As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

I have always favored a neat and tidy Home Screen on my iPhone, and one of the best ways to achieve that is by removing all the app, folder, and widget names. With a few workarounds, you can do this on iOS 17, but Apple finally just gave us an official feature on iOS 18 to hide app, folder, and widget names on the Home Screen. And it also works for iPad on iPadOS 18.

After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.

As if teasing its own smartglasses weren't enough, augmented reality gaming developer Niantic gave gamers a glimpse of how 5G speeds can revolutionize how they play mobile games in the near future.

While iPhone cameras these days are downright impressive, the same can't be said for the Camera app. In true Apple form, Camera is as simple as possible, forcing you to go third-party for pro-level features. With iOS 14, however, Apple adds a little extra professionalism, allowing you to lock focus and exposure separately.

Sure, you could leave a random monolith in Utah and get some notoriety for your street art. Or, you can let others put your art anywhere they'd like with augmented reality so they can appreciate it where they are.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Once again, Samsung has certified its flagship Note series with an IP68 rating. With this rating, the Galaxy Note 20 and 20 Ultra have some degree of dust and water resistance.

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.

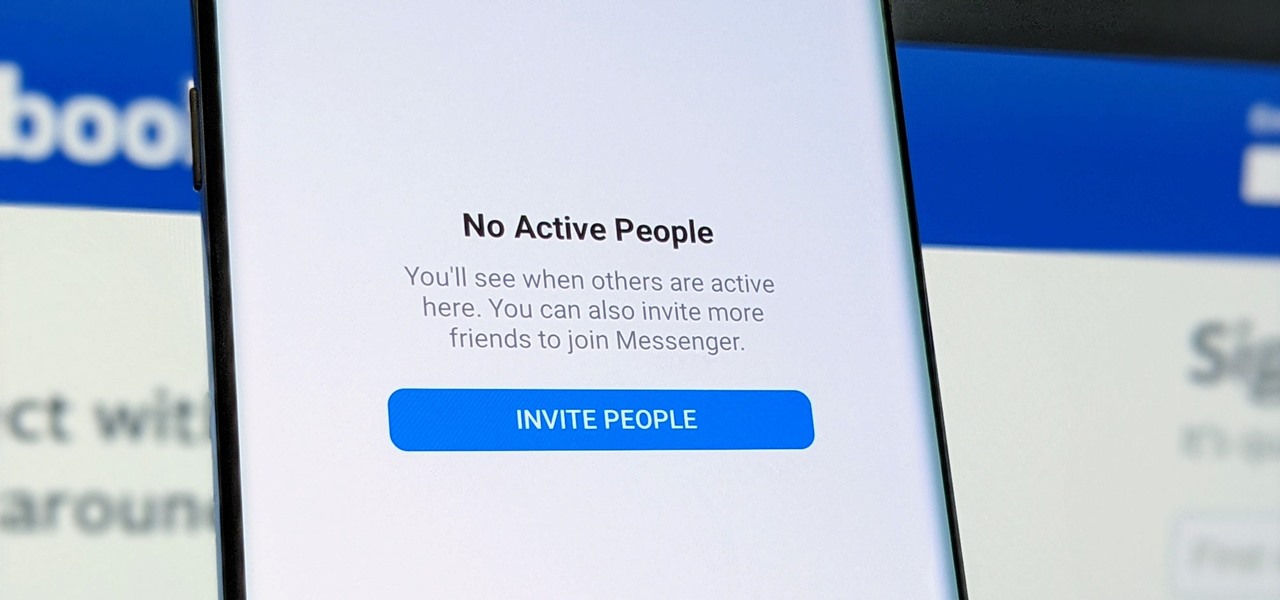
Facebook Messenger's user base has grown so much that it has taken over text messaging as the primary contact method for many people. However, sometimes you might want to hide your online status from specific contacts and appear offline to others. There's a neat little trick you should know that can help you achieve this.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

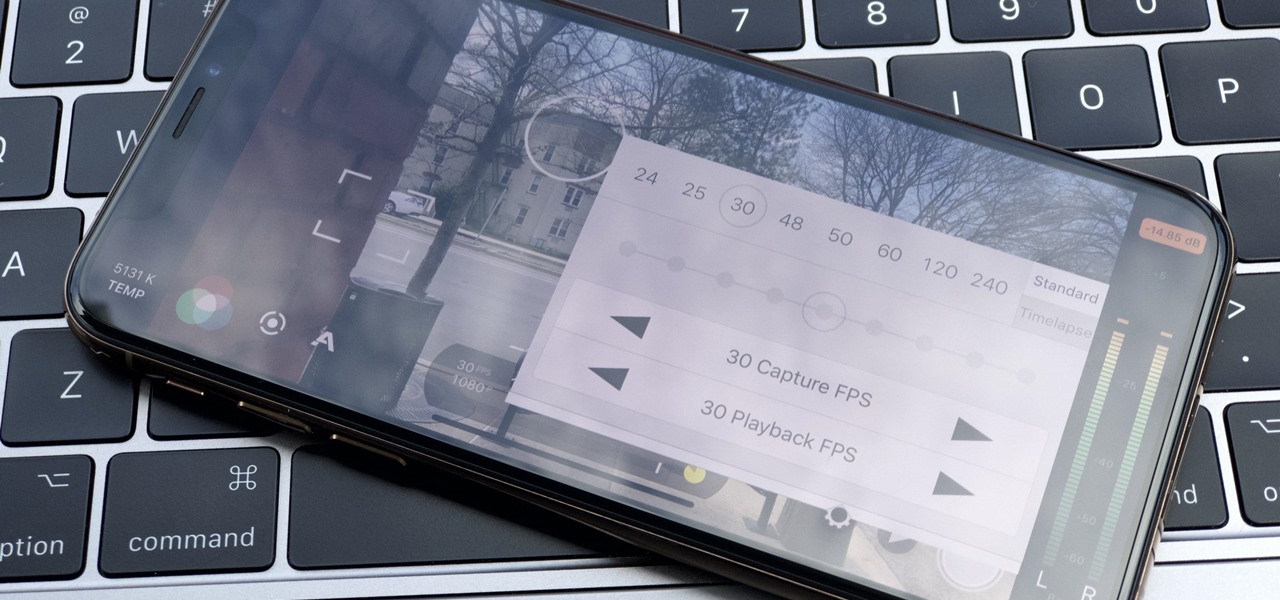
The days of bad smartphone videos are long gone. Your iPhone or Android phone is a capable video recorder, even offering different frame rate options in the native camera settings. Filmic Pro makes things a little simpler, however, and adds additional controls you wouldn't find on your device alone.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

For some Android users, this guide is sacrilege — but for others, iOS is just an attractive operating system that can be admired without feeling like you've betrayed your own phone. If you're one of those Galaxy Note 9 owners that have peeked across the aisle and desired an interface as clean as the one on the iPhone XS Max, you can configure your Note 9 to look like its rival with some tinkering.

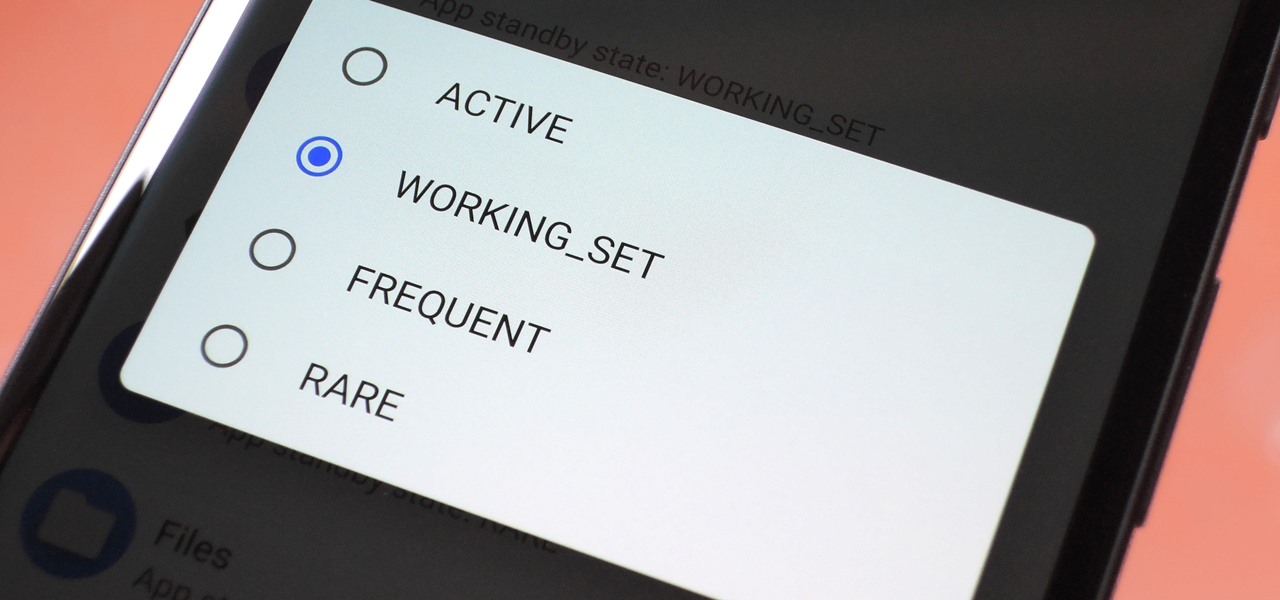
Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

After the first image leaked of the upcoming successor to the Razer Phone, many were taken aback by its design, specifically how familiar it was. Last year's Razer already stood out with its boxy design and large bezels, and many thought the successor would change this. It didn't. But what if the reason for the familiar form factor is a project they teased earlier in the year?

The world finally received its first official look at the iPhone XR, XS, and XS Max, Apple's 2018 suite of smartphones, on Wednesday, Sept. 12. If you're someone looking to get their hands on one, two, or three of these new iPhones as soon as possible, you'll need to know all of the important dates so you don't end up missing out to others ahead of the line.

Like an overbearing mother, Apple will constantly nag you through annoying red bubble alerts about iOS updates that are ready to install. Fortunately, you don't have to take this issue lying down, as there are ways to prevent your iPhone from receiving OTA updates and their corresponding prompts, regardless of whether your device is jailbroken or not.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

After first being announced at Mobile World Congress 2018, the ASUS ZenFone 5Z will finally be coming to the US. Deemed an iPhone X clone by some, there is more than meets the eye when it comes to this flasghip. While it is similar to the iPhone X, in some ways, it improves on the design.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

On Wednesday, the tech world woke up to fairly shocking news with the announcement that AT&T would be the exclusive wireless carrier for the forthcoming Magic Leap One, as well as an investor in Magic Leap.

LG is really coming strong at the flagship smartphone market in 2018. They have already released three new flagship caliber smartphones this year: the V30S ThinQ, V35 ThinQ, and the G7 ThinQ. But LG isn't done with flagship phones yet — they've just announced the V40 ThinQ.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.