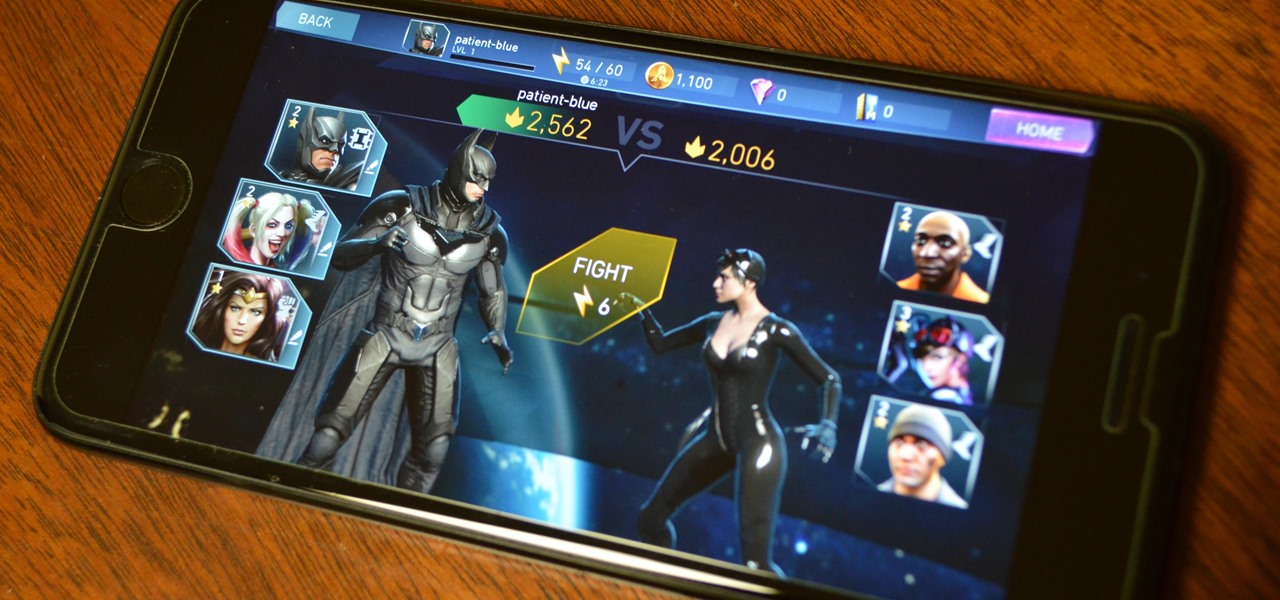
Based in the DC Universe, Injustice: Gods Among Us was a runaway success on the iOS App Store, generating enough downloads to rival its console-based iteration in terms of popularity. But now, the sequel to this long-running game, Injustice 2, is finally out in the wild, as it was soft-launched in the Philippines this past February.

Throughout the summer and fall of 2016, in the sudden whirlwind that was Pokémon GO, it was hard to go anywhere in public without seeing someone attempting to catch Pokémon. Now, thanks to an upcoming platform called Motive.io, from the Vancouver company of the same name, location-driven application development will soon be accessible to everyone.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader is absolutely pointless, as having it locked will not hinder normal device usage, which is kinda true.

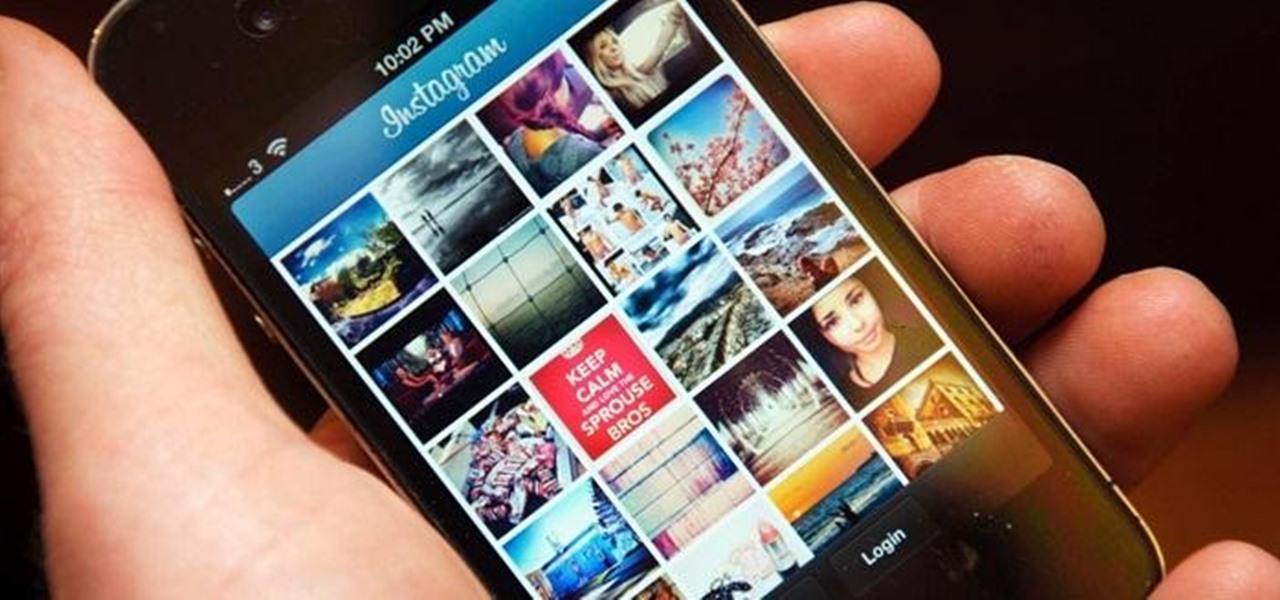
If you want to become a food Instagram star, you may want to consider having babies. Well, to be more specific, you might need Mike Chau's two adorable children, Matthew and Samantha.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

