Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

In the last couple of days there's been a lot of speculation about the powers of Microsoft's HoloLens 2, but few have had a chance to get their hands on one to see if the company's claims live up to what HoloLens inventor Alex Kipman showed off on stage.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

We see Steampunk props all the time and wonder where the maker found all their pieces. In fact, for some people it's almost like a game to examine each prop and see if they can name all of the original parts.

Previously, losing an AirTag or Find My network accessory meant relying on tech-savvy strangers to contact you via phone or email if they found it. With a new Find My update, you can ditch the passive approach and be more proactive about recovering your tracker by sharing its information with trusted contacts and even airlines, allowing them to track your tracker for you.

Generative artificial intelligence has taken the tech world by storm, and Google's AI chatbot will give you a taste of what it offers.

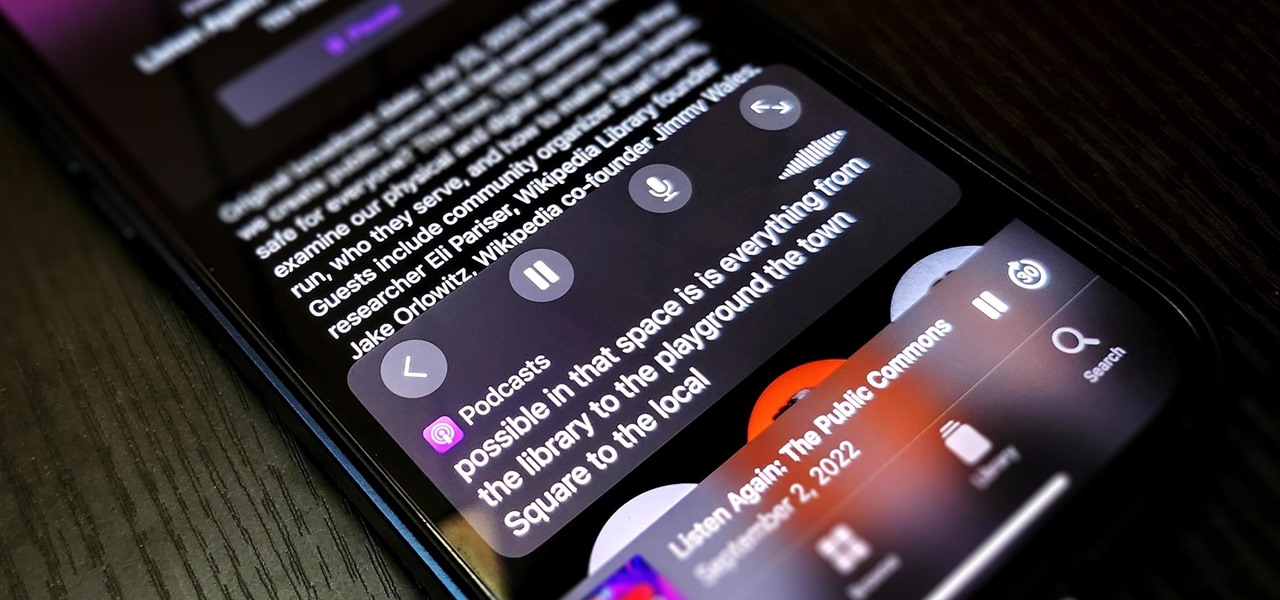
With Apple's latest accessibility feature, you can get live transcriptions of anything you're listening to on or around your iPhone. Real-time captions work for phone calls, video conferences, FaceTime, music, podcasts, streaming media, movies, games, and more — even someone sitting right next to you talking.

Google's been on a mission to improve the privacy and security of Android lately, and Samsung's always been at the forefront in these areas. As a result, One UI 3.0, which is based on Android 11, is the most secure OS version to ever hit Galaxy phones thanks to few key changes and new features.

You may be wondering what exactly makes the Pixel 4a's camera so great. Compared to its predecessor, it has the same Sony IMX363 sensor and no additional hardware. Well, beyond stellar image processing, it also has several great new features that Google has added since they released the Pixel 3a last year.

