A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.

Fans of Doctor Who know that the sonic screwdriver is the ultimate tool. It can unlock doors, turn on lights, detect life forms, solder wires, and sabotage weapons.

I think it's fair to say that every maker yearns for a 3D printer. You can replace circuit board connectors, fix your glasses, create ski grips, and make whole machines out of printed plastic parts—even a 3D printer. But without a 3D printer on hand, you can always resort to Sugru.

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.

In the first part we differentiated the two types of control, mental and physical. In part 2 we will dig deeper into Physical crowd control and analyze examples that are present today.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.
Does this video prove that otherworldly intelligent life has visited Earth? No. It does not prove anything other than there are designs ‘etched’ onto the surface of a field. Does the video immediately above prove that otherworldly intelligent life hasn’t visited Earth? Yeah, you saw it coming; no, it proves nothing more than humans are able to ‘etch’ designs in a field of grain.

It's once again Monday, which means it's time to highlight some of the most recent community submissions posted to the Math Craft corkboard. Since two of these posts were on polyhedral versions of M.C. Escher's tessellations, I thought we'd take a look at building a simple tessellated cube based off of imitations of his imagery.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

Kaplan University nursing alum Debra Eppley was already working in the nursing field when she started her RN-to-Bachelor of Science in Nursing completion program (RN-to-BSN program). Kaplan University’s flexibility and support offered her the opportunity to complete her degree online while continuing to work. Once she completed her Bachelor of Science Nursing online, she was able to make a career move that not only increased her salary, but also her level of job satisfaction.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

This week's FIGRR is all about games that are old-new (or new-old, if you like) school. Each celebrates a different vital, yet largely taken for granted, aspect of video game history in the decidedly new-school world of indie games. Their titles betray them. Blocks That Matter is all about blocks. Recettear: An Item Shop's Tale is all about item shops. Neither are particularly sexy aspects of gaming, but both are ubiquitous elements of great games that can stand on their own.

Difficulty Level: Moderate Photoshop Skills Photoshop isn't just for zapping zits and adding freaky colors to sunset pictures! You can use it for fun, altered-reality pictures, too. If you have a tripod and some friends, you can combine many exposures as separate layers and using layer masks, make one super cool image from many slightly cool images.

What's more fun? Winning against your friends or winning against others with them? It's an age old question, and in video games, the former one-on-one multiplayer has been the norm. But cooperative multiplayer has made a comeback, with Halo and Diablo II starting the trend, the first mainstream shooters and RPGs with great co-op modes. And now good local and multilplayer co-op games are available in almost every genre.

A woman from space that who has been dead hundreds of years has been resurrected on the internet and you're the IT assigned to fight the viruses attacking her. Child of Eden is a mesmerizing musical game, with fluid animations, great game play, and lots of replay ability.

Real-time strategy (RTS) was the most popular genre in PC games at one time. It put Blizzard on the map—one of the biggest game developers in the world. And it buried the once venerable turn-based strategy genre, the only survivor being the Civilization series. But like hair metal in the late ‘80s, RTS reached its saturation point. Many bands (games) were too similar and used ornamentation over innovation. Suddenly, the fans left. From ’95 to ’03, Command & Conquer releases were more like new...

If you found the world renown Body Worlds exhibition gnarly and perverse, perhaps you'll find this latest parade of plastination a little less so—considering we don't share the same DNA as these specimens of jerky-in-the-name-of-science. The Koerperwelten der Tiere—or Animal Body Worlds–doesn't showcase preserved corporal matter, but rather 20 odd plastinated mammals, currently on display at the Cologne Zoo in Cologne, Germany.

Here we have a unique piece of work. Miley Cyrus, the girl that started out as a 12 year old acting on Hannah Montana, is now 17 and showing some skin. Do we care? Apparently, parents do. So it seems as if if Cyrus wasn't able to do what she wants in her music videos because of these complaints parents are making. Of course, those complaints are natural, I mean, 8 year old girls look up to her, which really pressures her being a role model.

Jersey Shore's pickle-loving, drunken little ball of fun has captured the affection of many, as well as a fair share of haters. According to today's Wall Street Journal, Snooki and other Jersey Shore characters have surpassed Lady Gaga in popularity for Halloween costumes of 2010. Go Snook. (Not too surprising. For lots of ladies out there, the more revealing the costume, the better.)

Not long ago in Rome during a Master’s Tennis Tournament something remarkable happened. In a tightly contested game, American Andy Roddick challenged a linesman’s call on a ball hit by his opponent. The remarkable thing about this incident was that Roddick argued against his own interest. He insisted that the opponent’s ball had landed inside the line and that he, Roddick, should NOT be awarded the point. Spectators applauded as if they’d witnessed a miracle. Imagine! Sportsmanship in a profe...

Equipment list for the low budget crowd Let's assume you have a script (not just an idea) and have gotten your pre production out of the way. These are both incredibly important and should not be taken lightly, especially when you have no budget. So you have an awesome film and all of your ducks are in a row, what do you bring with you to the shoot... or what is really necessary?

There are no spoilers in this writing, read without worry. Finished Episode 3 of Alan Wake yesterday, impressed by different reasons. I originally bought the game for the possibility of great story, dialogue, and voice acting. That part of the game has been disappointing. What has stood out from playing episodes 1 to 3 is the level design and game play.

I’m terrified of you. Yes, you- Director of Photography (DP). Your framing is beautiful, but your lighting could kill me, and my career. I am the Makeup Artist, and I don’t believe we’ve met.

Both on and off the set, the Gaffer or Chief Lighting Technician is one of the most important positions around. Though the average movie goer most likely has no idea the job even exists, they probably don't know what 99% of the other crew is/does either.

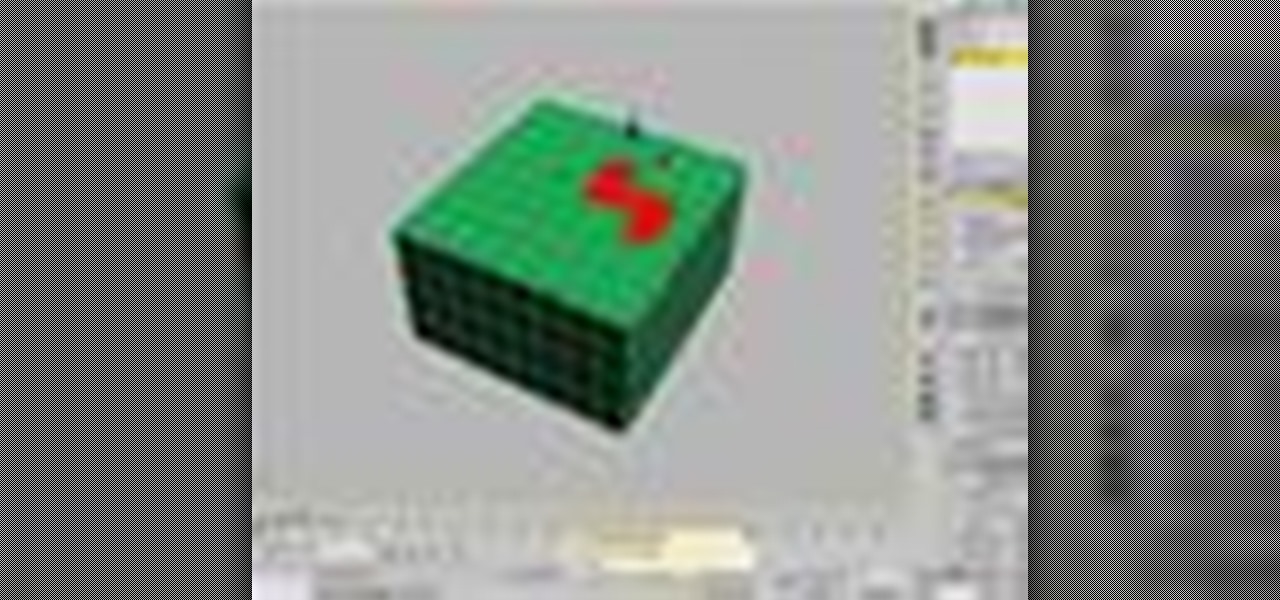
Cap Holes is a great modifier for modeling as well as making images in 3ds Max. The 3D Studio Max Cap Holes modifier builds faces in the holes in a mesh object. A hole is defined as a loop of edges, each of which has only one face. For example, one or more missing faces from a sphere would produce one or more holes. The modifier works best on reconstructing planar holes, but can do a reasonable job on non-planar holes as well. See how to use it in conjunction with a slice modifier, it’s a goo...

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

The war on dehydration is a commercially burgeoning marketplace. An increasingly sophisticated consumer population hoping to conquer everything from 26-mile marathons to vodka shots is deconstructing every functional remedy in the fight to quell the effects of severe dehydration.

It was brought up a while back in a Community Call to Arms that *math* is handy for encryption (and let's face it, everything) so let us go over things you just have to know. "In its simplest meaning in mathematics and logic, an operation is an action or procedure which produces a new value from one or more input values."[source]

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

This is a game for however many people would like to participate. The game is simple. Everyone plays a hand of poker, whoever has the lowest hand has to make a concoction. The person who loses has to role two dice. Each die and the six numbers on it corresponds to a different list of ingredients that must be mixed into a shot glass to drink.