After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.
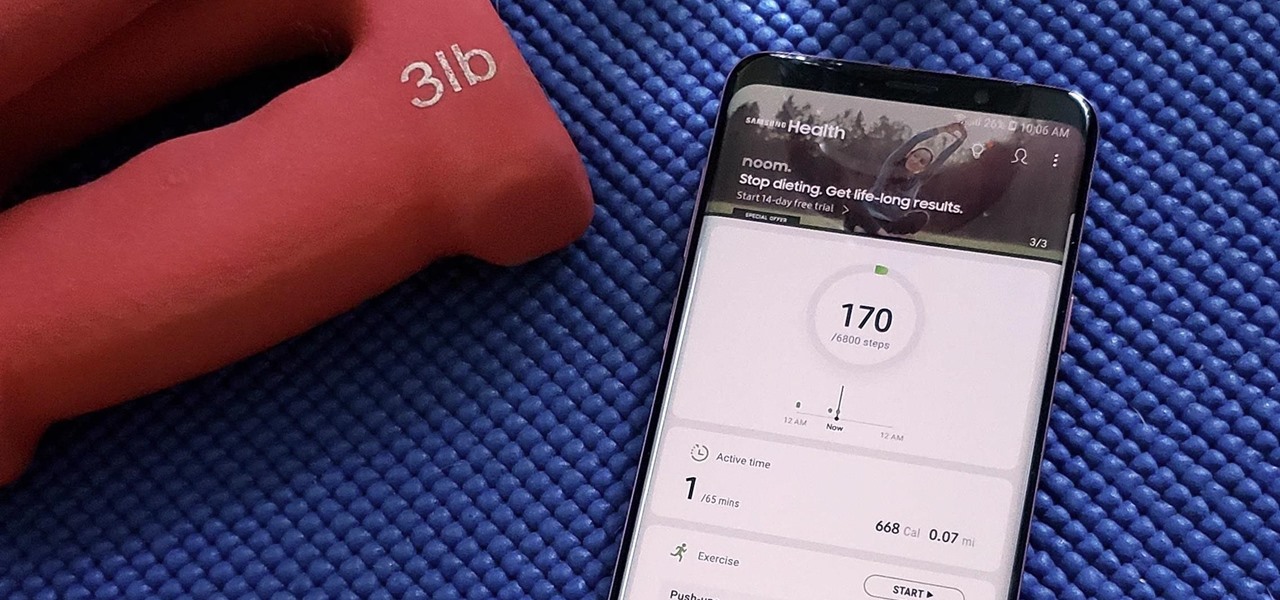
Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Chrome is the browser of choice for millions of iPhone and Android users, largely thanks to its user-friendly interface and native Google support. But with concerns over sharing private information with massive companies growing, many people are starting to want a little less Google integration in Chrome.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

