When the 6.1 version of iOS was released back in February, complaints of severe battery drainage for iPhone, iPad, and iPod touch users exploded onto every Apple-related forum on the Internet. Everyone was either losing a percentage every three or so minutes, or their battery only lasted half as long as it did before the update. Earlier this month, Apple released iOS version 6.1.3, to supposedly fix a recent exploit that allowed anyone to bypass the lock screen—but as it turns out, the update...

There's nothing worse than losing your phone—except losing your phone when the ringer is silent. If you're alone, it can be excruciatingly hard to find your lost device even if the ringer is on, considering most of us don't have landlines anymore. So, the next time you find yourself hunting for your phone, don't tear your house apart until you've tried some of these quick tips.
The Citrix Receiver is an app that allows you to securely access your desktop and business applications directly from your Droid Bionic smartphone. You will first need to make an account at the Citrix site, and from there you can decide what you want to have access to on your phone. On the Android app launcher, be sure to pick the Citrix Receiver app so that you can login with your Citrix account.
This video teaches you how to change your computer's account password using the DOS command prompt. The first step is to get to the command prompt, you can do this simply by clicking run in the start menu and typing "cmd." You next type "net user" which will show you all of the user accounts on the computer. Choose the one you would like to change the password for and type "net user (account name)." It will then ask you for a new password, you may type anything you like here keeping in mind t...

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

Getting new loot can be challenging in Fortnite Battle Royale. Whether you decide to pay for the Battle Pass or stick with the Free Pass, you still need to put in 50+ hours to unlock all the items. For those of us with Amazon Prime subscriptions, there's another way to unlock free items, and it won't cost you an extra dime.

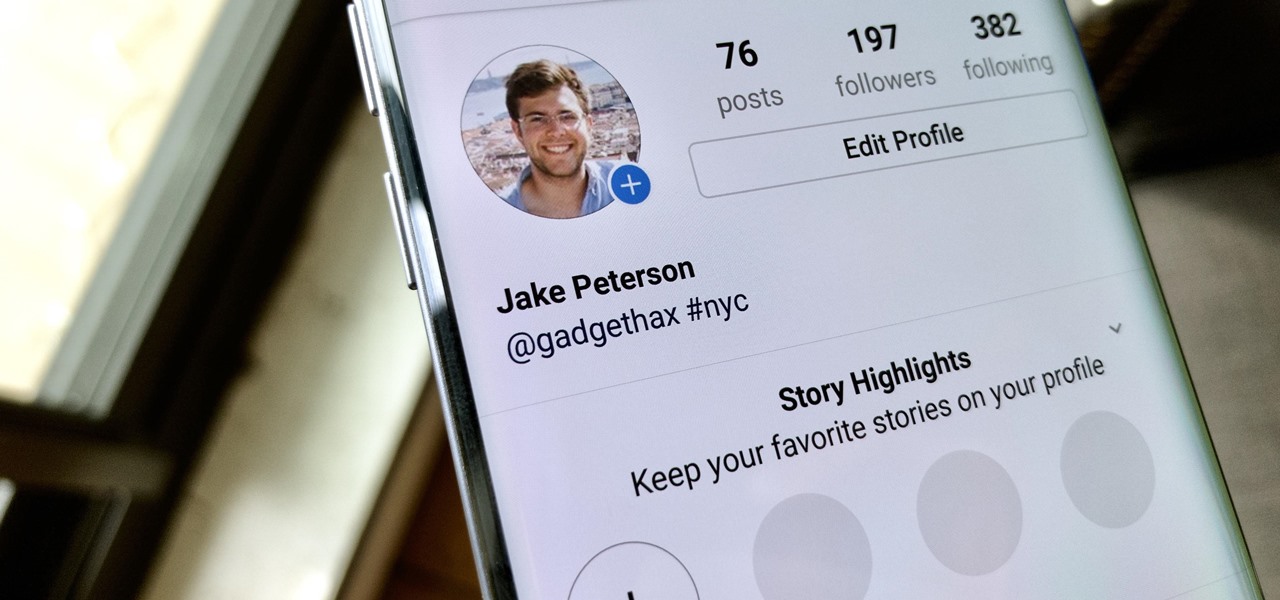
Your Instagram bio could always be used to link to other websites or profiles or just to show off your witty personality. Now, you also have the ability to use this section to tag other Instagram accounts as well as add tappable hashtags. Whether you want to link out to your best friend, company, or the latest trend in your city — if it has a profile name or tag, it can be in your bio.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

