Netflix has received a lot of publicity lately, and not because of its impressive worldwide library. From blog wars with Comcast to streaming deals with Verizon, it's easy to forget that the company exists for our entertainment, but sometimes that entertainment has drawbacks.
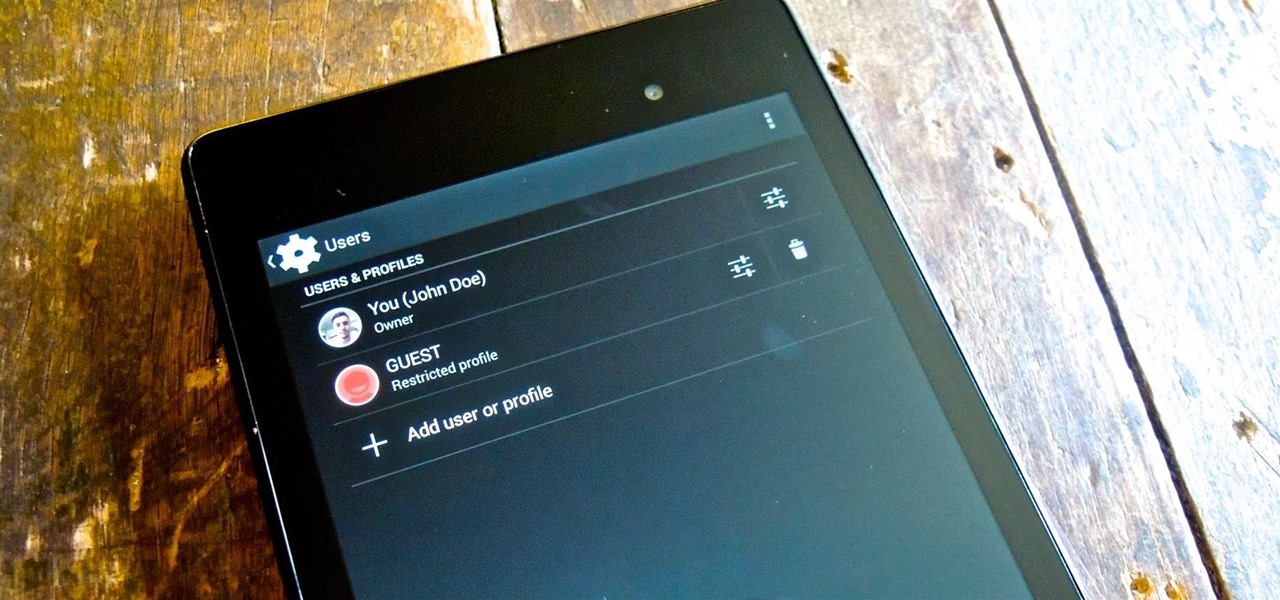
Whenever I hand my tablet over to someone, my heart always races for a second at the thought that they may stumble across my private pictures, texts, and videos. I trust them, and they may not be the snooping type, but it can be easy enough to come across private stuff by accidentally opening a gallery or messaging app.

Hey guy's, hope everything's going well! Here's a snippet of a few cool things and the latest news on Minecraft.

It has been 7 long years since the PlayStation 3 was released, which makes it no surprise that over 1 million gamers purchased the new PlayStation 4 this weekend.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

The first thing I do when I get a new phone is ditch the USB cable. At least, when it comes to data transfer. My brand new HTC One came with a USB cord that feels sturdy, but like any other cable, it will eventually fall apart from overuse. It will probably still charge just fine, but at that point it will be unreliable for transferring data. Lucky for me, there's a solution. Transfer files over the air. This will let you save that USB cord only for charging and the occasional situation when ...

