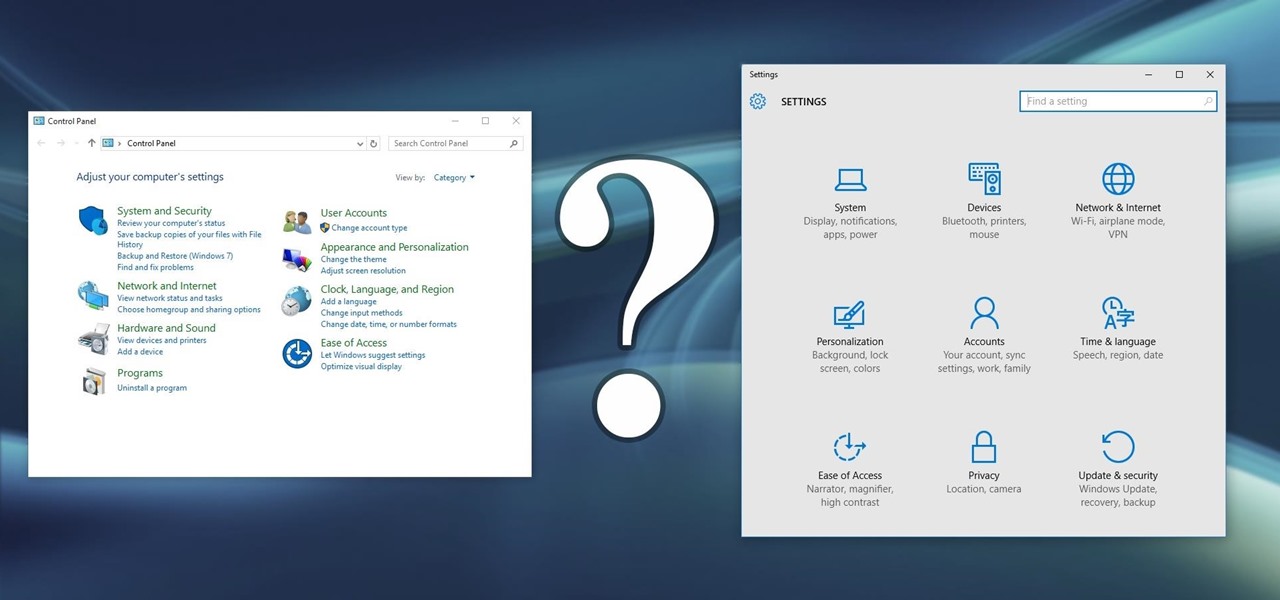
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

The Gmail app recently became stock Android's central hub for all of your email accounts. Instead of being limited to just Gmail accounts, the app can now handle POP3, IMAP, and exchange service email accounts, making it a one-stop shop for all of your emailing needs.

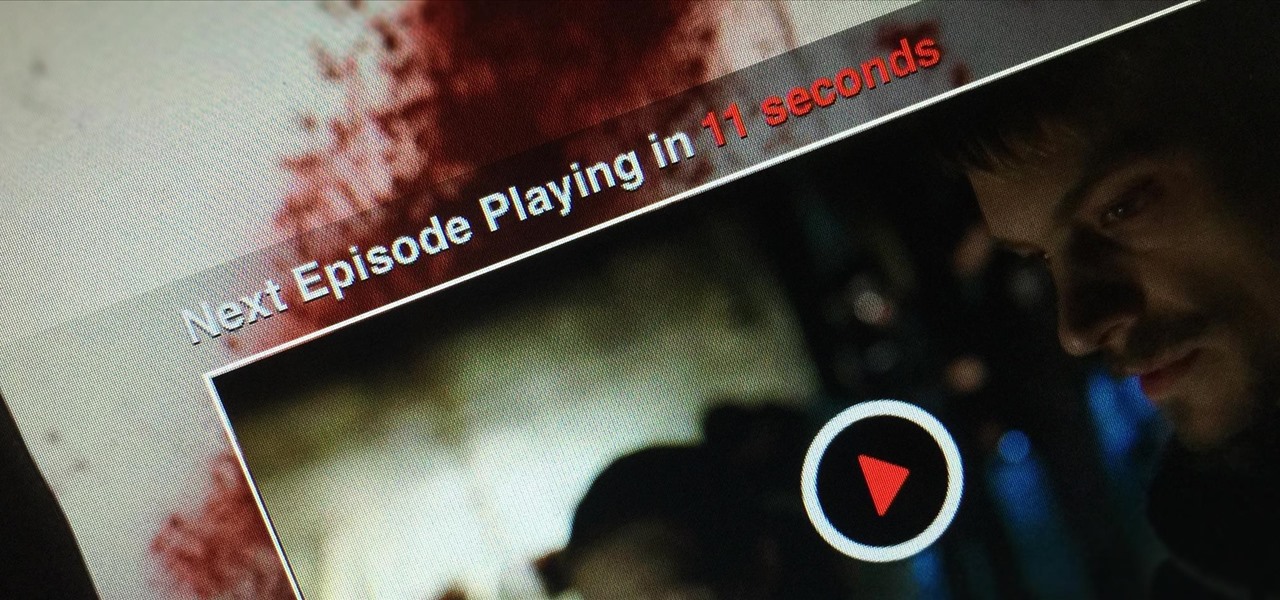
Netflix is an enabler. It creates a joy around binge-watching and couch potato-ness, and the major contributor to this epidemic is its built-in "Post-Play" feature.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