For the past three or four months, Microsoft has been pushing advertisements onto the lock screens of some Windows 10 users as part of its "Windows Spotlight" feature. This feature normally shows you scenic photographs and gives you the option to learn more about them by launching an Edge window once you log in. However, the aforementioned users have reported seeing the image below for the new Rise of the Tomb Raider game. Rather than taking you online in Edge to learn about it, you're given ...

By default, the Play Store app on Android is set to automatically update your apps in the background. This definitely makes it easy to ensure that you're always running the latest versions, but it does come with some downsides.

Android's Google Play Games app has let you track your feats and accomplishments in the games you play for quite a while now, but for some, the immersion experience might be broken after you finish dominating a game only to see your regular-ass name from your Google account on the leaderboard.

Ready or not, the USB-C cable is about to take over your electronics. The new industry standard is fully reversible and packed with enough power to serve as a laptop charger or an HDMI cable, so it actually has the potential to replace every cord, wire, and connector in your house. In fact, the conversion has already started: The latest MacBook, Chromebook Pixel, and Nexus phones are sporting USB-C connectors out of the box.

The first time you launch any type of file, Windows 10 will usually prompt you to select an app to open it with. Occasionally, though, this "Open with..." screen doesn't show up, and instead Windows will use a pre-installed system app to launch the file without ever giving you a choice in the matter.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

When it comes to news, updates, and arbitrary nonsense, it's hard to find a better source than Twitter. And for some of us, the best way to consume Twitter is through the web (versus a mobile app). But as much as I prefer the standard browser version, it's easy to make it better, faster, and more convenient using a few Chrome extensions—and here are my favorites.

Hi, dear co-apprentices and wise masters. I've been recently trying to learn the basics to hacking here, and I've read all guides on Wi-Fi hacking and noticed no word is dedicated to this awesome script that comes bundled with Kali!

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

In today's world, we're constantly switching back and forth between all of our internet-connected devices. A PC may be great while you're at your desk, but the living room couch is tablet territory, and nothing beats the portability of a pocket-sized smartphone while you're on the go.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

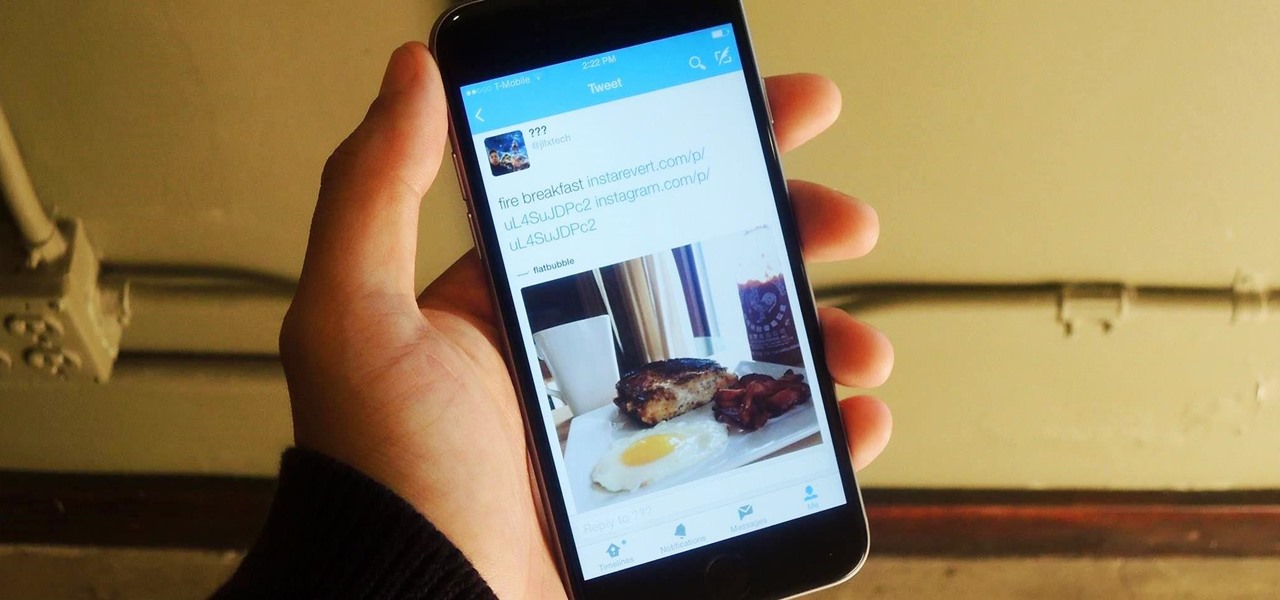
In late 2012, Instagram CEO Kevin Systrom made a sudden and controversial change to his social media service when he removed Twitter Card support.

