Back in August, Google unveiled a new YouTube Gaming service meant to compete with e-sports streaming sites like Twitch. At its launch, the service was capable of broadcasting desktop PC gameplay, but when it came to the mobile segment, users were only capable of viewing streams hosted by others.

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.
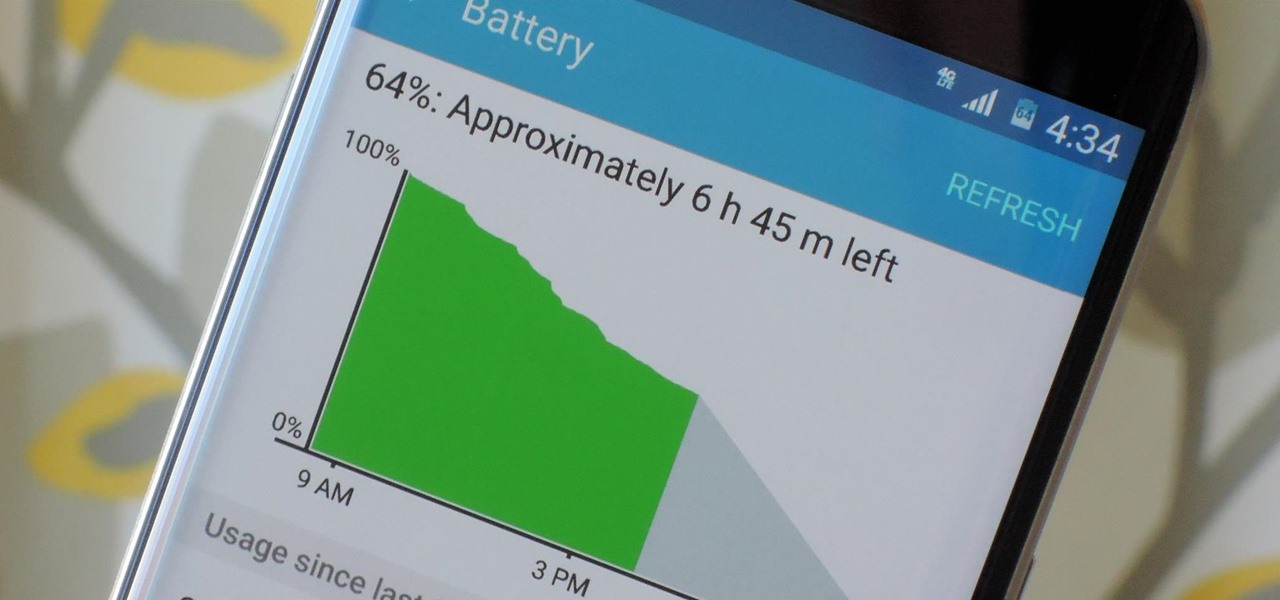
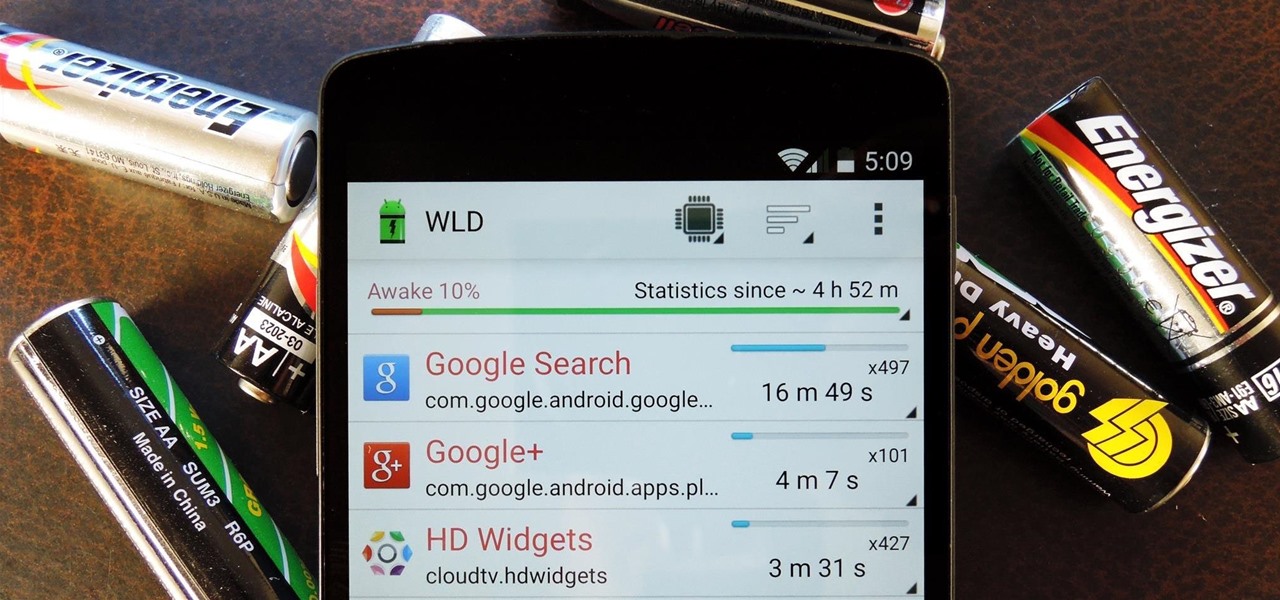
Smartphones have otherworldly specs these days, so it's relatively uncommon that you hear someone complaining about display resolution, build quality, or general speed and performance. At best, these are secondary concerns, with the number 1 issue almost unilaterally being battery life.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Most mobile games have moved to an online-only format, meaning you need to be connected to the Internet in order to get any kind of multiplayer action going. This is great when you're at home on Wi-Fi, but when you're out and about, slow and inconsistent data speeds can cause serious lag. Or worse yet, you may be nearing your monthly data cap!