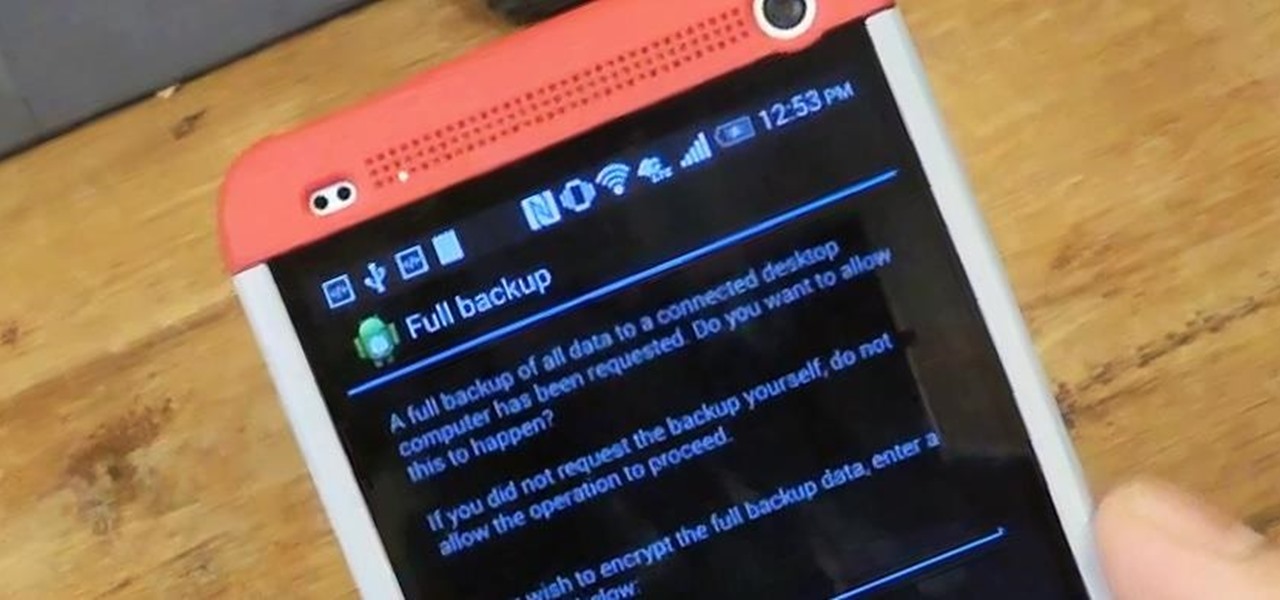
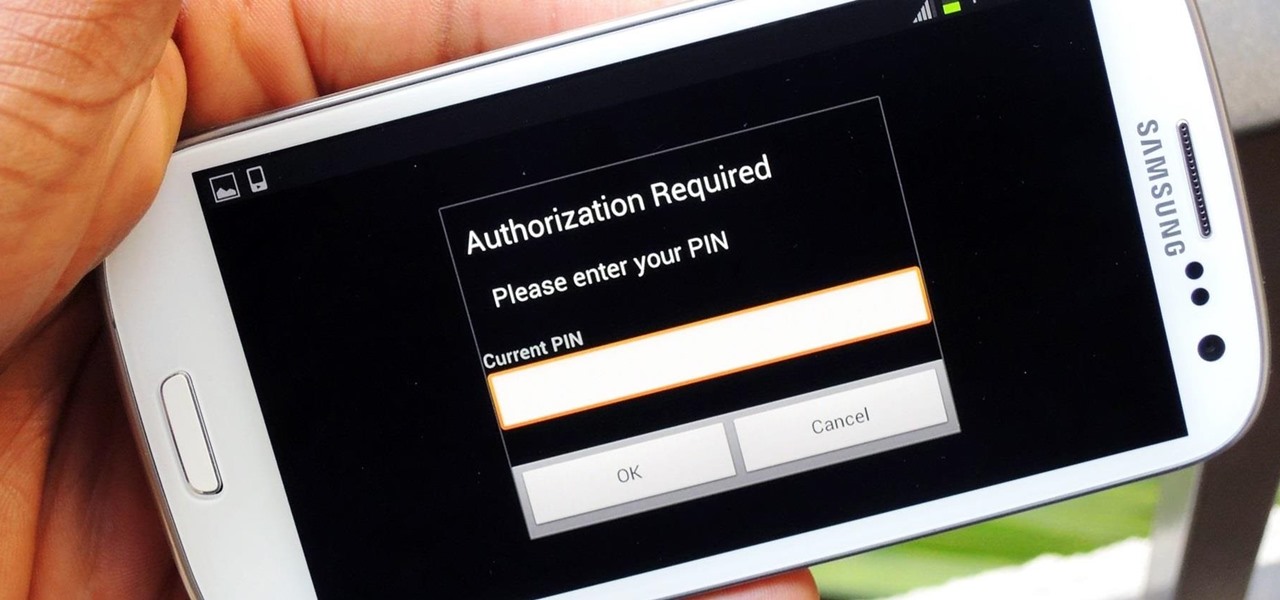
After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Verizon has long been king in the wireless provider market, but recently it has had to step up its game in the data department. A limited data plan — with supposedly superior service — was no longer cutting it for customers. Many of whom left to take up the sweet, sweet offers of competitors like Sprint and T-Mobile. This past fiscal year, Verizon had a net loss of customers in the first quarter. Something that has never happened to them before.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

The highly anticipated VR headset hasn't been on the market long, but there's an issue that has some consumers, and even government officials, concerned about the Oculus Rift. You probably guessed the issue surrounds privacy and the extensive, not-so-secret way that it's collecting your personal data. The privacy concerns came about as various customers and media outlets took notice of the rather lengthy Terms and Services that pop up once you strap yourself into the Rift headset.

