You know how sometimes you accidentally send a minecart shooting out down your tracks, and you can only watch helplessly as it fades into the distance? And then you know that you have to go find it and break it, so that it doesn't stop up your cart traffic on your tracks.

Sometimes you just want to grill. It doesn't matter where you are, what you have, or whom you're with—you just want a delicious burger and you don't care what it takes.

Mountain Lion (OS X 10.8) is out today, available in the Mac App Store for just $20. Unfortunately, installing Mountain Lion requires that you already have a Mac running Snow Leopard (OS X 10.6) or Lion (OS X 10.7). If you're currently running a Leopard system, you're out of luck, and need to pay $29 to upgrade to Snow Leopard, and then an additional $20 to upgrade again to Mountain Lion. That sounds like way to much trouble to me. But why exactly is Leopard incompatible? Turns out it's not—m...
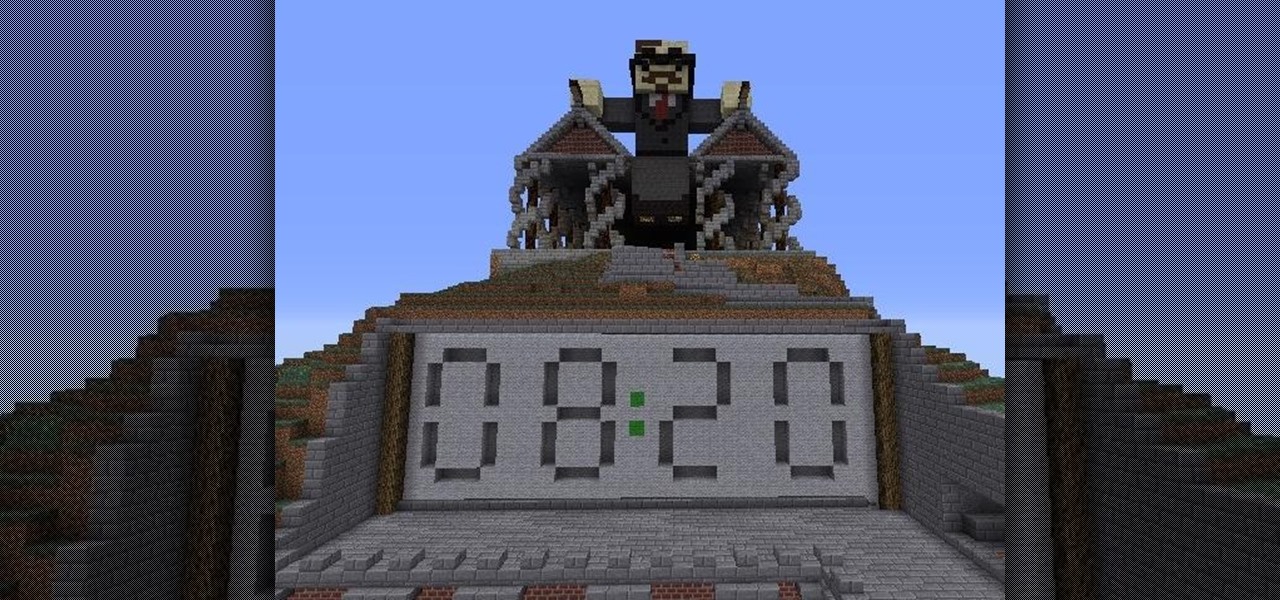
A redstone clock is a pretty easy mechanism to make. A digital readout for that redstone clock is a little harder, and that's what Lesnoydude has made that won him the staff choice award.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Make a multicolored friendship bracelet. But be prepared! Your friends will all want one, too. Go to http://www.wonderhowto.com/how-to/video/how-to-start-a-woven-friendship-bracelet-278802/ for a video on how to start the actual bracelet.

This scooter modification tutorial gives you some tips on how to bolt a velocity stack to a 28mm Mikuni carburetor on a Honda Elite DIO scooter exhaust system. The video doesn't cover the actual install but gives tips on ways to make the connection easier.

A tutorial on how to turn your laptop or desktop PC into a Wii, for under $50, and in less than 10 minutes. Note* this will not play actual Nintendo Wii games but will allow you to use the Wii modality to play PC games and games made specifically for this setup.

