Public beta testers are in for a treat today. While Apple is extremely inconsistent with the release schedules for the developer and public betas, the company has once again released both versions of iOS 12.2 beta 5 today, March 11. If you're a public tester, you now get to experience all of iOS 12.2's new additions for yourself, instead of needing to read about them for up to 24 hours in advance.

Augmented reality and computer vision company Blippar has a new lease on life, as previous investor Candy Ventures has completed a successful bid to acquire the assets of the beleaguered company.

YouTube has a couple of basic gestures: you can double tap each half of the video to skip forward or back ten seconds, and you can swipe down to minimize the video. But wouldn't it be more useful if there were gestures to control brightness and volume? Well, as with all things Android, where there's a will, there's a way.

AMC Theatres was never a fan of MoviePass and even predicted its unsustainability. After the struggling MoviePass turned off diehard fans with too many new restrictions to combat its cash problems, AMC stepped in to save the day with its AMC Stubs A-List subscription for cheaper movie tickets.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

Each year, Apple seems to design its devices to be more difficult for owners to repair themselves. So when an iPhone breaks, a trip to the Genius Bar or an Apple Authorized Service Provider is most likely necessary. But if you have an iPhone X that needs a new battery, a leaked video just spilled the beans on how to replace the battery precisely as Apple would.

We've shown you the best augmented reality headsets, and now it's time to show you the rest. These are the AR headsets you've probably never heard of or even seen. The AR headsets that, in some cases, have a shot at the big time, and may one day reach widespread adoption, and, in other cases, are unwieldily contraptions that look like something out of a weird science fiction movie.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

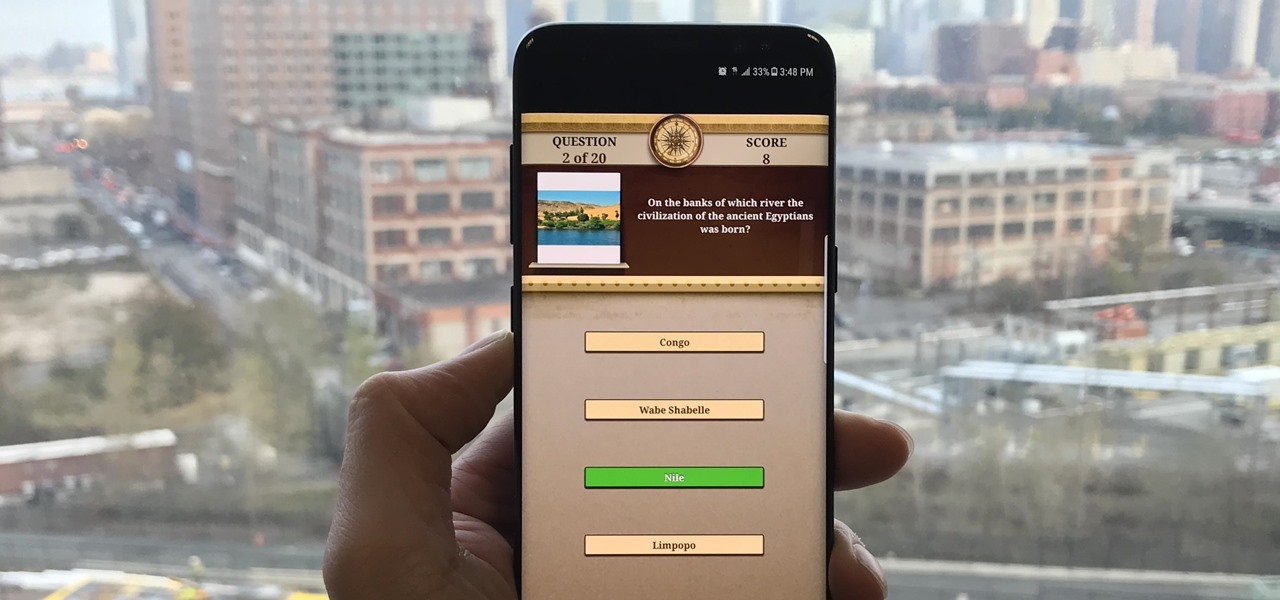
Trivia games are among the most entertaining ways to learn factoids and interesting info you may have never known about before. They're also the perfect genre to enjoy with friends and family, as they're particularly great at breaking the ice to make for a more memorable time together.

When you run an augmented reality company worth billions of dollars, backed by some of the biggest names in tech, and you haven't even released a product yet, even late night tweetstorms rank as worthy of dissection. Such is the case with Rony Abovitz, CEO of Magic Leap, who decided to spend a little time on Twitter on Wednesday to outline his vision of the future of immersive computing.

When it comes to technology, there are no bigger names than Google and Apple. They're the two most valuable companies in the world, and they've swapped places a few times over the last year, so they're truly neck-and-neck. But let's put business aside for a moment — which of these companies makes the better flagship phone?

Not to be outdone by Apple and it's new line of flagship phones, Google has followed suit and finally announced the followup to their highly regarded Pixel line of handsets — the aptly named Pixel 2. Thankfully, the tech giant has also joined in on the trend towards more durable devices, and has engineered both the Pixel 2 and Pixel 2 XL to have a rating of IP67 under the IEC standard 60529.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

The search is on to find antibiotics that will work against superbugs — bacteria that are rapidly becoming resistant to many drugs in our antibiotic arsenal.

