Many home chefs are deterred from whisk-intensive recipes such as mayonnaise because they seem to require more than two hands—which is obviously the maximum number we possess. One hand is required to stabilize the bowl, another must be whisking constantly... and a third hand is needed to pour a steady stream of oil.

There are a few key ingredients that you always need on hand when baking cookies and other desserts, but when you run out, you run out. You either have to stop what you're doing and go to the grocery store, find a good substitute, or scrap the project entirely. Chances are, you'll never accept defeat, and why go to the store if there's a good substitute on hand?

There are rules that cooking in general always follows: cakes should be fluffy. Steaks should be heavily seasoned, and nowhere near a bottle of steak sauce. Every stock should start with aromatics (onions, carrots, & celery). And, until very recently, meringues should always be made with egg whites.

Taking care of your car requires effort, whether you take it to the pros for washes, waxes, and detailing, or you spend time to make it shine yourself—and it often seems that, right after your car is sparkling again, rain or midnight moisture appears to cover its surface in water spots. With a small tweak to your typical car care routine, you may be able to keep your car's surface and windows shining longer and better: you just need to add a little hair conditioning liquid.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

Summer cookouts and barbecues come with a lot of delicious foods, but to me, there's nothing better than dishes heaped with avocados. From guacamole to simply eating an avocado right out of its skin, I devour this fruit constantly—but it's one that can be tricky to find perfectly ripe.

Ice pops are like summer on a stick, with all the sweetness and stickiness of July and August. Store-bought popsicles, although refreshing, are never as good as homemade. So it's time to up your popsicle game with some of these beautiful creations, including some boozy pops (poptails) for adults.

We're all familiar with the sinking feeling that happens when you cruise through a recipe, only to arrive at an instruction that calls for a tool you don't have. Some of the best food hacks (and my personal favorites) exist to combat that problem. Why spend money on a kitchen tool—or worse, avoid a recipe altogether—when you could find a new way to achieve the same result?

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Summer is right around the corner, which means it's time to switch from perfect hot coffee to perfect cold coffee. A nice icy glass of cold coffee is wildly refreshing and just plain delicious. In my opinion, it's the key to enjoying any sunny day (warning: if you don't already drink cold coffee, you may find yourself drinking four or five glasses a day very quickly).

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

The AMOLED display on the Nexus 6 wastes no power to show black pixels. This is because pixels on such a screen emit their own light, and black can be easily achieved by simply not lighting any given pixel.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

Like many others, I like a good cocktail every now and then, and I've always been impressed when my cocktail enthusiast friends would come up with a new drink or even just remember how to concoct a Clover Club (FYI, it's made with gin, raspberry syrup, lemon, and egg white). There's a secret bartenders and craft cocktail aficionados know, though: It's all about math, the simplest and most intoxicating math. Pythagoras would be so proud.

Can you tell when someone is shooting you a fake smile? Even though fake smiles are easy enough to see through, we all still do it, attempting to show others just how happy we are when we're really feeling less than fantastic. Unfortunately, every smile we fake makes us a tiny bit more miserable.

Officially, in order to use AirPlay to stream music from your iOS device, you would need either an Apple TV, AirPort Express, or an AirPlay-enabled receiver or set of speakers. Despite what Apple wants you to think, there is another way to stream music without any of those AirPlay-capable devices—you just need to have two iOS devices (or just one iOS device and a Mac).

You hand your iPhone to a friend to show them a picture. What happens? They swipe. Left, right, it doesn't matter. You don't remember what lies in either direction of the photo in question, and you don't want anything compromising exposed to the unassuming viewer. Luckily, Apple includes a safety net in iOS to prevent this scenario from ever happening, so long as you set it up ahead of time.

Geohot's Towelroot exploit made rooting the Galaxy S5 so easy that it was almost unreasonable not to try it out—even for the first-timers out there. This, of course, meant that folks who didn't truly need root for their usage went ahead and got Superuser privileges anyway.

The book that started it all (published in 1967). When Virginia Harvey wrote this book, she remarked that macramé was almost a lost art...

Known for its easily recognizable filters—and coining the hashtag #nofilter—Instagram has long been an app that focused more on photo posting rather than photo editing. Yet today, Instagram released an upgrade for both Android and iOS users that edges the app towards becoming a full-fledged photo editor.

It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.

The international hit Xperia Z2 may be headed to Verizon if a posted, and quickly erased, image is any indication. Take this information with a grain of salt—I certainly am—but this could be Sony's entrance into the non-GSM realm. The image above was posted to Sony's Xperia Google+ page, and very quickly removed. Compared to the Z2 that's currently on the international market (below), we can see that not only has the Sony logo shifted to the bottom, but a Verizon logo rests squarely along the...

