Apple released iOS 12 beta 9 to developers on Monday, August 20. The company seeded the update just five days after releasing dev beta 8 to testers, itself a quick replacement for the problematic beta 7. This update was followed closely by public beta 7, confirming Apple's new same-day release schedule for both developer and public betas.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.
While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.
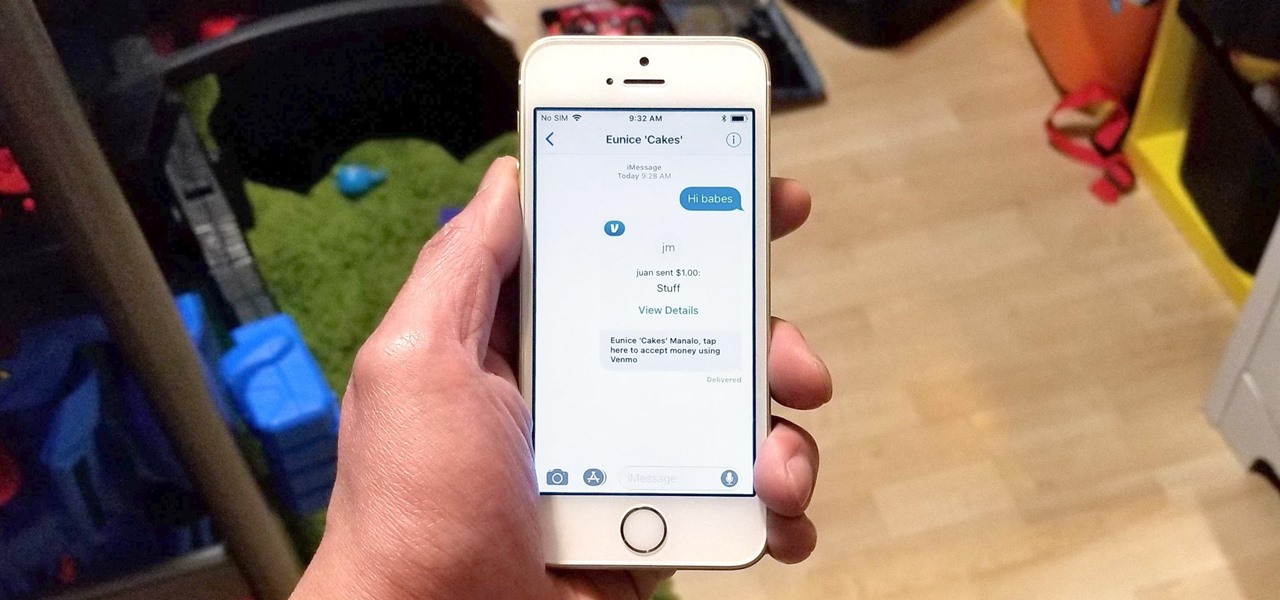
Venmo makes it incredibly convenient to send money to friends and family, and it all happens instantly from the comfort of your smartphone. Even better, if you have an iPhone, Venmo lets you conduct transactions straight from the default Messages app, giving you more flexibility and convenience over Android users.
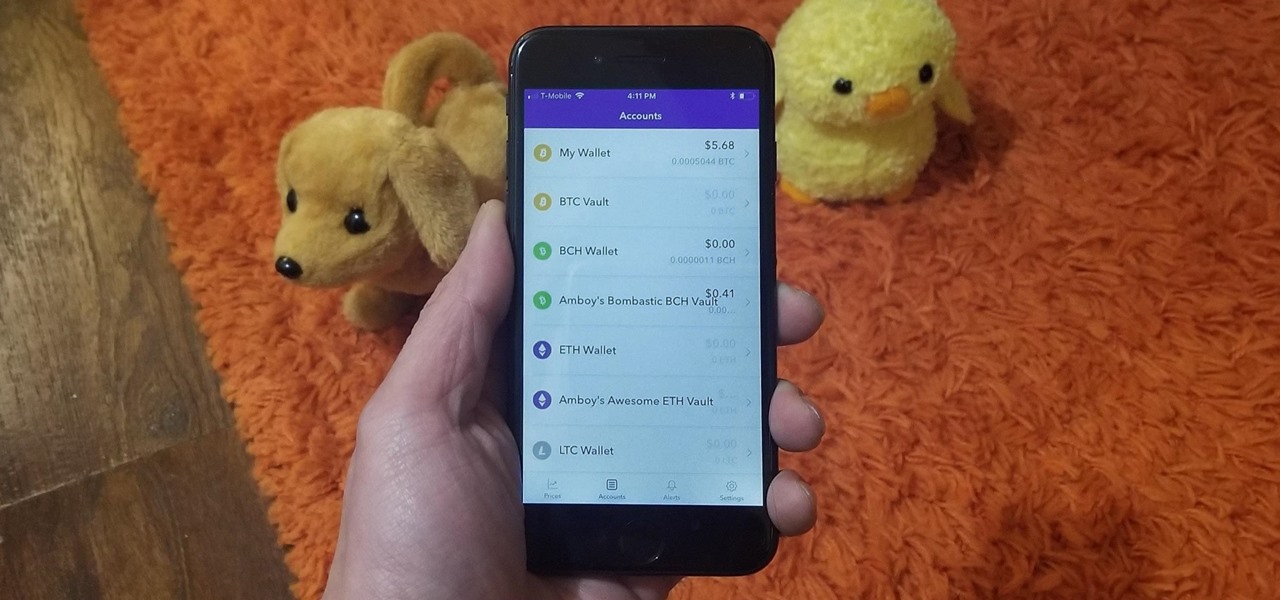
As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