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

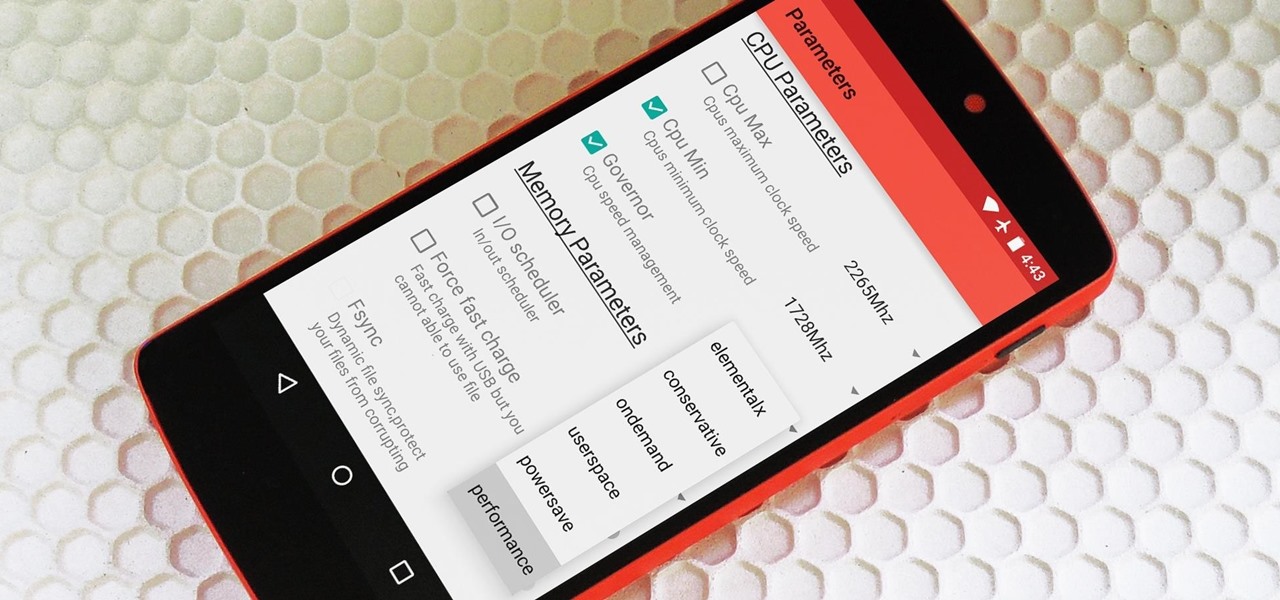
Deep down at the core of Android lies the system kernel, which serves as a bridge between software and hardware. Custom kernels can be installed in place of the stock offering, and these are generally optimized for better performance or increased battery efficiency.

It's 3 a.m. and you're wide awake—your mind is running wild with worries, workplace stress, and panic about the day that lies ahead. How can you possibly slip back into sleep and snag a few more hours of rest when you're so anxious?

