
How To: Create Folders in Your Gmail Account
Folders help you to organize your mail in your Gmail account. In this tutorial, we are going to learn how to create these folders.


Folders help you to organize your mail in your Gmail account. In this tutorial, we are going to learn how to create these folders.

Gmail is a free, advertising-supported email service provided by Google. Users may access Gmail as secure webmail, as well as via POP3 or IMAP4 protocols. Gmail initially started as an invitation-only beta release on April 1, 2004 and it became available to the general public on February 7, 2007, though still in beta status at that time. The service was upgraded from beta status on July 7, 2009, along with the rest of the Google Apps suite.
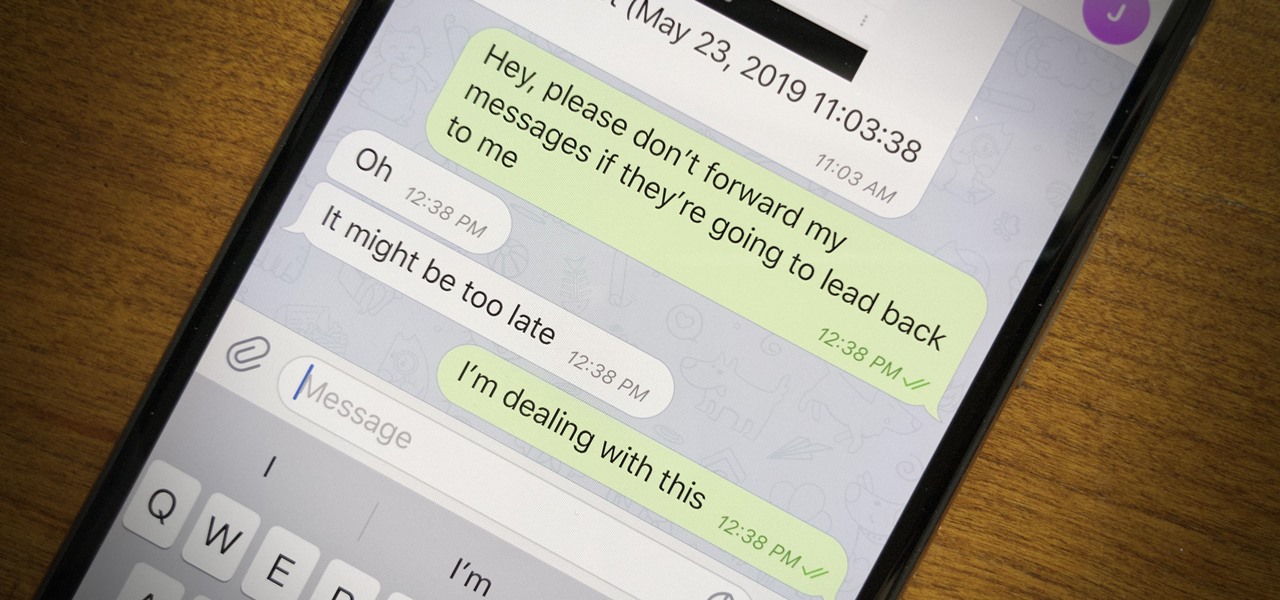
Forwarding messages is a helpful Telegram feature that makes it easy to share funny and entertaining content with other contacts. However, for the privacy-centric, forwarding poses an issue, as messages of yours that are delivered elsewhere carry a tag back to your account. Luckily, you can make your messages anonymous, so anyone receiving messages of yours that are forwarded won't be able to see you originally sent the message.