It's always a big deal when the company that makes Android releases a new phone. Google's Pixel series has made a name for itself in three short years behind its camera prowess, but now it's time to start competing with the major players. That said, Google should like how their Pixel 4 and 4 XL stack up against the iPhones and Galaxies of the world.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

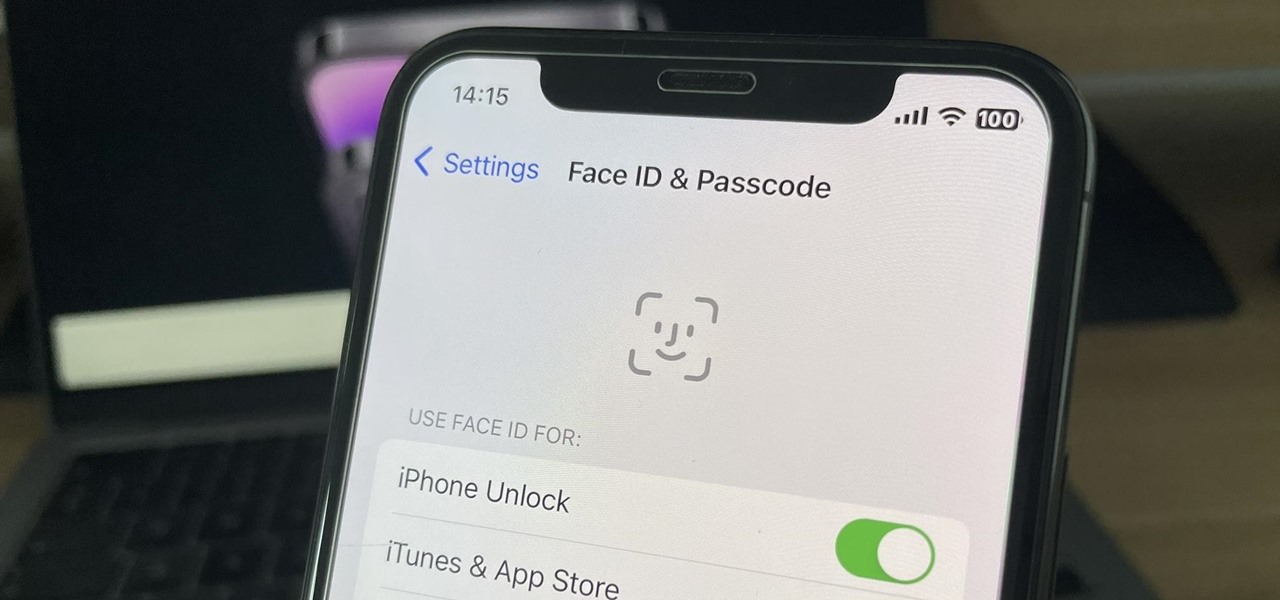
The iPhone 13 and iPhone 14 series models have a new feature on iOS 16 that lets you use Face ID when your iPhone is in landscape orientation. This is most helpful when trying to make purchases in apps and games where you use your iPhone rotated on its side. If you're having issues using Face ID in landscape mode, there may be some easy solutions to getting it working.

The new iPhone 14, 14 Plus, 14 Pro, and 14 Pro Max all come with great, never-before-seen-on-iPhone features, including the A16 Bionic chip, Bluetooth 5.3, precision dual-frequency GPS, and dual ambient light sensors. But that's only a few new features exclusive to the 2022 lineup.