Although mainly demonstrational, this video shows you how to play the melody "Lord Mayo" on guitar. This video is intended for advanced players who learn easily by watching or listening. Read the useful tips posted below to aid your guitar learning:

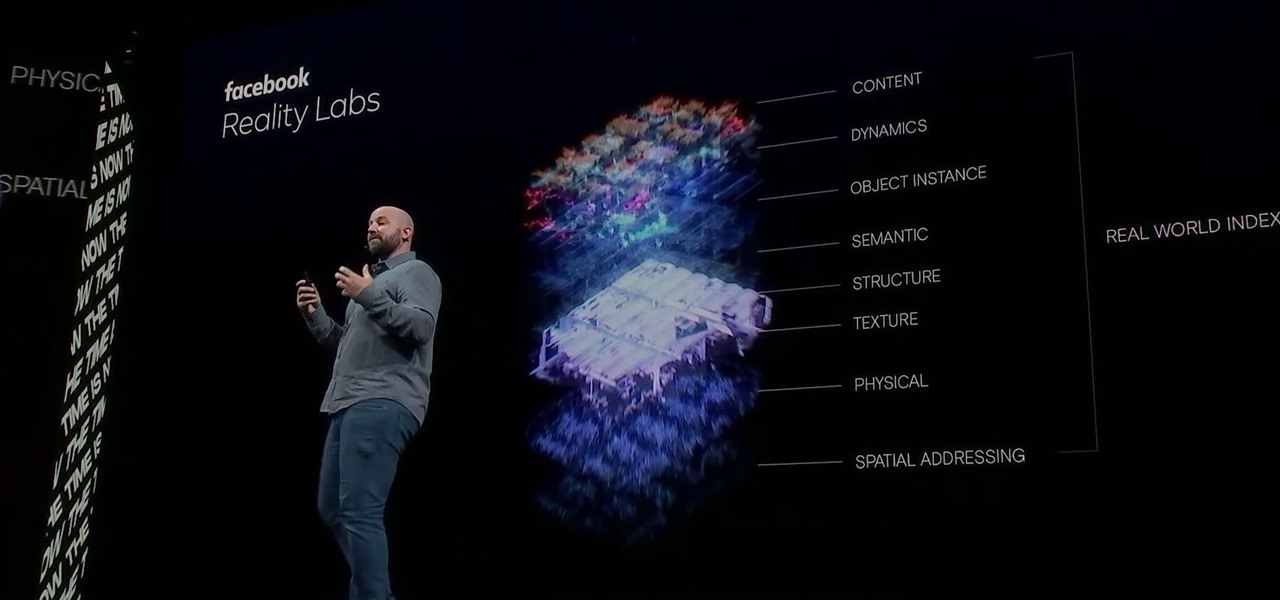
Facebook had a pretty big week in terms of augmented reality, with much of its news coming from the Oculus 6 keynote presentation. But Mark Zuckerberg's social media company found other areas of impact outside of Oculus 6 as well.

Some investors play the short game, placing their bets on industries that show the quickest return on their investment, and, in the augmented reality space, that means the enterprise sector.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

Sleep lets our body processes rest and restores us for the next day, so a bad night's sleep can ruin the following twenty-four hours and even make us feel sick. Now, new research published in the journal Sleep cements the idea that loss of sleep actually leaves us vulnerable to sickness.

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something like that) and pentesting, but never made a full return. I will be occasionally coming back for a while.

Want to show all your foodie friends that you're really in the know? Then it's time to master the art of making edible dirt. Chefs out there are finding ways to take various foodstuffs and dry, char, and combine them to give the appearance of actual dirt—only with a rich, savory taste.

