Learn how to solve the infamous Rubik's Cube. Yes, that's right, watch this three-part video tutorial to see how you can solve Erno Rubik's Magic Cube, now known as the Classic 3x3 Rubiks Cube. Learn the notation and the algorithms involved.

Dolphins are some of the best, most graceful swimmers in the sea. Majestic and beautiful, they achieve both speed and form while looping from wave to wave.

Offense tactics are important in rugby, where the ball cannot be thrown forward. Learn how to play rugby, including rules and skills, in this video rugby lesson.

This how to video shows you the step by step process of making a baby beaded frog. This is easy and fun activity to do with your kids. Beading is a great way to introduce your children to the creativity of arts and crafts. This is a good project for older children because it does involve small beads that can be swallowed. With this how to video you will be able to teach your children how to make a beaded frog.

Kung fu is an ancient Chinese martial art that involves using powerful punching techniques. Learn several punching combinations from a professional kung fu instructor in this free video series.

In this 5 part manicure tutorial you will learn how to apply acrylic nails. This process is quite involved and a bit difficult so it will take a lot of practice. Watch this 5 part how to video and you can apply acrylic nails in your own home.

During the video tutorial, you'll learn how to simply solve the easy and fun fifteen number puzzle. You'll learn a couple different moves to help you solve the 15 puzzle, which are called the curl and the box and twist. The curl is easy, but the box and twist is a little more complicated.

The Jitterbug is a popular swing dance, also known as the Lindy Hop and East Coast swing. This how to video demonstrates a Jitterbug dance sequence. These steps are quick and easy to learn. The routine involves the Texas Tommy step, the left side under-arm turn, the left side waist turn, the tuck turn and the right side under arm turn. Watch this dance tutorial and you will be doing the Jitterbug in no time.

In this math lesson we will learn how to solve problems involving simple interest. When you deposit money in a savings account, the bank pays you interest at a certain rate called interest rate. There are two types of interest: simple interest and compound interest. In this lesson we will talk about simple interest. We will use the following important formula:

To learn how stop worrying involves regular fasting from fear, learning to plan without worrying and to accept the future as it comes. Part of a Yoga class on Rasa Sadhana, the Tantric practice of emotional fasting.

If you like 2D side-scrolling video games, then Shank's your man. Shank is full of "beat 'em up" action and combat, perfect for any gamer addicted to the old style of play. Shank is available on both the Xbox Live Arcade (Xbox 360) and PlayStation Network (PS3). But this Mahalo walkthrough for Shank is for the PlayStation 3.

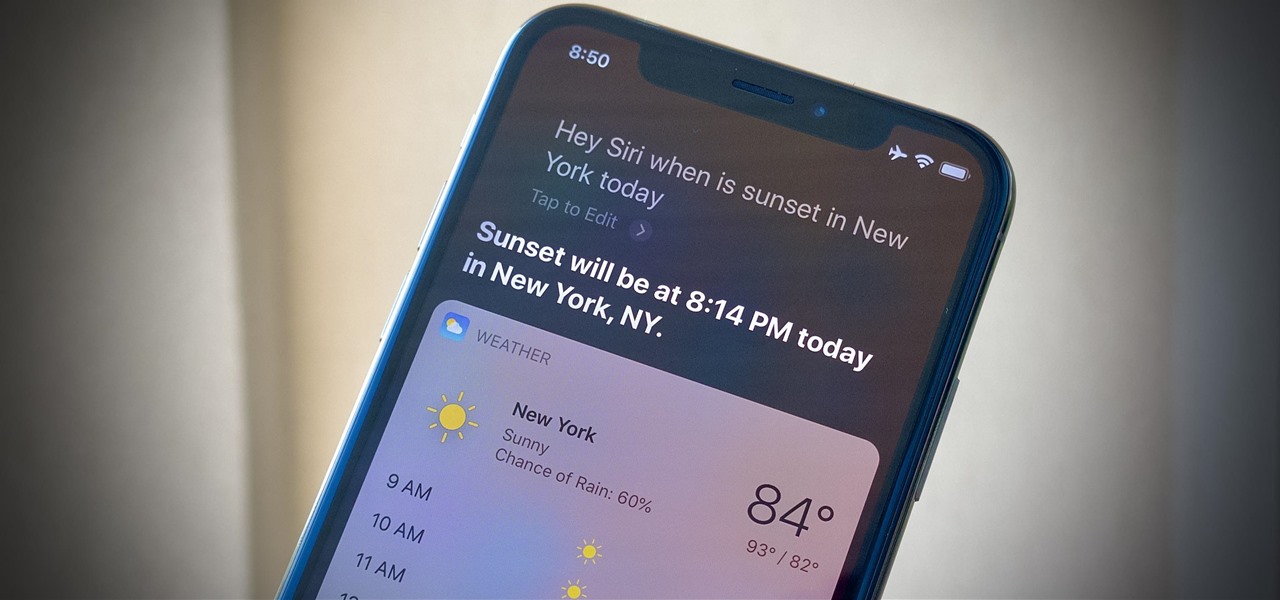
HomePod and HomePod mini are excellent smart speakers if you're entrenched in the Apple ecosystem. They even offer ways to protect your sensitive information from friends and visitors who try to ask Siri to spill your secrets. But there's an extra layer of privacy you can put in place to make sure nobody gains access to any important notes, reminders, and calendar events.