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

Forum member Luciano posted a terrific guide on adding hacks to our phone by editing build.prop. The article was great, but one of best things I saw in it was the "What You'll Need" section:

It only takes a minute for something well intentioned to turn into something sinister. Facebook created 'memorial pages' as way for friends and family to share their thoughts and feelings for those that are no longer with us.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

There have been plenty of headlines recently about fake followers in both politics and entertainment. Everyone gets hit by a spam account here and there, but when a large percentage of someone's followers are fake, it can look pretty bad, especially with influential people being accused of buying their followers to look more popular.

Hello, today I will tell you about how you can create a page through wordpress. this is a performance for those who have scarcely been touched wordpress. This guide will put you through basis and create a user and a website among millions of people.

Forex— what is it? Any investor could tell you a complicated description of what Forex is, but the basics of the FX currency markets is— an over-the-counter financial market for trading currencies. The foreign currency exchange market has no central exchanges like the stock market and little regulatory oversight. With this beginner’s guide, learn the trading basics.

This video discusses the basic steps necessary to start an online business. The first thing you need is a name for your business. Keep it simple, easy to spell and remember. Once you have your name, register it with the government. Next, find a good hosting company for your website. He recommends Godaddy.com. Also a good web designer is a necessity. They will meet with you to discuss your ideas, and your website should be ready in about a week.

This video explains how to send the Text message to any where specifically to mobile using Yahoo mail. To do that first type the "www.yahoo.com" or "www.yahoomail.com" in the browser. And then choose the Mail option from the front page of the yahoo website. From that click the sign in option, and give your Mail id and password in the yahoo sign in page now you will logged into your yahoo account. Into your account you will have the "New" menu option on left to corner. From that you have to ch...

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

Wearing masks and social distancing doesn't sound like a fun movie night with friends, but you can still be comfortable and watch films together remotely. Services like Discord and Netflix Party make it possible to watch movies simultaneously from different parts of the U.S., and now you can do it with Movies Anywhere too.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Everyone should know that assigning complex passwords to sensitive digital accounts is the best practice for protecting yourself against hacking. Those who adhere to password creation best practices also know that keeping up with passwords for every account is nigh impossible, even when using passphrases. This is why using a password manager is highly recommended.

Your Apple Music subscription is tied to the Apple ID that subscribed, so you can stream content from any iOS, iPadOS, macOS, tvOS, or watchOS device that your Apple ID is signed in to. However, things get slightly more complicated when you want to listen to Apple Music on another device you use with a different Apple ID, such as a work iPhone. Complicated, but not impossible.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

MoviePass was once the best subscription service on the market for getting cheap movie tickets. For the price and the number of films you could see and save money on, it was unbeatable, but recent changes to the service have made it less enticing. While it still works well for some users, others may have to rely on other options. Personally, I'm leaning toward the latter.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

Ever notice how some augmented reality apps can pin specific 3D objects on the ground? Many AR games and apps can accurately plant various 3D characters and objects on the ground in such a way that, when we look down upon them, the objects appear to be entirely pinned to the ground in the real world. If we move our smartphone around and come back to those spots, they're still there.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

It hasn't been long since Apple released iOS 16.0 with over 350 new features, but iOS 16.1 just came out with even more cool updates for your iPhone. While some of the recent upgrades were expected, others are somewhat surprising — and there's even one that you may not even think was possible.