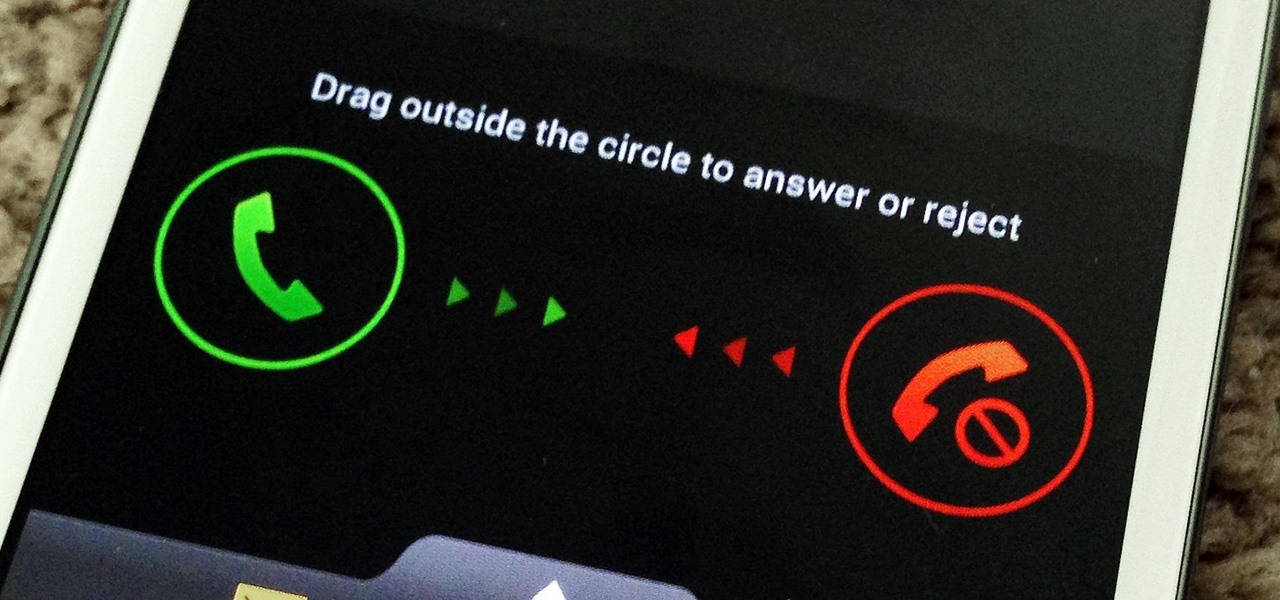
You don't have to be in debt to receive annoying calls from unwanted numbers. You may love your grandma, but if she calls you three times a day to ask how to turn on the television, you might just want to push all of her calls to voicemail.

This video shows you how to apply eyeshadow on your upper and lower lash lines to look like eyeliner. You would need a Q-Tip and any color eyeshadow that you like - though the instructor recommends dark eyeshadow so it will look the most like actual eyeliner. You take your Q-Tip, bend it, and wet the tip. You then take the dampened Q-Tip and dip it in your powder eyeshadow. This creates a paste type effect. Now you can draw the q-tip across your upper lid, close to the lashes, and it will loo...

This video is about a particular pool or snooker game shot technique called "Shooting or Going around the Angles." The presenter, with a alias name of 'Forcefollow', first describes a particular 9-ball pool game situation that would require this technique, using a computer generated picture image to show an overhead view of the pool table, with the pool balls in question placed at certain locations within the table and showing the various angle trajectories paths of the desired ball to be str...

Kiwua demonstrates how to make a woven yarn friendship V bracelet. There are three chapters, click on all of them to see the full tutorial.

Have you always wanted to make a prank call but never had the guts to do it? Well, now you can because there's the Internet. In order to make a cool prank call without getting caught, first you have to choose a voice. The best one to choose is Arnold Schwarzenegger. To get his voice, go to Google and search for Arnold soundboard.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

When you have a personal Instagram account but also manage other profiles — like ones for work, your entrepreneurial startup, an alter ego, or your famous pet, to name just a few examples — how do you manage them all from the same device?

Safari has always done a great job at letting you browse the web, but it has never so much as offered a way to download files locally. Other apps have stepped in to help fill the gap, but they never felt as integrated into the iPhone as a native downloads manager would. They aren't needed anymore though, because Apple added one in iOS 13, pushing Safari on the iPhone closer to its sibling on the Mac.

