How To: Beginners x86 Linux Assembly
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Sometimes the best way to hide things is in plain sight. Whether you're trying to sneak some medication past security at a concert with a zero-tolerance policy, or you're just worried that maybe Omar comin', YouTuber MrGear has a clever way to put your mind at ease.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

Most of you probably heard about Rasberry Pi and if you haven't; what is wrong with you? But nothing less a Rasberry Pi is a computer a very small computer. Despite these size limitations, the Rasberry Pi is to not be underestimated. Not only can it do anything like a normal laptop or desktop, but, in my opinion on of the coolest features is that it boots off a Micro SD card. It can do anything that you want, but it's built to be played with. A hacker heaven.

The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

Arcade games have always been more about chance than skill (at least when I play them). Whether you're at a children's party at a Chuck E. Cheese's or drinking it up with your pals at a barcade like Dave & Buster's, you'll find similar games that hold the golden ticket to fun and cheap prizes that no one needs—boy, do you want them.

There is a huge myth that most Americans believe, and it might be the marketing triumph of the 20th century. We pay an absurd markup (Zero Hedge says as much as 280,000% for "designer" water) on something we can get for free because most of us believe that bottled water is healthier than tap water. But is it? Here are 5 reasons why tap water is probably better than that bottled stuff you drink. 1. It's Not Cleaner (& Might Be Dirtier) Than Your Tap Water

Why did I write this when they're tons of scanning tools available.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

While I frown upon any form of uneaten cookie, sometimes we overestimate our late-night cravings for baked goods leaving us with extra cookie dough at 4 a.m. If you're in the privileged dilemma of not having enough excess dough to make another batch of cookies but just enough left over that you can't justify tossing it, don't fret. Here are five effortless and unexpected ways to salvage it.

Christmas trees, once decorated and brightly lit, are the penultimate holiday decoration, but authentic pines lose their brilliance fast without any nourishment. Plus, they are major fire hazards without regular hydration. But watering one requires a lot of sliding around on the floor, and it can be hard to tell how much water is in the bowl beneath the dark, prickly branches. These five hacks can help!

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Look, I'm no food snob. I once dedicated an entire day to eating only deep-fried things (butter, Twinkies, Oreos, pickles) at the Minnesota State Fair. But even I draw the line at instant mashed potatoes. I mean, why bother? It's not that hard to make perfectly delicious and fluffy mashers yourself.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Update: After playing around with our new iPhone 6 and 6 Plus over the last couple weeks, it occurred to me to see if my DIY stylus would work with these new devices. I'm happy to report that it does, just as expected.

It's one hell of a device, but the Samsung Galaxy S5 is still susceptible to the many hazards that other smartphones are prone to: theft, cracked screens, poor battery life, and particularly, overheating.

You know you've had a long day when you head home with a headache, back pain, and eyes so sore they feel like they might roll out of your head. Turns out your medicine cabinet isn't the only place you can find help—instead of popping painkillers, just open up your wallet for instant pain relief.

Fresh salsa is so tasty. Who can resist the robust mix of spices, the mouth-watering heat of jalapeños, and the juiciness of fresh tomatoes? Alas, I don't always make my own and have to get the pre-made stuff.

While we've already covered several good ways to tame the itch of a mosquito bite, you're much better off preventing them from biting in the first place than dealing with the itchy aftermath.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

It seems nowadays the word "easy" has taken on an alternate meaning. When I see "easy," I expect a quick and painless process, but when it comes to flashing or installing a custom ROM, easy means anything but.

A well-executed jack-o'-lantern can be pretty damn impressive, but some of us lack the carving skills necessary to pull it off and end up disappointed. Sometimes you just don't want to put in all the time required to cut open a pumpkin, gut it, and chisel an elaborate face or cool design into it.

Welcome back, my aspiring hackers!

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

I'm sure that there are plenty of people out there who have no idea what a plague doctor is/was, so I'll start with an explanation.

Sorry gentlemen but unless you like wearing skirts this pranks & cons how-to video is mostly for the ladies. Watch and learn to cheat on tests using low cut skirts and well placed cheat cards to achieve academic glory. Boys maybe be able to use this cheating technique with other clothing so be creative and enjoy all the straight A's. Follow along and con your teachers into thinking you really studied for the test. Use a skirt to cheat on exams.

This Sports video tutorial shows how to hit the golf ball as a draw. Frank demonstrates in this video how to hit a draw. It is very easy to hit one. What you should aim to achieve is an inside outside swing. He has laid out three clubs on the ground. One club is on target line. The other two clubs are parallel to each other and are on swing path line with the ball placed in their middle. When you swing your club back, go through the two clubs winding up. In the unwind portion, your club shoul...

