Check out this instructional video that will teach and demonstrate how to play corn hole. What is corn hole? Corn hole is a game in which players take turns pitching small bags filled with corn (or sand or beans) at a raised platform with a hole in the far end. These platforms are usually plywood sometimes plastic and either all white or decorated with a team name or any other custom creation.

In this episode, we dive into the expensive, or, at the least, tedious realm of camera stabilization equipment. This ranges from the all-powerful, all-knowing fluid tripod head, to the much used and often abused dolly. We don't own and operate an actual Steadicam or a jib or a crane, but hey, we'll mention them, too.

This instructable aims to show you how to cut any type of disk to a desired shape. It is particularly useful in cutting down cheap 12cm DVD-+R 's into more expensive (can be up to 10 times more) 8cm DVD-+R disks. The technique shown here works with all disk types. The video below shows us cutting a music CD into a heart shape, and also illustrates the basics of cutting 12cm disks into 8cm ones. The actual cutting of a disk (and the guide) can be seen here:

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

Can you be too lazy for video games? That's how I feel sometimes. I want to play the latest PlayStation has to offer, but I can't be bothered to get out of bed. As if Sony read the minds of lethargic gamers everywhere, the company has released an amazing thing — PS4 Remote Play allows you to play your PS4 on your iPhone, no TV required. The best part? It's 100% free.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

We've already seen plenty of shopping potential for mixed reality headsets, from holographic car showrooms to trying on clothes and picking out furniture. Very few of those ideas have been put into actual practice, but we're getting closer, and consulting firm Valorem is making headway. They created HoloTire for the Microsoft HoloLens to demonstrate the advantage of experiencing a product in mixed reality. I'm hard-pressed to think of a more boring product to put on a holographic pedestal tha...

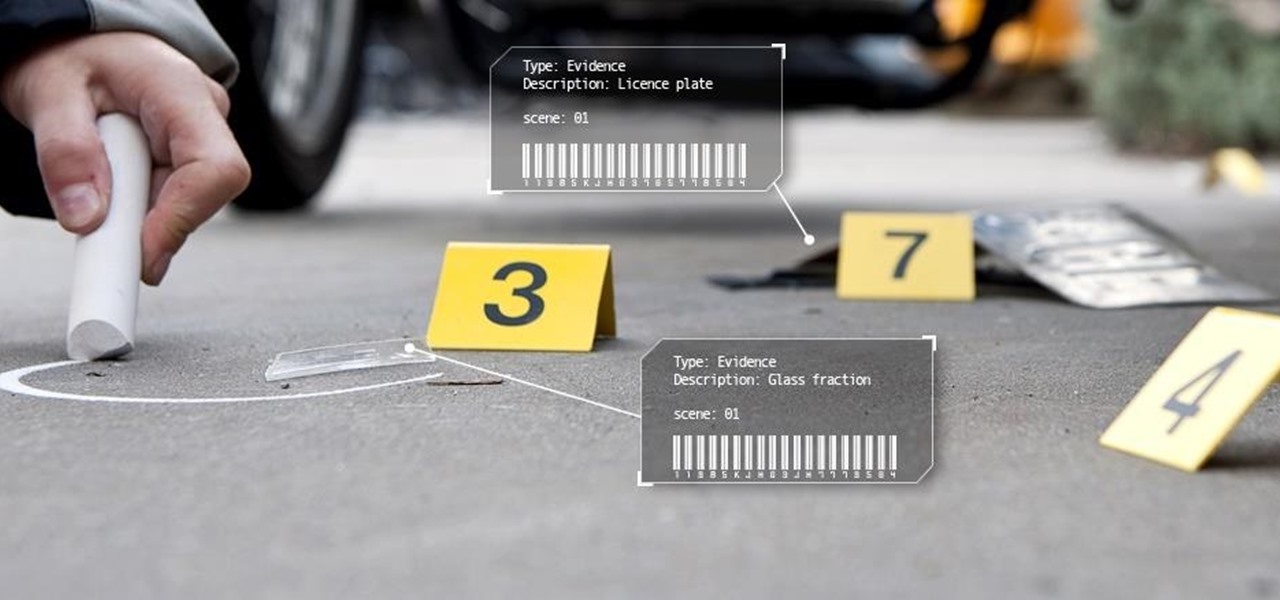
In this tutorial I am going to show you how to change some file metadata, this could be very useful if you want to edit or access a file and remove any evidence of your changes.