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

One of the most feature-packed camera suites out there resides on the Sony Xperia Z2. Along with the regular camera and video modes, it comes with Motiongraph, AR Effect, and Social Live.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Today, I'm going show you how to back up all of your apps and their data using Android Debug Bridge (ADB)—an essential function for all softModders. These commands will be especially useful when you are updating your version of Android, since they don't require a third-party program to run on your device.

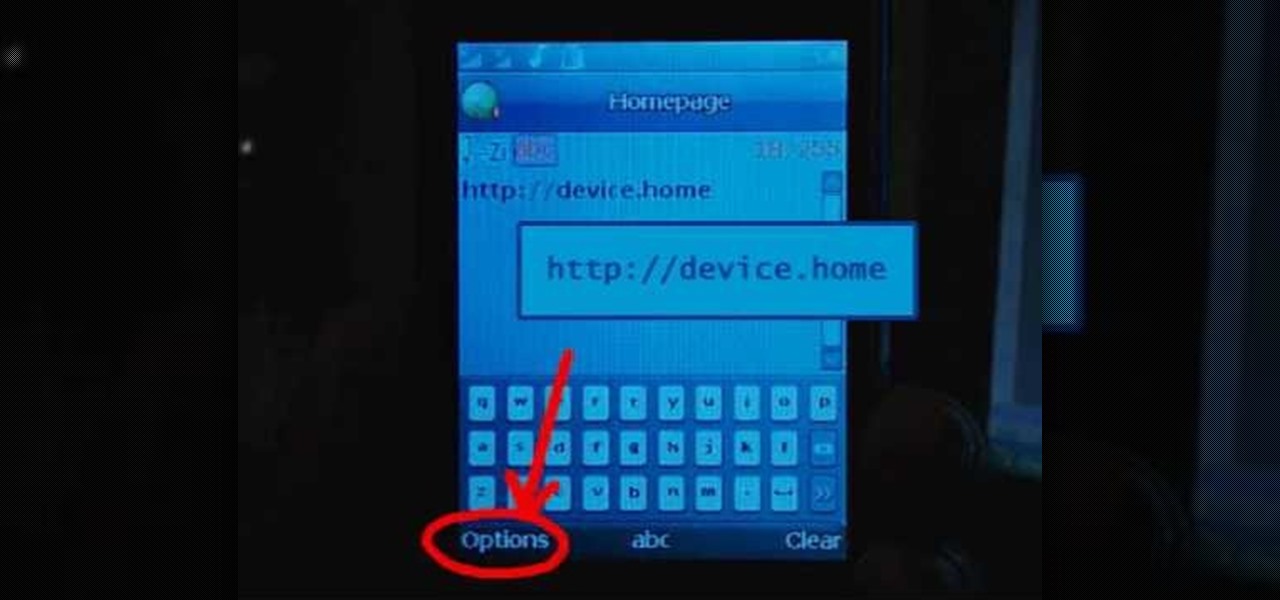
Normally, "restricted access" is something you despise. No one likes to be told they can't do something, especially when it comes to the Internet. Unfortunately, having web access at all times can not only eat away at your wallet, but make your day less productive overall, so some sort of moderation is needed.

The iPhone 5 will be here in no time. Pre-orders started at 12:01AM PST this morning and it's expected to start shipping in about two weeks. Verizon, AT&T, and Sprint are all handling unlimited data plans differently, so if you currently have an unlimited plan and are going to get the iPhone 5, you'll want to know what your carrier is doing before you upgrade so you don't end up with a very unpleasant surprise on your next phone bill. Verizon

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

Attention all optometrists and ophthalmologists— there's a new tool in town, and it's called the Diaton Tonometer. Diaton's tonometer is an easy-to-use and accurate instrument for measuring intraocular pressure (IOP) through the eyelid, which makes it simple to diagnose patients with glaucoma during the early stages, so that immediate treatment and medicines can be administered. This transpalpebral tonometer is handheld, pen-like and no-contact, which provides absolutely no risk of infection....

There are signs you're having a baby even before you miss a period. You Will Need: * A knowledge of physical symptoms

Need to make a PCB quick? Well, this video tutorial will show you how to create a PCB with the toner transfer method using photo laser paper.