This video shows the process of removing scratches from an iPod. The video demonstrates the best way to remove scratches not only from the metal but from the front viewing screen also. One starts with the recommended Weiman Metal Polish and 100% cotton cloth. To achieve best results and a scratch free finish, the video also gives tips like shaking the polish before use. Your iPod as well as any other similar piece of equipment will look scratch free and as good as new by following these simpl...
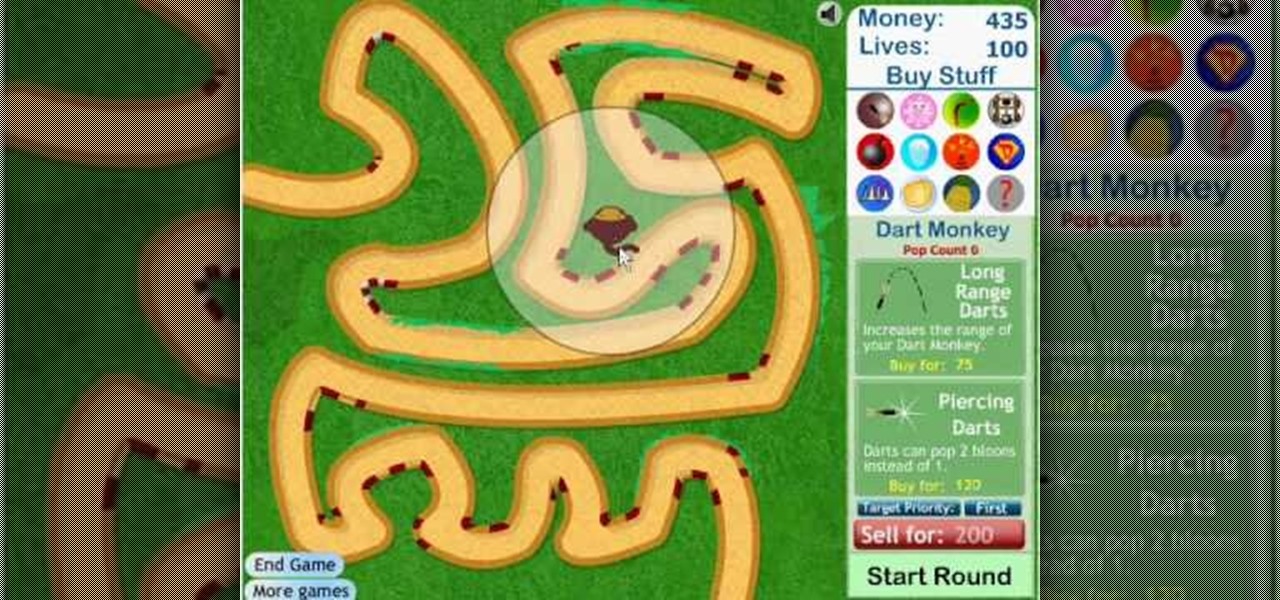
Bloons Tower Defense 3 is a flash game from Ninja Kiwi. Learn how to hack Bloons Tower Defense 3 with tricks and cheats. Watch this video tutorial to learn how to hack Bloons Tower Defense 3 (09/27/09). You just need Cheat Engine 5.5.

How To Sing Without Lifting Your Larynx

This 3D software tutorial shows you how to use the affect region modifier in 3ds Max. The Affect Region modifier is a 3D Studio Max surface modeling tool, primarily used with vertex sub-object selections while surface modeling. With Affect Region, transforming a selection of vertices can also transform vertices in the region that surrounds the selection. This can help you form a bubble or indentation in the surface of an object. The easiest way to see this modifier’s effect is with a shallow,...

In this video you will see how to heel toe shift and double clutch shift while auto racing with Gary Sheehan. Both methods are used in racing but can be applied to regular street driving as well. There is no verbal instruction, but you can get the idea just from watching Gary's feet. More experienced drivers will pick up how to heel toe and double clutch from this video better than beginners. Heel toe and double clutch with Gary Sheehan.

In case you missed out on slumber parties or your mom never taught you how, this video demonstration will show how to braid pigtails. To braid two simple braids, divide the hair into two groups and comb. Divide each group of hair into three sections and push the side section between the two remaining sections, so that the right section moves to the middle and then the left one moves to the middle. Continue until all the hair is braided and secure it with a hair band, then repeat

Tired of boring old ponytails? This video demonstration shows how to make a unique twisting ponytail on curly hair. Gather the hair into a high ponytail and secure it with a hair band. Now, pull the hair band up, split the hair in two, pull the ponytail over and through the opening that was created, and tighten the hair band. In order for the hair to remain neat, use hair spray and smooth it down with the hands. Watch this video hair styling tutorial and learn how to create a twisting ponytai...

The coiled updo is a unique alternative to traditional and stuffy buns. For a head of bouncing coils, begin by dividing the hair into 4-5 sections. Tightly