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

Sometimes you've got a head of lettuce that you want to eat but it lacks a certain youth. In other words, it's wilted and browning at the edges. Other times, you get to the grocery store near the end of day and the only lettuce or greens available look a little on the sad side. Never fear. You're not doomed to a meal of fast food or mouthfuls of soggy salad. You can easily revive those leaves and have something crisp, green, and delicious for your next meal, so don't dump it in the trash.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

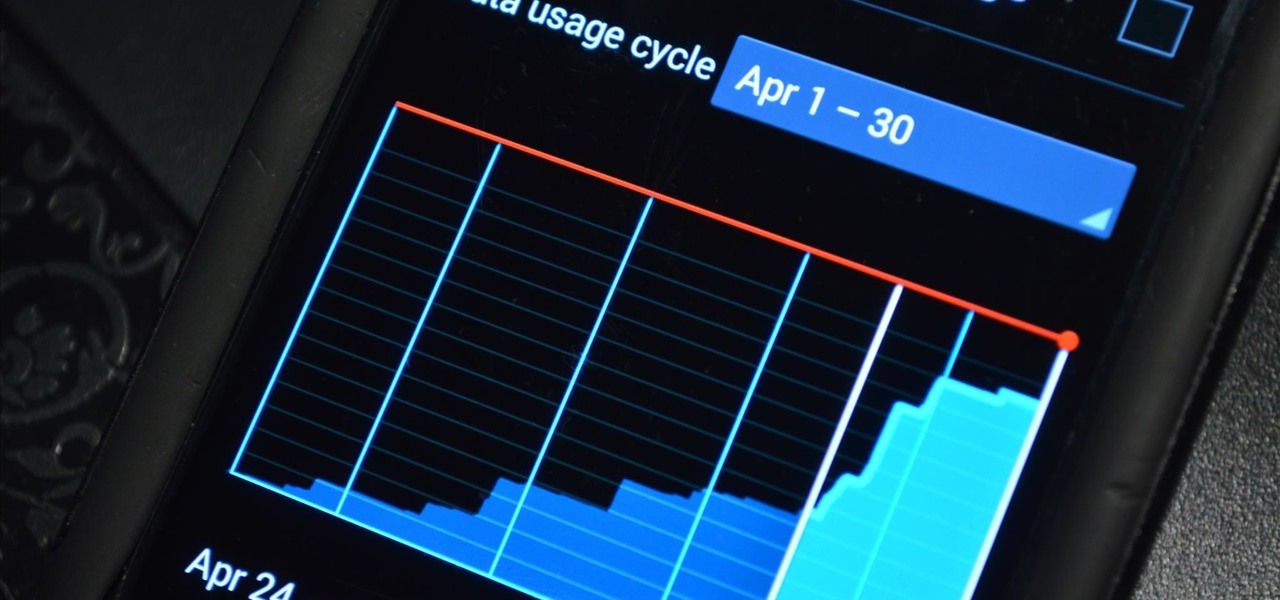
I remember how fast my Nexus 7 was the first time I turned it on. Boy, do I miss it. Now my tablet is pretty buggy and crashes happen frequently, and I'm sure that goes for many of your Nexus 7s as well. Even if you upgrade to the new Nexus 7 next week, it will eventually develop similar issues.

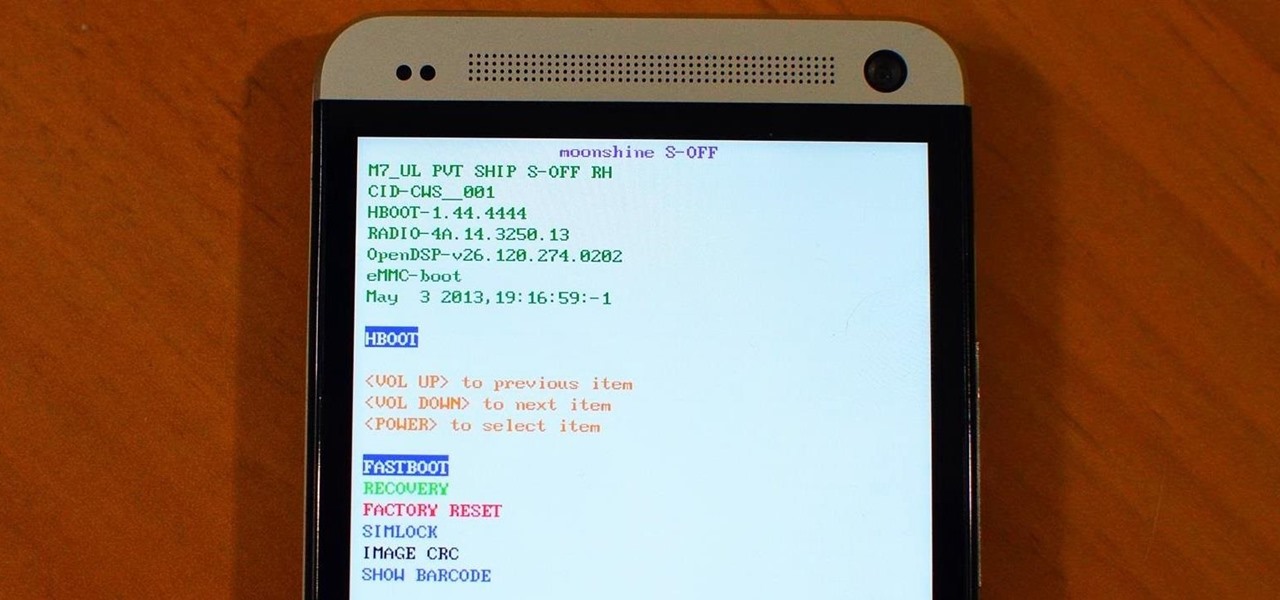
If you still have time left on your warranty, taking your HTC One in for repairs can be a serious pain if you've modified it in any way. To avoid the chance that they'll reject your phone because it's been tampered with, you'll have to return it to stock condition.