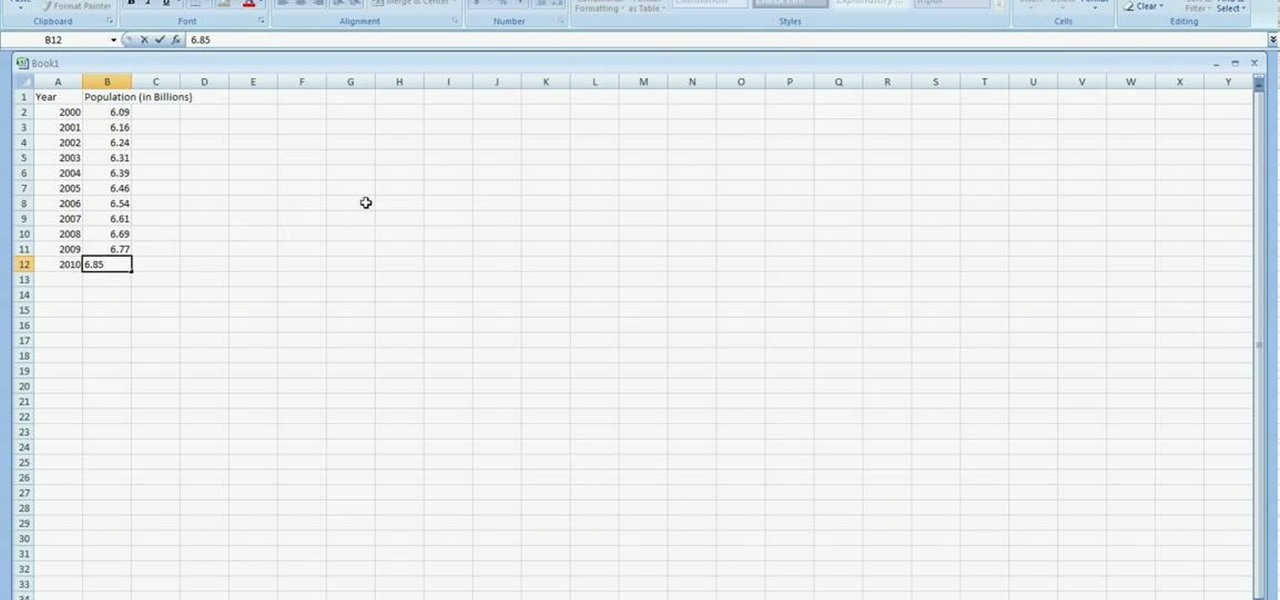
In excel a left click is made on box A1 and the X title is typed in as year. In A2 the year 2001 is typed and in A3 the year 2002. Both A2 and 3 boxes are highlighted and the bottom right hand corner is used to drag the work into a copied sequence down to A12. In B1 "population in billions" is typed. From the web site the data is copied and typed in as it appeared and the numbers are rounded off. A click is made on the "insert" tab and line is selected from the menu which appears. The upper l...

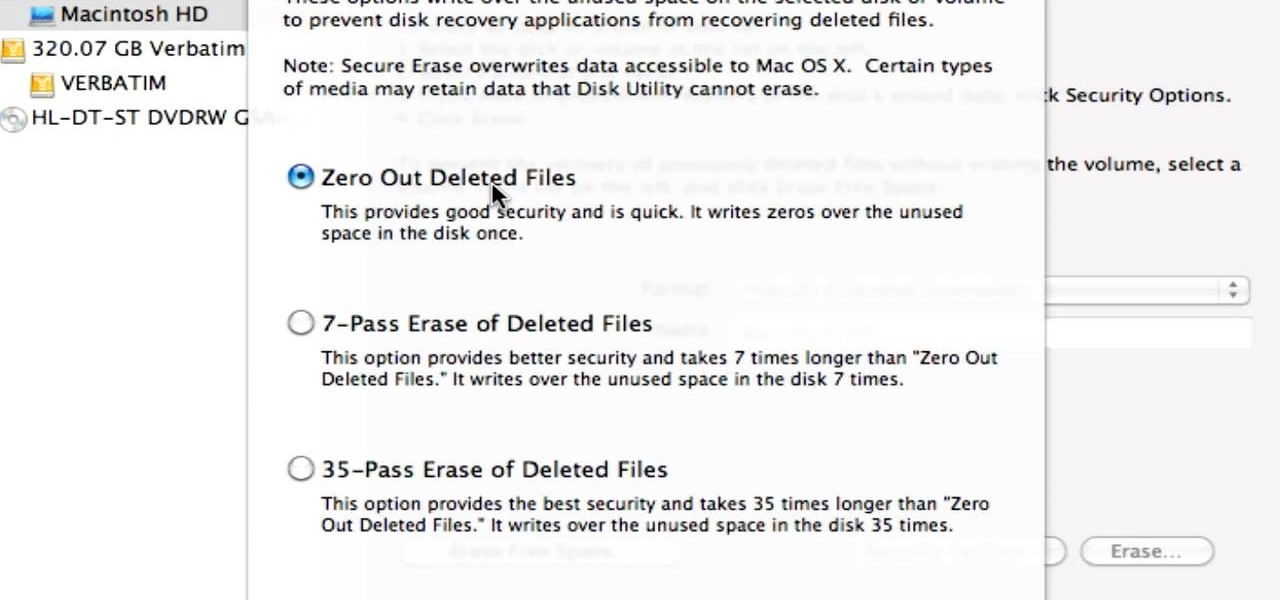
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...