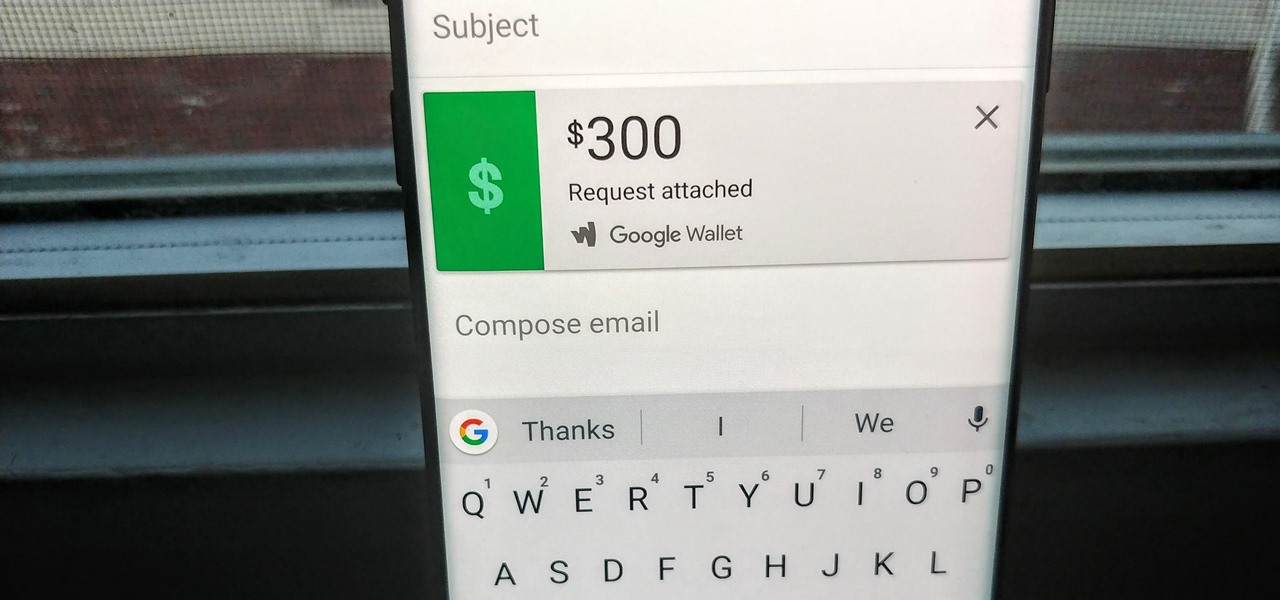
Since its debut in 2004, Gmail has become the go-to email service for the internet at large. Over 1.2 billion people use it, so Google has wisely continued to add features that address the needs and wants of its diverse user base. For US and UK users, one of these new features is the ability to transfer money.

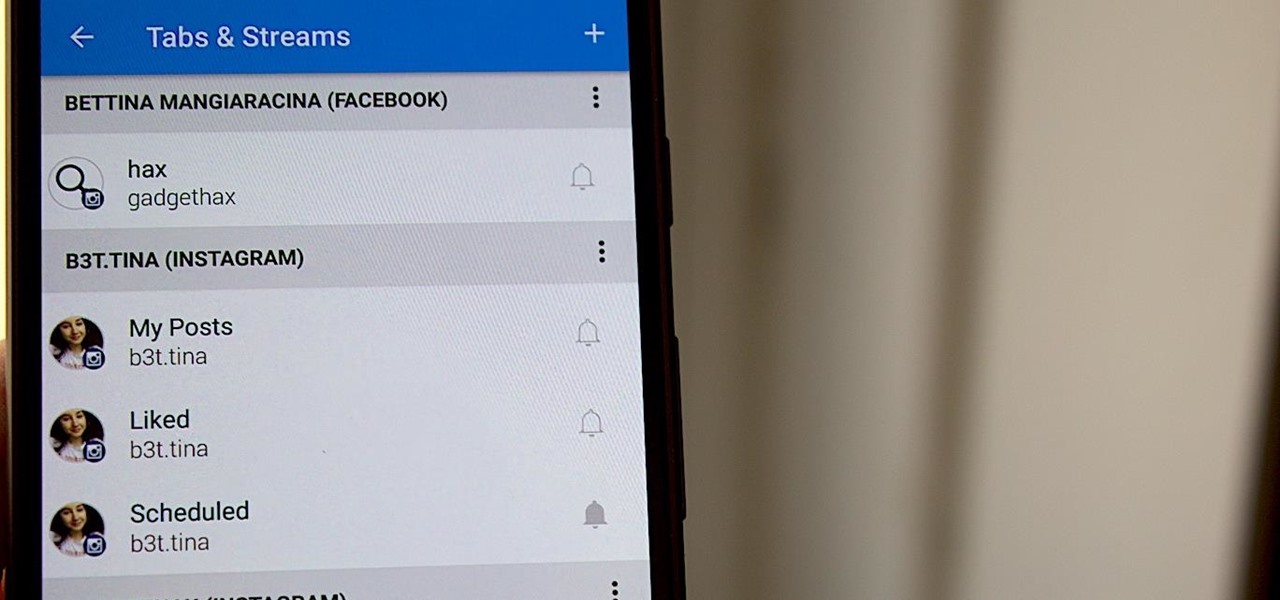
In this day and age, publishing content to one social media account just doesn't cut it. VSCO, Facebook, Twitter, Instagram ... you need to be active on all. And if you prefer editing and posting all of your photos on VSCO, you need a way to share those images with your other accounts.

