There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

Yogurt is more than an excellent source of protein, calcium, and gut-healthy probiotic bacteria. A protein isolated from probiotic lactobacillus bacteria in yogurt is capable of inhibiting drug-resistant bacteria.

The act of liking someone's really old Instagram post is called "deep-liking," which is pretty apt if you think about it. While going "deep" into older posts on the feed of your ex or crush or whoever, your finger may slip accidentally and double-tap on a photo or video that you'd rather not let them know you're looking at.

The Galaxy S8 and S8+ might not have made it into the hands of the public yet, but we sure have come across a lot of the stock apps from Samsung's latest flagship phones. First, there was the new launcher, then Hello Bixby, and now, the extremely elusive Record Screen feature has been leaked.

Our brains do a magnificent amount of work to process visual stimuli, but they aren't difficult to fool. Optical illusions can trick our minds into believing what we're seeing is real, even if it's not—and virtual and mixed reality technologies take advantage of this little loophole in our brain to help us accept the unreal.

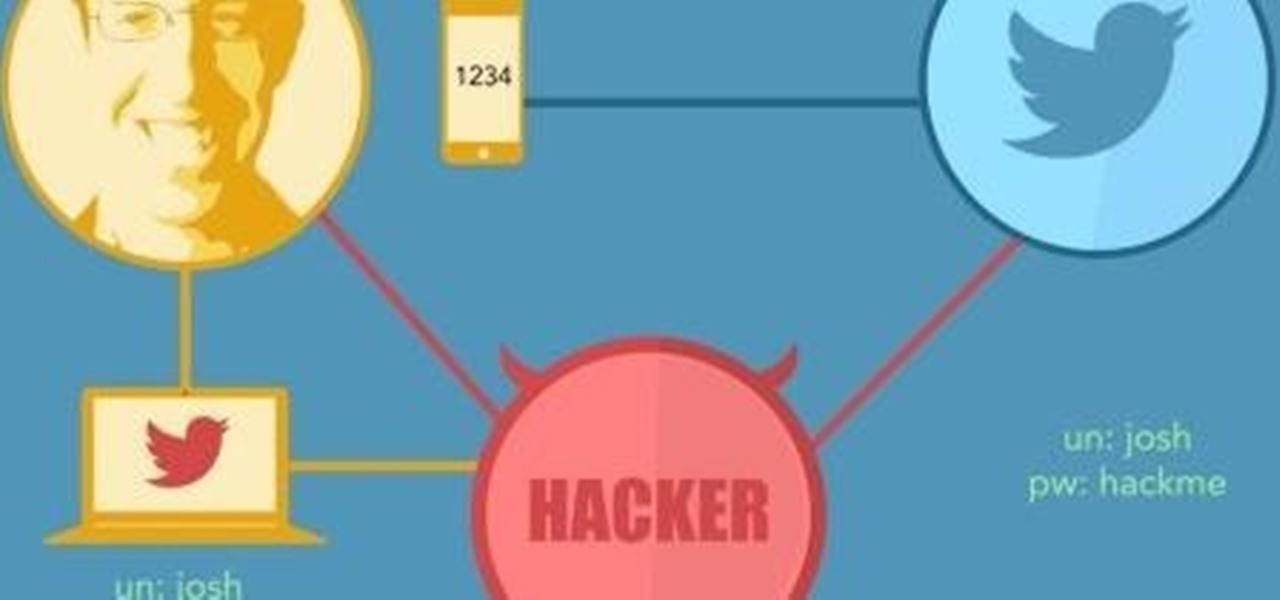
Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Garlic isn't just a food, it's a legend. It's been found in the pyramids of Egypt and is referenced in the Bible. Hippocrates, the father of Western medicine, prescribed it regularly, and it was given to the first Olympic athletes in Ancient Greece to enhance performance (take that, Lance Armstrong). And, of course, it's famed for its ability to ward off evil, whether it's in the form of vampires, demons, or werewolves.