Okay, so you might not need a how-to for this one, but nonetheless, just in case, here you go— plugging in the data cable to your Samsung Galaxy Tab. It's basically the same way you plug in all mobile devices these days, and it's just like any other Android tablet, so you should be able to do it with little difficulty. Just don't force it in, or you risk damaging it and your device.

A non-CPU lens is one which does not have contacts on the rear mount, meaning it communicates with the rest of the camera solely through the aperture. This tutorial shows you how to set up the lens data for your camera, so you can get the most out of your non-CPU lens.

Learn how to set up Internet on iPhone clones with this video. *First thing you need to do is to make an AT&T GPRS data account.

In this Silverlight web application tutorial you will learn how to create a basic stock quote application that updates in Realtime. You can apply this ASP.Net backend application to any realtime data update application you need to make. All you need is Silverlight to get you started.

If you've ever entered a lot of data into an Excel spreadsheet before, then you know that putting together even one spreadsheet is a pain in the butt. So if you are required to place all the data on one spreadsheet onto another spreadsheet, don't slave away for hours copying and pasting.

This screencast tutorial from Matthew MacDonald, author of Access 2007: The Missing Manual, shows you how to use pivot tables to analyze data in Microsoft Access 2007.

Are you 100% sure that all of your data is gone? Use Darik's Boot and Nuke to completely wipe a hard disk of all data.

This video shows you how to use Windows Task Manager to restart your computer without losing any data.

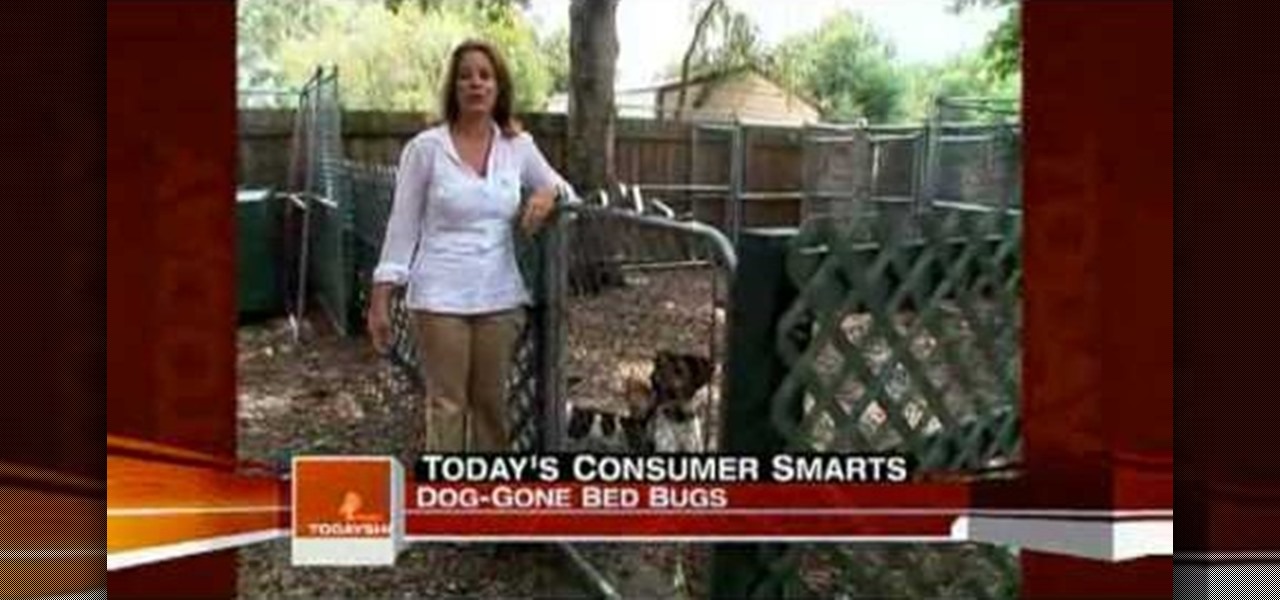
Trained dogs may be used to help eradicate bed bugs. A sign that your home is infested with bed bugs is the presence of bites. If bites appear in a straight line, on the skin, then that's a classic sign of bed bug bites. Trained dogs are able to pinpoint the bed bug infestation. They are 98% accurate, when other methods are only effective 30% of the time.

