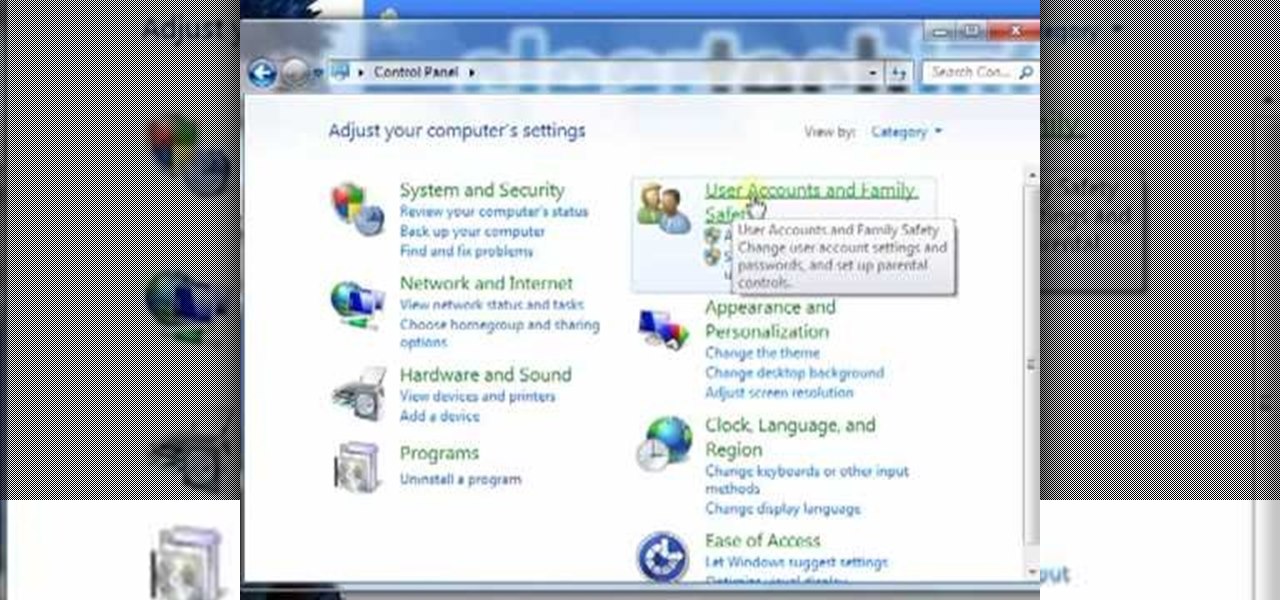
This video contains instructions about how to disable or enable the user accounts on Windows Vista. It is very simple; just go to control panel -> user accounts and safety -> user accounts. You can click the check box on or off to disable or enable the user accounts. This can also be done by using command line. Open run and type the following command:

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.
If you have two or more accounts logged into Instagram at any given time, you likely know how confusing it can get. You could like content, post pics, and share stories from the wrong account, as well as perform embarrassing searches that show up in the history of a shared work profile. Switching accounts is easy to forget once you open the app, so do it beforehand instead.