IFTTT (short for If This, Then That) is an amazing piece of software that automagically links actions on your phone with online services and real-world objects. For example, an applet could read: "if you come home, then turn on Wi-Fi." IFTTT goes further than just using simple smartphone functions, though — thanks to applets, it's fully configurable with a ton of smartphone apps.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

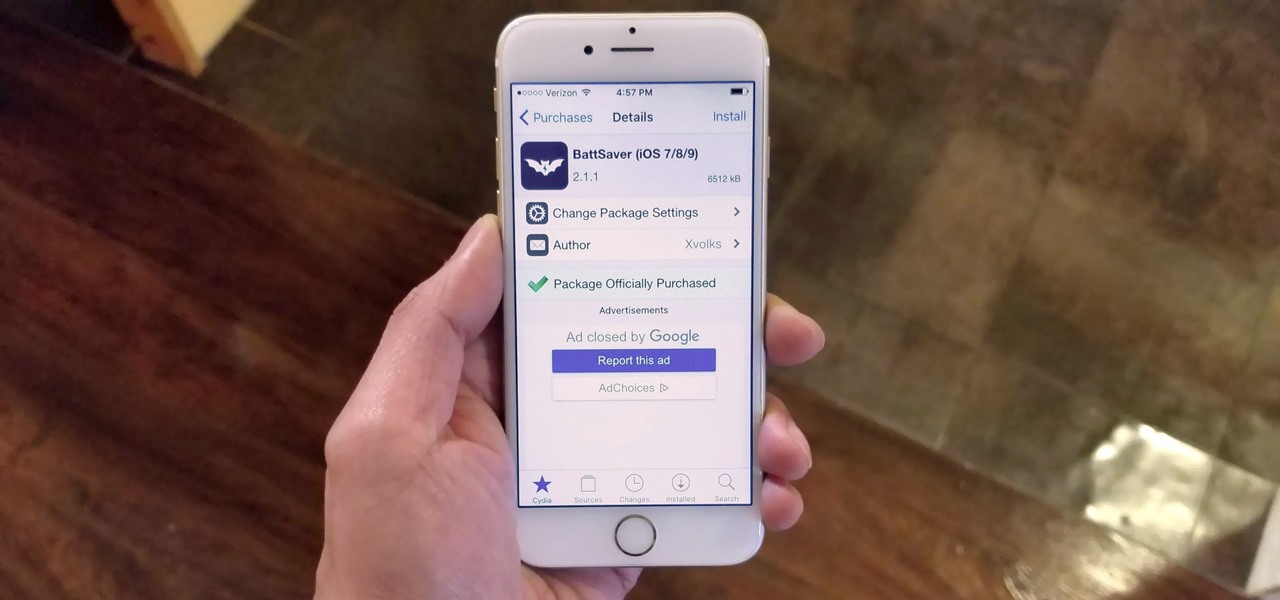
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.