Attention all Redditors: Between June 14 and June 18, Reddit experienced a data breach. The popular website claims it discovered the breach on June 19 and has since made the necessary moves to contain and eliminate the threat. Unfortunately, there isn't much they can do about the data was that accessed and stolen — your user data.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.
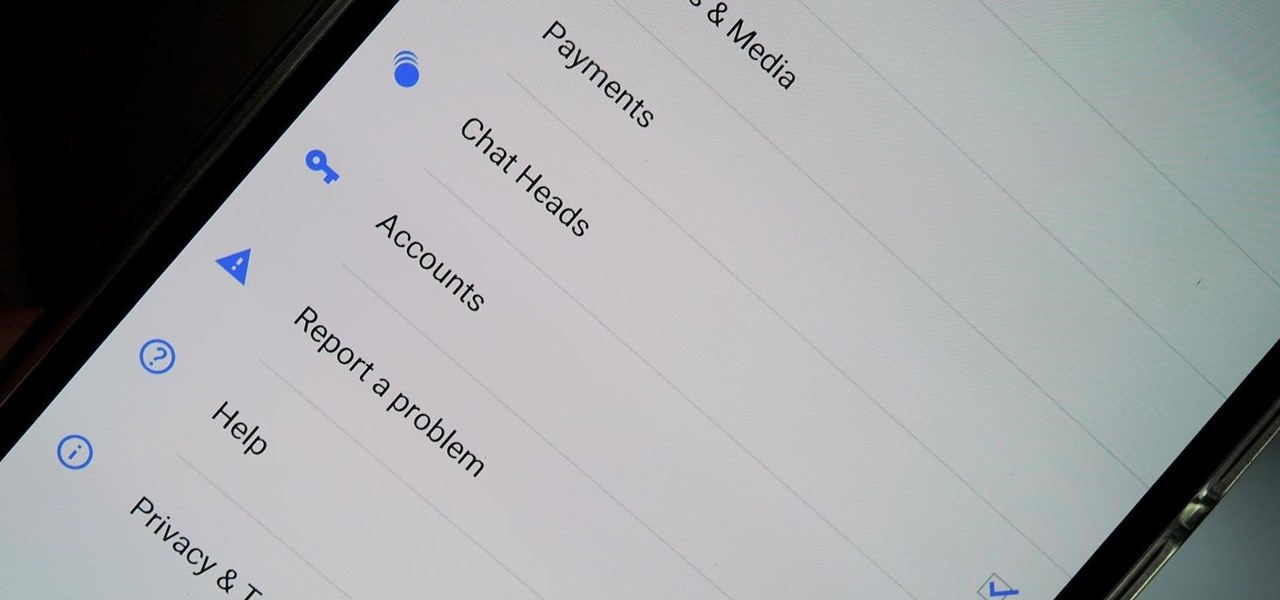
Earlier this week we showed you how to use multiple accounts on Instagram, and now Facebook is rolling out a similar feature for its Messenger app, as well as a few other features.
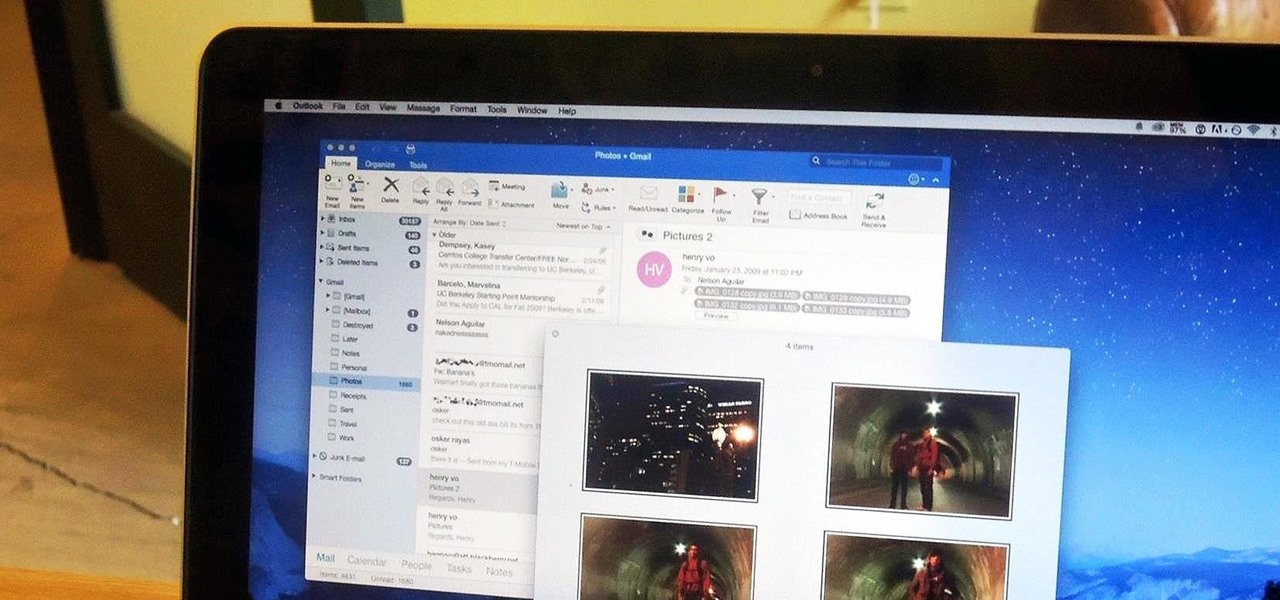
After my hard drive crashed recently, I lost everything. Old college essays, half-written stories, short films, and most importantly, all of the photos that I had saved from the past five years... all gone.