Apple released iOS 7.1.2 just over three weeks ago, mostly to address some big security issues and a few minor bugs. Unfortunately, the update came with a problem of its own regarding missing contacts and iCloud syncing.

As great as Google's own Play Music app is, your MP3 library is restricted to Google's own app. There are much better music players that give Google Play Music a run for its money, but duplicating music files on your device for this reason alone is a waste of storage space.

The folks behind StumbleUpon have created a video service that is just as awesome at introducing you to new content as their website service is.

You can't always have your media on the same network as your Chromecast. Say you're at a friend's house or even out of town—it sure would be nice to cast your videos when you're out and about, wouldn't it?

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

Hey guy's, hope everything's going well! Here's a snippet of a few cool things and the latest news on Minecraft.

It has been 7 long years since the PlayStation 3 was released, which makes it no surprise that over 1 million gamers purchased the new PlayStation 4 this weekend.

If you had the original Microsoft Surface with Windows 8 and a Type or Touch cover, you know how big a pain in the ass it was to change the scrolling direction of the trackpad.

The first thing I do when I get a new phone is ditch the USB cable. At least, when it comes to data transfer. My brand new HTC One came with a USB cord that feels sturdy, but like any other cable, it will eventually fall apart from overuse. It will probably still charge just fine, but at that point it will be unreliable for transferring data. Lucky for me, there's a solution. Transfer files over the air. This will let you save that USB cord only for charging and the occasional situation when ...

It only takes a minute for something well intentioned to turn into something sinister. Facebook created 'memorial pages' as way for friends and family to share their thoughts and feelings for those that are no longer with us.

It might be time to move those Instagram photos to another service. It seems that Instagram has never heard of the phrase, "If it ain't broke, don't fix it." In a very big WTF moment, the extremely popular photo sharing and editing app decided that it has the right to sell its users photos to third parties without pay or notice. Yep, you heard that right. That photo you took of your girlfriend laying out on the beach could be in the next stupid Corona commercial without your consent and witho...

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

Most people have multiple email addresses these days. Gmail is one of the more popular services, but did you know you can access your Gmail account using the Mac OS X mail program? Not only is it possible, but it is incredibly easy!

Getting locked out of a bedroom or bathroom can be a real bummer. Fortunately, these locks are easy to "pick" and get yourself in. This how to shows you clearly what to do to get yourself back inside so you don't feel frustrated all day long. This excellent video takes you step by step through the process. This video talks about 2 different types of locks and the two different types of tools you'll need.

This video series come straight from Google. It's about their new web-based product called Google Voice, which provides you with one phone number for all of your phones (landline, cell phone, etc.), giving you full online control of your telephone experience. Google Voice also allows you to make free domestic calls anywhere in the United States and Canada, gives you a cool voicemail account that's just like an email account, and many enhanced calling features.