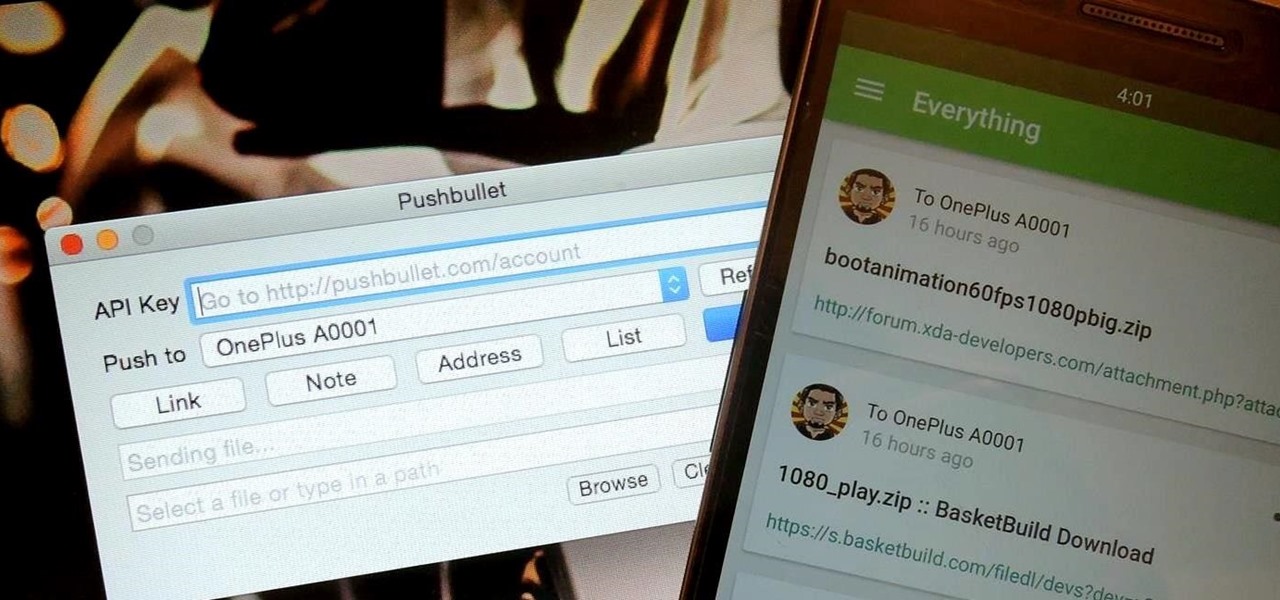
Before Continuity and Handoff were even announced, Pushbullet was already allowing users to quickly send notes, links, and photos between their devices with a few clicks.

Since the days of Friendster and MySpace, social media platforms have taken leaps forward, revolutionizing how we live our lives by changing the way we communicate with others. Not only has social media become a catalyst for major uprisings around the world, but on a personal level, it connects people together in ways that were unimaginable even 10 year ago—no one was taking pictures of their brunch to share with the world in 2004.

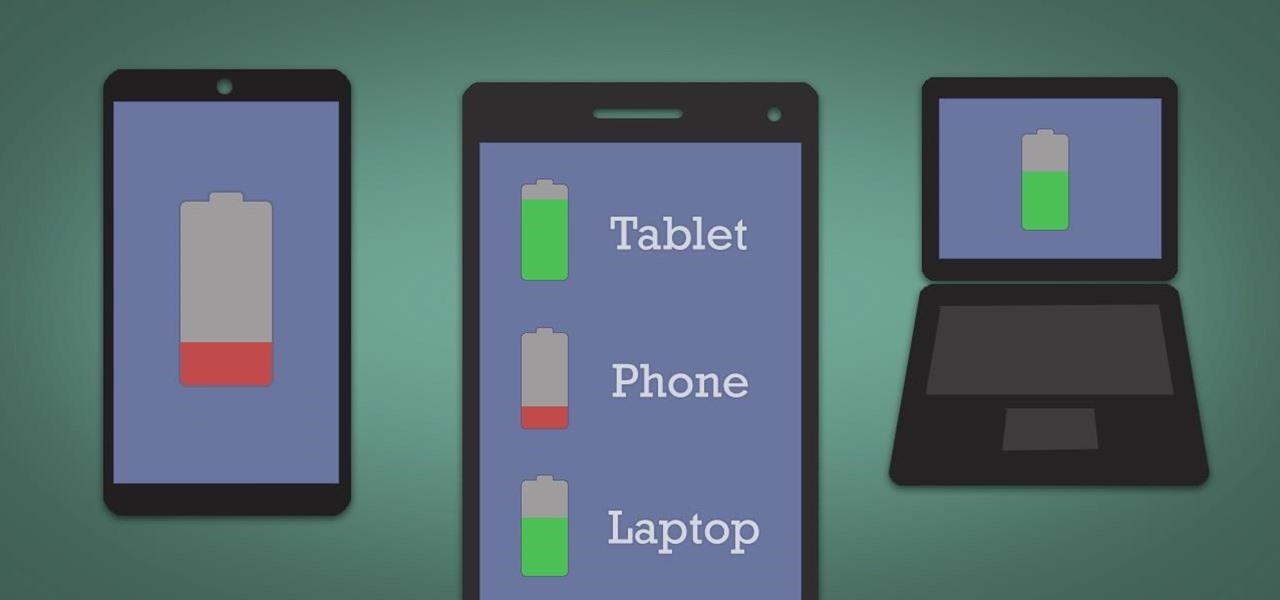
It's hard enough to keep tabs on the battery life of one device, let alone all of the different gadgets that a typical consumer owns in this day and age. Say your smartphone is running low on juice, so you switch to your tablet only to find out that it's almost dead as well. Better hope your laptop is fully charged, right?