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.
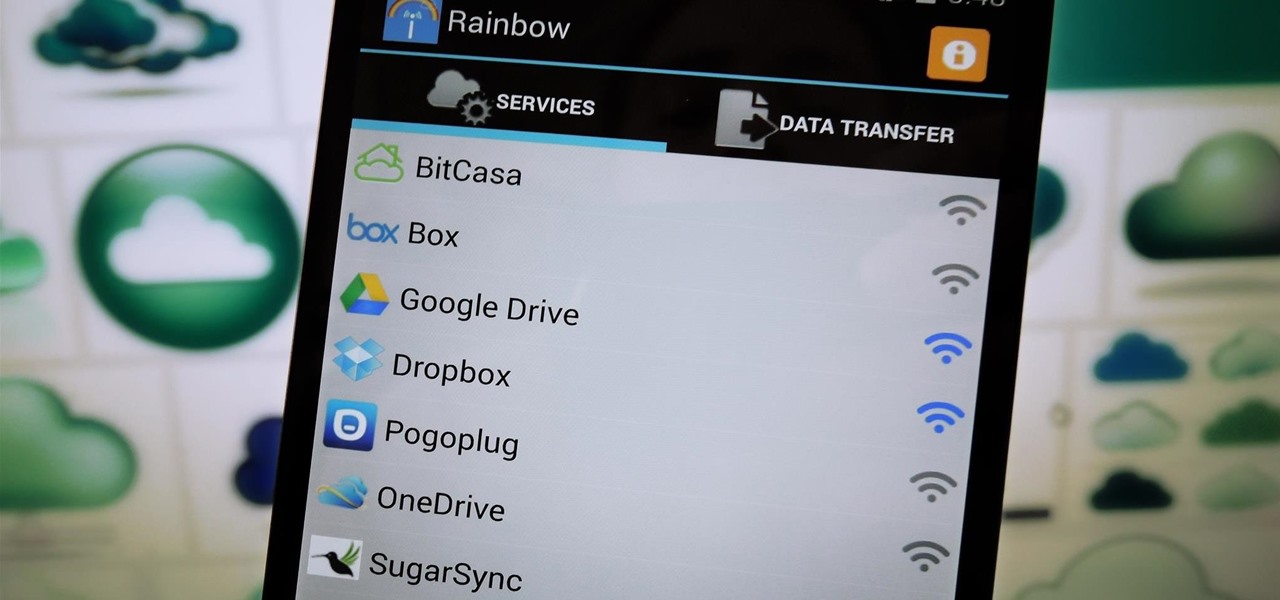
With limited storage options available on the Nexus 5, cloud storage can definitely come in handy. But sometimes, with the seemingly endless options of cloud services for us to choose from, our online data can get a bit disorganized.

The majority of our documents and music are digital, which is great for convenience, but it presents a problem for those with a lot of stuff—where do you store it all? There are tons of sites that offer cloud storage, like Dropbox, SkyDrive, and even Flickr, but most of them have limits unless you want to pay, and no way to connect them all.

There's a feature hiding in your iPhone's Mail app you may have missed but should definitely know about. It gives you quick access to something you'd typically have to dig around in folders to find.

While Touch ID has been a part of the iPhone's legacy since 2013, Apple waited until 2016 to add biometrics to its MacBook lineup, and it's not as impressive. An iPhone with Touch ID can register up to five fingerprints, but Macs can only register a maximum of three per account. If that seems unfair, there's an easy trick to doubling that number, meaning six of your fingerprints could unlock your laptop!

With iOS 12, Apple is offering users more options than ever to create, store, and manage their saved passwords. Not only can iOS 12 make you new passwords via the AutoFill feature, you can quickly and efficiently access your entire iCloud Keychain using Siri. Why go hunting for the passwords yourself when you can ask your iOS assistant to find them for you?