When most people first become aware of Kodi (formerly known as XBMC), they hear about its ability to stream illegal content. But the real Kodi community knows that it's much more than just a haven for pirated material — it's an all-in-one media player that addresses the majority of home theater needs, particularly for those that decided to cut the cord.

Now that iOS 11 is official, everyone can enjoy all of the great new features available, but there are certainly a few bad seeds in there that you'll probably find annoying. Luckily, a lot of these disagreeable quirks can be changed for the better.

The Google Assistant comes in several different flavors. There's the baked-in Google app on Android, the dedicated Google Assistant app on iOS, and the Assistant-powered Google Home smart speaker. But no matter how you access it, your Assistant will only get better if you take some time to personalize things.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

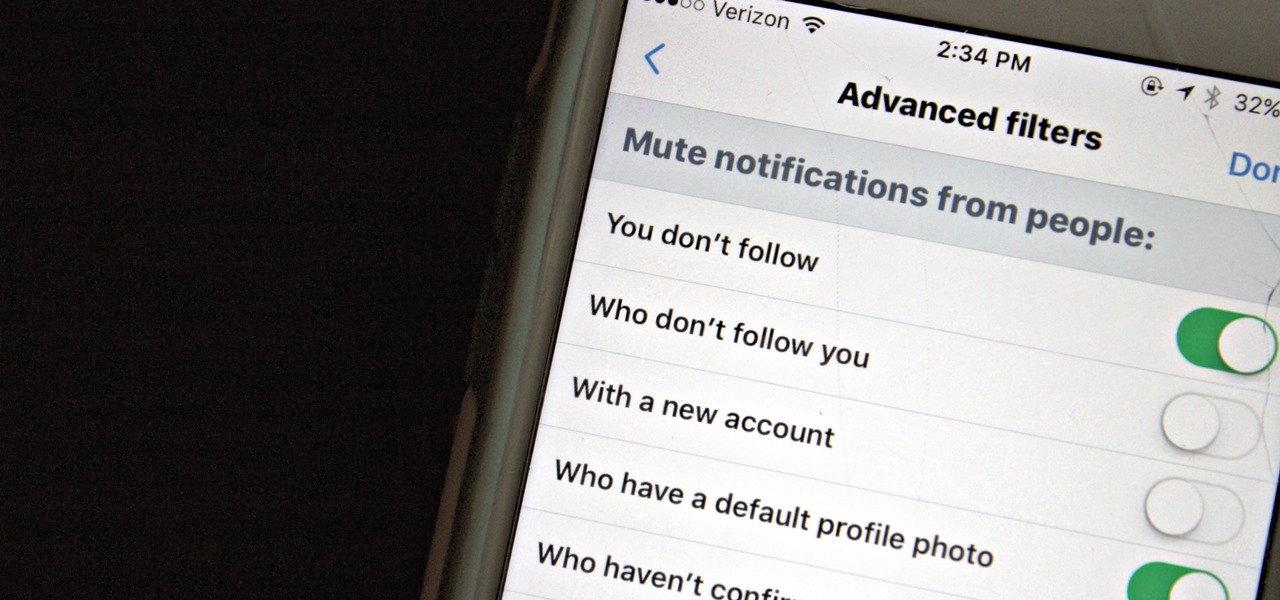
Twitter is a hotbed for abusive accounts. Because it's such an open app, strangers from all over the world can see your tweets. Obviously, not everyone agrees on everything, but sometimes things can escalate to the point where it's considered harassment from people you don't even know.

To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship.