Hashtags are one of the most important marketing tools available to you on Instagram. Although, it's hard to know which hashtags are working for you or not. You may think #fun is a good one to use but is it really? Okay, yeah, it's a popular one. But that doesn't mean it's the right one for you to use.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

These days, when you're setting up an Android device for the first time, you'll be prompted to add extra email accounts directly to the Gmail app. It's really simple, too—just sign in with your work or exchange account, then emails from those accounts will be mixed in with your personal account in the Gmail app's "All Inboxes" view.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

We've already shown you how to free up internal space on your iPhone, and now it's time to tackle another problematic storage issue—your iCloud account.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

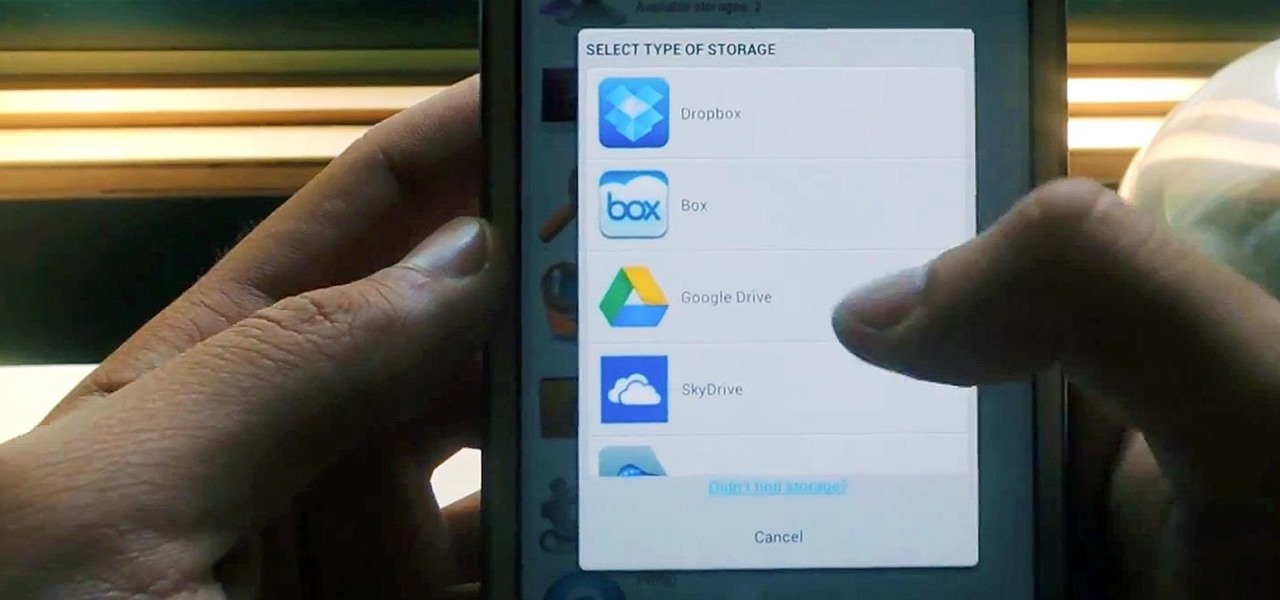
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...

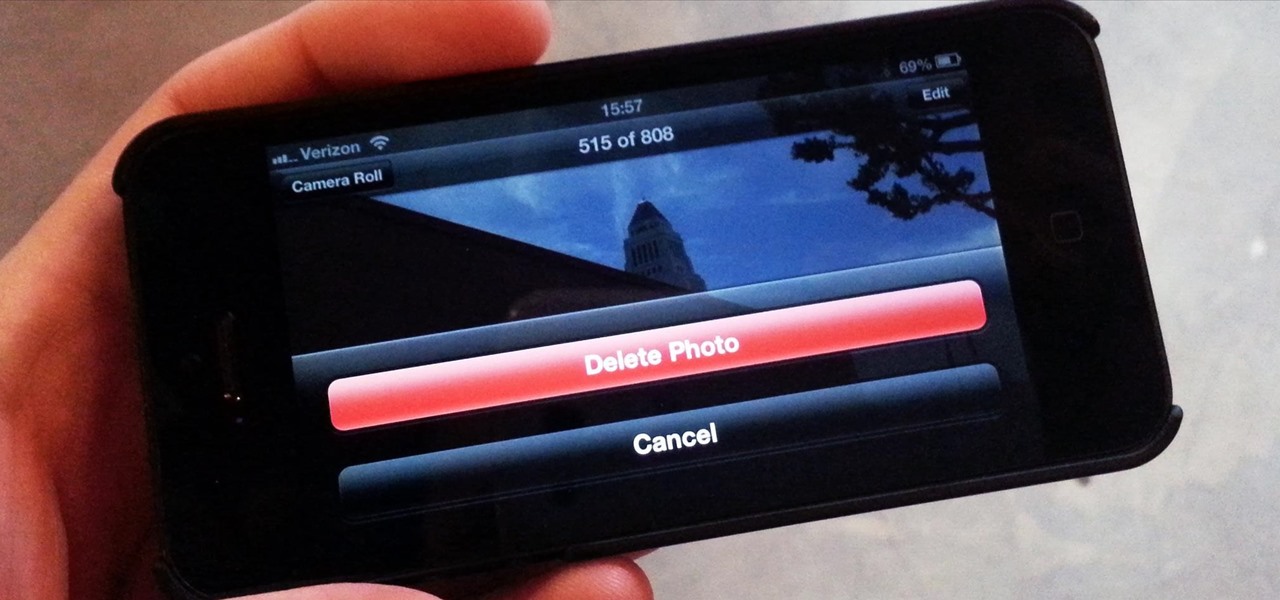
In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