Converting files from one format to another can be a pain. Sometimes you have to download software that you'll only end up using once. Other times you have to use a shady third-party conversion site that's riddled with ads. Not to mention that after a while, unless you're extremely organized, your converted files will be scattered all across your hard drive.
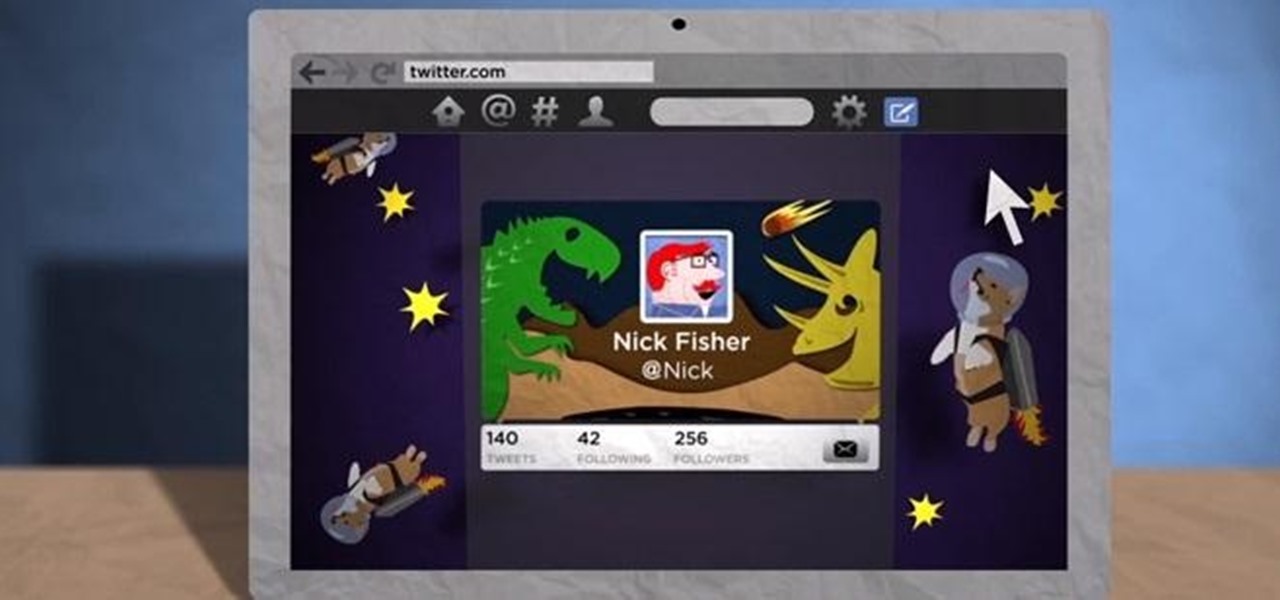
This goes out to all of the Tweeters out there looking to get a little more creative with their Twitter accounts. My page has always been extremely basic, because I just never bothered to pretty it up. I just had one of the stock backgrounds and the good ole Sacramento Kings logo for my profile pic. So, if you want to add your own cool photos and backgrounds to your account, the folks over at Twitter made this funny cartoon video just for you. It's not the most complicated of tasks, and every...

