Typography is an important aspect of the video editing process. You deal with it when adding captions to news clips, giving on-screen recipes in food videos, creating burned-in subtitles for short films, making no-sound-needed videos for social media, and so much more. Enlight Videoleap for iOS makes this all easy.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Update: The LG G8 ThinQ has been announced. You can read all of the official specs at our full article on the new phone.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

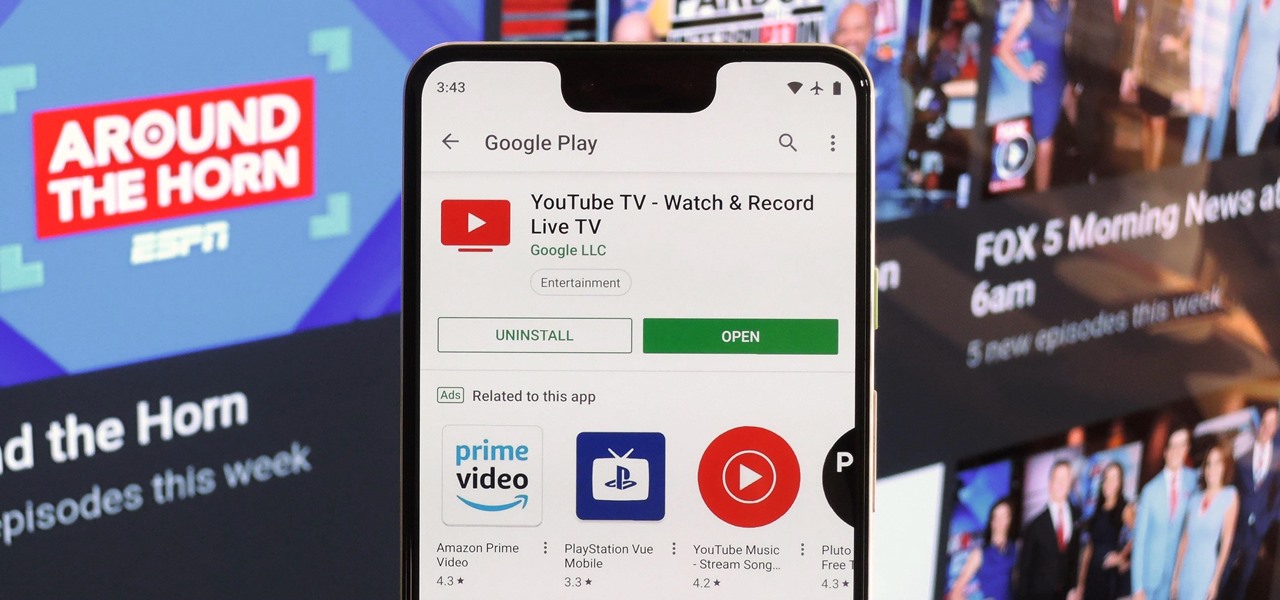
With YouTube TV and DirecTV Now starting at $40/month, and others like Sling TV offering an eye-catching $25/month plan, streaming cable services may sound like a great way to cut costs while cutting the cord. But when you look at all the factors, the price you pay may very well end up being just as high as your traditional cable bill — if not more.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

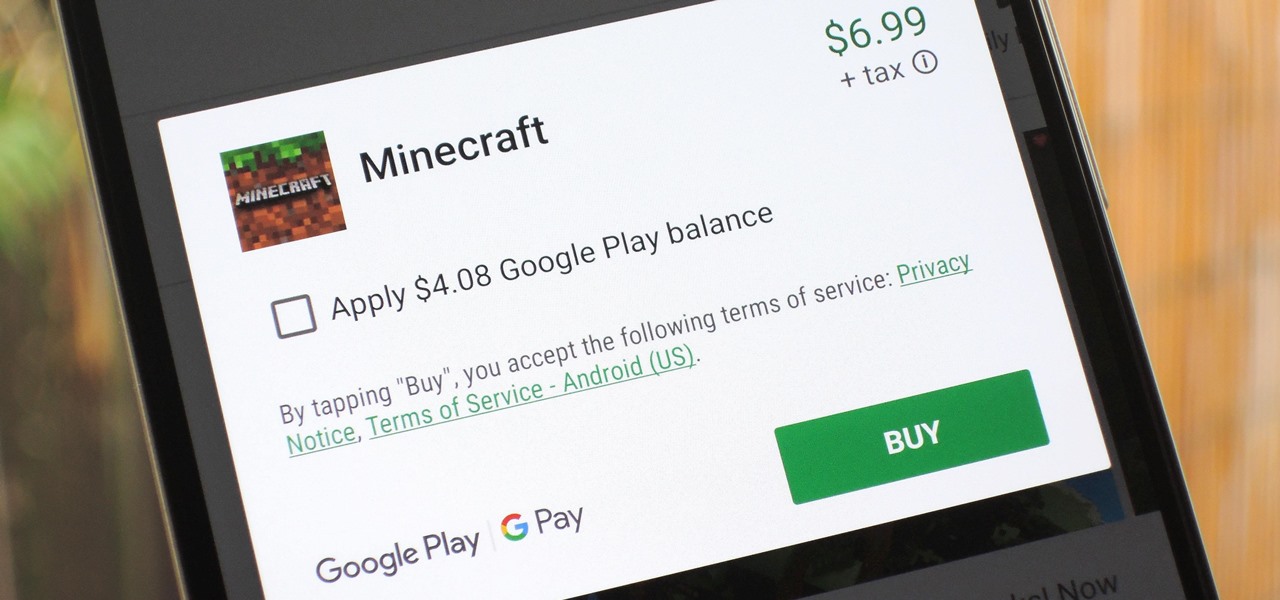
The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.