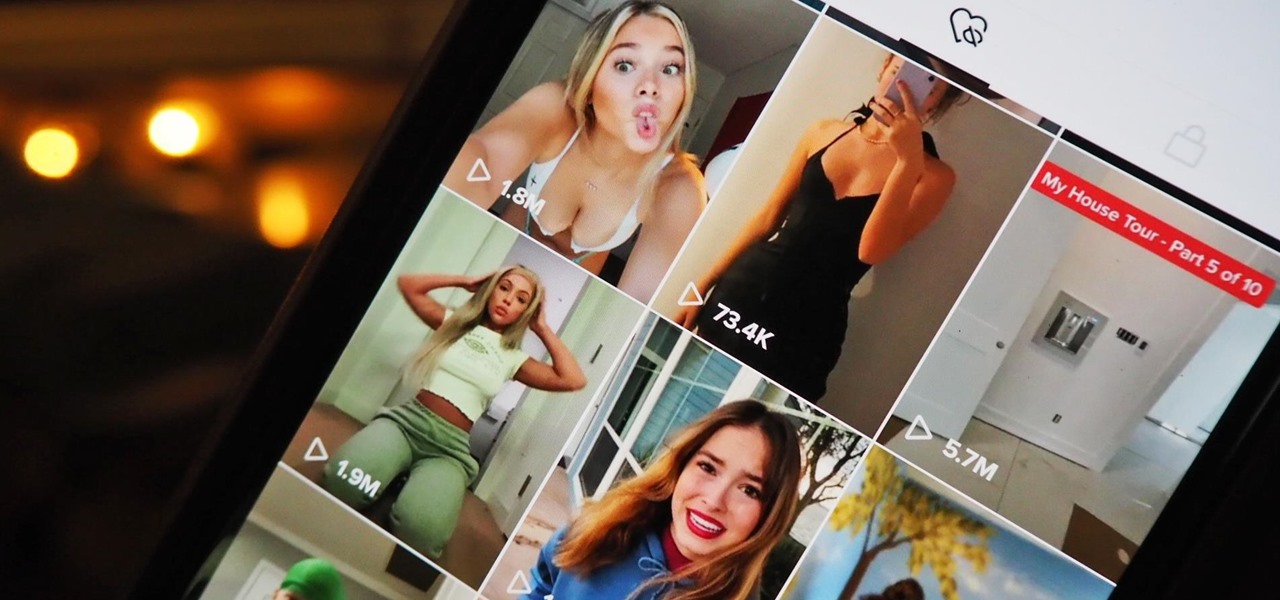
Every video you like on TikTok, whether it's a stranger performing a series of choreographed movements or a celebrity showing off their new workout, is saved to your profile. If you want to watch your liked videos at any time in the future, you can easily do so from your profile — but so can everyone else.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

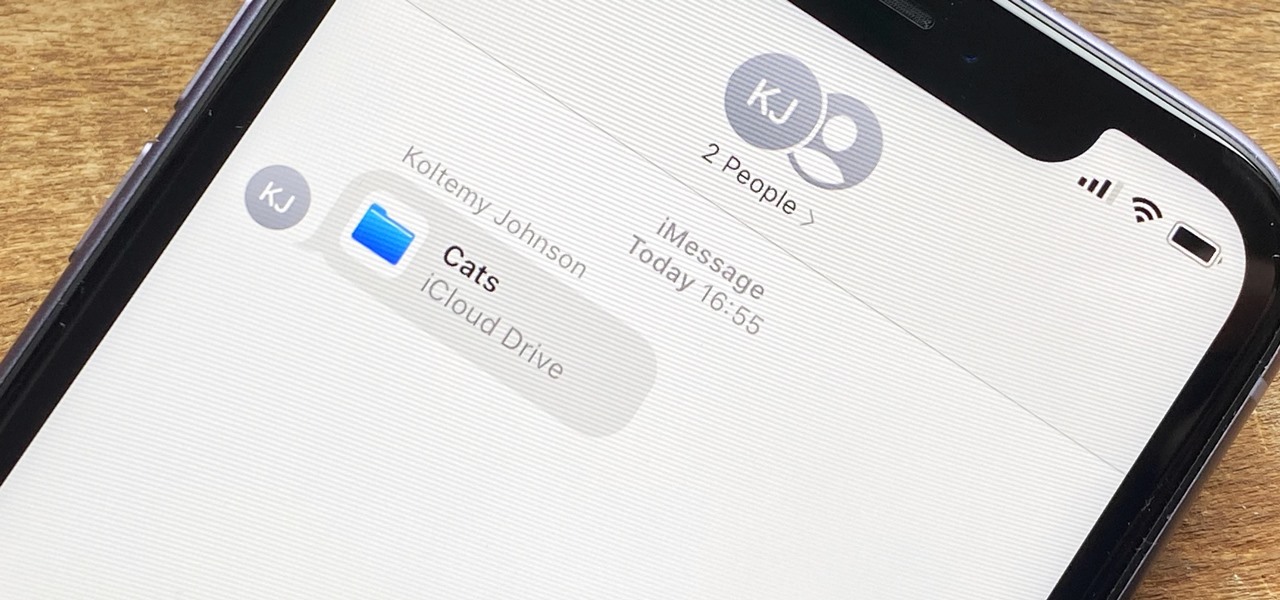
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

