In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

Texting has become the king of communication—gone are the days where everyone called each other. These days, it's down-right weird when someone calls first. Whether it be on a phone or on a computer, SMS and MMS messages are the most common way people keep in contact, so why not make sure your app of choice is the best possible one out there?
Make no bones about it—having an "undo" option is a freaking godsend. Whether you accidentally deleted an entire essay, screwed up the shading on a Photoshop job, or sent an email that wasn't quite ready, having the option to undo a click or button-press can definitely be a lifesaver.

Hi, my name is Alan, and I am not a script kiddy brat from Xbox Live asking you how to boot someone offline for being mean to me. I am an amateur white hat hacker hoping to learn and teach and this is my first tutorial.
With our internet-connected devices growing in number by the year, it would be nice if they could somehow all be interconnected. This is becoming commonplace for our tablets, smartphones, and laptops, but our media streaming boxes still seem to be isolated in their own little worlds.

On the internet, everything is possible, even if it's not grounded in reality (check no further than anything The Onion publishes). Witty headlines combined with clever photo edits make even the most absurd topic seem like a serious news story. Some of these stories are so convincing that they even fool news organizations, such as the New York Times and even the official newspaper of the Chinese Communist Party. While some of us can tell when something sounds a bit off, others (like our paren...

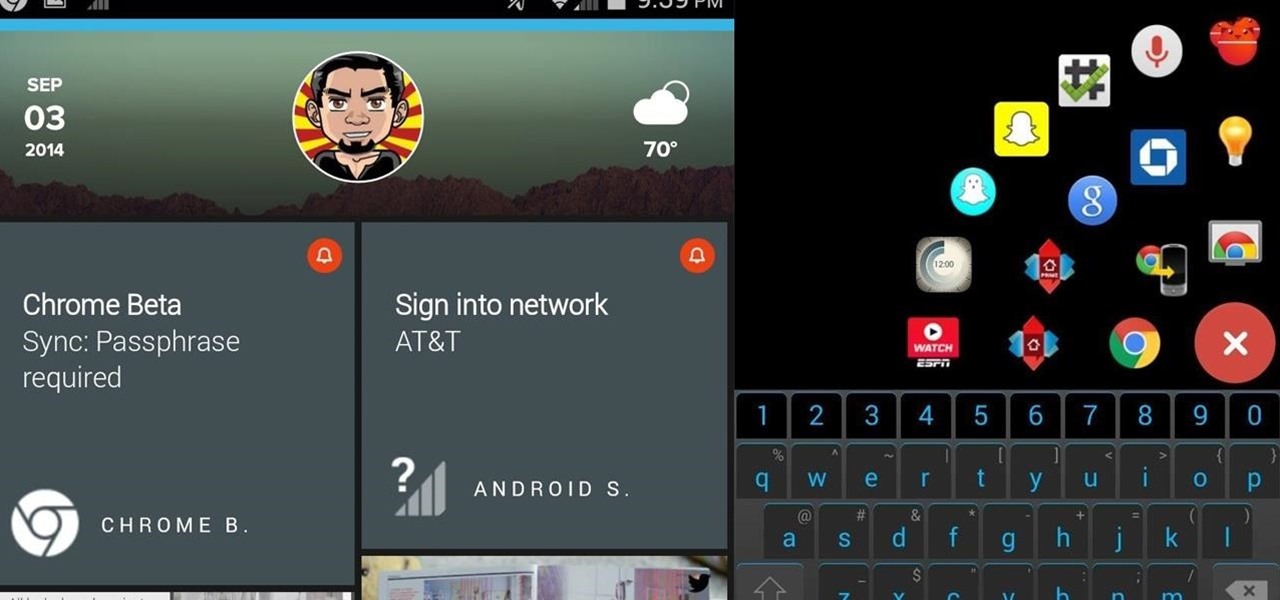
If you're like me, you probably encounter the lock screen on your Android device more than any other screen. Every time you check for new notifications out of habit, or simply pull your phone out to see the time, the lock screen is front and center.

