Samsung decided to jump into the foldable category early, announcing the Galaxy Fold in February 2019. After a major hiccup, Samsung released the phone four months later to praise. But Samsung's not finished with foldables, as the new Galaxy Z Flip is just on the horizon.

We all want to be healthy, but in practice, it can be tricky, especially from the fitness angle. Our lives seem busier and busier, which makes hitting the gym quite the challenge. What if we told you there was a real way to work on your fitness in the comfort of your own home — in just seven minutes a day? All you need is a chair, a wall, and a 7-minute workout app.

While we just called the Apple Watch Series 5 the "best lifestyle assistant and fitness wearable you can get," it doesn't mean that it's the model you should get. Whether you're shopping for yourself or someone else and are on a tight budget, the Series 4 offers the majority of features that the Series 5 does at up to $300 less than the newer comparable models.

In a bold move, Samsung has decided to forgo the Galaxy S11 moniker and jump straight to the S20. Perhaps it's marketing for the new 20:9 aspect ratio and 120 Hz display, or maybe it's just the fact that it's releasing in 2020.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.

Apple Maps has had a rough lifecycle. After completely dropping the ball during its inception, Apple has been slowly improving its usability and feature set. After six and a half years, users still prefer third-party apps in iOS 12 over Apple Maps, with Google Maps stealing a large 67% market share. But iOS 13 for iPhone may finally close the gap.

The worlds of augmented reality and virtual reality are closely linked in many ways. That means it's smart for AR insiders to keep a close on new developments in VR. If you have been paying attention, you know that Oculus CTO John Carmack is one one of the most important thinkers in the VR space.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Whenever the name Magic Leap comes up, the talk inevitably seems to turn to the company's big-name backers and "unicorn-level" amounts of cash poured into the venture. And if it's not that, observers tend to focus on the company's market strategy and overall prospects.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

Though more well known for their OLED displays and advanced cameras, Galaxy phones like the S8, Note 10 & 10+ and S10 series are a force to be reckoned with when it comes to audio. In fact, flagships from the S9 on up feature AKG-tuned stereo speakers, along with a slew of software enhancements that make listening to music a truly pleasurable experience.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.

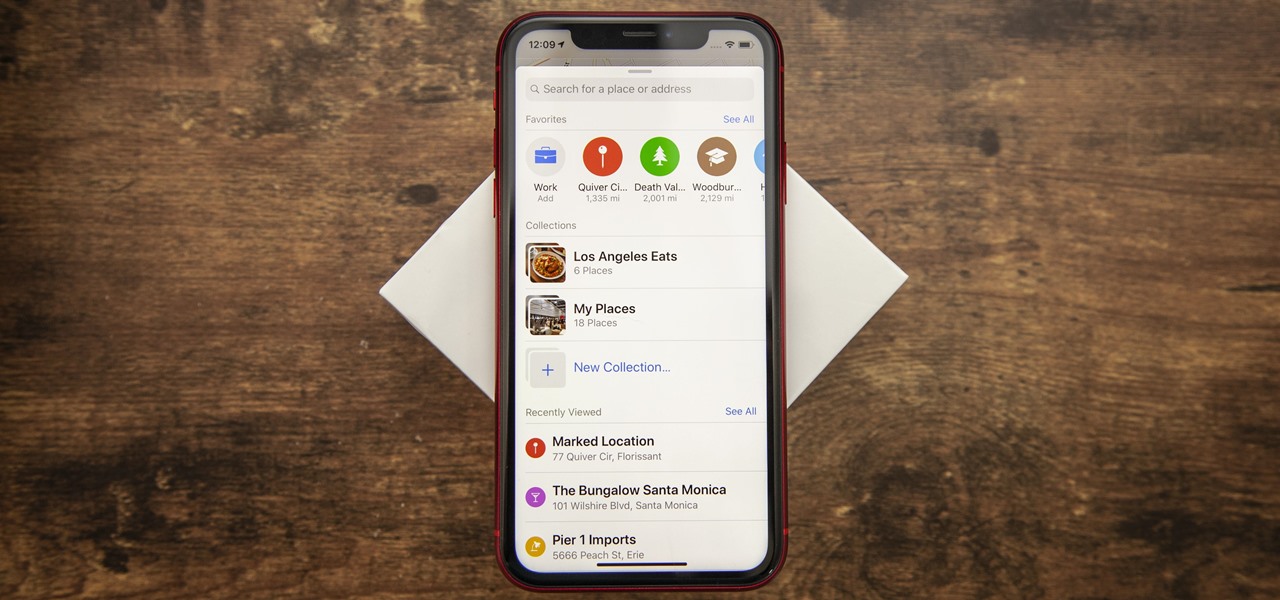
You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