The 13-megapixel camera on the OnePlus One is capable of taking some pretty impressive shots, but the stock CameraNext app doesn't do the hardware justice. When compared to the camera app that ships on the ColorOS version of the One, you can immediately see an increase in clarity and low light performance.

With over a billion monthly active users, it seems that Facebook is nowhere close to being dethroned as the most popular social media service in the world (sorry, Ello). While their stats may be impressive, it doesn't mean that Facebook is as good as it can be.

Sitting in a cubicle and never seeing sunlight during the workday is unpleasant to even think about—and sitting in a flourescent-light cube can have terrible effects on both our work performance and overall attitude. Yet there are ways to counteract the effects of cubicle sitting, even if you can't sit in a sunny office or work from home.

We all carry a bit of anxiety around with us. Is our boss still annoyed because we could barely stay awake in yesterday's pre-dawn meeting? Will our friend hate us forever because we forgot to call them back two weeks ago? Whatever worries pop up in your mind, whether they're monumental or insignificant, it can be hard to quiet those nagging voices, but you can shut down your nonstop mind with a bit of relaxation, distraction, and action.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

Google's Android L developer preview has given Android a more refined look, with developers excited to update their apps with the new Material Design UI. While some apps are slowly getting updated, QKSMS (QK for quick) is a 3rd-party text messaging app that was built with Material Design in mind.

I may not be a parent just yet, but I've dealt with enough worrisome mothers to know that keeping a watchful eye over your child is of the top-most importance. Since most people cannot afford to stay right by their child's side 24/7, developers are always looking for ways to make the pain of stepping away a little less stressful for parents.

Accessing your favorite and most recent contacts on your iPhone is now faster than ever before, thanks to the iOS 8 update. Just double-click your Home button, select your contact above the app switcher menu, then choose how you want to contact them.

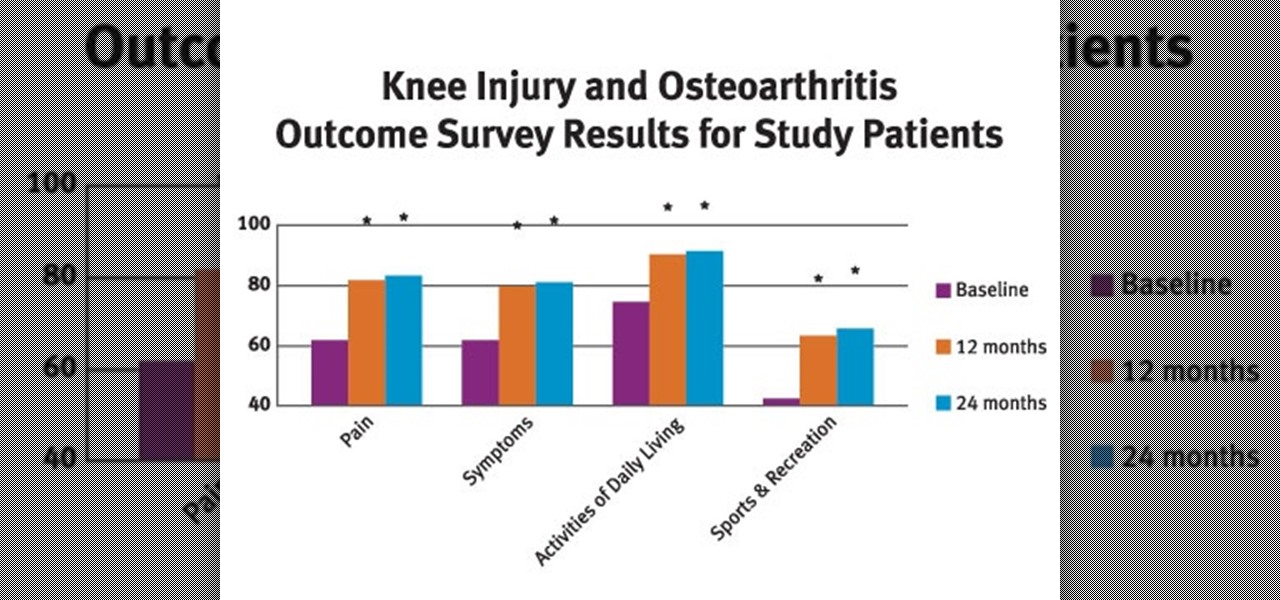
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