This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

There is no SD card support on the Nexus 7, so managing internal storage can be tricky. There are ways to free up space, but the biggest space hog on my tablet is music, and that's not something I'm willing to delete just yet.

Netflix has received a lot of publicity lately, and not because of its impressive worldwide library. From blog wars with Comcast to streaming deals with Verizon, it's easy to forget that the company exists for our entertainment, but sometimes that entertainment has drawbacks.

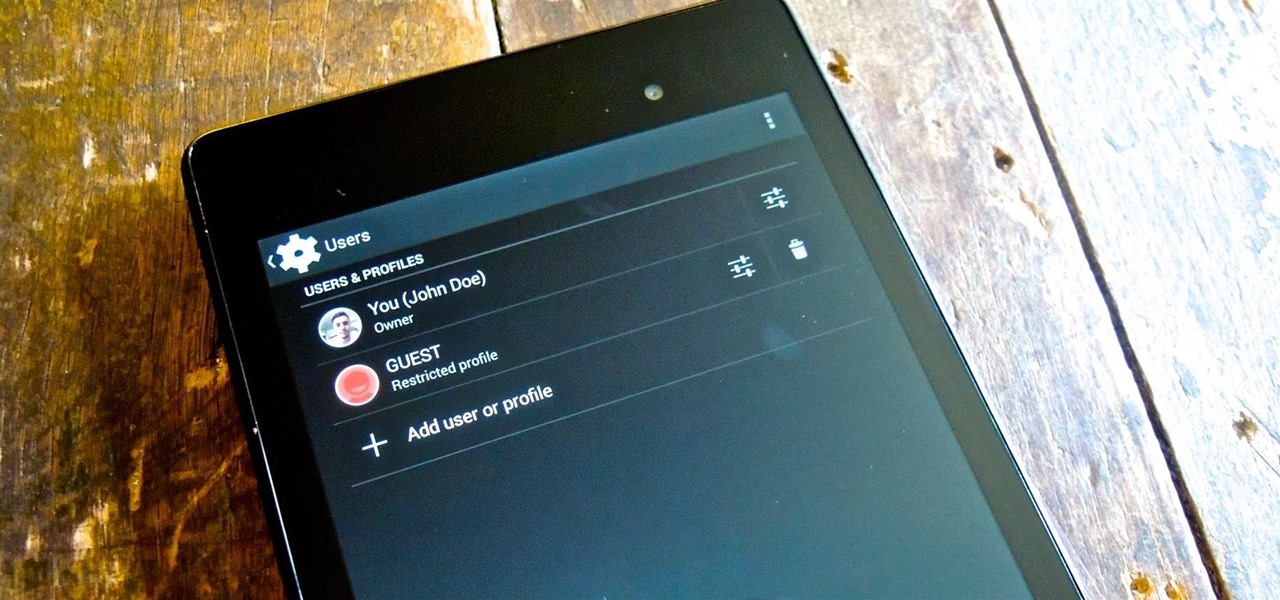
Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by accidentally opening a gallery or messaging app.

The majority of our documents and music are digital, which is great for convenience, but it presents a problem for those with a lot of stuff—where do you store it all? There are tons of sites that offer cloud storage, like Dropbox, SkyDrive, and even Flickr, but most of them have limits unless you want to pay, and no way to connect them all.

When it comes to text documents and spreadsheets, Microsoft Office is the be-all and end-all office suite—but it's not cheap. Paying anywhere from $140 to $400 puts a big dent in your bank account, especially if you're a broke college student eating ramen for breakfast, lunch, and dinner. Something that I wish I would've known about during college is Microsoft's HUP (Home Use Program). With HUP, any employee or student of an organization that has a Microsoft volume license is eligible to purc...

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.