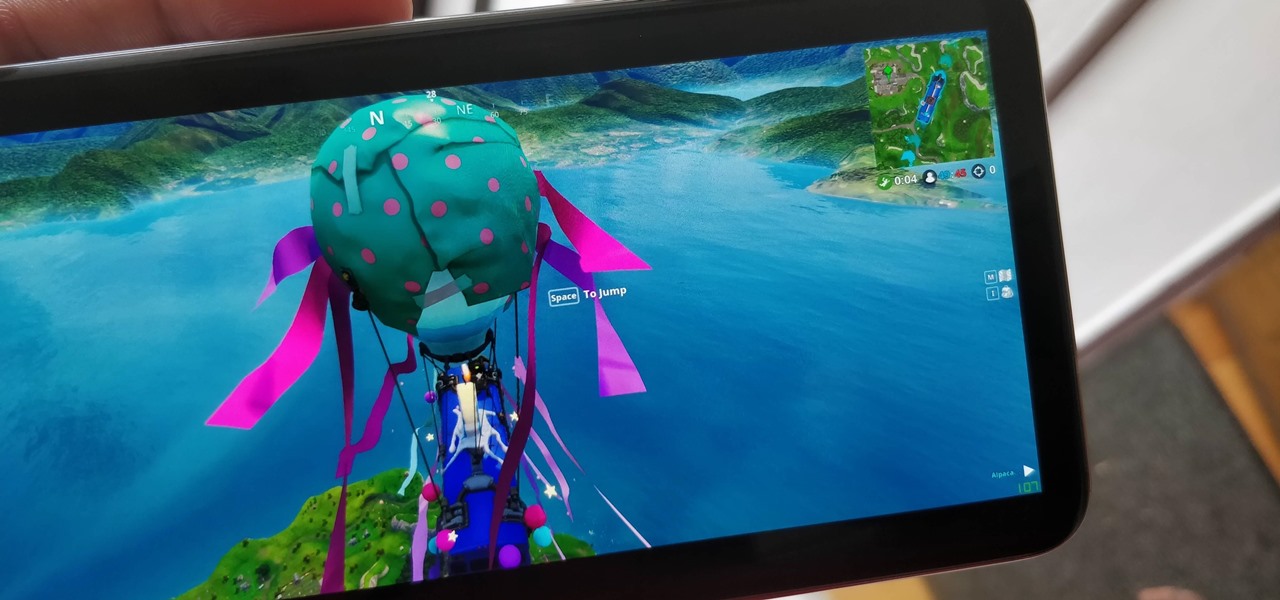
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

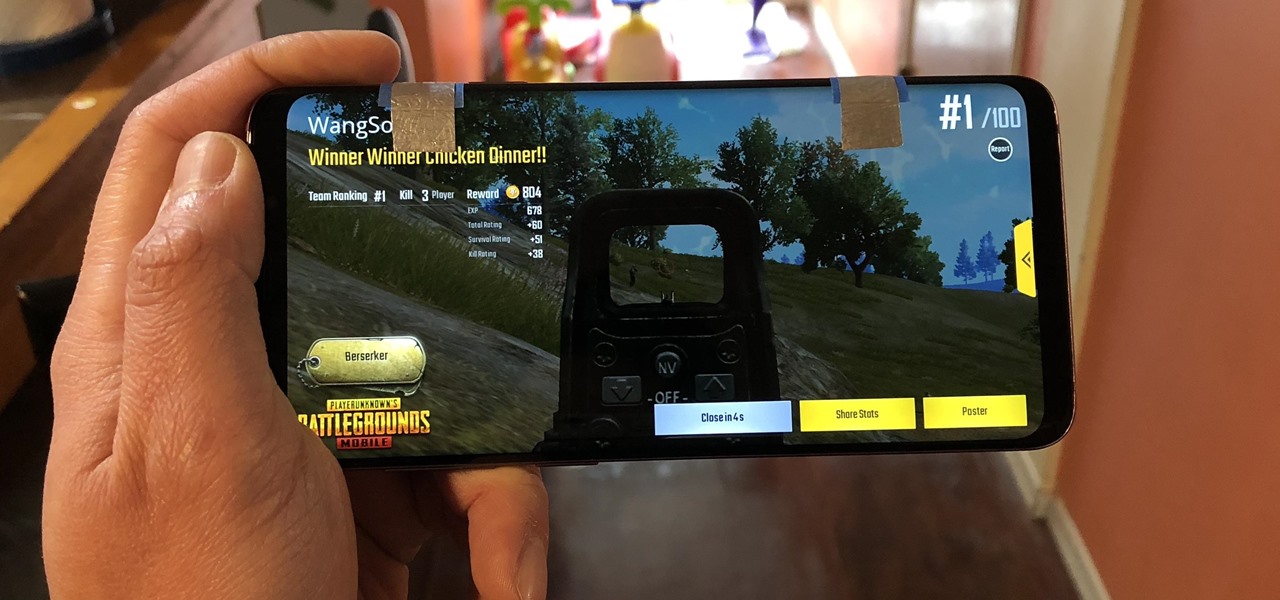
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's not exactly easy with a touchscreen.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

After spending a good portion of 2017 teasing us with images and bits of news, Lenovo, in a partnership with Disney and Lucasfilm, has finally released its Mirage AR headset along with the Star Wars: Jedi Challenge game collection.