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.
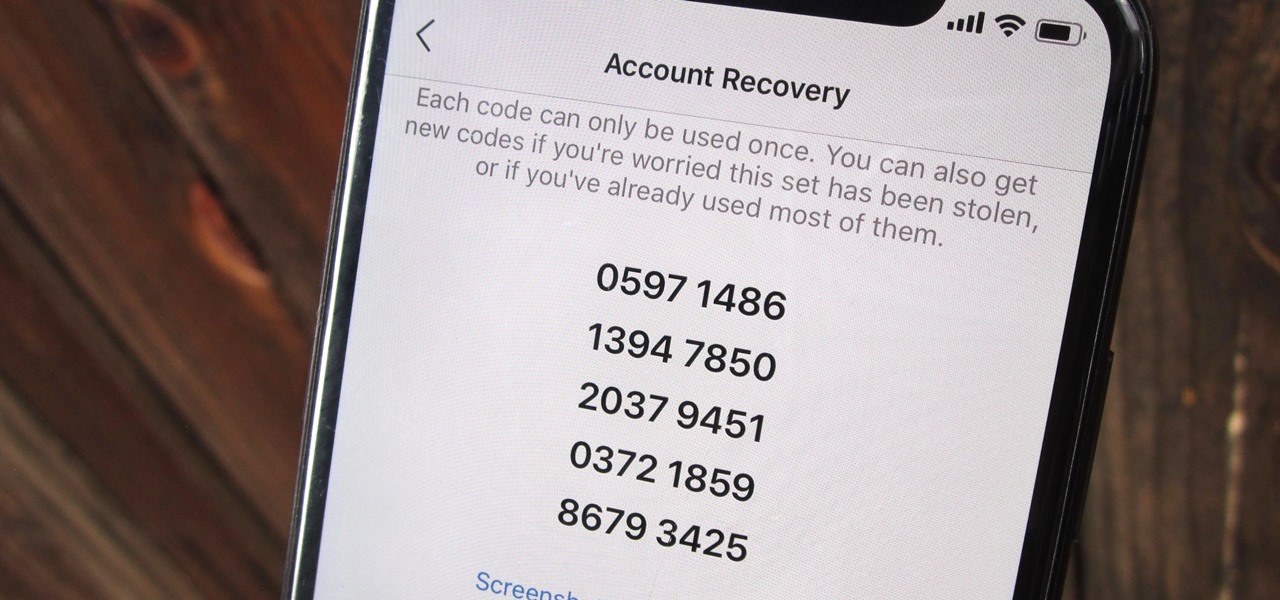
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.
Feelings can get hurt on Twitter as fast as an update. Everything is fine and dandy because two people are mutually following each other, then out of nowhere, one person has unfollowed the other out for seemingly no reason. Twitter doesn't notify users when someone has unfollowed them, so there are millions of people out there who get used for their