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

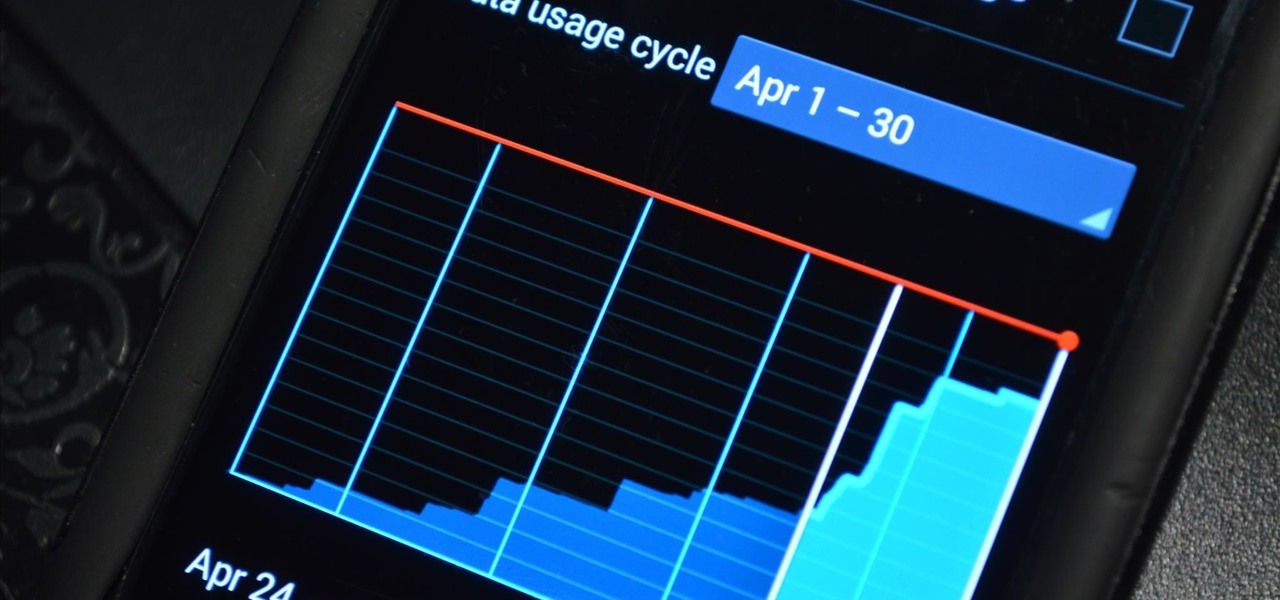
Ever feel like you're receiving notifications way too late on your Android device? Many Android apps use Google's Cloud Messaging service to send and receive notifications, including Hangouts, Gmail, Pushbullet, Facebook, and even WhatsApp to an extent.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Using spaghetti squash "noodles" for a healthy, low-carb meal seems like such a great idea, but as many of us know, turning this vegetable into a decent pasta facsimile usually has less-than-satisfying results. The usual method is to cut the squash lengthwise and roast, microwave, or steam it. Often, it comes out overcooked and underwhelming.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Over the weekend—just days before Apple's big event—an actual iPhone 6 leaked on Chinese site cnBeta. Again, nothing here that we already didn't know about—Sapphire screen, round(er) corners, larger display, and new button stylings. Below are images of the new iPhone 6 next to the current iPhone 5S. We can clearly see the protruding camera module as well as sections on the top and bottom of the back where the antennas will be housed. A second source was able to put together some videos, as yo...