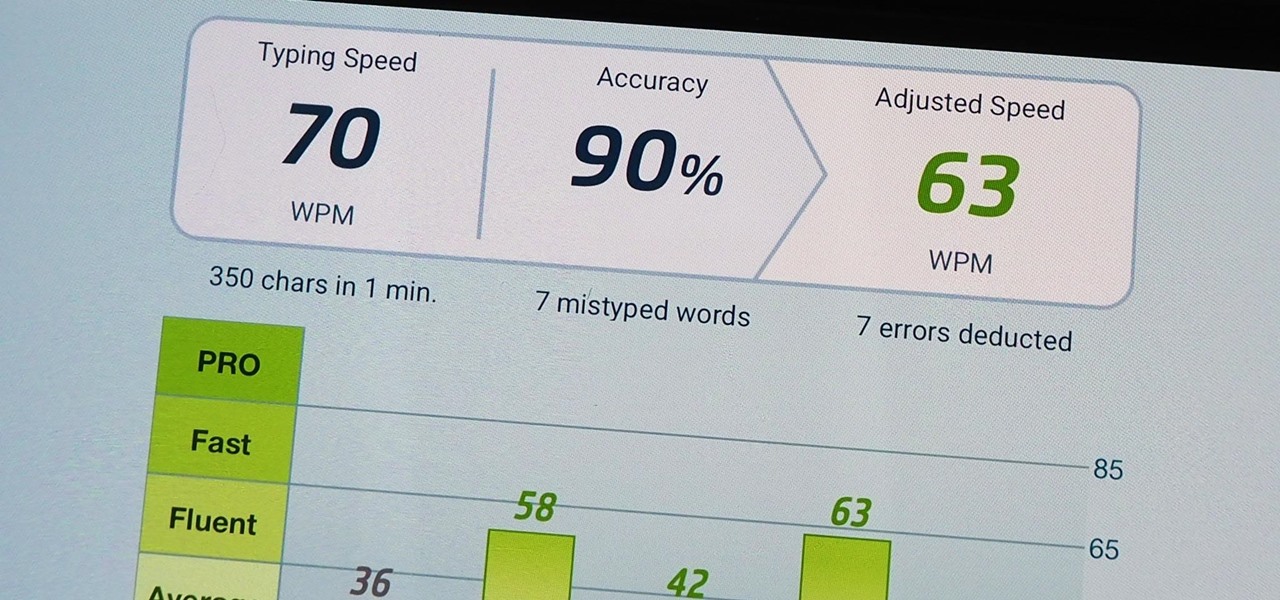
We use our smartphones every single day. They're a part of our daily routine, and as a result, we've gotten really good at using them — especially when it comes to typing very quickly. But just how fast can you type on your iPhone? Can you match your speed on a physical keyboard for your computer or tablet? You might just surprise yourself.

Whether it's a short road trip or an 18-hour flight, our phones are now essential travel companions. No longer do we need a GPS unit, maps, cameras, camcorders, or even boarding passes. However, not all phones are created equal in this regard. Some are more suited for traveling, no matter the duration.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

If you have an iPhone 15 Pro or 15 Pro Max, your Action button has even more actions it can perform thanks to the iOS 18 software update. These actions are also available on the iPhone 16 series lineup — the iPhone 16, 16 Plus, 16 Pro, and 16 Pro Max — all of which have the Action button.

The new iPhone 16, 16 Plus, 16 Pro, and 16 Pro Max are worth upgrading to, but if you want more advanced features, especially for the camera, you may want to take a closer look at the iPhone 16 Pro and iPhone 16 Pro Max.

When they first appeared, smartphones came with a promise to make our lives easier and make us more productive so we could have more free time and energy. But now, the average user spends almost 5 ½ hours daily on their smartphone. If that sounds like you, there are ways to use your iPhone more efficiently — without getting sucked into distractions.

If you're not using Control Center on your iPhone, you're missing out on a powerful tool that can streamline how you interact with your device, make certain tasks more efficient, and give you quick access to system tools, switches, and sliders for quick changes no matter where you are or what app you're in.

Apple just announced its new iPhone 15, iPhone 15 Plus, iPhone 15 Pro, and iPhone 15 Pro Max models. This year, the 15 and 15 Plus models have a lot in common with the 15 Pro and 15 Pro Max, but there are still some pretty incredible features that the Pro lineup sports that the regular lineup doesn't.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Siri has long relied on basic sources like Google and Wikipedia for answers, but with iOS 18.2 and iPadOS 18.2, Apple is taking its virtual assistant to a new level by integrating ChatGPT. Now, you can use Siri to generate text and images with ChatGPT — and that's not all. ChatGPT is deeply integrated into Apple Intelligence and goes beyond just Siri.

There are some important new features in the Photos app on iOS 17 and iPadOS 17 that will streamline editing, give your pets more recognition, help you learn about the world you've captured, and even add a bit of fun to your day. There are even a few hidden tricks that may surprise you.

Many of the iPhone 15, 15 Plus, 15 Pro, and 15 Pro Max features were carried over from last year's models. Still, quite a few capabilities are exclusive to the 2023 lineup, and some may be worth the upgrade.

Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

Samsung's lineup of Galaxy Note devices for 2020 include the specs-behemoth Galaxy Note 20 Ultra and the slightly more cost-effective Galaxy Note 20. Excuse the pun, but there's a lot to unpack here in terms of unique features and hardware.