This walkthrough will help your through the entire gameplay of Lost Planet 2 for the Xbox 360. Lost Planet 2 is the sequel to the third-person shooter Lost Planet: Extreme Conditions, and besides the Xbox 360, is also available for the PlayStation 3 and Windows. It takes place 10 years later, back on the planet E.D.N. III, which has more foliage compared to its previous white, frozen entity. To see how to defeat the game, watch this walkthrough, which provides you with all of the knowledge to...

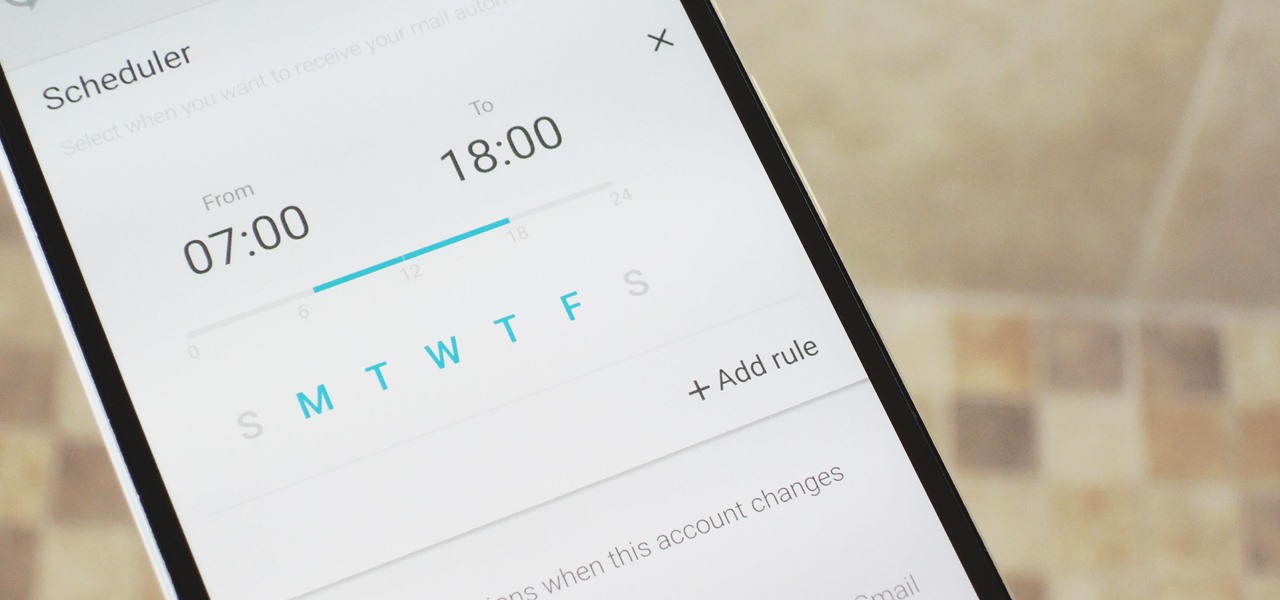
Check out this informative video tutorial from Apple on how to organize your Mail in Mac OS X's Mail. See how to sort messages with rules, create smart mailboxes, and comlpletely organize your mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