Admin accounts are given special privileges to change the system (like installing programs) that user accounts are not. This tutorial shows you a quick way to check using Windows 7's calendar, and also how to go through the Control Panel to find out if you're an Admin or general User on your computer.
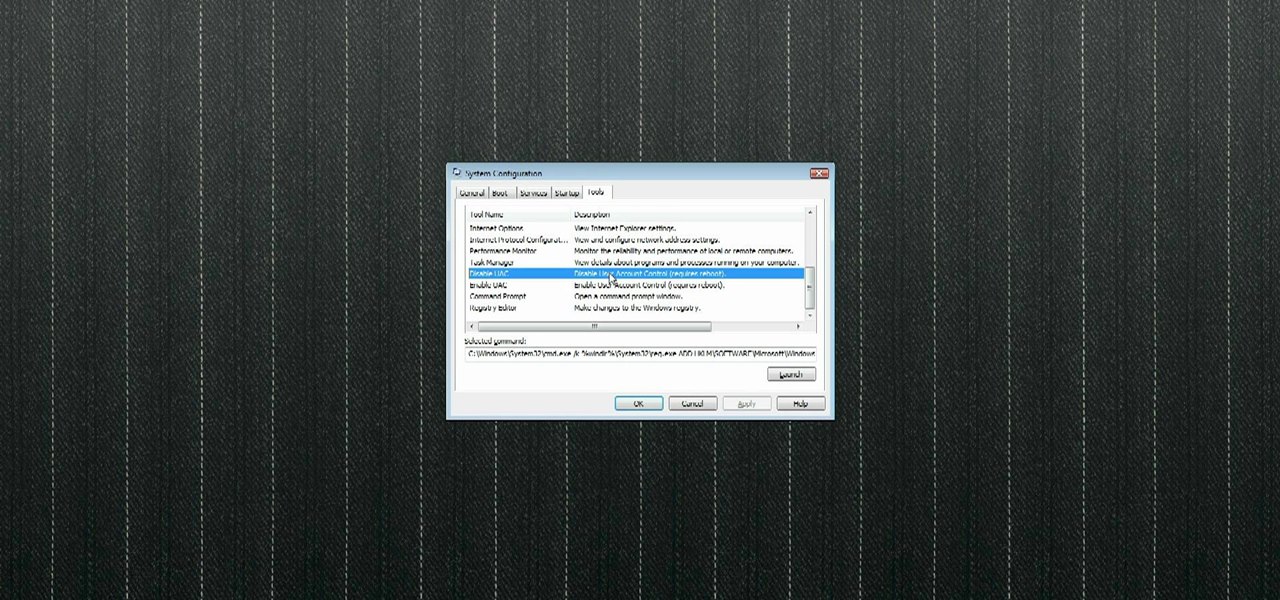
In this video tutorial, viewers learn how to disable the User Account Control in Windows Vista. Begin by clicking on the Start menu and select Control Panel. Then click on User Accounts and Family Safety. Now select "Add or remove user accounts". Then click on "Go to the main User Accounts page" under Additional things you can do. Now click on "Change User Account Control settings" and deselect the box. Finish by clicking OK and restart your computer. This video will benefit those viewers who...
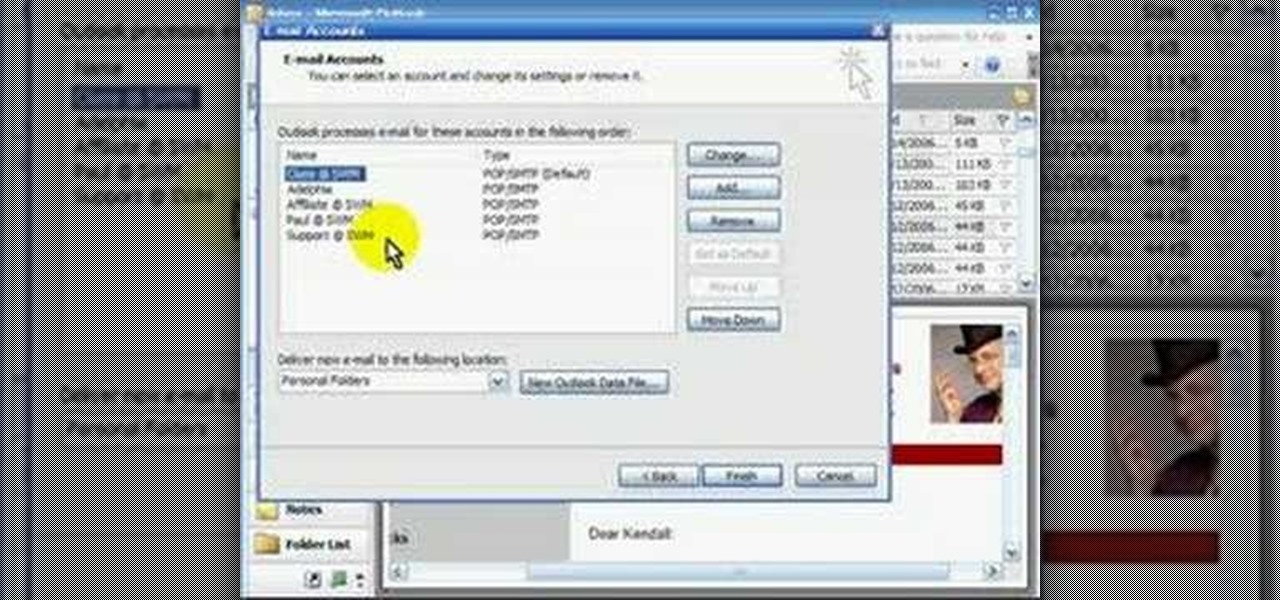
POP3 stands for Post Office Protocol, a way in which you receive mail on the internet, paralleling how mail is received in your mailbox. To set up your POP3 for Outlook, go to tools, click “view or change existing e-mail accounts’ and press next. You’ll be able to see a list of your current email accounts that you can change or remove. When you select an email and press change, you’ll be able to see the account in detail: the email address, the POP3 and SMTP server information, and th...