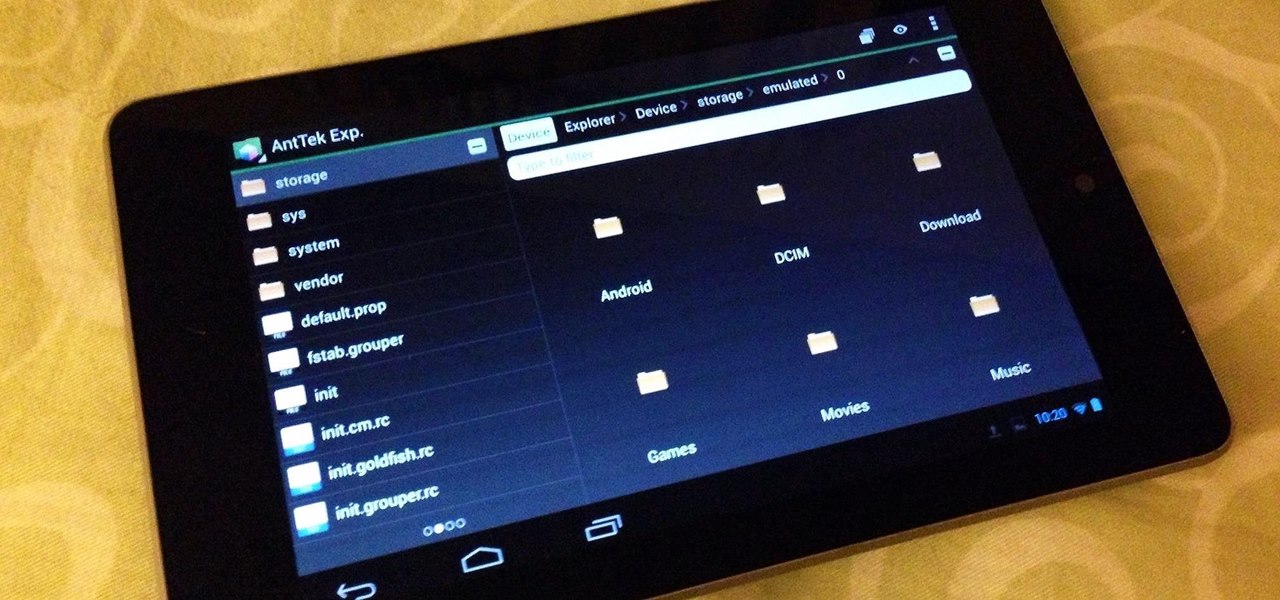
If you're always on the go, the Nexus 7 is a godsend for having everything you need at the tip of your fingers—music, videos, text documents, photos, and more. Unfortunately, as good as that is, it also means one hell of a messy tablet.

Cinema is a matter of what's in the frame and what's out, according to director Martin Scorsese, who asserted that when describing his life's work. Getting the perfect shot can turn an otherwise ordinary scene into something great, both on and off screen.

The art of persuasion is a very crucial characteristic that anyone can learn, and it has countless benefits. Whether it's at work, home, or in social situations, the ability to be veritably persuasive can have an unheralded impact on your daily life.

As a kid, I was always interested in what was beyond our world. I remember lying down on the top of my dad's car and watching the stars for hour, gleefully excited whenever a shooting star streaked across the night sky.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Halloween costumes.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

Learn how you can achieve this purple and white eye shadow look with this how to video. This tutorial uses MAC cosmetic products.