I spent just about my entire weekend trying to break the 800, 900, and 1,000 levels of Instagram — because it's a game, y'all — by playing around with my follower count. I shamelessly manipulated my IG account in such a way that was extremely time consuming and left many of my friends pretty pissed off at me as I spent most of my time glued to my phone. (Sorry, friends. I know I'm obsessed.)

Mosquitoes are a big problem, and citronella candles are not the solution. There are a lot of mosquito species. The American Mosquito Control Association reports there are more than 3000 mosquito species in the world, and about 200 of those occur in the US. The most common are the Aedes, Anopheles, and Culex species. These are also the three mosquito species most likely to transmit serious illness, and all of them live in the US.

A groundbreaking new Android feature called seamless updates was announced at Google I/O 2016. No longer would we have to wait for updates to download and install — instead, they'd be applied silently in the background, and the new Android version would be waiting on us the next time we restarted our phones.

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

Colorado State University scientists have developed new tech that quickly identifies the presence of Zika virus in mosquito populations — and in human body fluid.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

You may have heard that Samsung Push is an incredible service that all Android users absolutely love. For one, Push provides extremely useful notifications for Samsung apps to assist you in all aspects of your life.

The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

A new study confirms that antibiotics can prevent surgical intervention if your child's appendix becomes inflamed, potentially saving his or her life.

Every year, 100-200 people in the US contract leptospirosis, but usually 50% of the cases occur in Hawaii where outdoor adventurers are exposed to Leptospira bacteria found in freshwater ponds, waterfalls, streams, and mud. That's why it's so alarming that two people in the Bronx have been diagnosed with the disease and a 30-year-old man has died from it.

Responding to the emergence of Zika in the US, researchers investigated what type of repellent works best to reduce your odds of a mosquito bite from Aedes aegypti, the mosquito species that spreads the Zika virus.

Where in the world did it come from? All of a sudden, one day, someone had an infection with flesh-eating bacteria. It captured headlines and worldwide attention because it was such a severe, strange, uncontrollable, and really disgusting condition.

When the time comes to replace your car, you most likely have a checklist of criteria that you would like on the new one. Your car is possibly the most expensive possession you have—or the second-most expensive, after your home—so you want to make sure that you are not only getting what you want, but that you are getting the best deal possible.

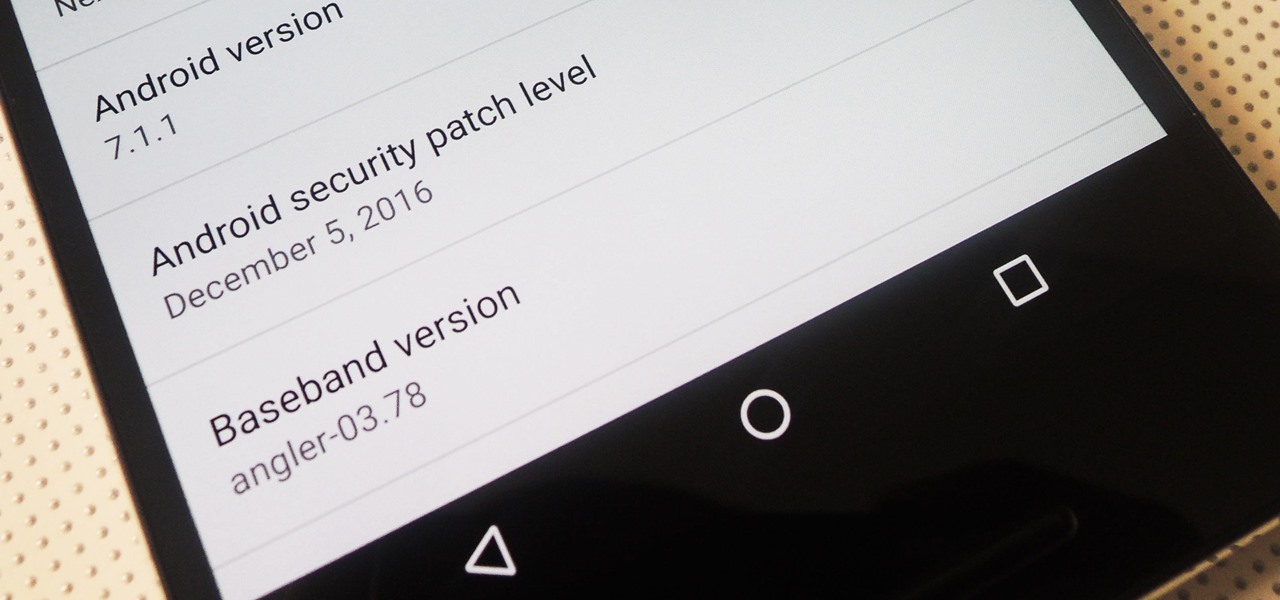
Android 7.1.1 stock images for the Nexus 6P were released last week on December 5, 2016. However, Verizon users seem to have been excluded from the update. Google's factory image page states "All carriers except Verizon" next to version number NMF26F. This doesn't seem fair, especially since Verizon Nexus 5X users received the latest Android Nougat update.