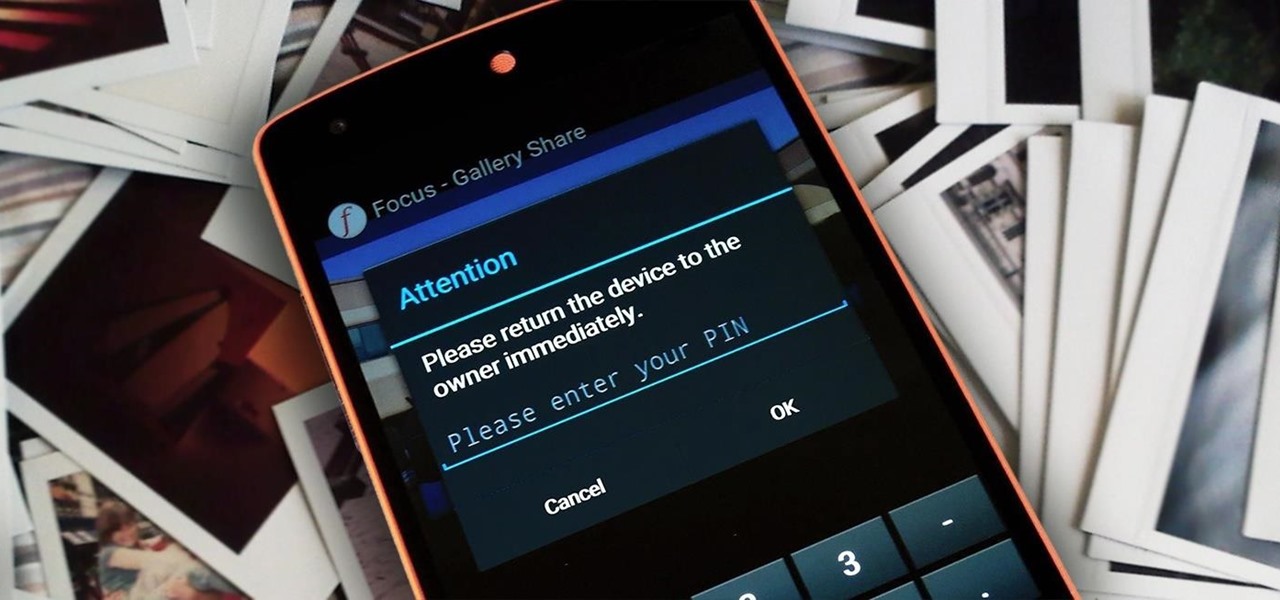
You have a cool picture that you want to show someone, but when you hand your phone over, they start swiping through all of your photos. Surely, you've encountered this scenario before. I definitely have.

If you've ever had issues charging your iPad, iPhone, or iPod touch, like most other Apple products, the culprit to blame is usually a frayed or damaged cable. It's a common design flaw due to the thinness of the cords and the weak sheath surrounding them — but that's not always the problem.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

Android uses a set of permissions that apps can request to perform certain actions, and you're notified of these permissions each time you install an app. The problem here is the fact that you aren't given any built-in way to deny apps these permissions (although Danny just showed a workaround for this).

Just what are probiotics and why are they so good for you? Probiotics are "viable microorganisms" that can confer lots and lots of health benefits if they reach your intestine while they're alive. You may have heard them described as "friendly bacteria."

There are spontaneous times in everyday life that just scream to be recorded on video. The crazy guy yelling obscenities on the bus. Your favorite actor at the supermarket check-out register. Maybe even your kids just being super adorable.

When the Nexus 5 debuted, one of its coolest features was the fact that you could say "OK Google" any time you were on the home screen to launch a Google Voice Search. This feature was ultimately made available for other devices by way of the Google Now Launcher.