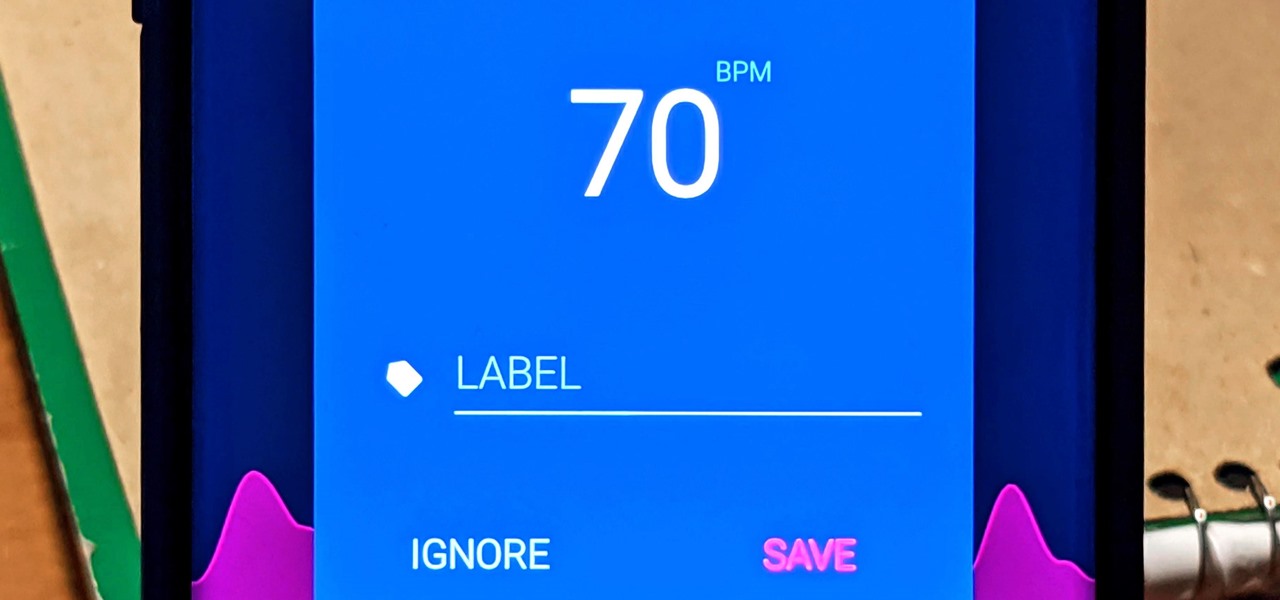
With the rise of smartwatches and wearables, you'd almost expect to need one to get a heart rate reading. While these devices can be helpful, not everyone has or wants to wear a gadget all the time to track their BPM. Luckily, when you combine Google Fit with a popular third-party heart rate measuring app, it will make things easy for you.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

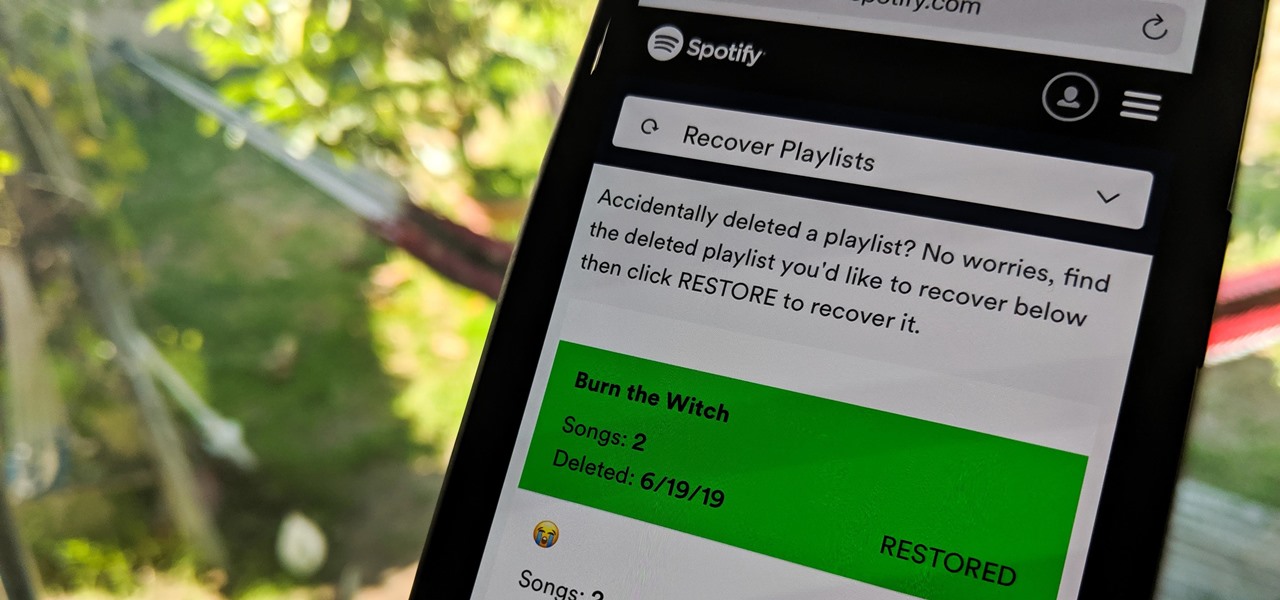
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.

Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

Instagram integrated Stories back in 2016, and it flew right by Snapchat as a whole, becoming a bigger success itself than the whole entire Snapchat app. Still, the constant bombardment of information can be tiring in Instagram, so much so that you may want to mediate what Stories are shown to you. Fortunately, there's a way to do just that — without unfollowing accounts or hashtags.

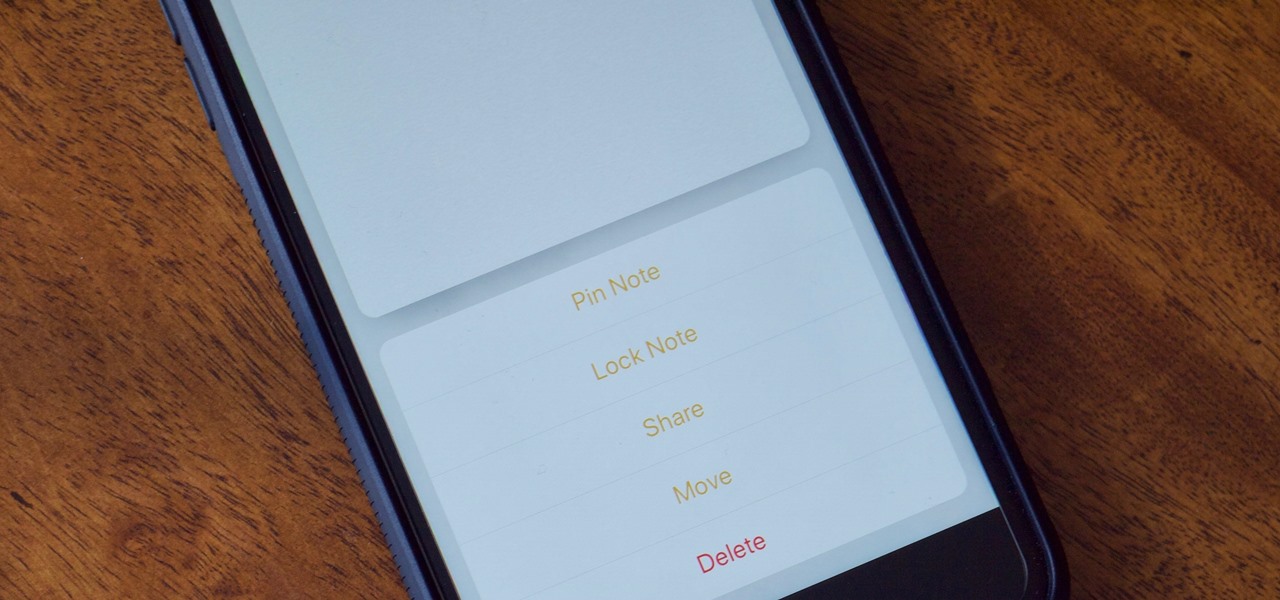
If the Notes app on your iPhone is anything like mine, it's a mess. Even with the addition of folders, adding note after note can really clutter things up. You need a way to quickly identify the notes that are most important, and that's where pinning comes in.

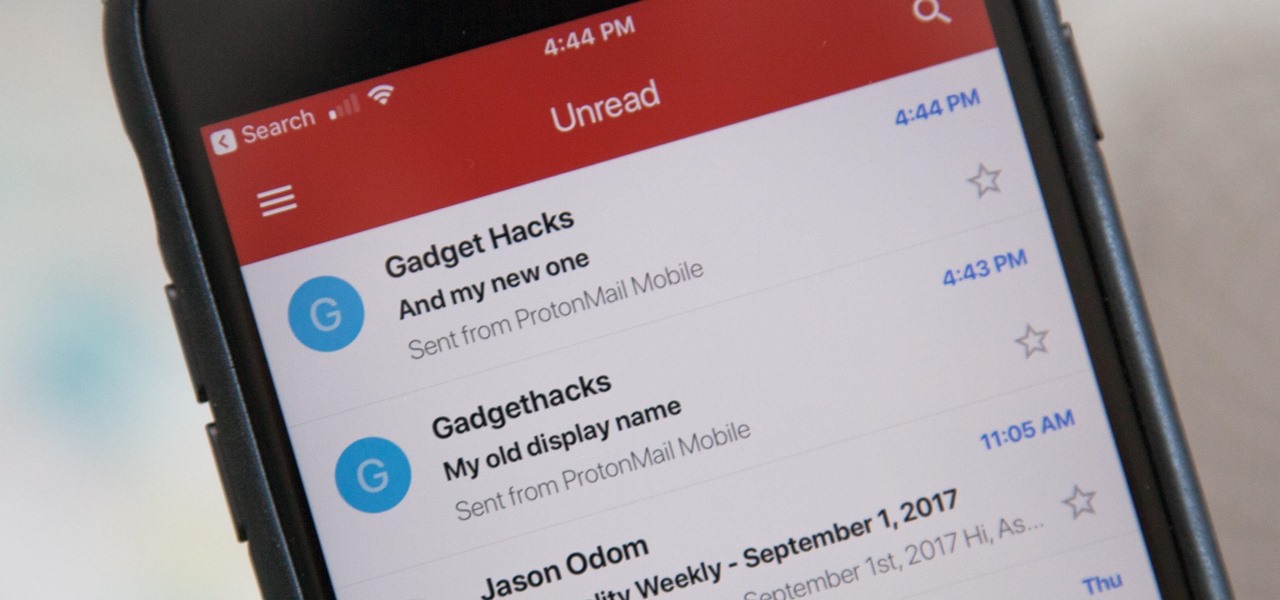
Your display name in ProtonMail is what email recipients will see when they first receive your message in ProtonMail, Gmail, or another email provider. You can choose this name when you first set up your ProtonMail account, but it can also be set up after the fact if you skipped that step.