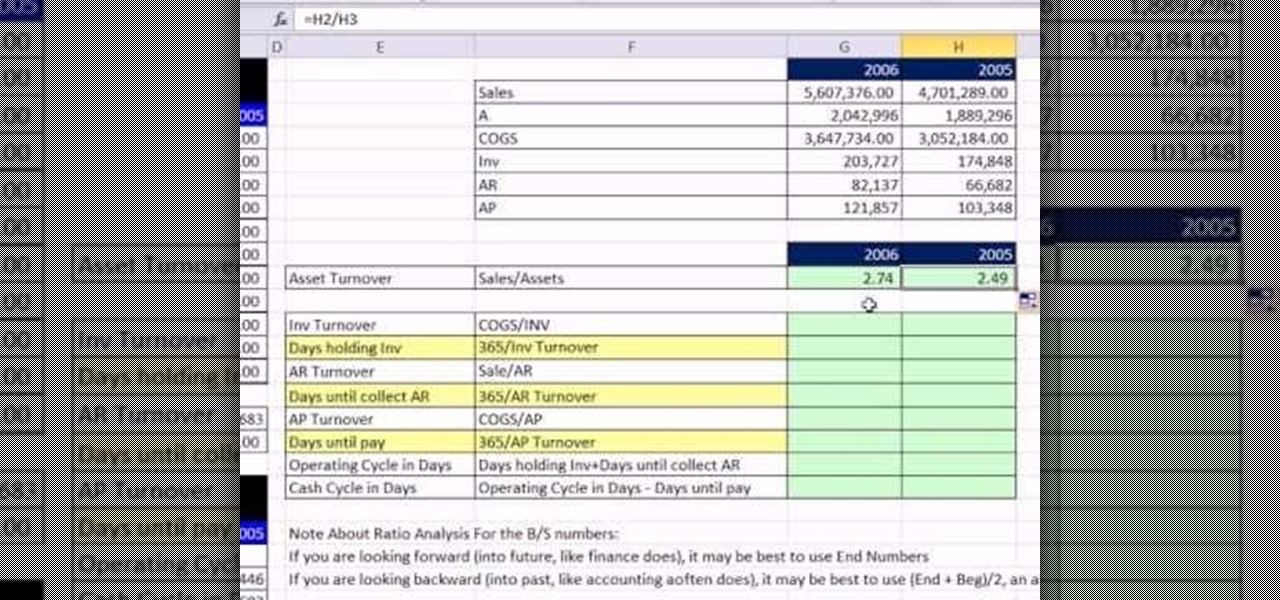
As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 11th installment in his "Excel Finance Class" series of free video lessons, you'll learn how to calculate asset turnover, capital intensity, inventory turnover, days to sell inventory, receivable turnover, days to collect accounts receivab...

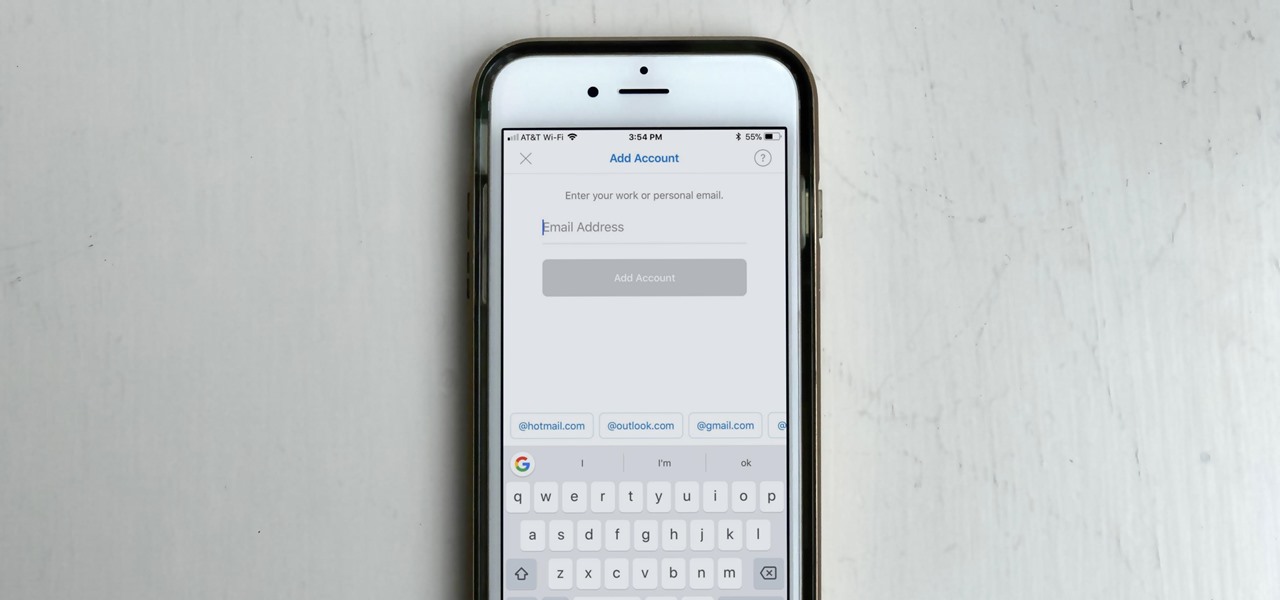
If you work with multiple email addresses, you need an app that can organize and declutter your day-to-day messages. Outlook is a great choice, but if you only have one account attached, it somewhat defeats the purpose. Lucky for you, adding additional email accounts is both quick and simple.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

Horrible at saving money? Creating a savings account to put aside and accumulate money is easier with these strategies.

In this video the instructor shows how to set parental controls for a user ID account in Windows 7. To do this go to the 'Start Menu' and go to 'Control Panel'. In the Control Panel window select the 'User accounts and Family Safety' link. There is an option called 'Set up parental controls for any user'. Select that link and it opens a window where it asks you to Choose a user and set up parental controls. There you are presented with some user accounts that are currently active on that syst...

This video describes how to create a new account on Windows 7. In this video it is shown the whole procedure and all you need to know to crate new user account.

Smartphones generally have limited storage, but counter this issue with an always-on internet connection. This led to the proliferation of cloud storage services, which allow us to store and access our large media libraries remotely.