Better sleep, smartphone news, and changes to your favorite forms of entertainment. There's been a lot going on over the last couple of weeks in the world of tech, and we thought we'd show you all of the need-to-know products, updates, and ideas that we think are most important.

It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

There's a popular new trick in the fishing community and that's tying a braided line to a fluorocarbon leader line. To do this, you'll need to know the proper knot, and this video will show you how to do it. With this method you will reduce some of the problems of twisting and tangling with using braid right up to your lure. Check it out. The braid helps absorb some of the pull on the line, so see if you can feel it when you go to land the big one!

This video will show you how to tether your Samsung Messager 2, (the MetroPCS phone) to your PC to use as a modem for internet access. This will allow you to use your cell phone as your internet connection point, meaning you'll connect to the net for the cost of your cell phone's data plan. You will need your Samsung USB cable, a PC with Windows 2000 or higher, all current drivers for your phone and PC, and you will also need to head here to get the Samsung PC Studio program. This is part 1 o...

If your iPad, iPhone 4 or iPod Touch is already on a tethered jailbreak, this is the tutorial on the new Redsn0w release for all you experienced users. An untethered jailbreak is a type of jailbreak where the device does not require rebooting with a connection to an external jailbreak tool to power up the iDevice. Jailbreaking allows users to get root access to the command line of the operating system, to download otherwise unaccessible extensions and themes, or install non-Apple operating sy...

Someone has just smashed the side mirror off your perfect Nissan Altima that you parked on that busy road you know you shouldn't have parked on anyway, so now it's up to you to repair it— unless you want to pay an overpriced mechanic, who will charge you for parts, labor, and whatever else he thinks he deserves. If you're up for repairing your side view mirror by your lonesome, for cheap, then this video by Richpin will show you the exact steps required to fix your Nissan Altima's side mirror...

Make sure you're getting the best experience from your Blu-ray movies on your PS3 by optimizing your PlayStation 3's audio, video and display settings. Scott Lowe for IGN, shows you step-by-step, the exact process for an enhanced Blu-ray experience.

It's good to know the IP address of your computer. With this information, you can track your computers usage online, and will also know how to change it if you want to surf unnoticed. This tutorial will show you exactly how to find the IP address of your PC, so you will never be lost again. There are a number of programs that require your IP address, for example if you are setting up an external device like an XBox live to your Internet connection, you will need to make sure the IP address is...