follow! Well, now you can find out who unfollows you on Twitter with these mobile apps.
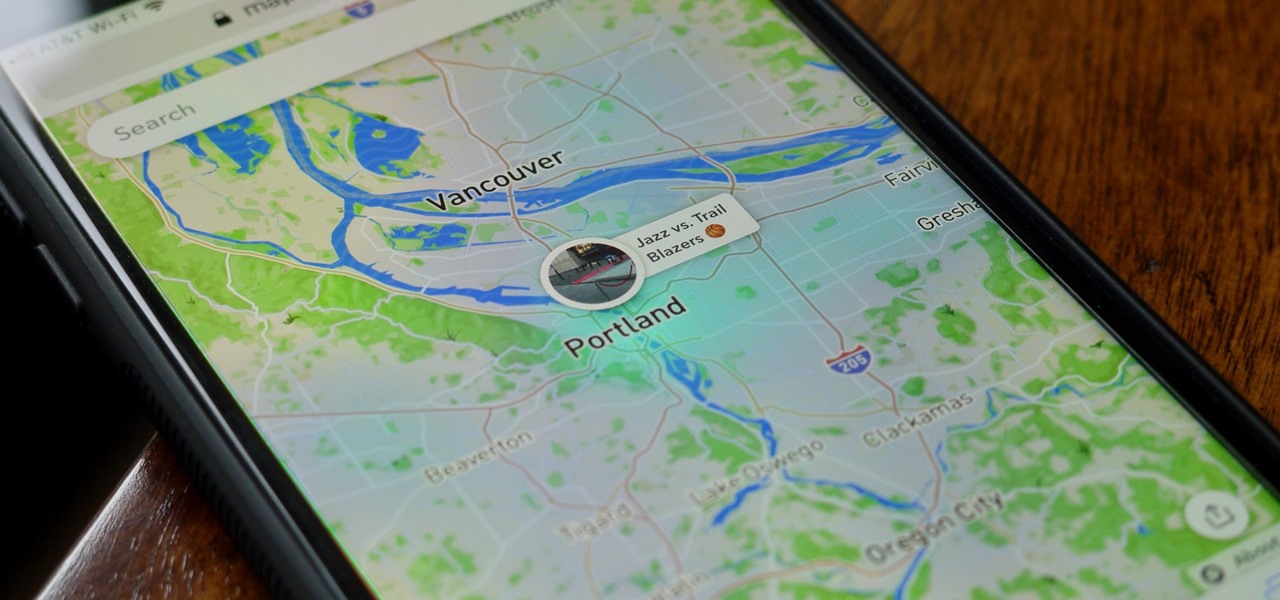
While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.
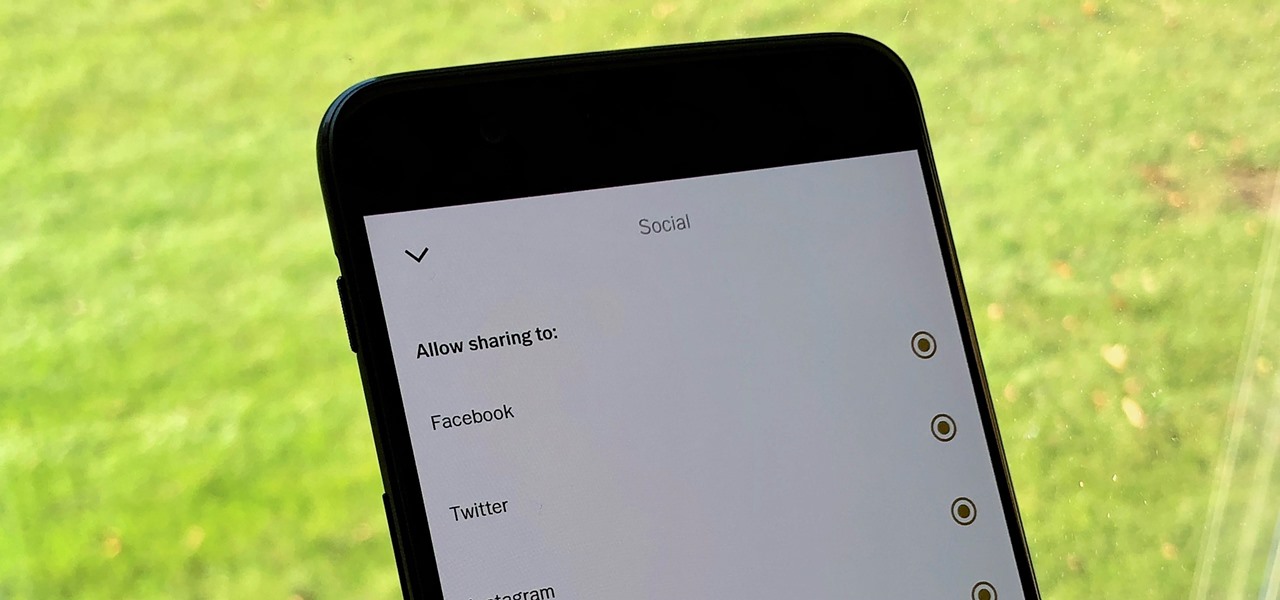
In this day and age, publishing content to one social media account just doesn't cut it. VSCO, Facebook, Twitter, Instagram ... you need to be active on all. And if you prefer editing and posting all of your photos on VSCO, you need a way to share those images with your other accounts.