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

Using either iMessages or FaceTime on the iPhone is a great alternative for coworkers to stay in touch in the event that messaging services like Slack go down. They're also a handy means of communicating between buyers and sellers, as it provides a more intimate way of either checking out or showcasing a product. But you're not always going to want to give out your real number to everyone.

Want to know how to check your email accounts using a Motorola Droid phone? This clip will show you how it's done. Whether you're the proud owner of a Motorola Droid Google Android smartphone or are considering picking one up, you're sure to benefit from this hands-on guide. For more information, including detailed, step-by-step instructions, take a look.

Life on the Internet is made up of passwords. You have a password for your Facebook, a password for your email, a password or your online banking - And the list goes on. In this video, learn how to create good passwords that are easy to remember.

It's never too early to put away money for your child's education. Consider these options before choosing a plan. Watch this video to learn how to get started with a college savings plan.

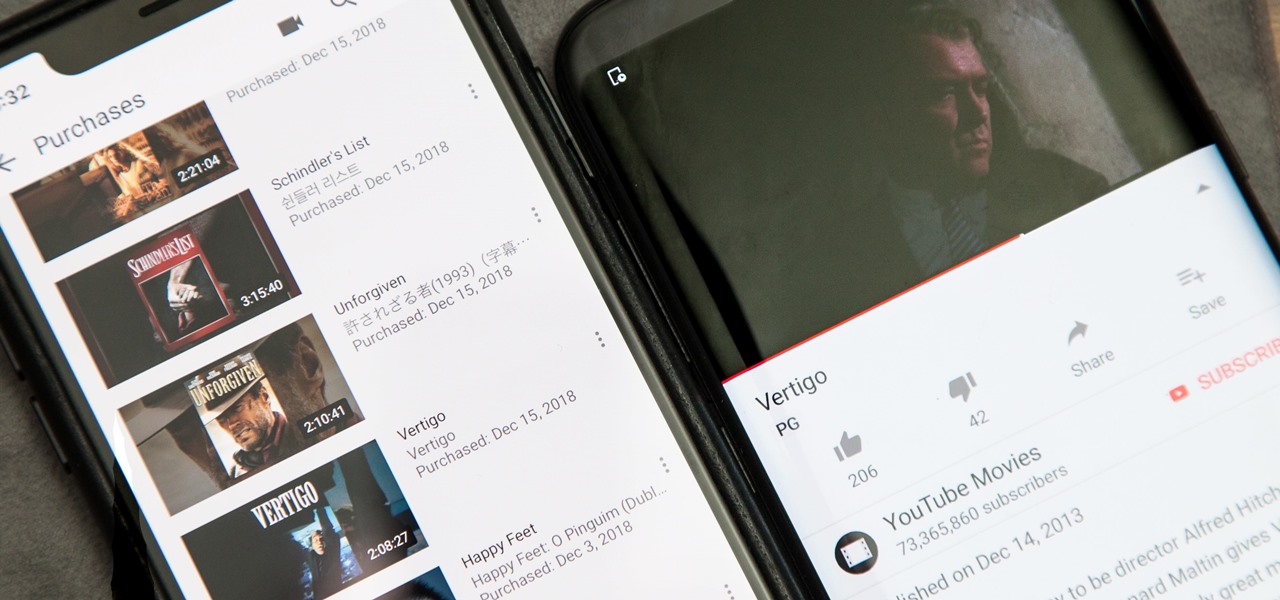
Owning digital movies has many advantages over physical discs, such as easy access and a variety of online stores you can turn to for good deals. There's Prime Video, iTunes, Vudu, and the list goes on. However, this leads to fragmented video libraries, unlike DVDs and Blu-rays which can be stored together. Surprisingly, YouTube is one app that can help consolidate your collection online.

One thing that makes Apple great is the connectivity between its products. Many tasks you do on an iPhone can be switched over to a Mac or iPad quickly and easily. The Notes app is no exception to this advantage, but you need to make sure you're set up so that your notes sync properly on each device you have.

In this video tutorial, viewers learn how to create a new standard user and administrator account. Begin by clicking on the Start menu and select Control Panel. Then click on User Accounts and Family Safety and click on User Accounts. Now select the "Manage another account" option and click on "Create a new account". Users are able to name the account and select the account type (Standard or Administrator). Finish by clicking on Create Account. Users are then able to make changes to the accou...