With Samsung's One UI 3.0 update, the main on-screen volume slider has a little menu button on the top of it. Tapping this will expand the slider into a full-blown volume panel, complete with controls for all of the various types of sounds your Galaxy might make. Standard stuff, really, but there's more to it.

Apple just rolled out the of iOS 14.5 to developers and beta testers, and one of the headlining features is the ability to keep your iPhone unlocked when your Apple Watch is nearby. As these things tend to go, Android has actually had this same feature for years, though it isn't quite as polished.

The true crime genre has long been popular on television and more recently on podcasts with shows like Serial.

Apple's Dark Mode in iOS 13 and later offers a cool, comfortable viewing experience on your iPhone. You may prefer the dark theme all day long, but if you like to use it only at night, it's not very convenient to switch it on and off daily. But there's a setting that lets you set it and forget it, so you never have to do it manually again.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

TWRP won't be ready for the Pixel 4 and 4 XL until months after release. But since you can already root with Magisk and tinker with the OS, you might find yourself in a situation where your phone won't boot, yet you don't have a custom recovery installed to fix it. Luckily, there's still a way around this.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

If you recently received your new Galaxy S9 or S9+, you're probably excited to try out all of the features the flagship offers. While many of the features are self-explanatory and easy to access, there are a handful of very useful items that Samsung has buried in the settings menu. Enabling these hidden features will help you unlock the true power of your new device.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

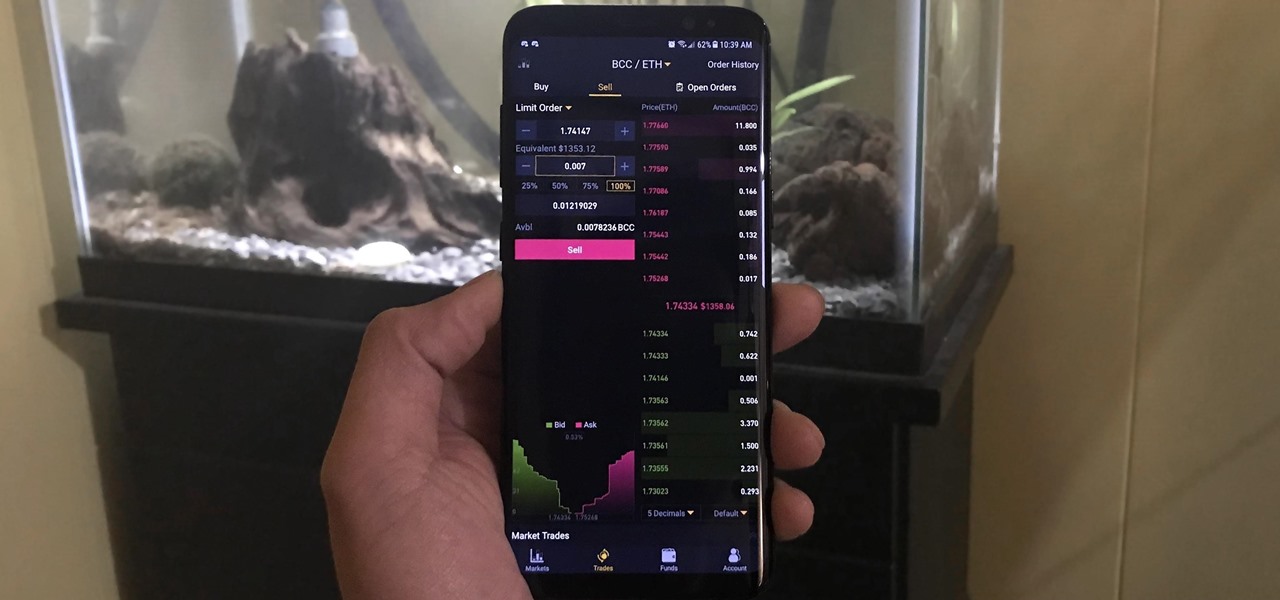
Selling alt-coins like Stellar (XLM) or Ripple (XRP) in exchange for more widespread coins like Ethereum (ETH) or Bitcoin (BTC) can be a daunting task if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