In this first part of my series on getting started with Windows Holographic, we are going to cover everything you need to get set up for developing HoloLens apps. There are many pieces coming together to make one single application, but once you get used to them all, you won't even notice. Now there are different approaches you can take to make applications for HoloLens, but this way is simply the fastest.

Before we dive any further into getting your Mac ready for hacking, I wanted to continue on with the concept of encryption. In the last part, we talked about full disk encryption on your Mac, but now I want to quickly cover the encryption of disk images before we dive into managing passwords, terminal emulators, etc.

The new USB Type-C standard was supposed to revolutionize smartphone charging, but so far, it's done more harm than good. Many cable and charger manufacturers are struggling to keep their products in line with the proper USB-C specifications, so as a result, we now have to check to see if a cable is compliant before purchasing one.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Before you sell or give away an old iPhone, Find My iPhone, which works in conjunction with Activation Lock (Apple's anti-theft system) needs to be deactivated from your iCloud account. This also applies if you've lost your passcode and are locked out of the device, if you're restoring to a previous iTunes backup, or just want to remove it from your list of iCloud devices.

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

Your average Android phone or tablet comes with quite a few apps already installed—even before you turn the device on for the first time. These pre-installed apps are certainly helpful when it comes to getting your feet wet with Android, but in many cases, they're not always the best apps available for accomplishing the tasks that they perform. Additionally, many third-party apps can add lots of cool functionality to your device, so you might say that sticking with only the pre-installed apps...

Being an Google fanboy means that I pretty much use anything with the company puts out, so it's no surprise that out of all the cloud services out there, I stick with Google Drive. But, this is way more than just some blind allegiance.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

iCloud Drive is Apple's new solution to file management syncing across iOS and Mac OS X. If you've upgraded to iOS 8 and you have an iCloud account, you can use iCloud Drive to store files for certain apps. While you won't really be able to benefit with file syncing between iOS and Mac apps until you get Yosemite, you can still access your iCloud Drive documents online.

Google's text-to-speech engine is getting pretty good these days. In a recent update, the computerized voice that reads on screen text (like Google Now search results) got an audio quality bump that brought its clarity up to its highest level yet. And with each update, that robotic voice becomes a bit more human.

The level of customization that Android has to offer is insane. You can replace the stock keyboard and home screen with any third-party app of your choosing, allowing core experiences to be tailored to fit your needs.

Notice anything different about your Google searches lately? Your favorite businesses are becoming even more reachable online. Now, you can simply Google a business and click on its highlighted phone number to give them a call immediately from your computer.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

I have an embarrassing habit: I type with six fingers. Just as your grandma pecks at the keyboard with her two index fingers, I rely solely on my index, middle, and thumb fingers only. But it's not as slow as you think, and I'm not the only one out there that does it.

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

Your Nexus 7 may be a tablet, but it can also be used as a phone, thanks to the continued upswing of VoIP applications, which send voice and media messages over the Internet—not over a cellular network.

When the 6.1 version of iOS was released back in February, complaints of severe battery drainage for iPhone, iPad, and iPod touch users exploded onto every Apple-related forum on the Internet. Everyone was either losing a percentage every three or so minutes, or their battery only lasted half as long as it did before the update. Earlier this month, Apple released iOS version 6.1.3, to supposedly fix a recent exploit that allowed anyone to bypass the lock screen—but as it turns out, the update...

If you haven't figured it out by now, a foundation that matches your skin tone and skin type perfectly may not work at all for your friend, and vice versa. When it comes to makeup, customization is your best friend.