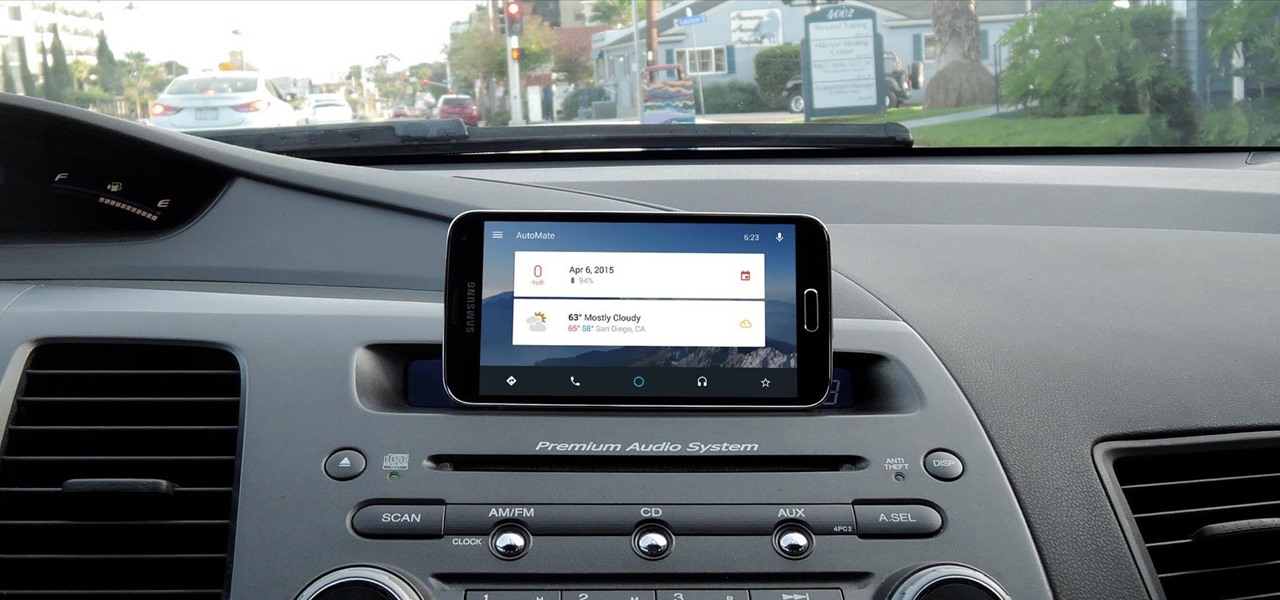
Auto manufacturers are slowly starting to debut models with Google's new Android Auto software baked into the dashboard console. Starting with the 2016 model year, we should see vehicles from Honda, Ford, Chevrolet, and many others sporting the new software.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Tinder, the extremely popular dating app, has the wonderful tagline, "Any swipe can change your life." However, if you downloaded their most recent update, your next swipe could cost up to $19.99.

If you're a fan of double-tap to wake gestures, you're going to love the newest app from ElementalX developer Aaron Segaert. On supported kernels, it allows you to associate custom apps and activities with each of the wake gestures you've set up, which will immediately be launched even with the screen off.

There's no such thing as a perfect Android keyboard. Some, like Swype, have gesture typing down to a science, but lack in predictive technology. SwiftKey, on the other hand, boasts awesome next-word prediction, but less than stellar gesture typing. Many others are optimized for multiple languages, space saving, or emojis, but none are without their flaws.

Step 1: Introduction: Hello! Hackers

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

Samsung phones have a pretty nifty little feature called Smart Stay that will prevent your screen from turning off while you're actively using your device. Trouble with this is that it's exclusive to Galaxy devices and it uses a ton of battery since it monitors the front-facing camera to detect when you're facing the screen.

By now, everybody knows that overcharging a battery will reduce its overall life span. This is why many smartphone manufacturers recommend that you charge your device to 100%, then unplug it immediately. Some even go so far as to automatically stop charging when the device is fully juiced, although not all devices have this functionality.

The front-facing stereo speakers on the Nexus 6 certainly pump out some awesome sound—but it could always be better, right?