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

We're glued to the news now more than ever, but our "free press" isn't necessarily free of charge. Cable news outlets like CNN and MSNBC are locked behind expensive cable TV packages and cord-cutting streaming subscriptions such as Sling TV and Hulu + Live TV. Luckily, there are plenty of alternatives to get your TV news fix, free of any payment, account, or commitment.

proxyFinderEnterprise is a tools for find proxylist . in this topic you learn how to use this tools for find a proxy list .

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

You must have read news about hackers dumping the data online, recent one was Ashely Madison. It's only the big companies' data, which gets noticed once it is out. There are many other small leaks which don't even get a mention. So this article is the first one of my series which will help you to find hacked accounts. Some of you must already know about this, but this post is intended for the new learners. This also serves as an example of my learning how a good service can be used in other w...

This is a tutorial I made in order to help people have a little more control over their pc and a little more options to change settings.

While you may suck at Instagram, it's likely that you manage multiple Instagram accounts, whether strictly for personal use or for managing blog and business pages.
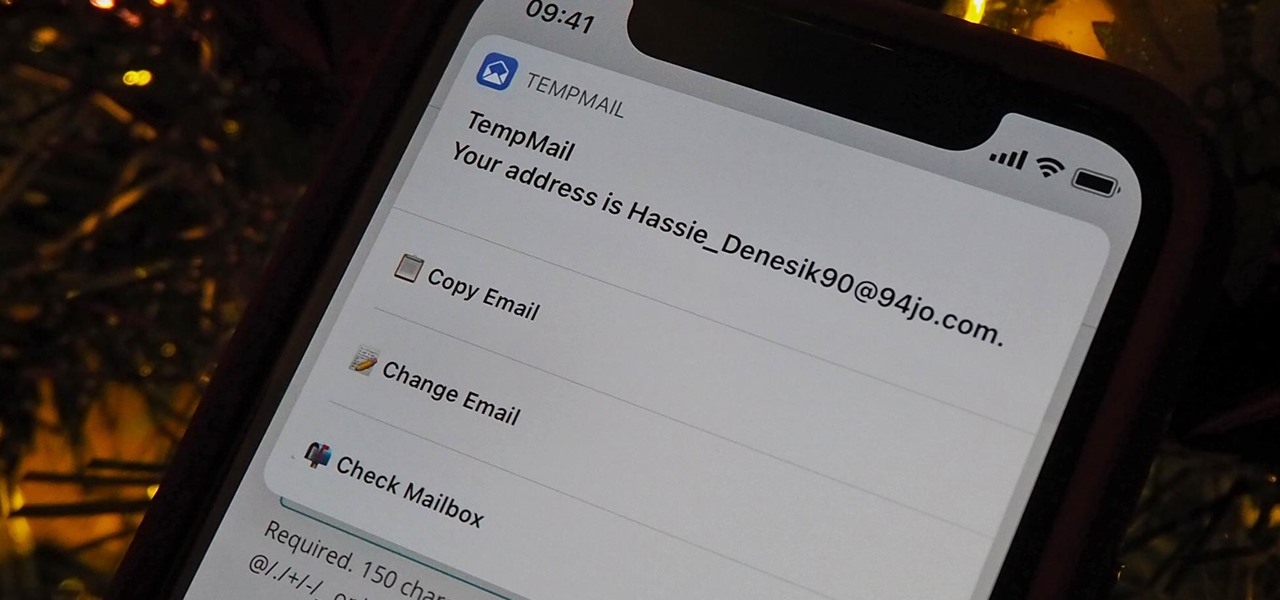