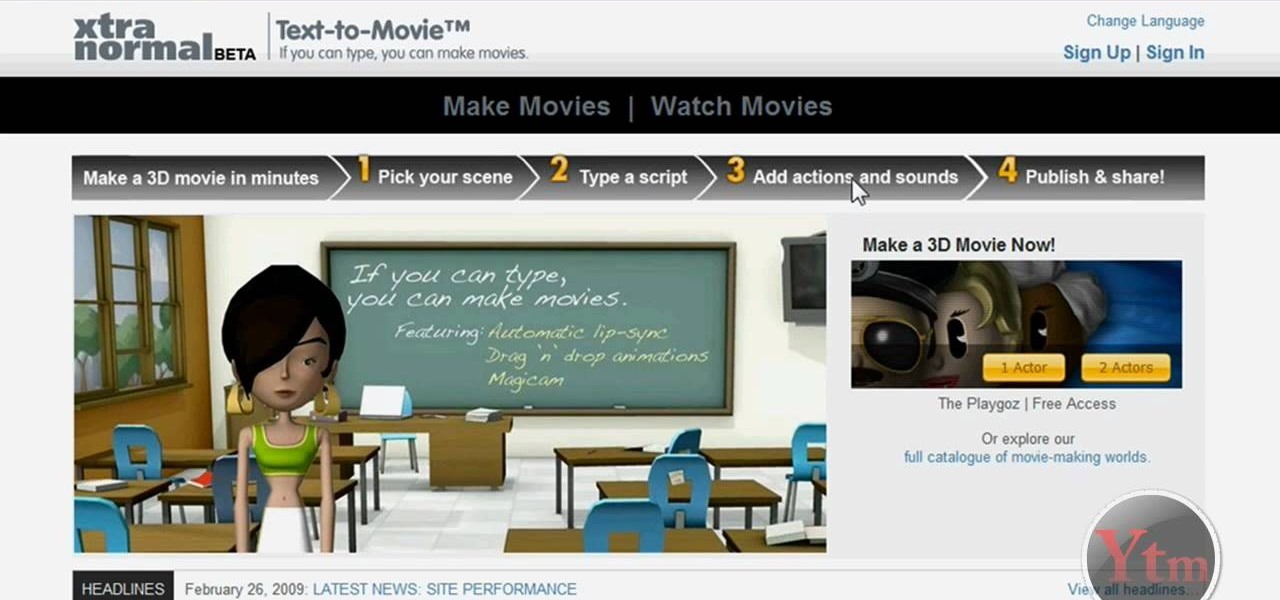
This video will show you how to create a 3D cartoon character using a website called Xtranormal. In the program, you should first pick the scene where you want your action to occur as well as the 3D character which you would like to be present in the scene. You can then type a script and choose a voice for the character to speak. The website will be able to read your script and your character will say whatever you have typed. Next, you can add additional sounds and add actions to the cartoons...

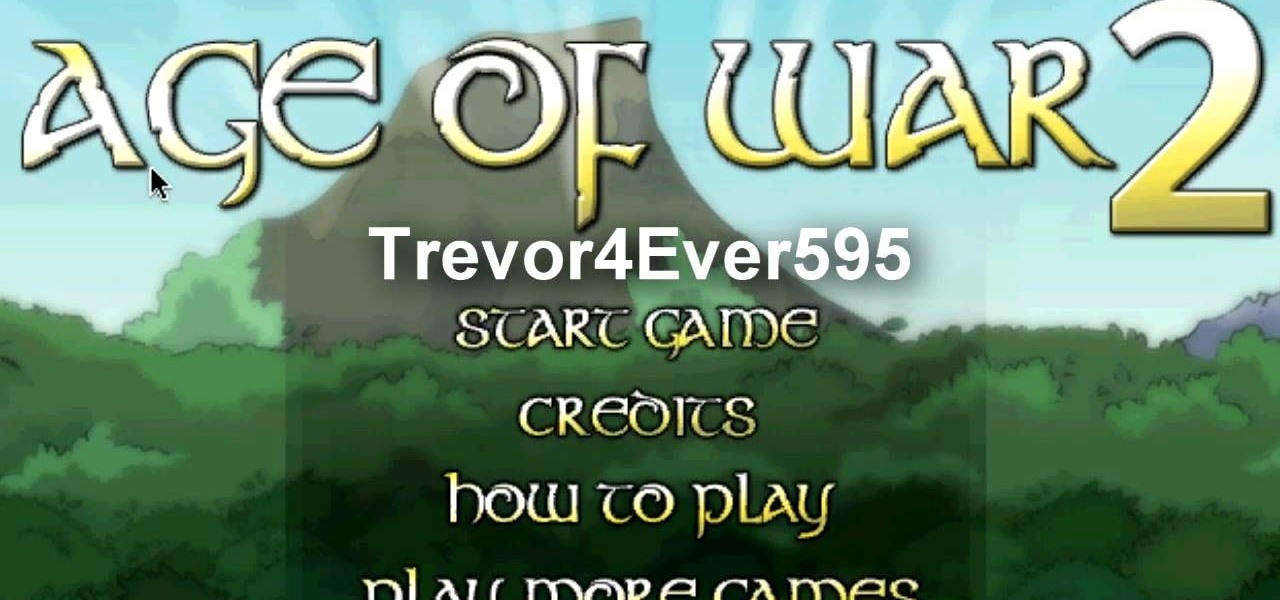
In this video tutorial, viewers learn how to hack the flash game, Age Of War 2. Users will need to download the Cheat Engine program for this process. Begin by starting the game. The game should start with 2500 gold. Then pause the game and open Cheat Engine. Click on the Process computer icon and select the current web browser. Now type "@500" into the Value box and click First Scan. Then deduct your amount of gold, type in the new value and click on Next Scan. There should only be 1 result ...