Most diehard Mac users have used TinkerTool at some time or another, and if you haven't, it's time to start. Whether it's to change your system's font or to disable UI animations, it seems like anything you could ever think about tweaking in Mac OS X is doable through TinkerTool. And now, developer Marcel Bresink has updated his app to work with Yosemite, so let's see what it can do now.

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

It's pretty logical for your MacBook to sleep when you close its lid, but under certain circumstances, you may not necessarily want this feature to kick in.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Placing widgets on your device's home screen is a quick way to gain instant access to shortcuts or to specific aspects of an app, like music controls or weather forecasts. As more and more developers create various types of app drawers and shortcuts, many overlook widgets and what they have to offer.

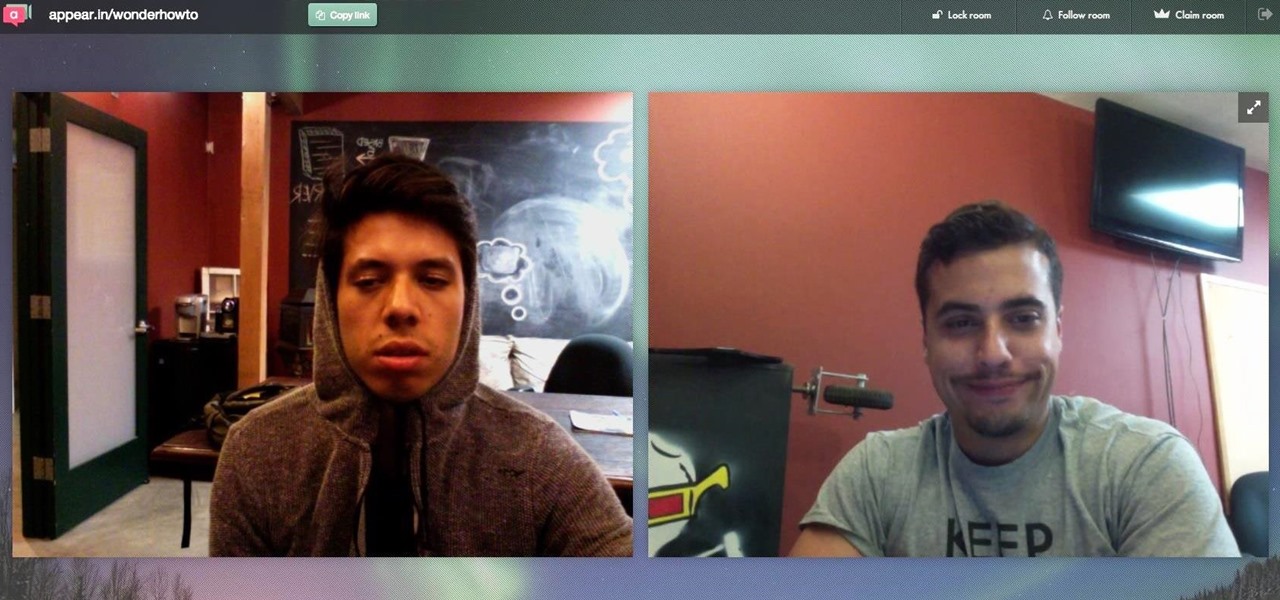
These days, phone calls aren't always the best way to communicate with others. Maybe you need to reach people out of the country, or you simply want to have a more visual conversation. Either way, there's a reason why video calling has become so popular.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

With all of the top-notch specs that the Galaxy S5 sports, the only minor quibble users have had with its hardware is the speaker situation. A front-facing earpiece is used for phone calls, but all other media is restricted to a single rear-firing speaker.

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

As soon as third-party keyboard compatibility was announced for iOS 8, Apple loyalists and the newly curious both looked to the popular Android third-party keyboard developer, SwiftKey, to see if they'd be offering their services to iOS.