A temporary email can go a long way. Using your actual email to sign up for a mailing list to receive 10% off a purchase doesn't make sense if you don't use the website much. It means you'll have to deal with spam emails from then on, which is why an anonymous email is perfect not to have to deal with all that trouble. And that's where the TempMail shortcut for your iPhone comes in handy.
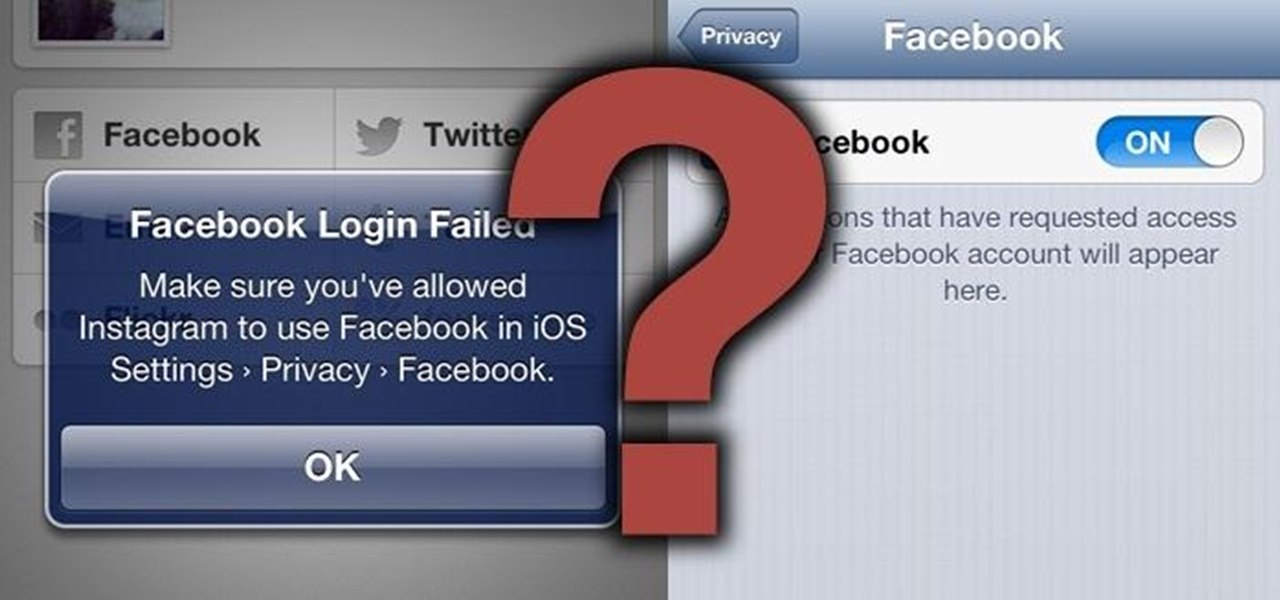
I recently ran into a problem connecting my Instagram app on my iPhone 5 to Facebook, and neither Instagram's or Facebook's help pages were as helpful as they claim to be.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.
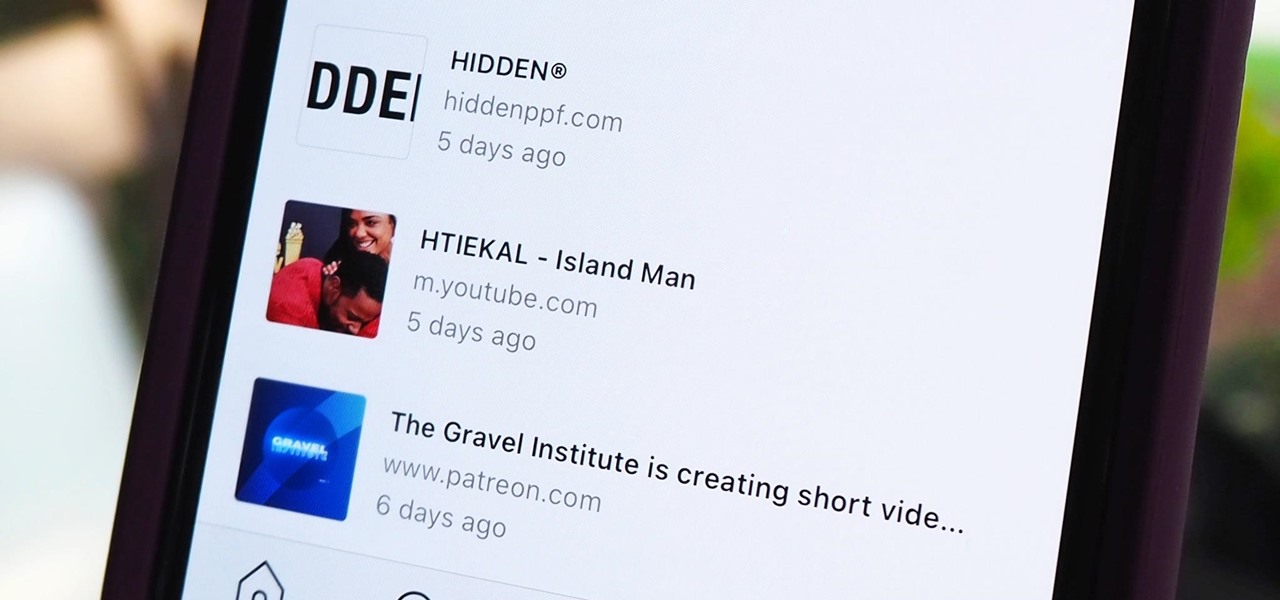
Instagram isn't as link-friendly as other social media platforms like Twitter and Facebook. Still, when you do find and open a link, whether it's for a petition or a product, you may want to find it again later. That's why Instagram keeps track of every link you've ever opened. That way, if you ever need to revisit a webpage, you don't have to find the original post or account from last time.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Hey, all you Instagram lovers, haters, or people who have no choice but to submissively bow down to the social app giant for other reasons, you've come to the right place. Today, I'm going to walk you through a very simple marketing trick to start boosting traffic to your IG account.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.
If there's any lingering uncertainty as to the mainstream viability of augmented reality, a list of the top mobile apps and games of 2019 serves to dispell those doubts.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.