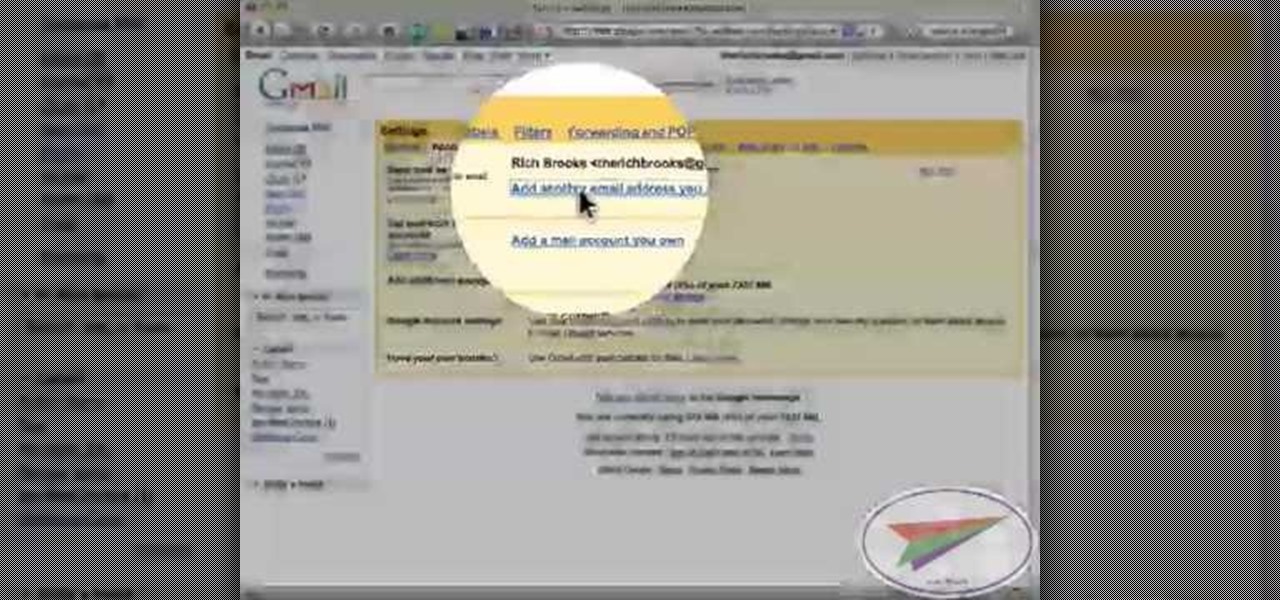
In this video from flytenewmedia we learn how to send from separate email addresses using Gmail. This is great for small businesses. To make it look like you are sending it from your other email address, and not Gmail, follow these steps. Click on Settings then click accounts. You need to add another email address that you own. Click on next step. Now Gmail will send a verification. click on the inbox and click the link within the gmail that you just received. Now it will say confirmation suc...

This video shows how to change your YouTube email address. It may not work for users whose accounts were made before the Google update.

You should watch this video if you want to improve your credit score with just 3 steps. To improve your credit score: Check your credit report. It is where your score comes from. You can also get a free copy of your credit report once a year at Annual Credit Report. Check it for errors. Timing. If you're going to apply for a loan as the application month approaches, stop charging because if your balance happens to be reported while it's big, it will temporary lower your score. Don't close you...

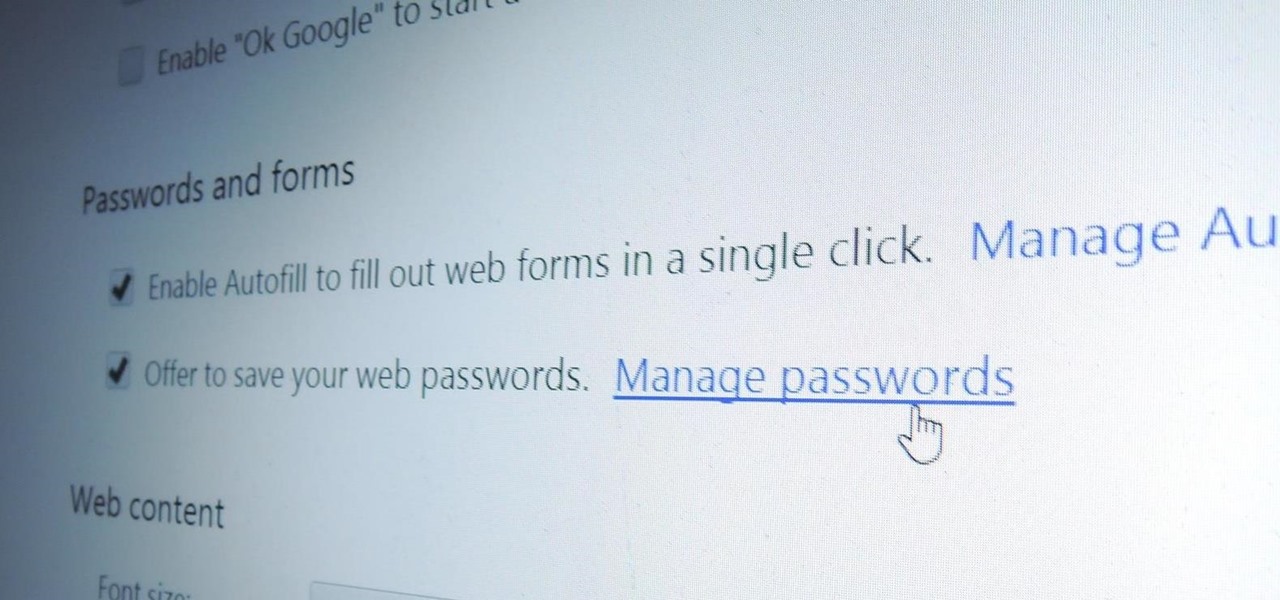
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