BlinkFeed completely changed the way I access new updates from Facebook and Twitter, but when I switched to the Google Play Edition of the HTC One, I lost access to the launcher. BlinkFeed is available in the Google Play Store, but HTC has not opened it up yet for all devices yet. While there are ways to port BlinkFeed over to other devices, it's reliability is dependent on the ROM, sometimes causing bugs and crashes.

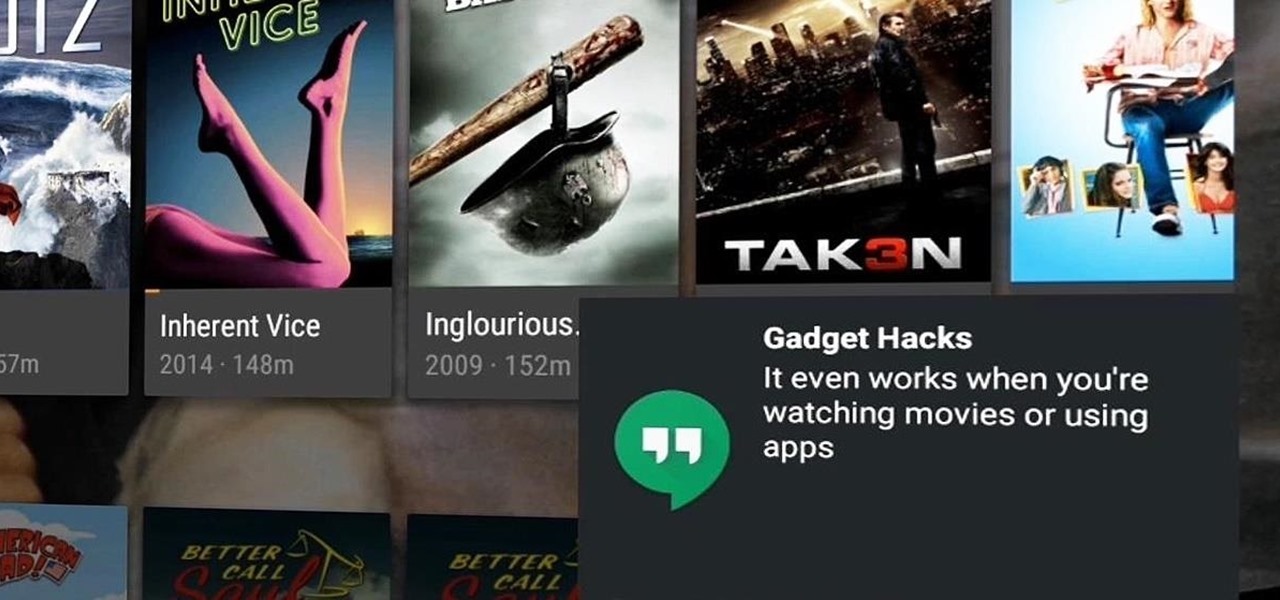
It's been a long-rumored feature, but today, VoIP calling has finally started rolling out to users of Google's Hangouts service. Essentially integrating Google Voice into the popular messaging platform, Google has given Android (as well as iOS) users an easy way to make calls without eating up their plan's minutes.

