Have a lock on your bike or shed but you have lost the key? Watch this hacking how-to video and learn the art of picking a lock using a common kitchen utensil. Yes all you need to crack open a lock is a fork for your kitchen drawer. Follow along and see how easy it is to pick any lock with a fork. Open a lock using a fork.

I'm sure everyone has heard about Google's changing privacy policy on March 1. It's scattered everywhere, with notification bubbles on Google Search, YouTube, and the rest of their products. Click here to see the new privacy policy that will take effect on March 1, 2012.

If you know anything about search engine optimization and online marketing then you know that having as many links going into your site from good sources is very important. And if you’re not really experienced at building links or SEO in general then you might not know the best way to get good links for your site. So please read on and I’ll present to you what I feel is the best way to get good quality links for your site.

We had a blast during last week's social engineering calls. One of our attending social engineers was so clever that she convinced several people on Craigslist that lost items were hers, even if it seemed she couldn't be trusted. But females are better social engineers, naturally. Some say that females have a special knack for manipulating men, but I think that's preposterous. I can't see why that would be true in a million years (note my sarcasm).

Mash-up Activity Directions: Pick three songs and grab 7 phrases or lines from each song, and then make a poem.

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

Here's another Null Byte on hacking our Skyrim game saves. Some of the rarer items in Skyrim are really fun to play with. However, seeing as they are rare, you will probably not see all of the best weapons in the game. Null Byte doesn't take too kindly to games that don't give us the rarest items when we please. Let's beat this game into submission by hacking our game save files via hex editing.

ZUGZWANG n pl. -S a situation in chess that forces a disadvantageous move 81 points (31 points without the bingo)

+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...

If you’re unfamiliar with League of Legends, you’re either not into PC gaming or you haven’t spent much time on the internet. Riot Games officially released League almost two years ago, and since then it’s become a huge hit. In fact, the Santa Monica based company recently announced that the DOTA inspired game has 15 million registered users, 4 million unique logins each month, and 500,000 people playing the game at any given moment.

The lack of a search function within Google+ is driving me crazy. It takes me way too much time to find the posts I want to save and refer back to, and it's counter-productive for Google to launch their social networking product without an integrated search.

Most indie game developers will never see a million dollars in their bank accounts, and I certainly doubt that Eul, the anonymous developer responsible for the original version of Defense of the Ancients (DotA), expected to. But now even the fans can earn a little green. Some lucky and talented DotA players are about to win $1,000,000 for playing the unreleased sequel to the free unsupported Warcraft III mod from 2003.

You've been on Google+ for a few weeks now. You're loving it. You're exchanging thoughtful posts, pictures with your friends, meeting new people and following lots of interesting, intelligent people. There's just one problem.

One of the coolest things about Twitter is the fact that you can get direct access to some of your favorite celebrities, and have one-on-one conversations with them in less than 140 characters. With Google+, you can have the same advantage, but you don't need to feel constricted by the 140 character limit. Although Google+ has been weeding out fake accounts, they do not currently have a system for celebrities to verify whether their accounts are legitimate or not.

World of Warcraft has been on top of the world for seven years. No other MMO has come close to challenging its dominance of the genre, and it has generated billions of dollars for Blizzard. They have spent a lot of money adding more and more content, to the extent where the full game with all the expansion packs takes up 65 GB of hard drive space. It is a beautiful game; well balanced, and a milestone in the history of the medium.

Netflix may be killing its competitors, but they're losing fans thanks to their reputation for rolling out interface updates without user knowledge or consent. PlayStation 3 owners were upset at the Netflix interface change earlier this year, and now nearly 5,000 diehard Netflixers are irate at the website's new look for its Watch Instantly section.

By Huffingtonpost Meg Whitman New Spanish- Language AD: I stood up against The Arizona Law

Zynga games has released their ZLotto feature that you can use to get exclusive prizes for FarmVille, Mafia Wars, YoVille, PetVille, and FrontierVille!

This is probably the funniest video I've seen this year, they really don't hold anything back. Things you'll see in the video, based on real events:

Not only am I ecstatic that my favorite team moved on to the semifinals, but I'm also so excited to see a team that's not Brazil in the semis! Just like supporting the Yankees, rooting for Brazil was like rooting for gravity. No longer.

You might know the feeling: the sinking stomach that informs you something terrible has happened. You click on your trash bin. Nothing is there. Your hard drive has been wiped clean.

A flashlight is one of those things you rarely need, but hardly ever have when you do. The normal-sized ones are unwieldy to carry around, and the small ones that you keep in a purse or car are easy to lose.

Sending and receiving email on the go is made easy with the Apple's "Mail" app on the iPhone. However, up until the release of iOS 5, plain text was the only option for sending emails (even though well-formatted messages could still be received). The information below, coupled with unlocking the emoji keyboard will make you an unstoppable force of communicating accurately.
Just a few days after a senior US counter-terrorism expert warned that US drone strikes were turning Yemen into the “Arabian equivalent of Waziristan”, US drone strikes yesterday aped the tactic of ‘follow up’ strikes used by the US in Pakistan.

You may have noticed an unusual email from Twitter over the last couple of days that showed recent stories and tweets from those you follow. This is a new initiative from Twitter that gives you "the best of Twitter in your inbox". It's basically just a weekly summary of the most recent and relevant stories and tweets from your connections.