Besides the Apple vs. Samsung competition, few battles are as vocal as the battle between the best Pixel and best iPhone. This year, it's the Pixel 3 XL and iPhone XS Max, two phones that are equipped with minor hardware updates from their predecessors, though both showcase significant OS-level improvements.

The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS.

If you've ever been on the receiving end of a threatening phone call, you'll immediately know the value in being able to record phone conversations on your iPhone. Beyond that extreme example, however, recording calls is still an extremely useful feature to have for important conversations like business meetings and verbal agreements, and it's totally doable with a third-party app.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

With new iPhone models out, you'll have updated cameras to try out, a faster processor, and new colors to choose from. The only thing that could stop you from picking one up yourself is, well, your current iPhone. Here's how to check if you're eligible to upgrade to iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max, or any other iPhone still being sold.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

In most macOS hacks, a non-root terminal is used to create a backdoor into the device. A lot of damage can be done as a low-privileged user, but it has its limitations. Think twice before granting a file permission to execute — an attacker might be able to convert your harmless scripts into persistent root backdoors.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

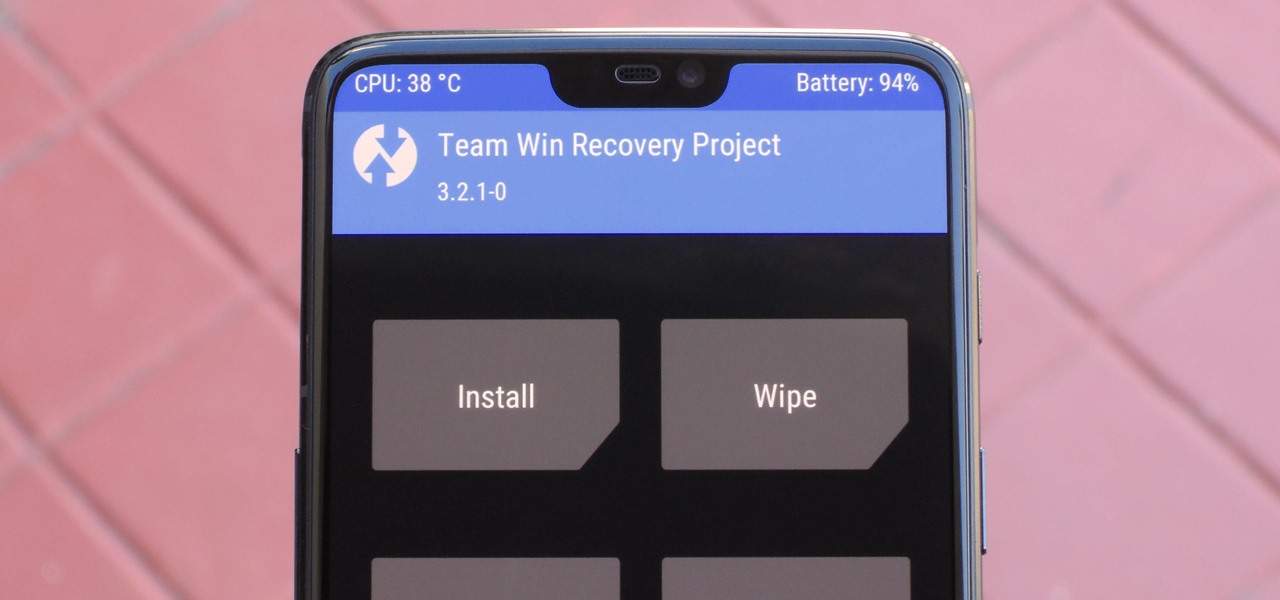
When it comes to modding Android, there's no better tool than Team Win's TWRP custom recovery. You can use it to root your phone, flash mods like Magisk or Xposed, and even replace the entire operating system with a custom ROM like LineageOS — honestly, there's not much this utility can't do.