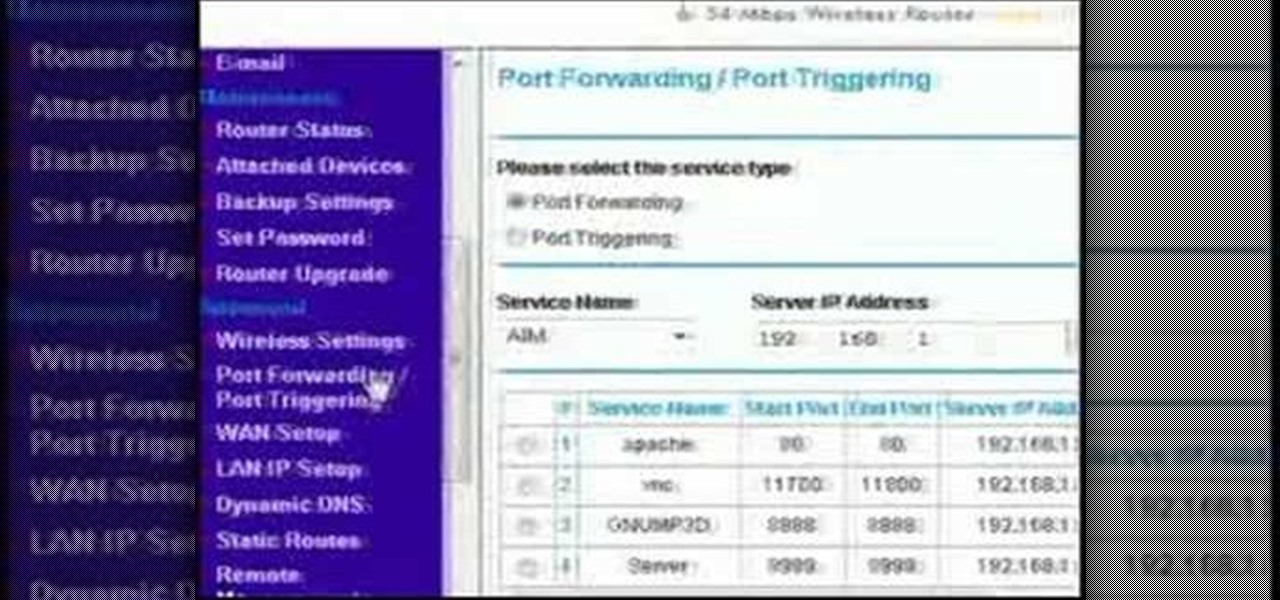
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

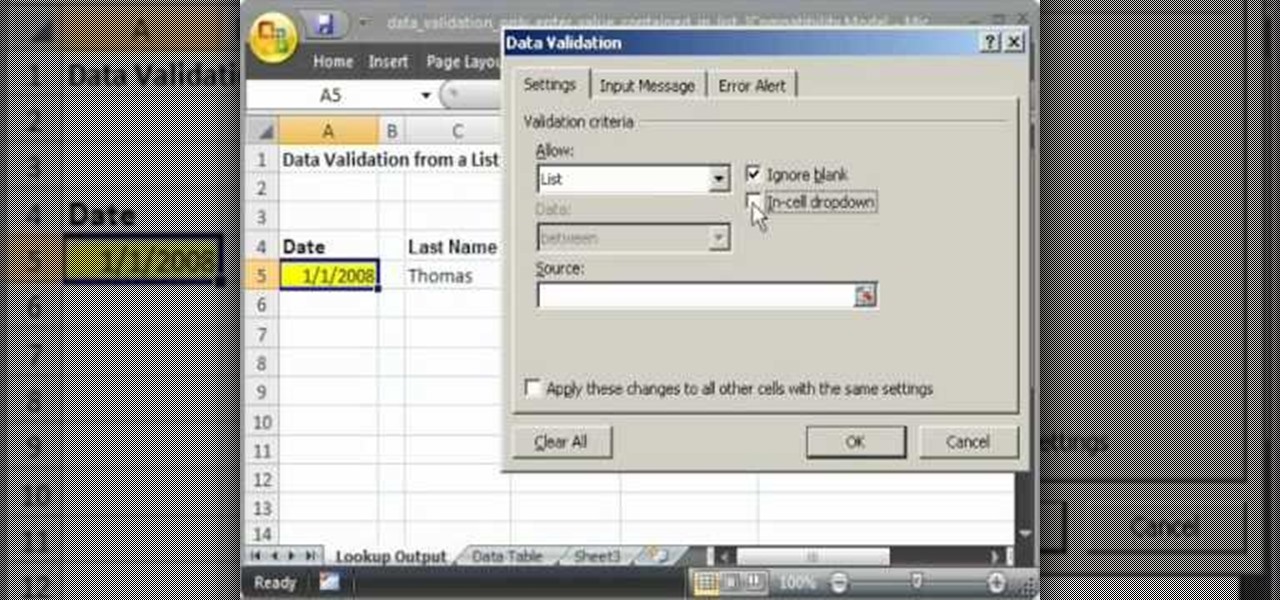
This video shows you how to idiot-proof a data set in Excel pretty much. It demonstrates how to enable data validation in a cell, so that when you type something in it must be in a predetermined list or will not work. Start by typing in your data table in a second tab. His example is a date, then information about certain employees based on that day. To enter the data validation menu, click the cell you want to use and then hit ALT+D+L to bring it up. Go to settings, then under the Allow menu...