Want to add location data to posts on a self-hosted WordPress blog or website? This clip will show you the way. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about the abovesaid things through videos like this one. Take a look.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 650th installment in their series of digital spreadsheet magic tricks, you'll learn see how to take all records from a data set and place them into one column using the INDEX, INT, ROWS and MOD functions.

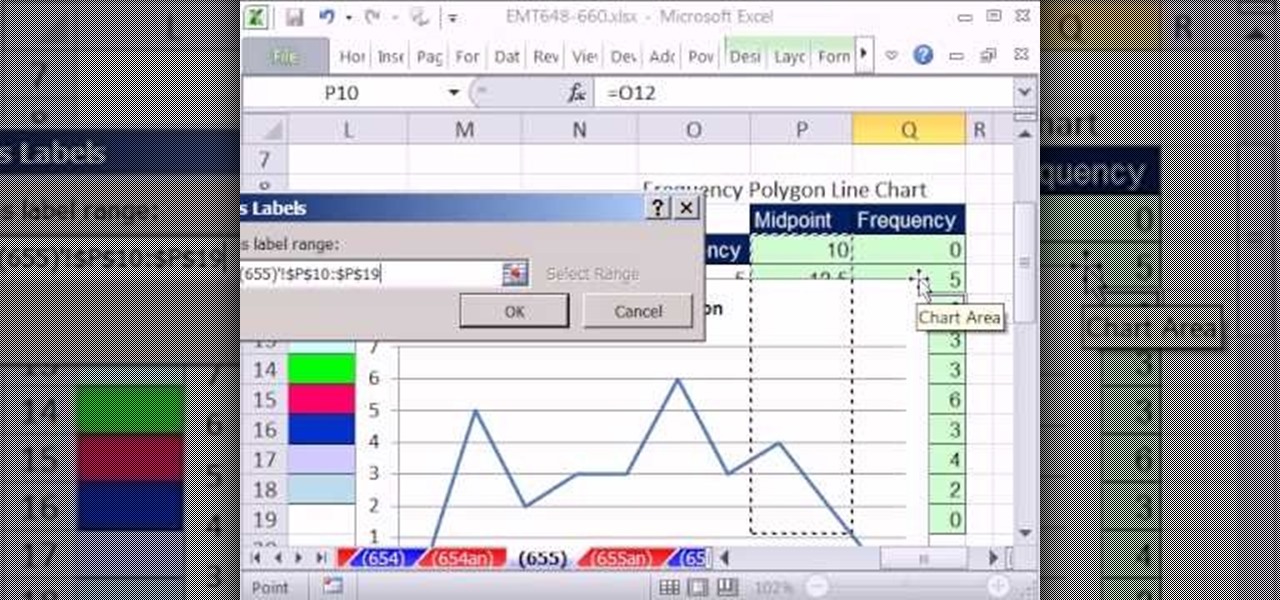
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 655th installment in their series of digital spreadsheet magic tricks, you'll learn see how to create a statistical frequency polygon using a line chart. Also see how Excel mistakenly interprets number category label data as Number Series data.

The FG-42 machine gun is one of the many brilliantly-designed weapons the Nazi war machine produced during its misguided attempt to take over the world. If you want to make a WWII battles set out of Legos, having some tiny versions of these guns will make your Nazi pieces much more historically accurate and intimidating. This video features detailed instructions for modifying one of the Lego Storm Trooper guns as common as raindrops to look like a FG-42 using only some common hobby tools.

See how to approximate a definite integral to a desired accuracy using Maclaurin/Taylor series and the alternating series estimation theorem with this free video calculus lesson. See how it's done with this free video algebra lesson. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study...