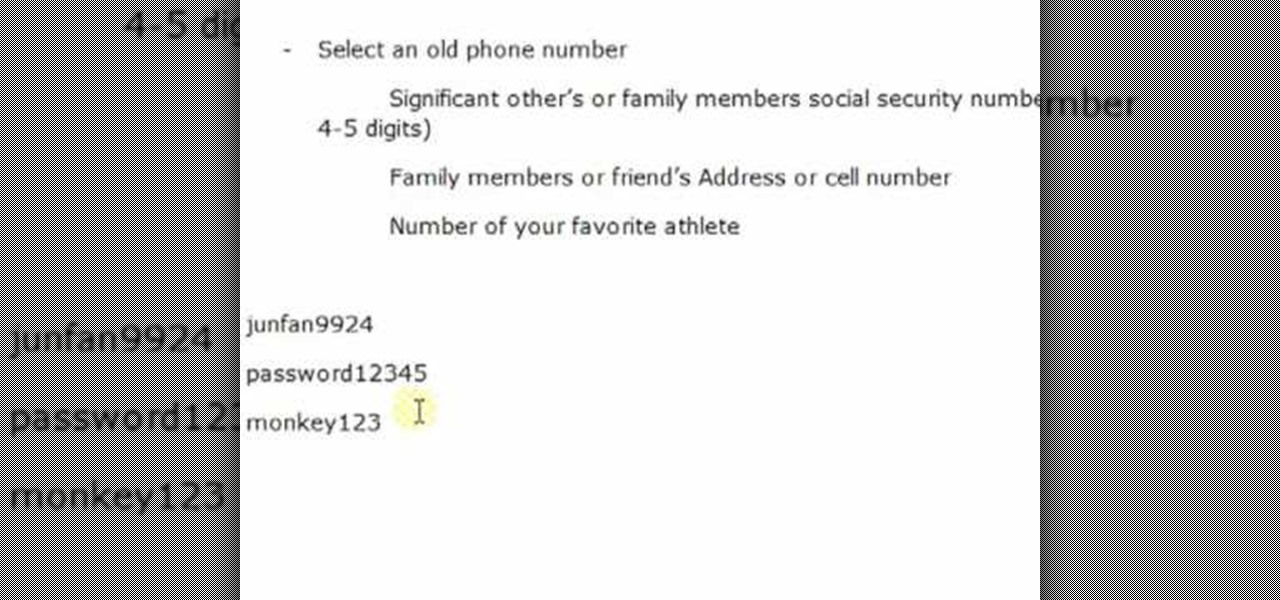
People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

Are you a newbie when it comes to Gmail? Watch this video and learn. It starts of with a brief overview of the registration procedure. Then proceeds to explain the welcome screen and then the main interface.

In this video, we learn how to use secure online passwords. There are a ton of things to consider when creating a password. A weak password is something that someone can easily guess. If you are using a birthday, common dictionary word, child's name, or something common then you are at risk. Your password should combine letters and numbers, and be at least eight characters long. It should also be completely random and have upper and lower case letters. You can use a password assistant if you ...

Sick and tired of receiving spam messages on your MSN and Windows Live Messenger Accounts. Put a stop to it. It's easy. So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete (and somewhat talky) overview of the process in just over a minute's time. For the specifics, and to get started blocking Messenger spam yourself, just watch this handy how-to.

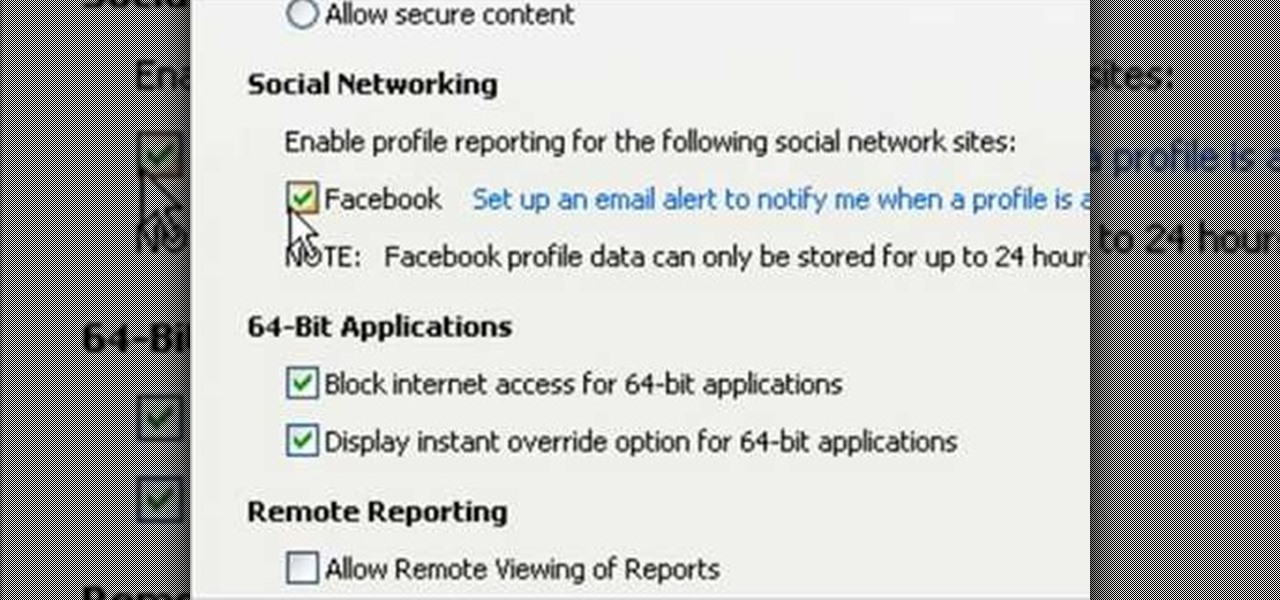
Danny with Top Ten Reviews will show you how to monitor social network activity with the Net Natty program. This will be helpful for monitoring social networking accounts on websites such as Facebook and MySpace. First, open Net Nanny. Go to the dashboard and select Additional Settings under Filtering. With this section, social networking sites that have been used on the computer will be listed. You can check whichever account you want to monitor. Under the dashboard, go to Reports and select...