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

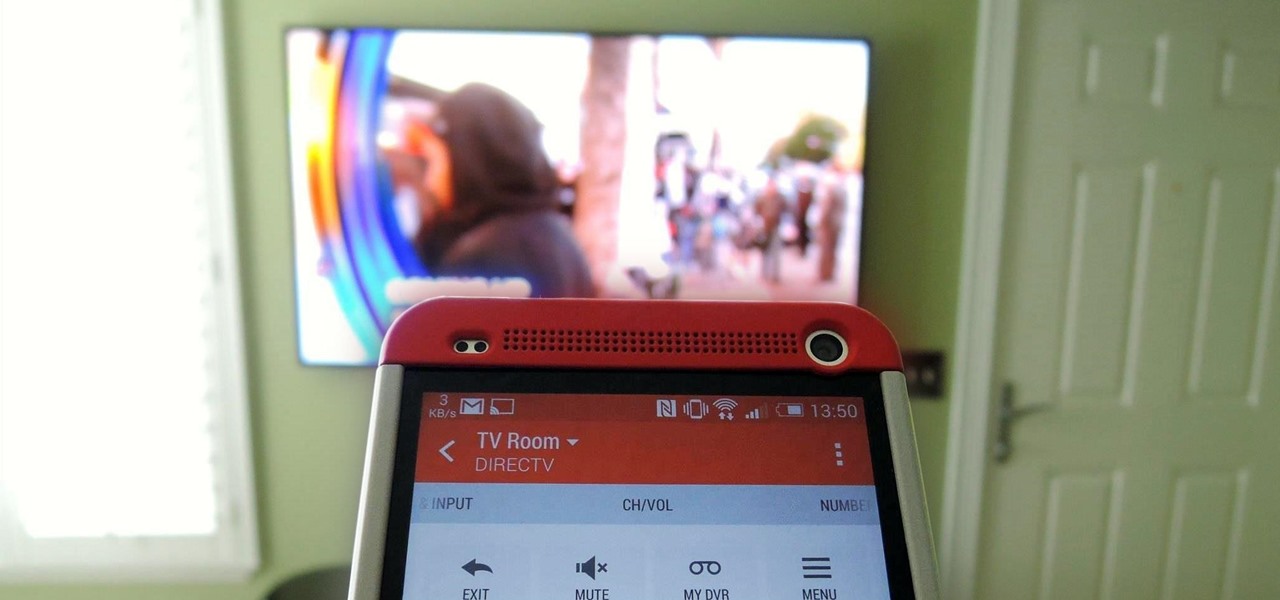
Let's face it, finding your remote, let alone finding something to watch, can take more time out of our days than we'd care to admit. There are remote locators and channel guides out there, but why use those when you have a perfectly good remote always on you—your HTC One. HTC put an IR blaster into their One and when it's coupled with their Sense TV app, it can make for one hell of a smart remote.

You've probably used Google to search for recipes, or to find out what the heck that mystery food on the ingredients list is. But with all its built-in features, there are plenty of other ways the search engine can help you out in the kitchen.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Like many smartphones nowadays, your Samsung Galaxy S4 comes bundled with a headset for you to listen to music, watch videos without disturbing others, and even make phone calls. I personally only use it for music, whether it's Play Music, Pandora, or streaming from YouTube.

The newest Android operating system, Android 4.4 KitKat, has been unleashed with the arrival of the Nexus 5, and soon to be rolled out to other Nexus devices and Google Play Edition smartphones any day now. Only problem is, the Samsung Galaxy S3 isn't getting 4.4 for a very long time. It doesn't even have 4.3 Jelly Bean yet.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

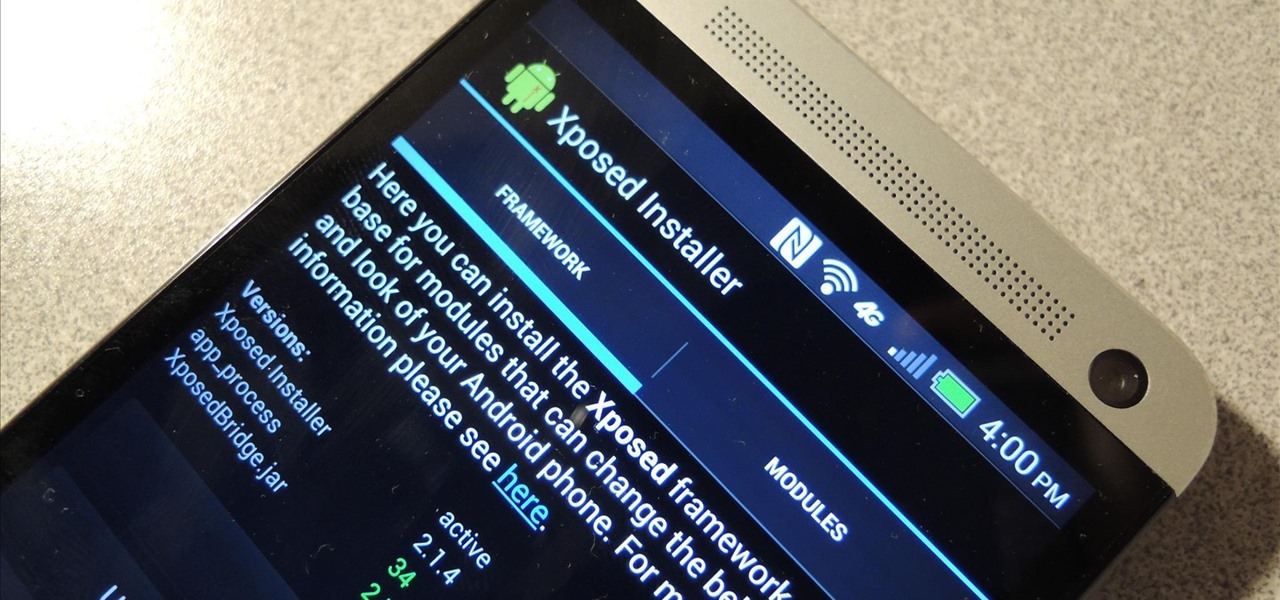
Xposed, by XDA developer rovo89, is a framework for your Samsung Galaxy S4 (or other Android device) that lets you add tweaks and customizations to your ROM (either stock or custom) without any real hassle.

Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

Smartphones are great. They help you keep in touch with your loved ones and stay up to date on what's going on in the world. The problem is that like everything else that's useful, they cost money to use, and between calling, texting, and data plans, it can get really expensive.

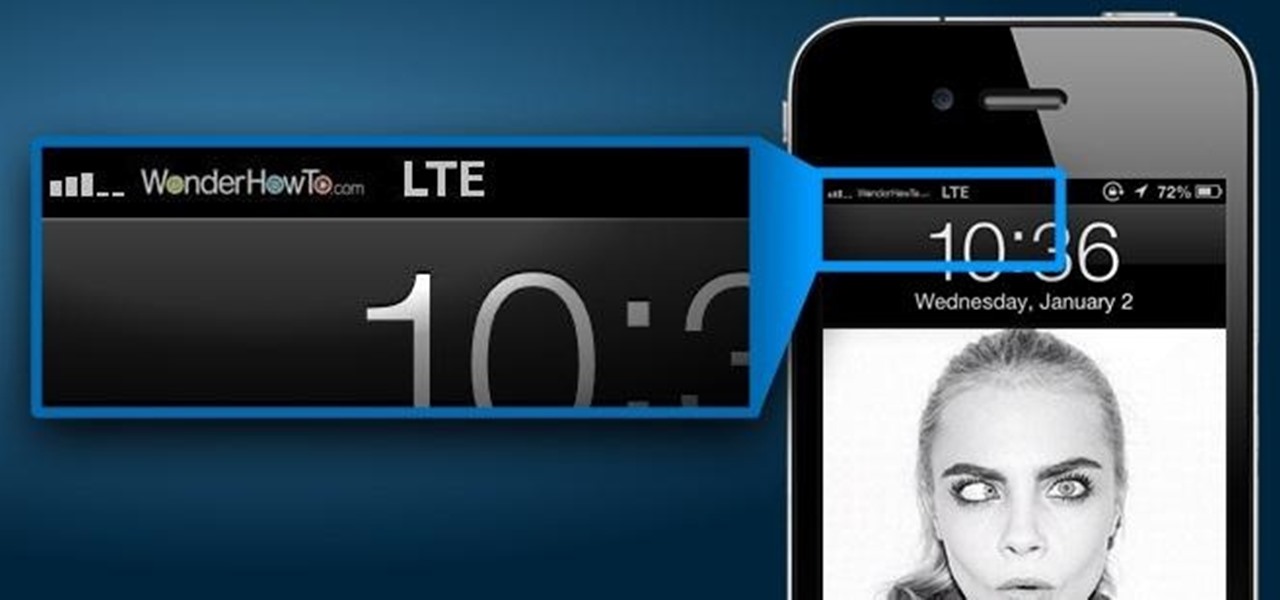
Changing the carrier name from an unlocked iPhone's status bar has been possible to do ever since Cydia released Zeppelin earlier this year. The application comes with preset logos you can use such as Pac-Man, Space Invaders, the Assassin insignia of the Assassin Order from Assassin's Creed (well, that was a mouthful) and my personal favorite...