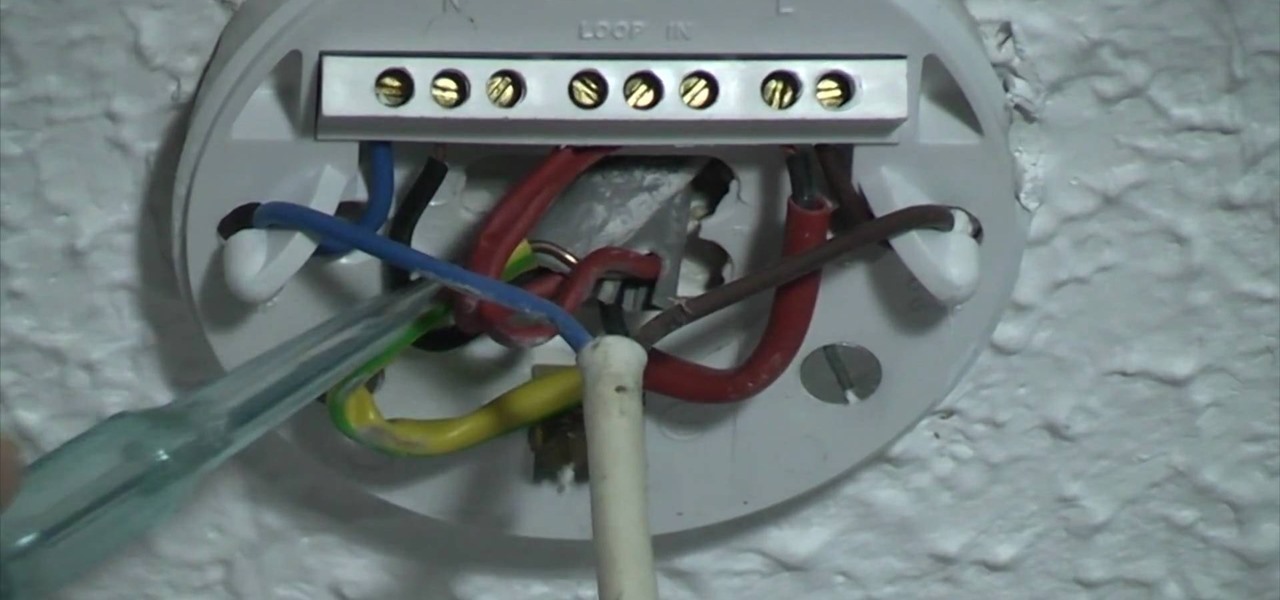
Modernize your home with a new ceiling light fixture. That old, traditional ceiling rose with the decorative chandelier or light fitting might just not look right anymore, with all of your modern furniture and appliances. The best thing… replace it.

In this soaring demonstration, deaf percussionist Evelyn Glennie leads the audience through an exploration of music not as notes on a page, but as an expression of the human experience. Playing with sensitivity and nuance informed by a soul-deep understanding of and connection to music, she talks about a music that is more than sound waves perceived by the human ear. She illustrates a richer picture that begins with listening to yourself, and includes emotion and intent as well as the complex...

In this clip, you'll learn how to speed up the Internet connection on a PC running the Microsoft Windows 7 operating system by using custom external DNS servers. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Having a backup sump pump is integral in making sure your basement is always protected from water, and if you have the Basement Watchdog battery backup sump pump system, this video will show you the complete installation procedure. Find out how to build a pipe connection to the discharge pipe, install check valves, connect to the backup system and more.

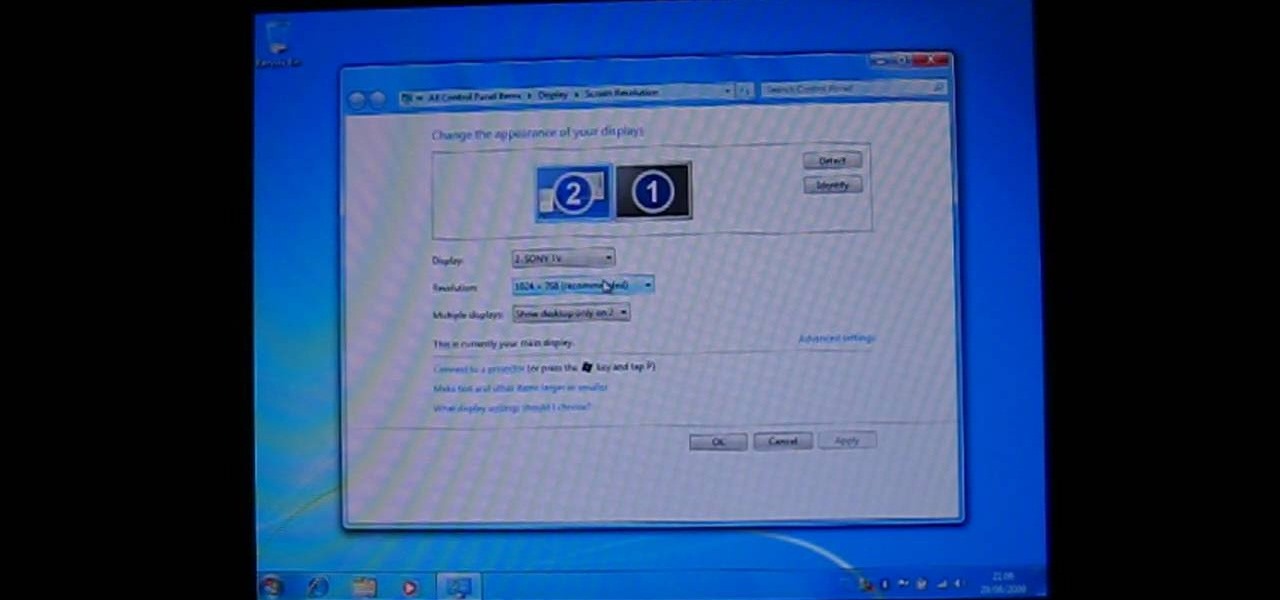
This Windows tutorial demonstrates how to connect a laptop with an Intel graphics card to a TV using the VGA port output in the laptop and a VGA cable.