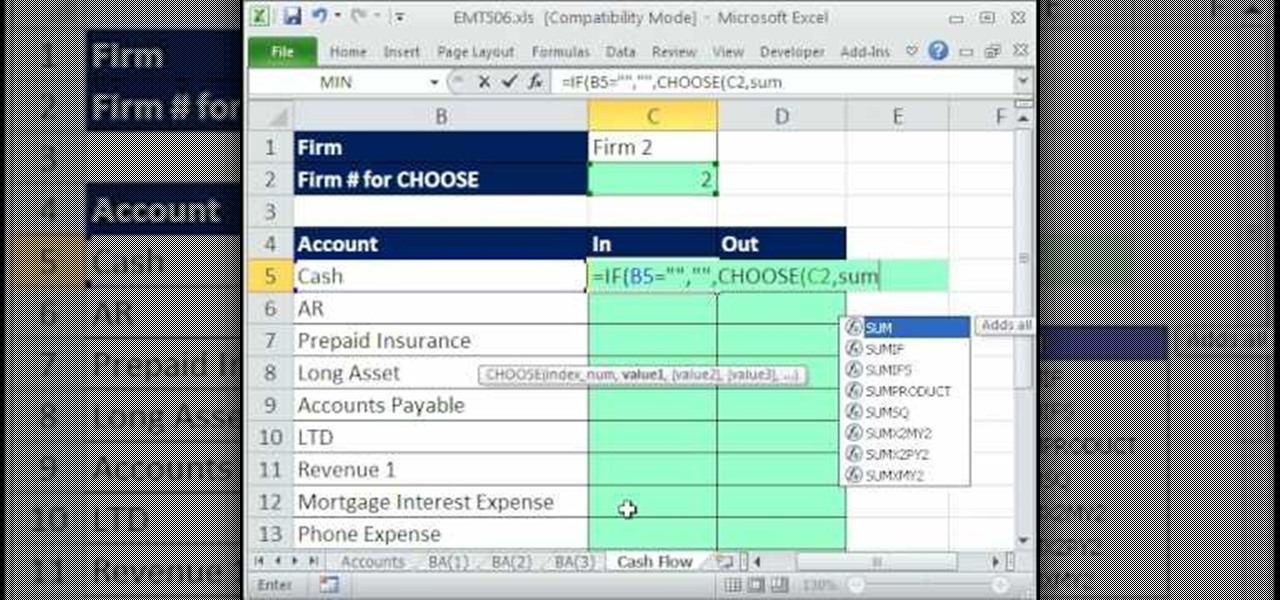
New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 506th installment in their series of digital spreadsheet magic tricks, you'll learn how to summarize data from multiple sheets. For example, you'll see how take checkbook register data from multiple banks accounts and summarize it based on account names.