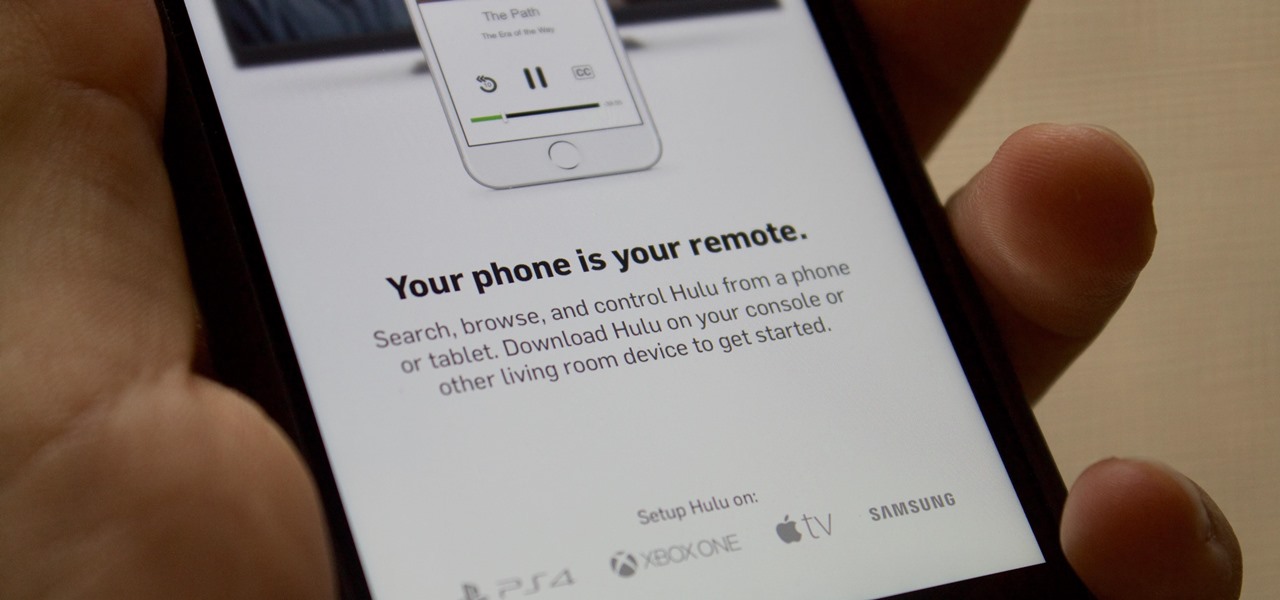
Your smartphone is the perfect place to watch Hulu on the go. Whether you're looking to catch up on your shows in a hotel, or your phone is the only screen available, mobile streaming can be a lifesaver. But what about when you have access to a TV? Wouldn't you rather watch your favorite Hulu Original on the big screen than on your comparatively tiny smartphone?