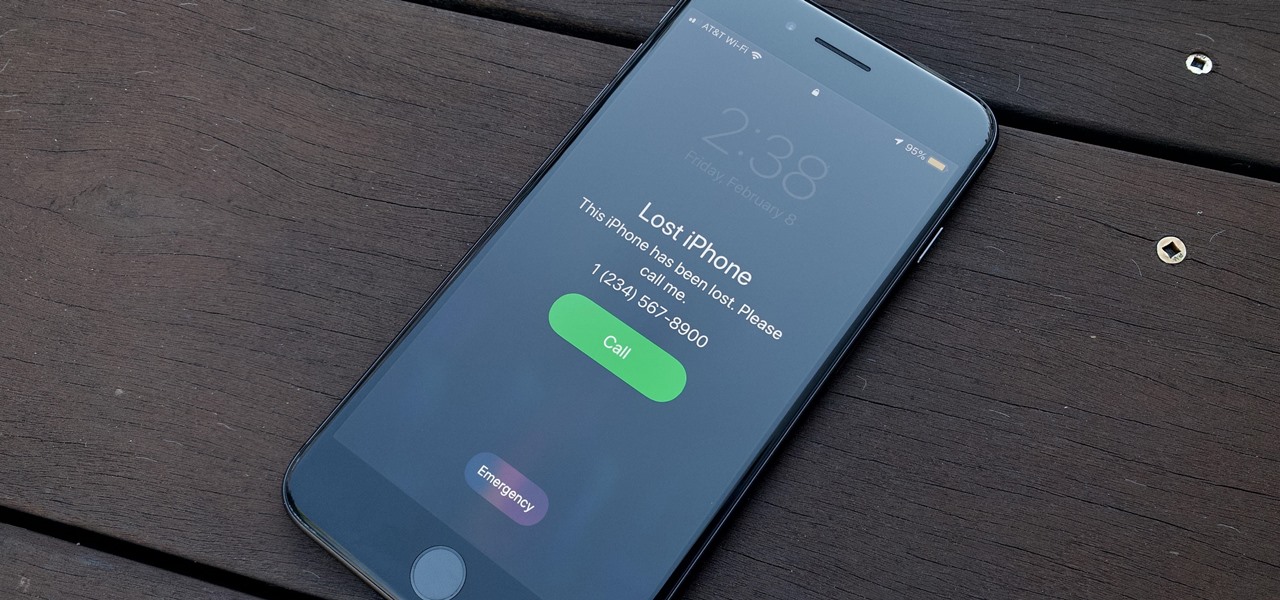
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

We recently set out to find the best phones for people whose primary usage revolves around social media apps like Facebook and Instagram. Samsung, Apple, and Google were the three brands that made our top five, and while the latter only had one finalist, the two bigger OEMs had a pair of phones each. What struck us, however, was that Samsung's phones edged out Apple's not once, but twice.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

There are more than a few subscription-based movie streaming apps available for Android and iPhone, each with different benefits and varying pricing plans. Needless to say, it can get expensive fast if you sign up for multiple services because you can't decide on what's best. Hopefully, we can help you out with choosing the right video-on-demand app to spend your hard-earned dollars on.

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

No matter how good a display is, the idea of perfect color calibration is subjective — some prefer warmer more saturated colors, while others prefer the calmer cooler side of the color spectrum. It is almost impossible to create a single color calibration that everyone can agree on out of the box. The display on the Pixel 2 XL was specifically calibrated with a more realistic color profile in mind.

Samsung isn't known for its timely rollout of major Android updates, and Android 9.0 Pie won't be an exception. If we go by their Oreo update timeline, we can expect Android Pie to officially touch down for the Galaxy S9 and S9+ sometime around November, with the final version rolling out the around the first quarter of 2019. But a leaked version of the beta has already hit the internet.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

While the iPhone XS actually comes with a smaller battery than the iPhone X, Apple claims it, along with the XS Max and XR, offer users longer battery life than last year's first Face ID model. While that may be true, your new iPhone still ships without meeting its full battery-saving potential. There are, however, steps you can take to make sure your X, XS, XS Max, or XR makes it from morning until night.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

Apple's new iPhone XR, XS, and XS Max are sure to be hits this year. Of course, that means plenty of hungry customers are looking to sign up for a model once preorders begin on Friday, Sept. 14, for the XS models, and Oct. 19 for the XR. Luckily, there are preemptive actions you can take right now to avoid waiting outside an Apple Store overnight or getting kicked out of the preorder queue online.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.