In this video tutorial, viewers learn how to choose the right icing for any cake. This video describes the different types of icings that can be used to decorate cakes. Butter cream icing is very versatile and consistent. Very soft and easy to work with. Royal icing is a type of icing that dries out. Rolled fondant is very similar to modeling clay, except it is edible. It can be a covering or decoration on a cake. Poured fondant used as a covering or filling for a cake. Whip cream can be used...

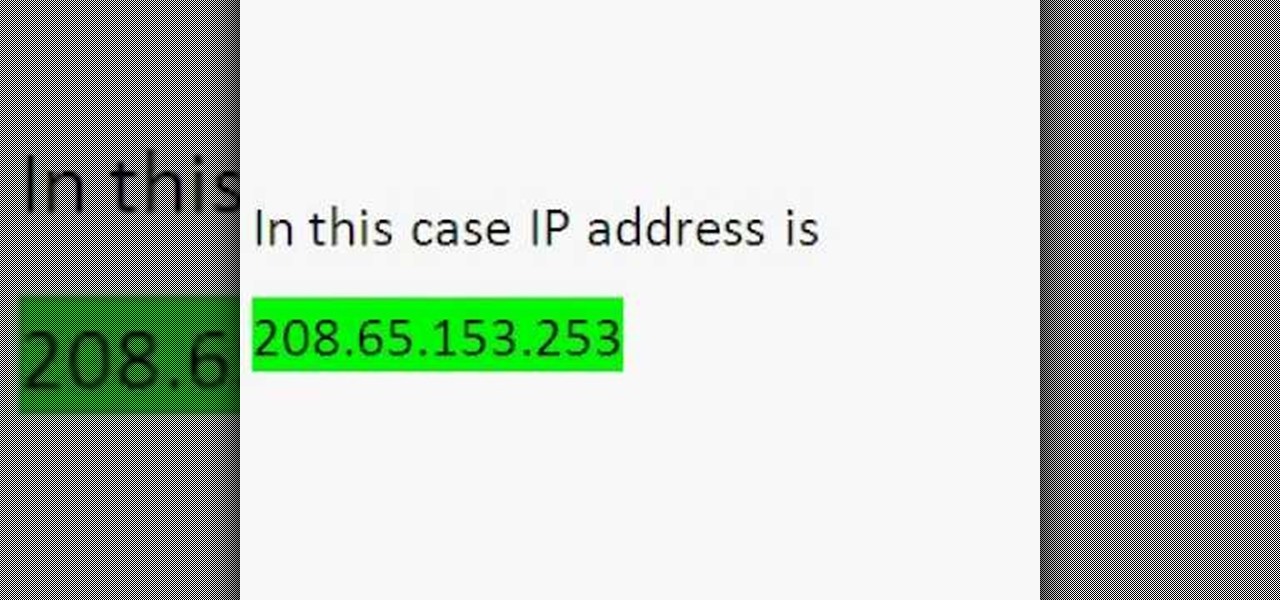
Wondering how to find the Internet Protocol address of a website?