I've been having this idea to build a redstone-version of rock-paper-scissors but never got around to do it. Building big redstone-contraptions on survival-servers isn't easy and single-player creative mode is a bit silly if you want to build a 2-player redstone-game. :)

In this article, I'll show you how to prank your friends on April Fool's Day with the very popular Google Voice, a computer to land/mobile calling feature. Basically, Google allows you to play whatever you like through the microphone port on your computer, and play it right through to your victim's phone. Whether it's Rick Astley ("Never Gonna Give You Up") or a text-to-speech application, general hilarity always follows.
The United States asked Russia to send Iran a message that the upcoming round of nuclear talks is its last chance to avoid a military confrontation this year, Russian newspaper Kommersant reported Wednesday according to a diplomatic source.

Hello, life forms and inanimate objects the world over. This week's competition is the Hobo Image Macro challenge, and we want to see more entries! Don't be intimidated by the hobo's dull, yet threatening stare—it's easy to do! Just to prove it, here are ten pieces of Hobo advice I prepared earlier in the kitchen (I live in a studio; it's all the same).
Swim Yes/ter/day /the/ tri/pod/ went/ to/ go/ swim A

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

Do you need proxy access, but cannot have it for some reason? The most common perpetrator behind the issue is the network you're trying to access the pages from. Some networks will block websites, then go as far as filtering out all of the web queries for terms like "proxy" because it can get around their filter. Quick web proxies can be used for tons of other things, though.

Flash memory can be a tad unpredictable at times. I have had 4 flash drives die out on me over the last few years, and they usually die without warning. When a flash memory based device dies, the data is likely impossible to recover. Adversely on an HDD, or Hard Drive Disk, even if the disk dies out, someone will probably be able to fix it and get it back to working order—at least long enough for you to back up your data. Hard drives are a bit more forgiving. As you can guess, due to the unpr...

As many of you may have noticed, nearly every Google product (i.e. Gmail, Google search, etc.) has gone through a bit of a makeover since the release of Google+. Big blocky buttons and enormous font sizes are apparently the thing of the future, and with a cool JavaScript hack, you can have a goofy YouTube, too! Now, I'm actually just being a bit facetious, the new YouTube is really the only thing that I like out of all of Google's recent redesigns. It looks pretty sleek.

The concept of Scrabble and Words with Friends is the same—play words, score points, win. But the games require different strategy in terms of letter placement, premium squares, tile point values and word choices. Here's the main differences between the two games.

APOLOGUE n pl. -S an allegory 61 points (11 points without the bingo)

This would make a fantastic illustrated Yumi-guide. According to Simply Recipes, apparently most blenders can be used with a standard mason jar (or wide-mouthed). If your standard blender container is dirty, occupied or lost, you may be able to swap in that old spaghetti sauce container. Pictures below.

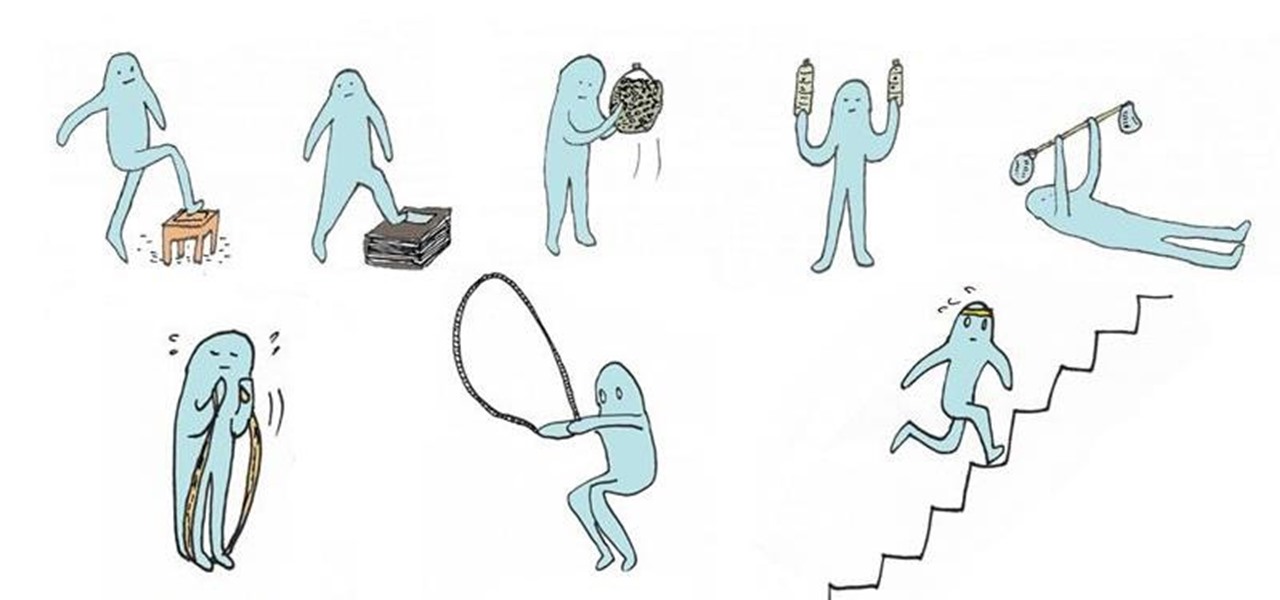
Work it without breaking the bank—with a couple of household items and a little ingenuity, you can transform your old junk into effective gym equipment for both cardiovascular workouts and strength training within the comforts of your own home.

Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.

Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites.