If you want free Poké Balls and eggs when playing Pokémon GO, you can find them at PokéStops in variation locations around your city, which are marked with towering blue icons on your map. Once you're at Level 5, they'll also grant you Potions and Revives to help you in your battles against other trainers, so they're definitely something you should be visiting whenever you can.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

It was definitely a shocker when Microsoft proposed cross-network play between the Xbox One and PlayStation 4 last month. After all, Microsoft and Sony have been competing for the same user base for more than a decade now, and this new feature might actually decrease console sales as a whole.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.

Winter and the winter holidays in general are a time of joy, laughter, and love… but not for everyone. For some, the stress of preparing for parties, hosting family, traveling long distances in bad weather, and just keeping up with your daily routine can start to bring you down.

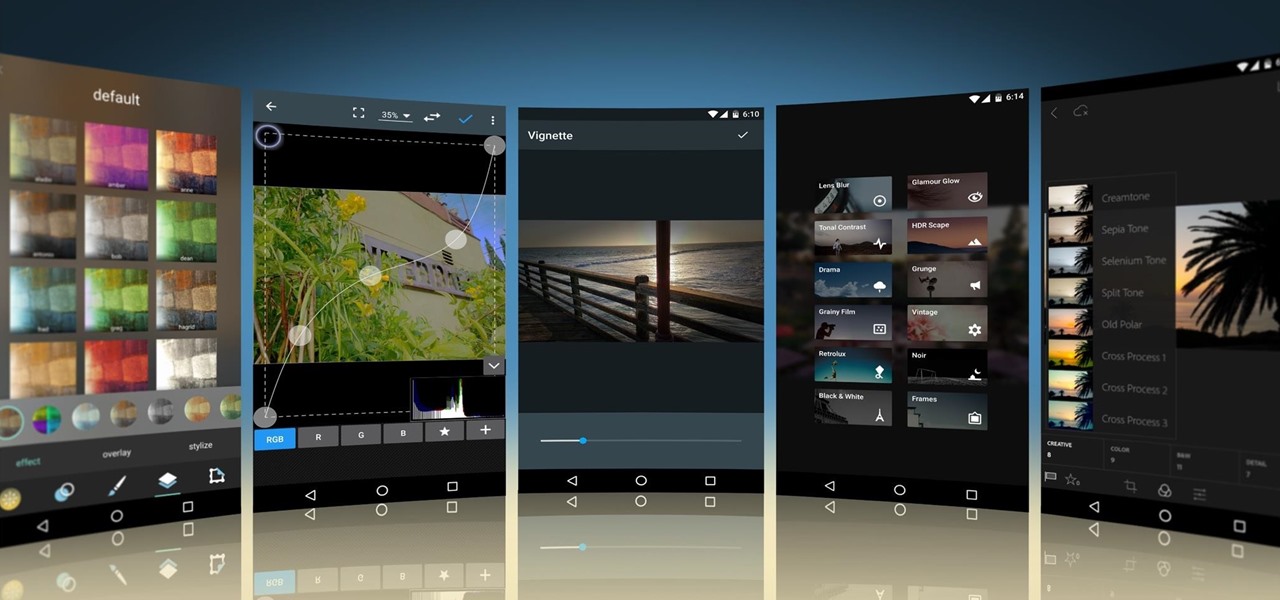
Smartphone cameras are so good nowadays that there's almost no reason to own a point and shoot. Once the megapixel spec race was finally settled (hint: more isn't always better), manufacturers started focusing on the quality of their camera sensors, which has led to a huge jump in color accuracy, dynamic range, and image clarity.

Nothing signals the end of fall and the start of winter like hot, seasonal drinks. And while pumpkin spice lattes may be the flavor of the day, and eggnog the Christmas favorite, one seasonal drink stands apart in my eyes: mulled cider.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

In 1987, two brothers, Thomas and John Kroll, began work on an image editing software, which was eventually acquired in 1988 and released to the world in 1990 by Adobe. That software was Photoshop 1.0, initially exclusive for the Macintosh platform. Over the years, Photoshop became a great wizard of image editing and gained application rockstar status.

Nothing makes my stomach growl and my mouth water quite like the smell of roasting chicken. It's a pretty universal reaction, too—there's a reason every grocery store places its rotisserie grills and delis near the entrance, after all.

Dumplings have been around for centuries in various forms; spätzle, as well as chicken and dumplings, are dough-y dumplings with no filling, whereas Russian pierogis and Chinese jiaozi are dumplings that contain meat, vegetables, or both.

In my opinion, there is no candy greater or more timeless than Sour Patch Kids. They're the ultimate treat: sweet and refreshing, yet sour and tangy. These contrasting flavors are what make Sour Patch Kids perfect for the people of all ages—especially your kids. So let's make dishes that incorporate this awesome candy into your cooking rotation!

Many people deal with motion sickness on a daily basis, and if you're reading this, chances are you're one of them. Kinetosis can make your stomach roll, your entire body sweat, and make you feel fatigued and dizzy at even the slightest movement, whether it's related to carsickness, seasickness, or airsickness. And let's not forget the worst part—vomiting.

Google now has an iOS version of Android Wear, so if you own an Android smartwatch (Moto 360, ASUS ZenWatch, Huawei Watch, LG Watch Urbane, Sony SmartWatch, etc.), you can finally connect it with your iPhone.

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

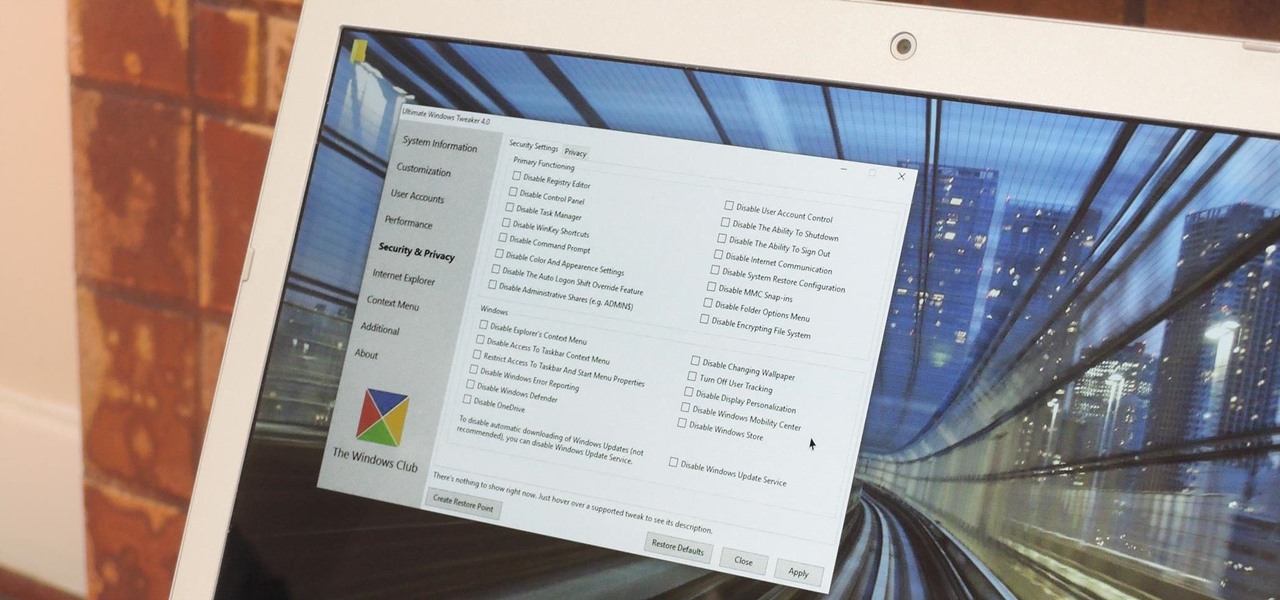
Every time Windows gets a significant update, the vast majority of existing tweaking utilities become obsolete. For every option that you fine-tuned with one of these tools on Windows 7 or 8, there's a change in the registry or system settings that cause your tweaks to now point to a dead end. This was definitely the case with Windows 10, since there were so many sweeping changes that very few existing options carried over.

In my opinion, spices are the key to a successful kitchen. With a healthy array of spices and spice mixes, you have the foundation for nearly any dish that you want to make; the culinary world is your oyster. With a depleted cupboard of spices, however, nearly every recipe looks intimidating and unattainable.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

In the realm of Android mods, none is more powerful than a custom recovery. This is installed in place of the stock offering, and it lets you back up your entire system, flash mods, and install custom ROMs.

If you're feeling stressed, there are many home remedies you could use for relief. Meditation, yoga, acupressure, an ear massage, more sleep, shower soothers, playing video games… the list is endless. But a lot of these methods require a significant amount of time, so what do you do when you need immediate stress relief?

There are tons of greasy drippings that can be used to flavor up any dish, but none will ever be more delicious than animal fat. The bigger and fatter the animal, the juicier and tastier their fat is. For those of you who have had your fill of bacon-anything, here's your next obsession. It's called caul and its very existence will divide those that are serious about their animal fat flavoring from the pretenders.

The wait is over. The Samsung Galaxy S6, arguably the best Android phone of this year, has just launched. There was already a lot of hype about this super phone—its looks, its specifications, and its other functions have been under the microscope for quite some time. It will not be a good idea that you take this phone in your hand and use it in the same fashion as you have been using your other phones in the past.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

Among the many gifts that Italy has bestowed upon the world, culinary and otherwise, pesto stands alone. The exact birthplace of pesto, that herby sauce made of pine nuts and olive oil, is an area of Italy called Liguria, whose microclimate is particularly kind to basil, one of pesto's key ingredients.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

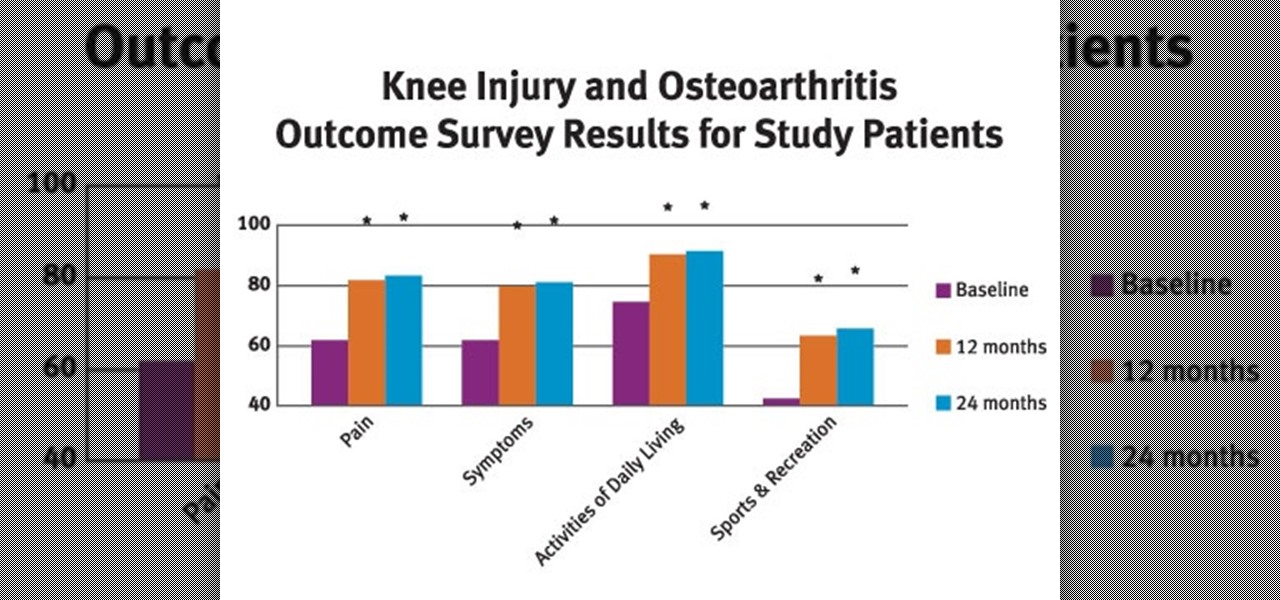
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis.

There are many, many home remedies out there for relieving itchy mosquito bites. Everything from mud to banana peels and basil leaves to Alka-Seltzer tablets can help curb the itch. But before you even have to resort to any of those methods, you should be thinking about prevention. Wearing white clothing can help to keep mosquitoes aways from your skin, and there are many plants that will help mask your mosquito-attracting smell. But there's even more ways to keep those bloodsucking bugs away.

For some, there's nothing more thrilling than carrying an armful of bags while wandering the mall; for others, there's nothing more annoying. No matter what category of shopper you fit into, the truth is that you aren't always in control of what you buy.

Android enthusiasts have their own opinion as to whether you need antivirus software on an Android device. This debate will never end, provided that Android malware is in existence. This guide is not here to say, "Yes, you need antivirus," or "No, you don't." It's to give you all the facts, so that you can make a decision as to whether or not you need antivirus on your Nexus.

The new Google Now Launcher has hotword detection and one-swipe access to Google Now, but personally, it's not enough to convert me away from other launchers like Apex or Nova. Just because it's Google's official launcher for stock Android doesn't make it better than all the rest.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

While Siri has never been my favorite, after using her in the new iOS 7, I have definitely become a fan. If you want to know why, check out the newest cool features that Siri has to offer!

To make soap, you need fat, and if you've seen Fight Club, you're probably well aware of where soapmaker Tyler Durden got his fat from. Liposuction clinics. If you're not willing to go that far for a perfect bar of homemade soap, you can just use some drain cleaner and America's favorite food instead—bacon!