If you have T-Mobile and haven't quite figured out how to get MMS working with it on the iPhone, check out this video. This tutorial will cover activating the iPhones original MMS feature to work with t-mobile. This feature also allows you to share your iphones internet connection with other computers.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Need some IBM Lotus Notes help? Well, check out this video tutorial to learn how to connect to a Lotus Domino Server from Lotus Notes. This is a very quick connection to the Lotus Domino Server from Lotus Notes. Easy to follow.

No more q-tips! No more alcohol! No more blowing in your cart! Did you know alcohol actually damages the carts? This is a much more effective, safe and long term way to restore the connection.

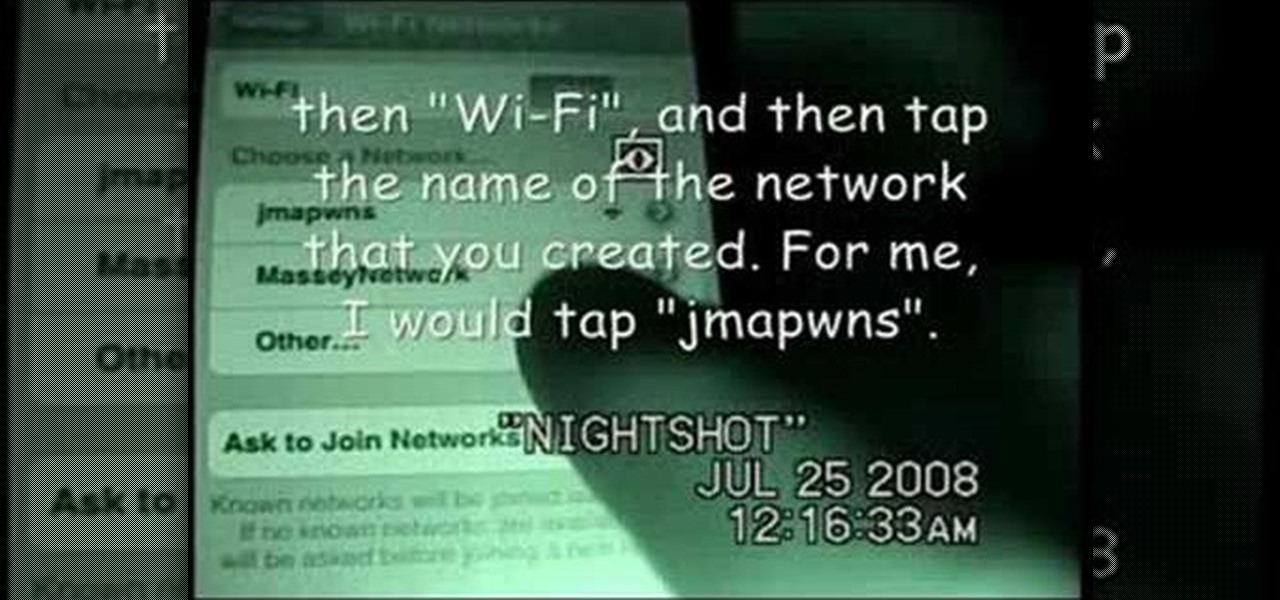
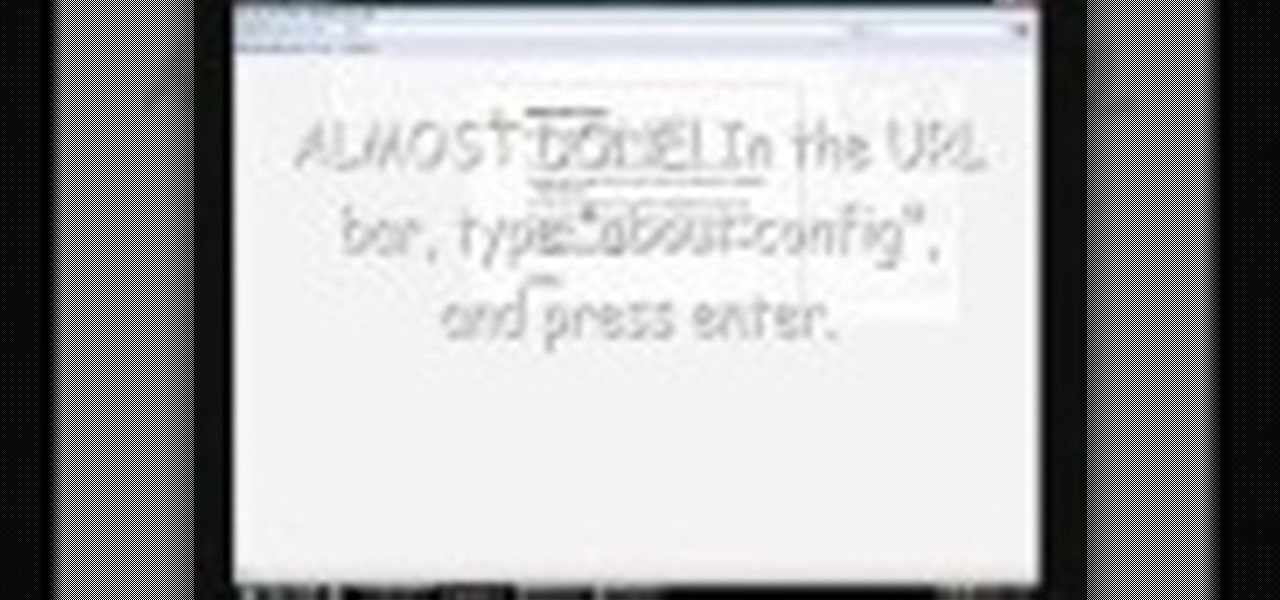
This is a nifty tutorial guide on how to tether your hacked iPhone or iPhone 3G to a windows computer for use as a high speed modem. Just Jailbreak your iPhone using one of the many tutorials on WonderHowTo, and install 3proxy. This video explains the rest of the configuration steps required to properly tether an iPhone 3G in Windows XP so that you can use its EDGE or 3G internet connection on your PC, for free.

This video will show you how to tether an iPhone 3G in Windows Vista so that you can use its internet connection on your own computer!

Watch this iPhone video tutorial to learn how to save those iPhone Web apps so you can use them even when you have no connection. This how-to video will help you learn how to use offline iPhone applications like a pro in no time. Perfect for new iPhone owners.

BPS golf instructor Steve Bishop discusses a particular technique used to improve your mental connection between what you want to do, and what you are doing.

When working in a network, you can't always see the connection lines if you are too zoomed out. This tutorial shows you how you can quickly connect nodes in Houdini.

Watch this video to learn how to use Google docs. You can view and edit your documents offline, without an active internet connection.