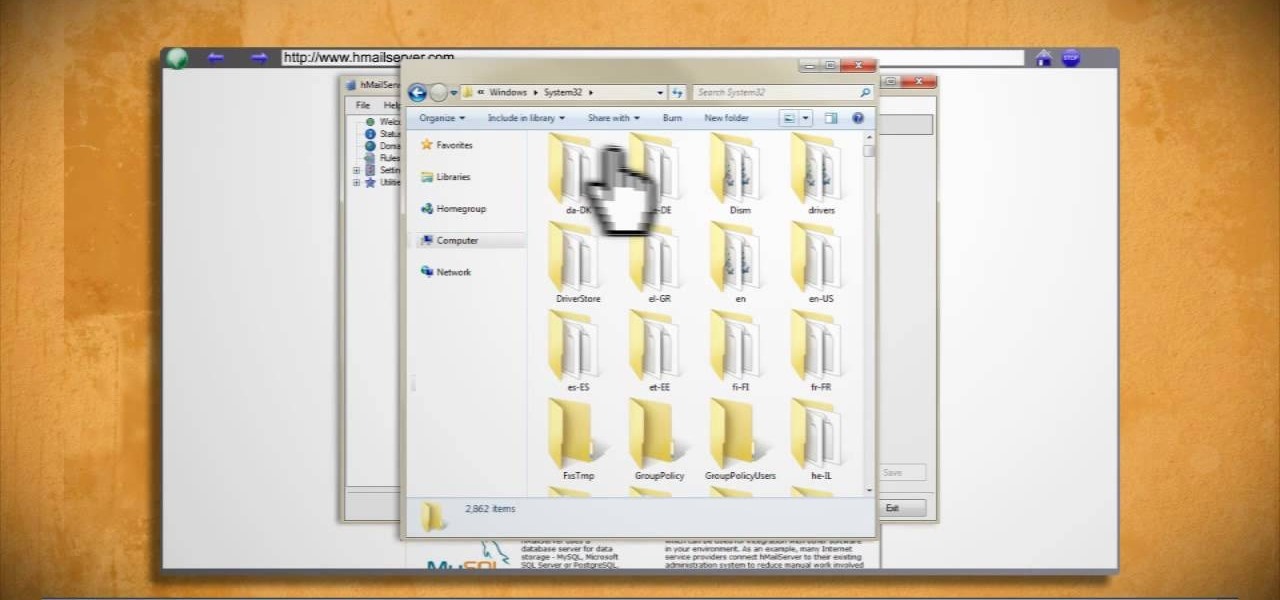
Learn how to make an e-mail server on your home computer to host your own web page and webmail service by following the steps outlined in this video tutorial. You will need a web server, an e-mail server, and a webmail interface. For the server, the most common program is WampServer, which you will need to download. Run through the installation process and grant the program access to your fire. Click on the new icon on your desktop and click Put Online and then Start All Services. This will g...

Follow along as we are shown how to set a password for a new user in Windows 7. -First, go to the Start menu.

You can create a multiple user accounts and enable fast user switching. To do this go to system preferences and open accounts. Now authenticate yourself by clicking the lock icon to be able to make changes. Now click + button

Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

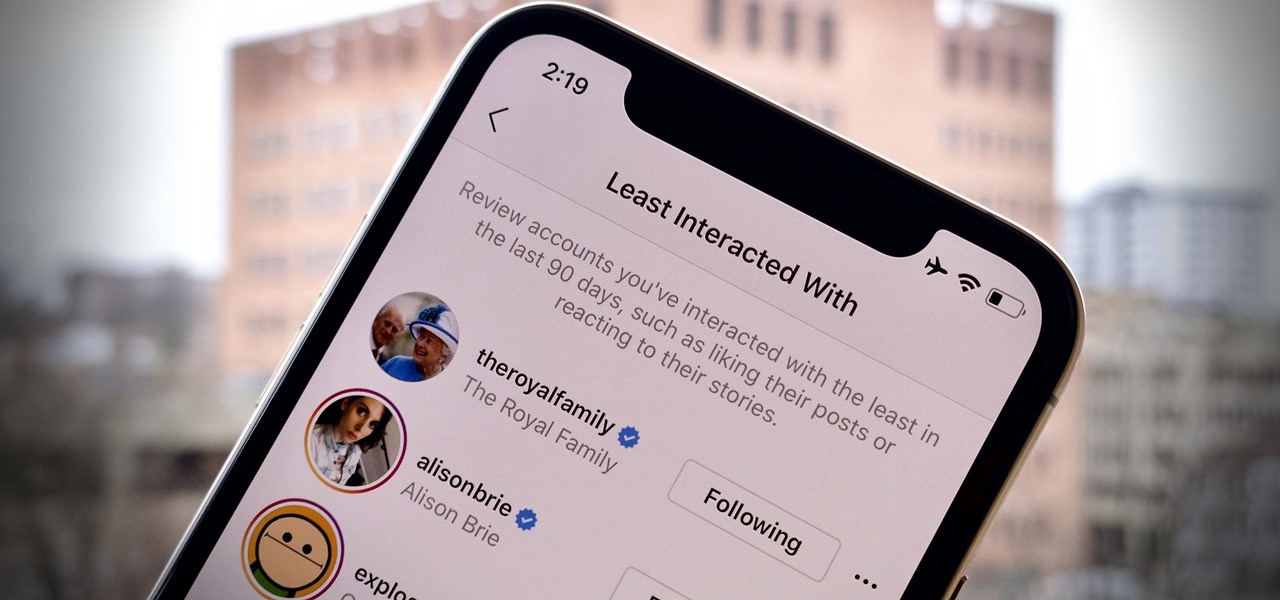
Is your Instagram feed a bit cluttered? Maybe you're seeing posts from people you don't even recognize. Perhaps the content isn't interesting. Whatever the case, it's common after years of having an account to follow too many users whose posts just aren't doing it anymore. Luckily, Instagram has an easy way for you to purge unwanted accounts from your following list.

If you use Apple's email services and the "From:" field in your iPhone's Mail app is cluttered with @Mac.com, @Me.com, and @iCloud.com variations of the same address — along with third-party accounts — there's an easy way to declutter things and hide the addresses you don't use anymore.

When Google released Android 4.2, a new feature was introduced for tablets that allowed for multiple accounts to be used on a single device. In order to create a unique experience for each user, apps and personal data were kept separate, and switching between users became as simple as tapping your profile photo from the lock screen.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...