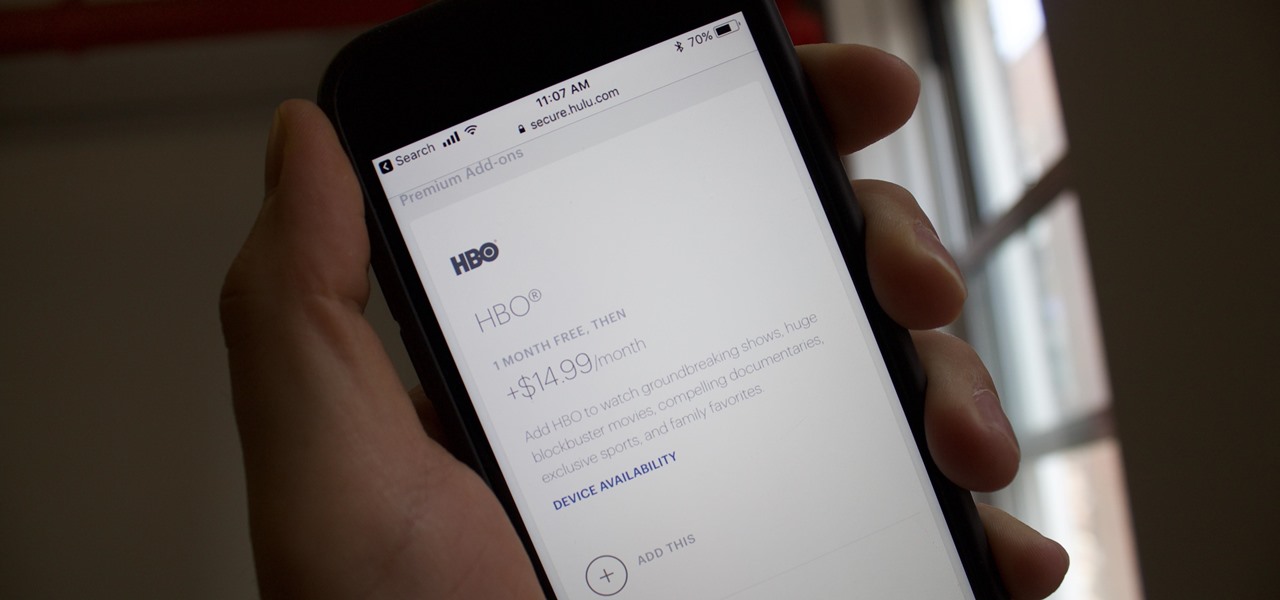
What's better than having access to Hulu's entire catalog on any device you wish? Having HBO's as well, obviously. Hulu recently began offering subscribers the option to either subscribe to HBO through their Hulu account, or to link a prior HBO subscription to their Hulu account. It's just one way to make binge-watching a little more convenient for you and your fellow Targaryens — the Starks can join, too.