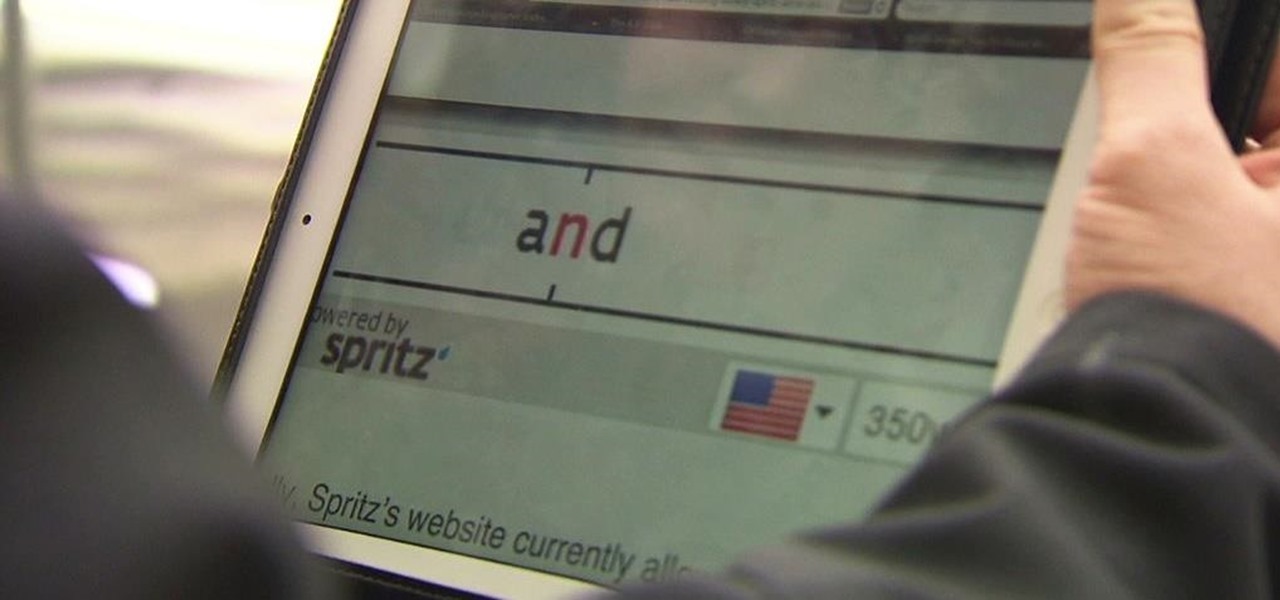
Reading is no longer a leisure activity—it's an on-the-go activity that requires speed and less attention. That's why speed reading apps are growing in popularity. As smartphones and tablets increasingly take over the traditional book market, reading skills need to be adjusted accordingly, so you can cram in 5 pages in-between texts and emails.

The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.

Origami is an activity which brings life to paper and can be enjoyed by both adults and children alike. In this video, Ngai Chun Cheung demonstrates how to make a mobile phone stand using origami. He begins by folding a rectangular piece of paper at the center lengthwise. Next, he folds the outer open sides to touch the folded edge on one side, which forms a triangle. Then he flips the long rectangular side to form another triangle next to the first one. The paper is opened out and folded alo...

Riding a unicycle is a great circus activity, or just a fun way to get around and impress your friends. Learn how to ride a unicycle with expert tips in this free video series on unicycling.

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now let's talk about another group competition game. This game is known as stack the chair. You can easily get this at one of your local Mal-Mart's, K-Mart's, or Target. These chairs came in a package. Don't forget to divide the group of party guest in half. So let's say you have 20 guests, 10 in one group, 10 in the other and their goal is t...

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. Now let's talk about another group activity game. Competition game that is. If you have let's say maybe 20 people in your guest party, make sure you divide them up into 2 groups of 10 and 10 and then provide a drawing board similar to this or you can just provide a big poster paper or poster sheet. The goal is to take one person from each gro...

In this series of playground game videos, our young expert tells you everything you need to know about this fun kids activity. Jamie show you how to draw the hopscotch boxes as well as the resting place.