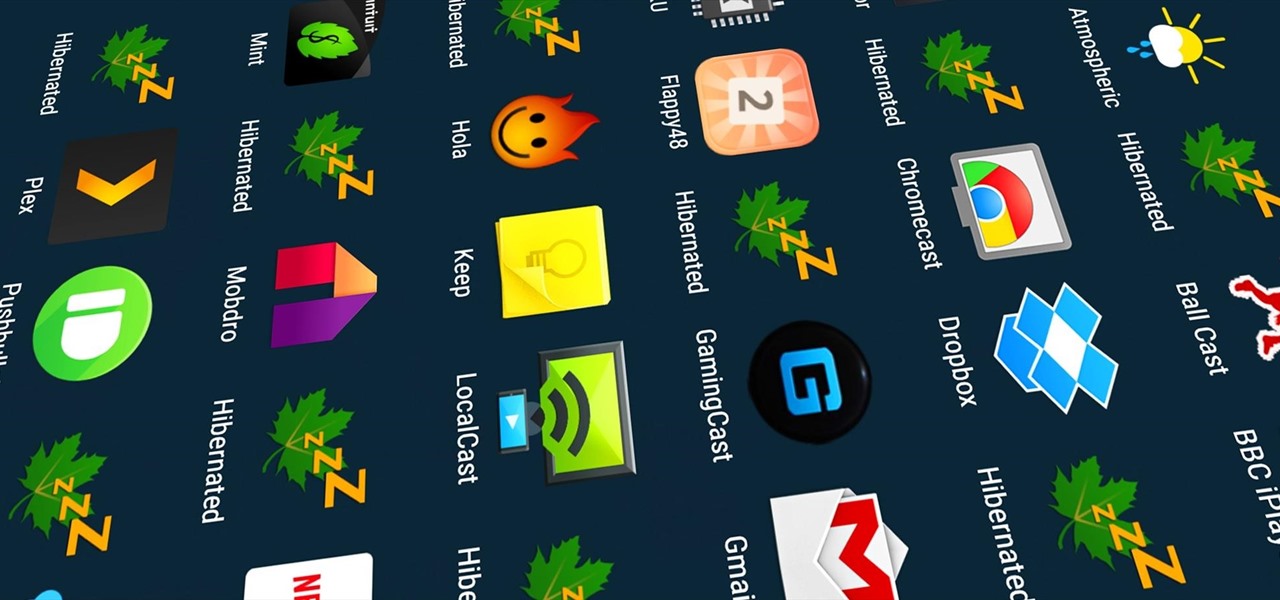
Greenify is a terrific app that allows you to put battery-hogging apps into "hibernation." Effectively closing the problematic apps and preventing them from running until you explicitly launch one of them, hibernation is a great way to save battery life while you're not using your phone.

Being healthy and active will help you live longer, but finding the strength to work out? That's hard. What does it do for me right now? I mean, here I sit, writing this article, thinking about going for a run, and I feel good just for thinking about running. But will I do it? Nah, I'm too lazy.

Last week's tech roundup featured iPhone 6 clones, an all-in-one sleep tracker, Xbox One updates, and other cool gadgets. This week, there's a lot more to show off, and a bunch of stuff that I need to get my hands on! Everything from app updates to putting stickers on your favorite items, I can't help but squeal at how much the "future" is right now.

It's really amazing how much you can do with root access on an Android device. From various themes to porting exclusive funtionality from other devices, the power of Superuser privileges is truly awesome.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

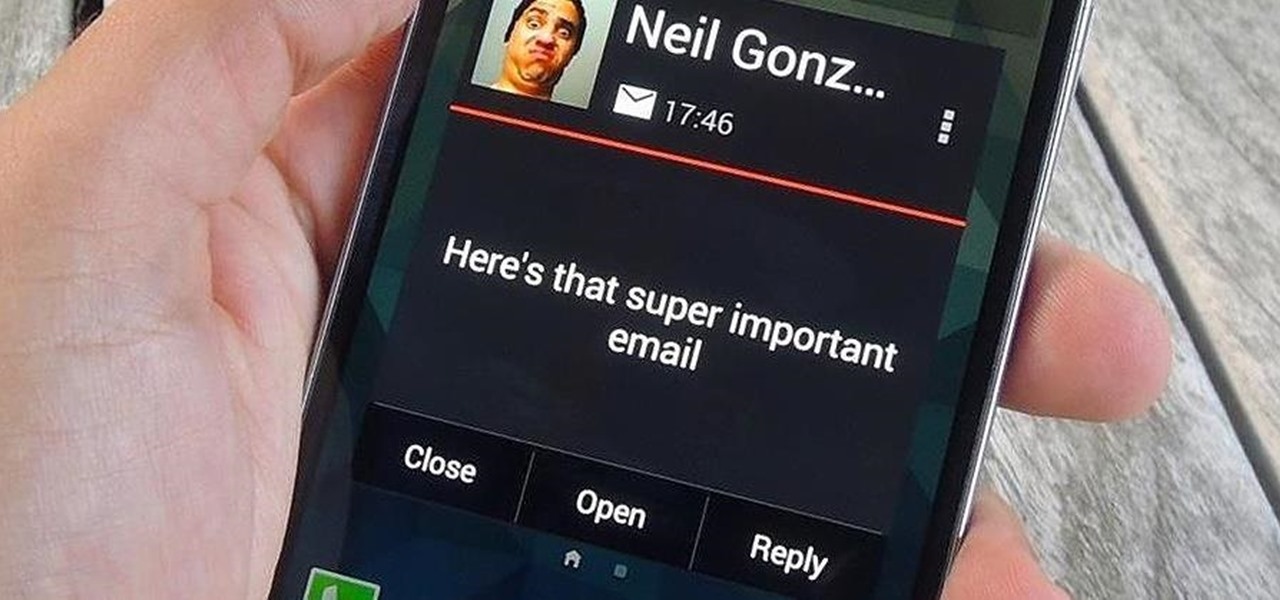
Believe it or not, but people are actually texting less than they did before, and that's all thanks to Facebook Messenger, Snapchat, WhatsApp, and other split-second communication services. However, one communication method that is still going strong—and dominating—is email.