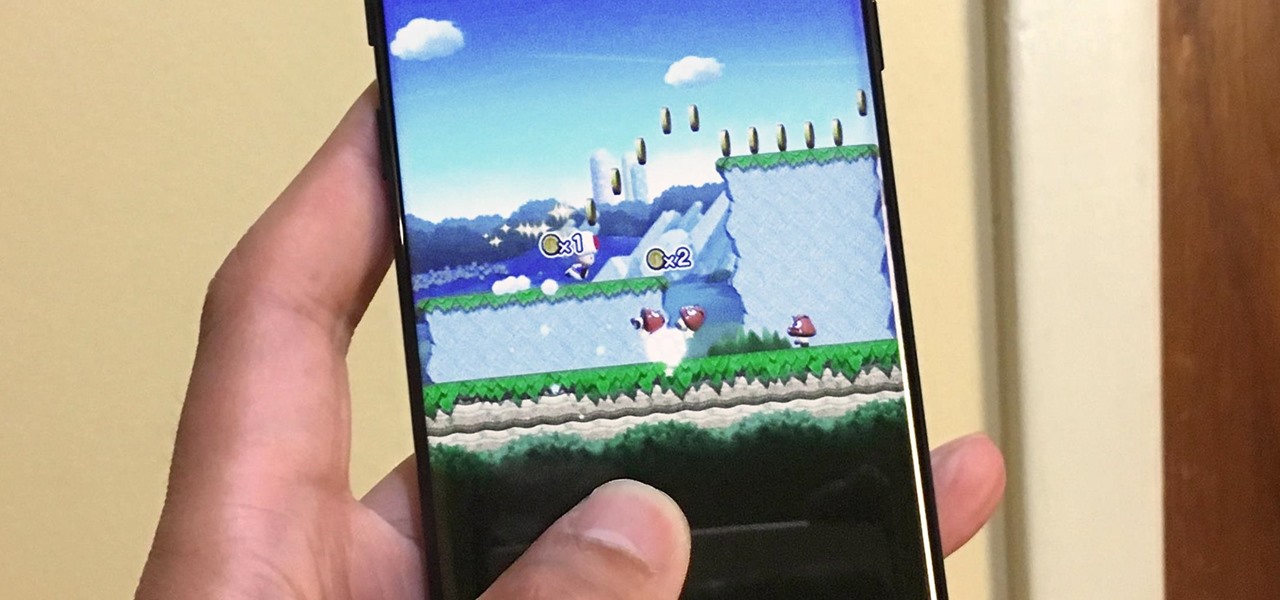
Though not quite as agile as the world famous plump plumber Mario, Toad, the lovable fungus, is still one of the most fun characters to use while playing Super Mario Run. Thankfully, he is also by far the easiest character to unlock in the game, requiring no special tasks to complete.

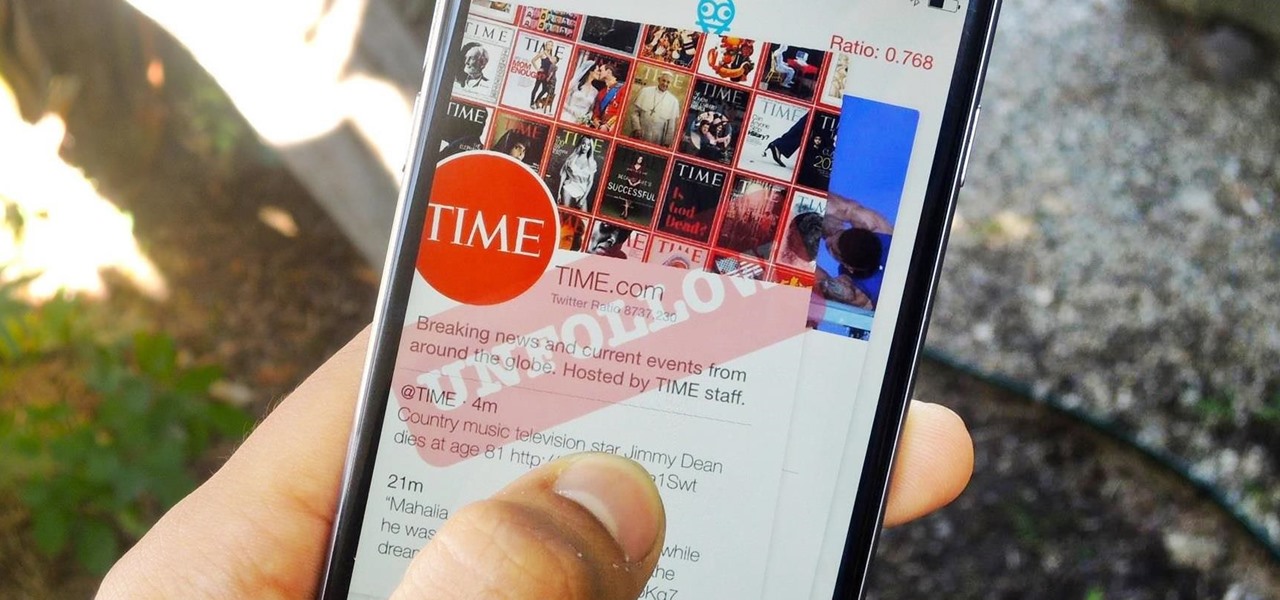
Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

Technology allows us to communicate with others like never before, providing us with the ability to stay connected with past and current coworkers, classmates from high school, and even relatives in far-away countries.
So, you wan't to become a Xbox Community Ambassador? Wan't to give support to other Xbox Customers and Earn loot doing it? Want to be different from a "normal" Xbox Customer? Want to share your knowledge to others who want it? Come on over here, friend! In this How-To, I will tell you how to become a Xbox Community Ambassador in the most correct way possible! In 3 Easy Steps! Here is the Link to the Website : http://ambassadors.xbox.com/