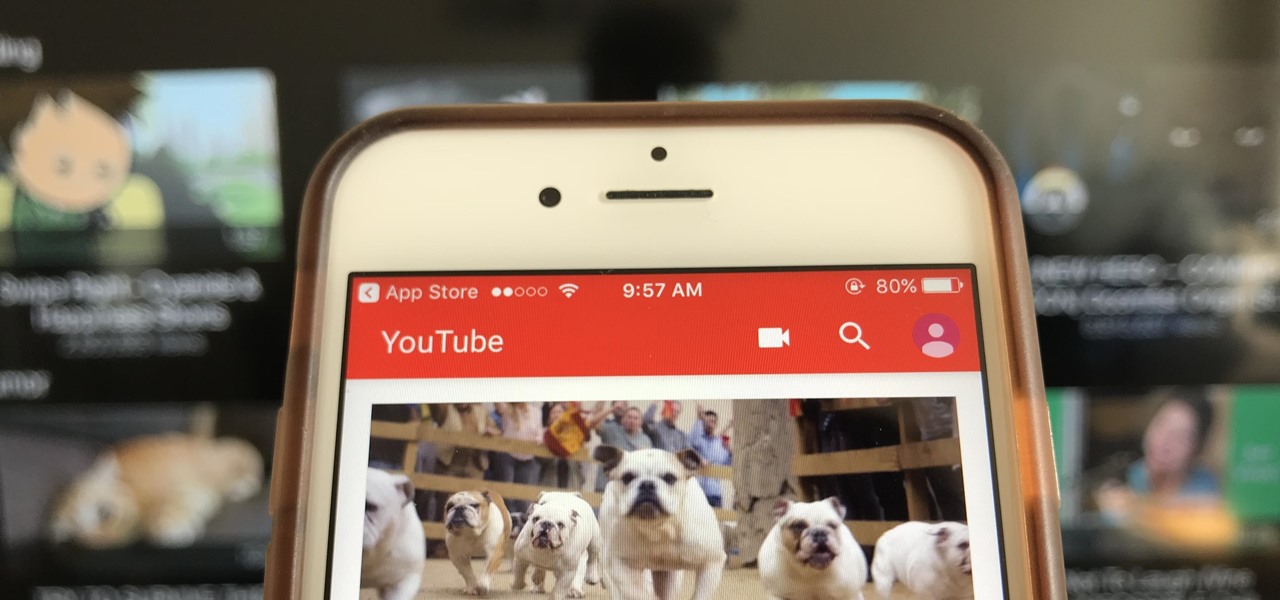
Watching YouTube on your phone has never been a better experience than it is today — our smartphones have super-sharp displays that make watching the newest HD, QHD, and even 4K content look fantastic. But there are plenty of circumstances where we want to watch our content on a larger screen.

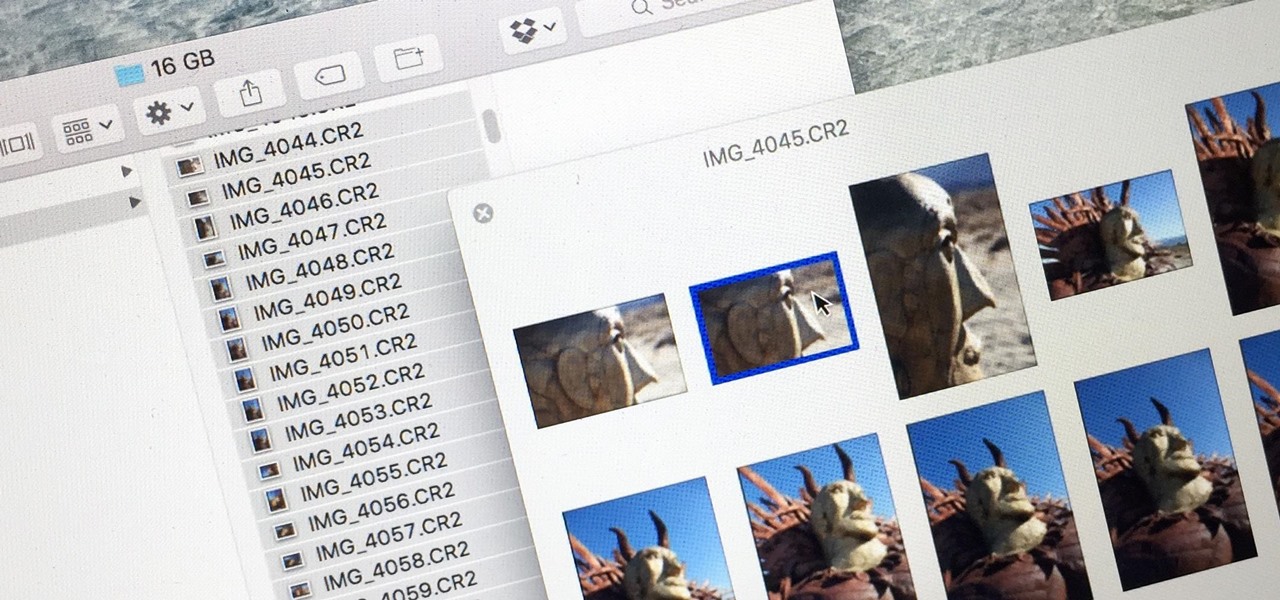
Quick Look, first introduced in 2007, is an instant preview feature on the Mac operating system that lets you view files and folders without opening them up. Just highlight a file, like a picture or text document, then press the spacebar on your keyboard to get a speedy preview of it.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.