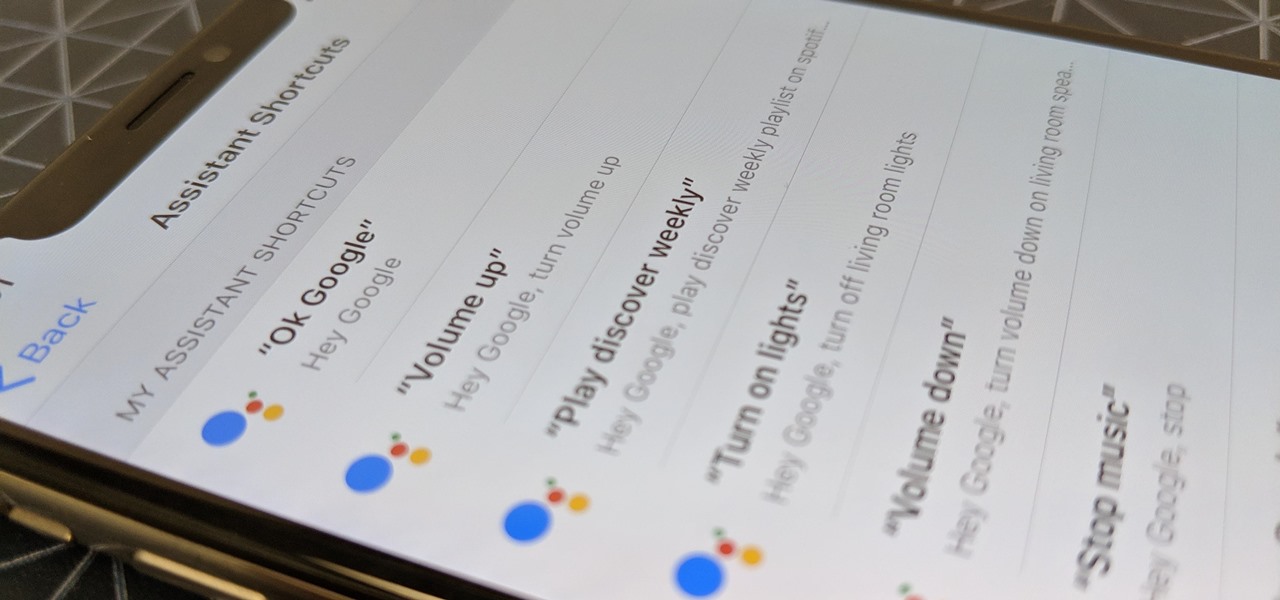
Using Siri to perform tasks on your Google Home device was never possible until Apple released Siri Shortcuts in iOS 12. Actually, it wasn't possible until Google added support for Siri Shortcuts for Google Assistant in Nov. 2018. No matter the timing, the important thing here is that you can use Siri to command Google Assistant which, in turn, can command Google Home.

Open TikTok, and you might find yourself spending hours watching video after video. While each video is usually pretty short, it's highly possible to binge-watch hundreds at a time. It's even more fun to create your own. But as a parent, you may not want your children falling into this same trap, and it's easy to limit how much time they spend watching TikTok videos on their iPhone.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.