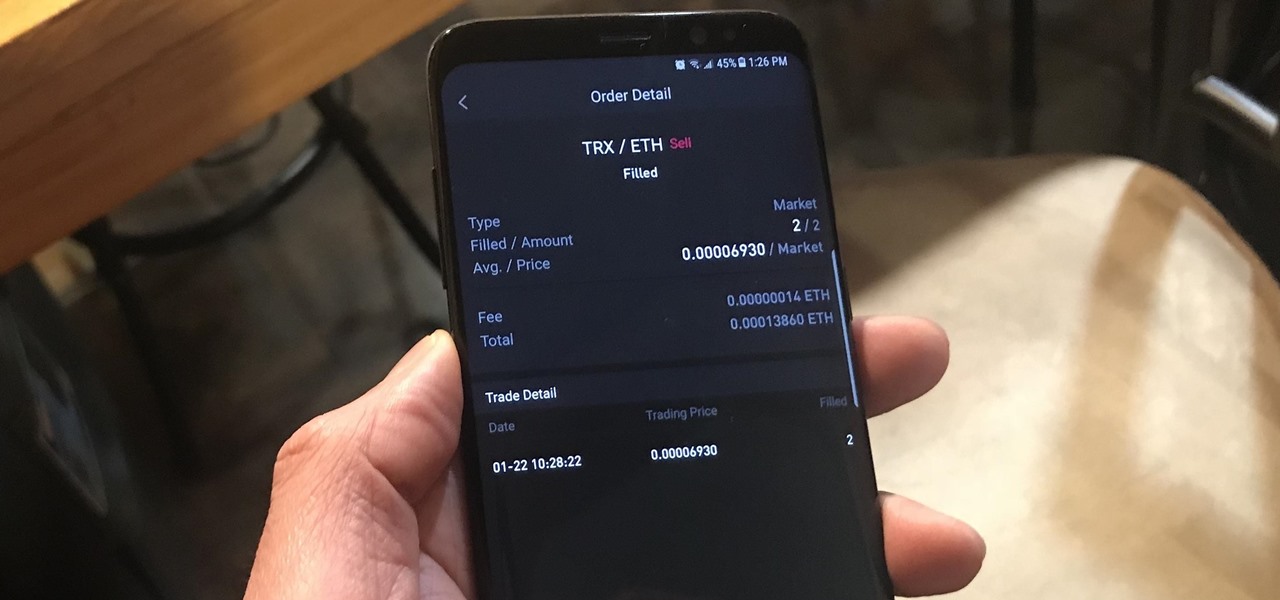
Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

The nemesis of music streamers is data caps, cell phone or otherwise. Restricting monthly data and forcing users to decide between quantity and quality of music has had audiophiles tearing their hair out since streaming toppled the iPod. While the problem regarding music quality seems difficult to tackle, it's far from impossible.

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Blowing dust and fungal spores are creating a public health problem that could be just a slice of what's to come with climate change.

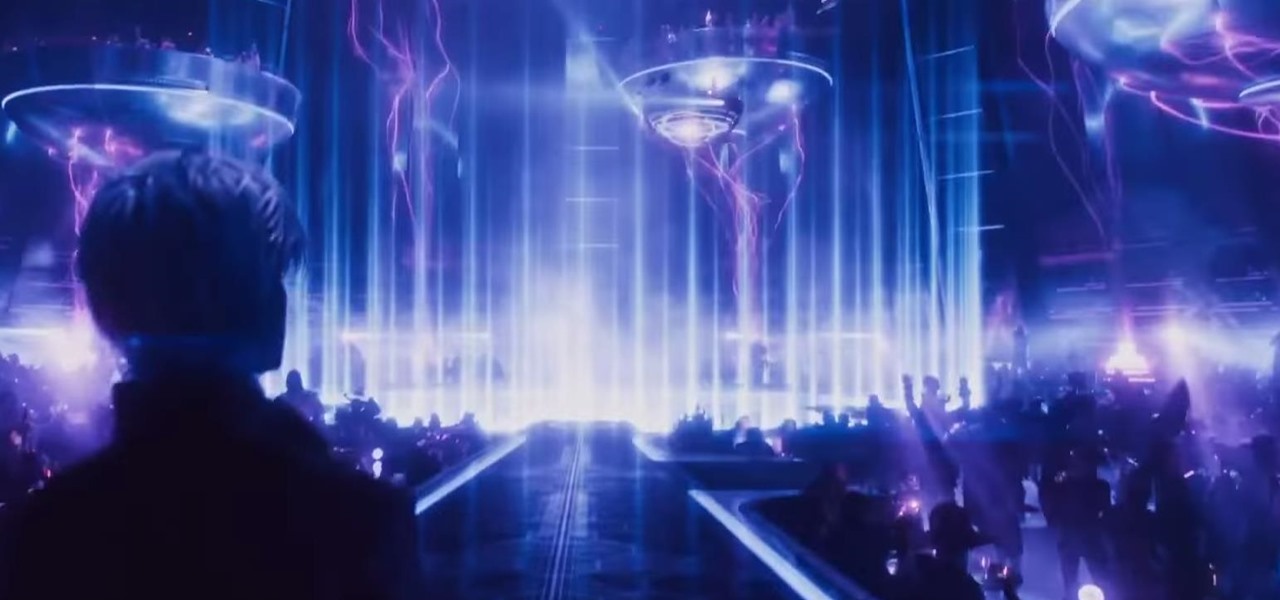
So while it is the weekend of San Diego Comic-Con, and it should not be a complete surprise — without a word of warning hitting my feed — the trailer for the upcoming film, Ready Player One was released today. And wow it looks amazing.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

There is an Indian story called the Legend of Paal Paysam, and while it doesn't seem like it at first, it has a lot to say about what motivated Paul Travers in the augmented reality space.