A huge chunk of my life revolves around my computer, and whenever I'm on my laptop and get a text message notification on my phone, I find it extremely distracting to stop whatever I'm doing to hunt it down. That's why I'm a big fan of text messaging via my computer.

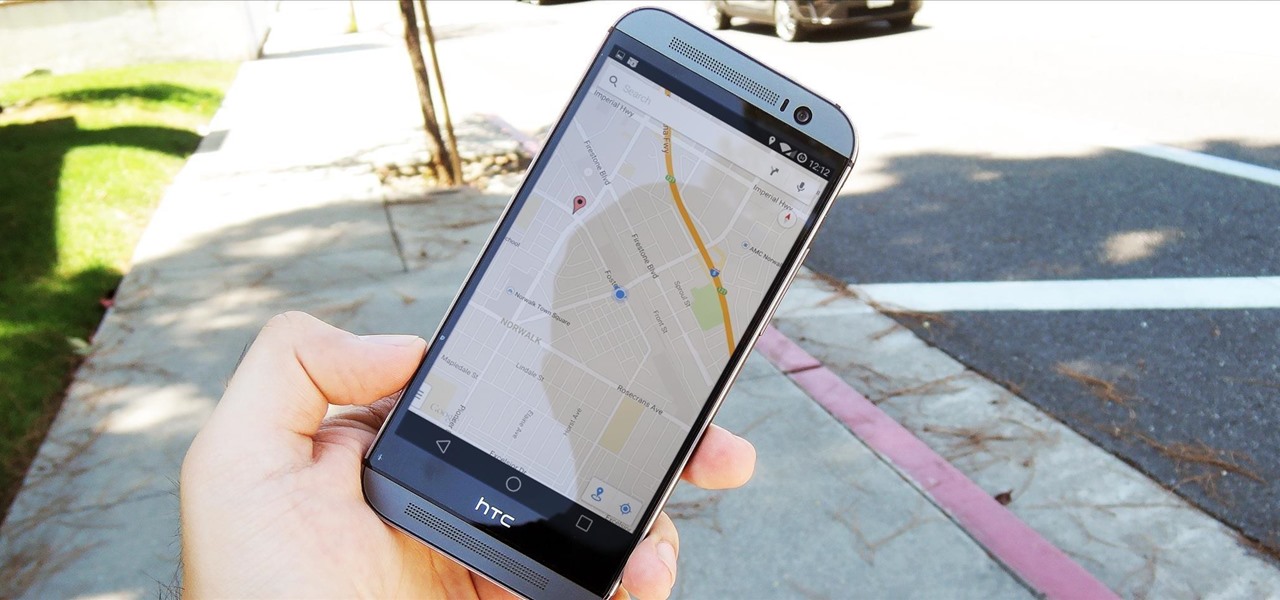
Google's Android Device Manager makes it extremely easy to track down your phone or tablet, but while it's simple to set up and use, it does require your device to have an active data connection, which can be an issue in some areas.