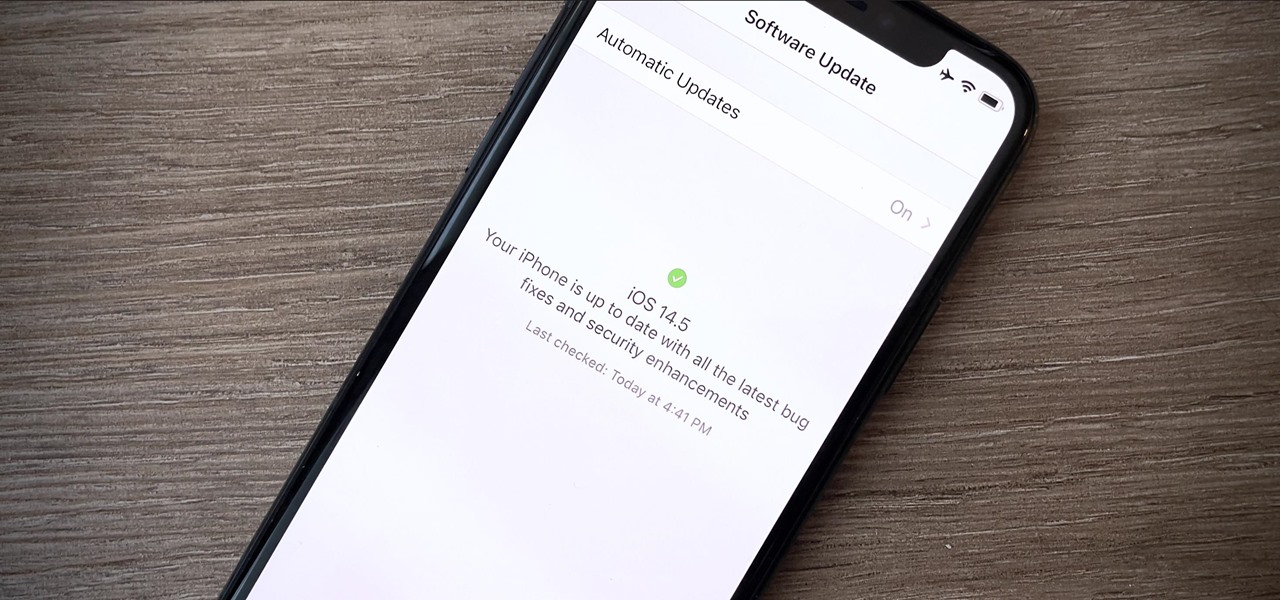
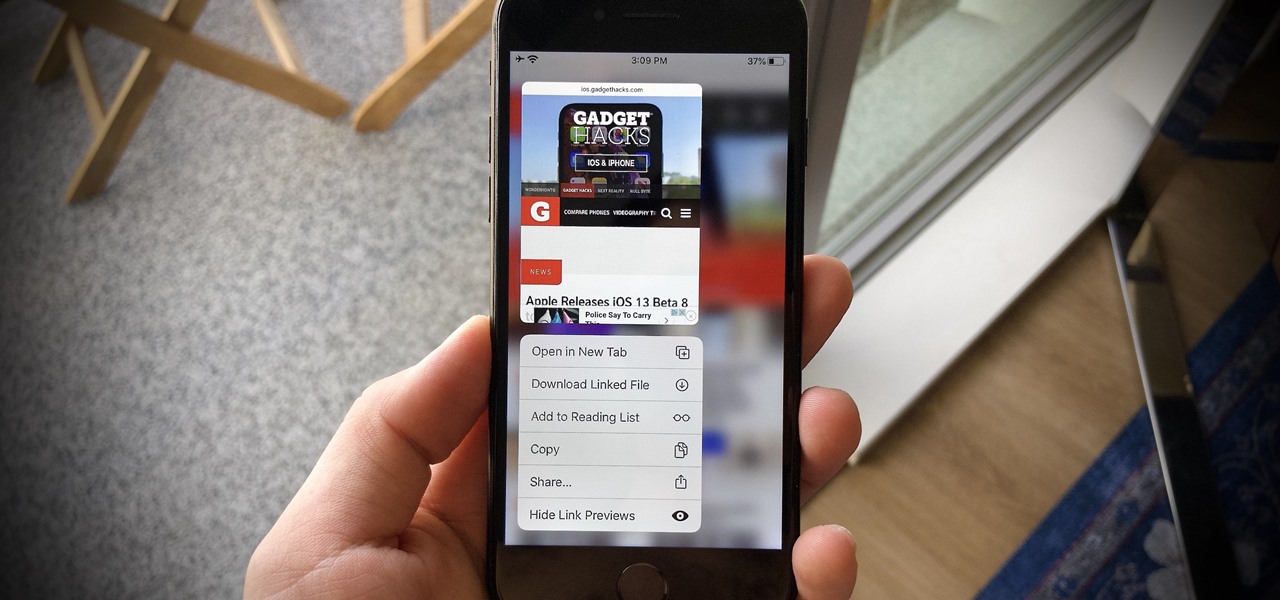
Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

Despite legends to the contrary, it appears that the saliva of a Komodo dragon is not teeming with pathogenic bacteria that kills their prey. Its reputation to survive while colonized with lots of horrible disease-causing bacteria, true or untrue, has made it the subject of research in pursuit of natural antimicrobial agents and led scientists to some remarkable findings.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Most of you have probably wondered at least once who has been checking out your social media profiles. While most platforms prohibit you from seeing who's viewed your profile, such as Facebook, Instagram, and Twitter, TikTok is one of the few places that lets you track profile visitors. And unlike with LinkedIn, you don't have to pay for the privilege.

Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

Apple released iOS 14.5 developer beta 1, and the update sports a list of interesting features and changes. Some of those include support for the Xbox Series X and PS5 DualSense controllers, the ability to unlock your iPhone with Apple Watch, AirPlay 2 support for Fitness+, 5G support for dual-SIM setups, and a refreshed Software Update page in Settings.

Whether you want to give a gift that your loved one has wanted all year or one that they never even knew existed, there's something awesome for everyone in these gifts. Just as exciting as their innovative features is their price.

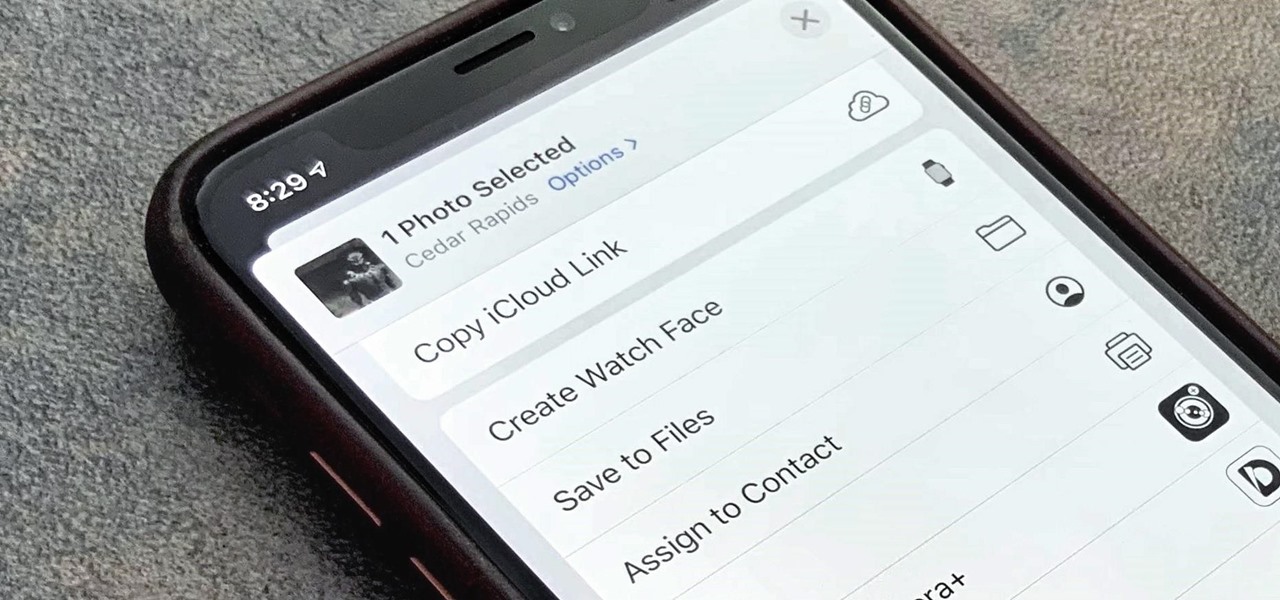
With Shortcuts, Apple has designed a way to create your own tools and automations right on your iPhone. And to top it off, your creations can be accessed in a variety of ways, including Siri phrases, widgets, and the Shortcuts app itself. Perhaps even more useful is adding them as custom actions to your Share Sheet and making them available to you system-wide.

Google's feature drops for Pixel devices have added fun and useful new abilities, such as AR effects for Duo, Call Screen automation, scheduling Dark Mode, and Quick Access Wallet for Google Pay, that are exclusive to the company's line of smartphones.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Beta testing certainly has its perks. While you do need to deal with bugs, you're introduced to new features before the general community. And if we're talking iPhones, there are over 200 new features in iOS 13 beta. If you're already on board with iOS 13 public beta 6 for iPhone, you can get an upgrade on that firmware as Apple just released public beta 7 today.