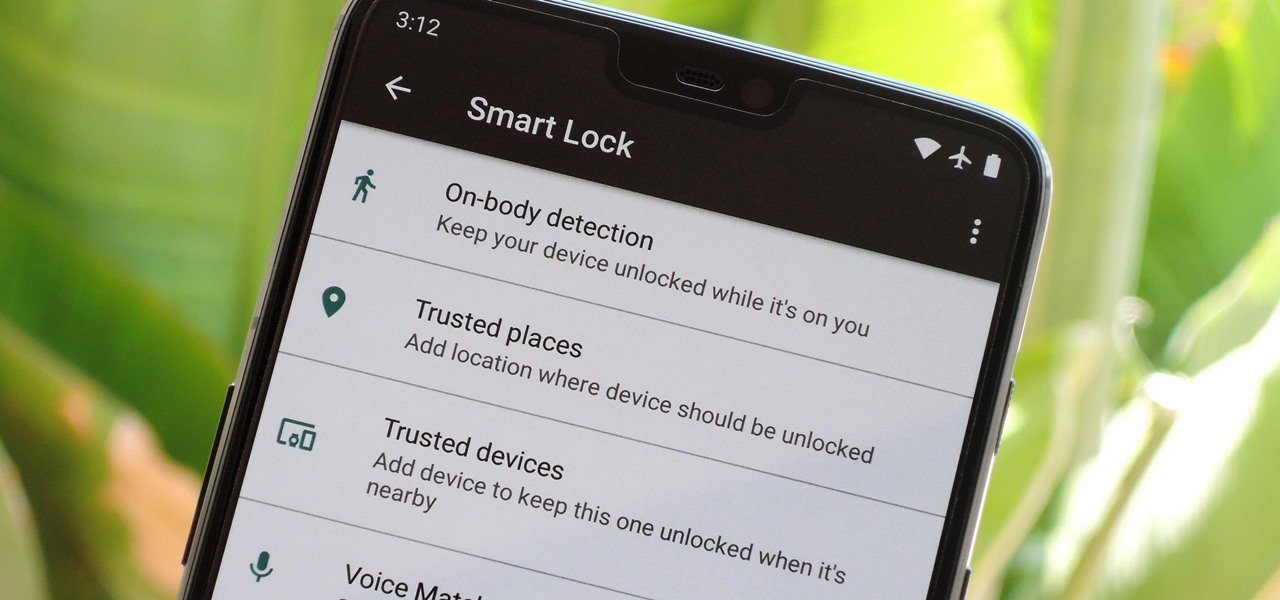
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.

Apple's own Photos app received some pretty amazing updates in iOS 11, but does iOS 12 have what it takes to one-up last year's Photos improvements? We think so.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Apple's goal with iOS 12 is to smooth out the problems with its famously flawed predecessor. Of course, change isn't for everyone, and by iOS 11.4.1, Apple had a pretty stable thing going. If you're not digging all the bugs and new features included in iOS 12, here's how to downgrade your iPhone back to iOS 11.4.1.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

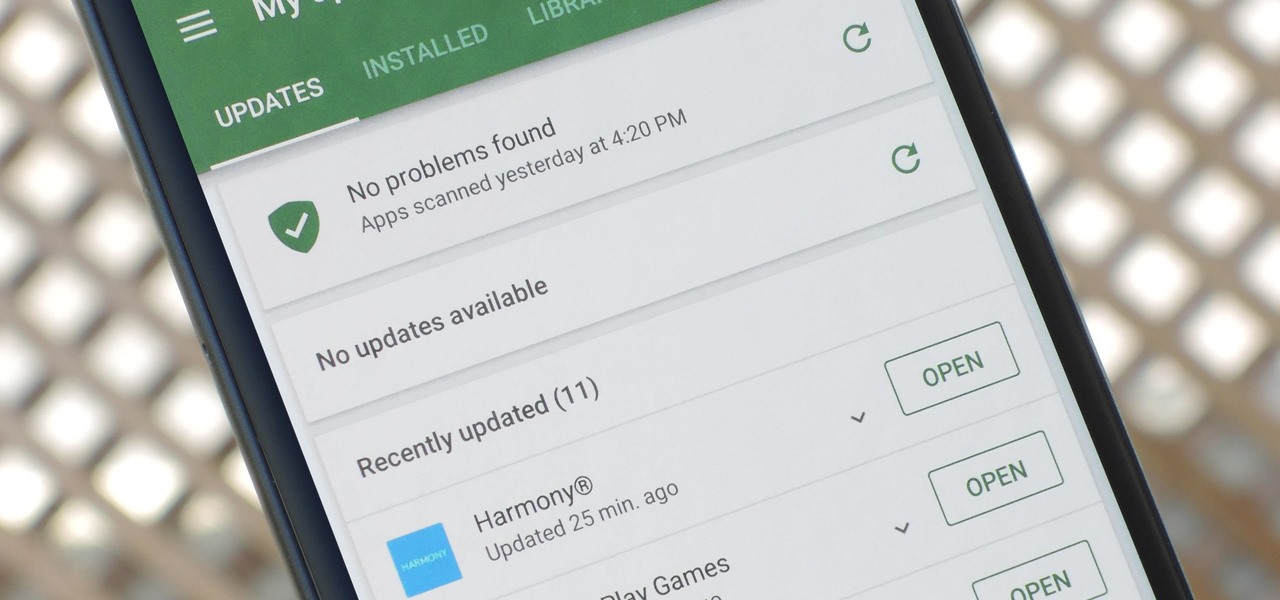
App updates bring new functionality, but they can also break old features or introduce changes no one wants. Unfortunately, if you're holding onto an older app version because you don't want to accept the update, it becomes a lot harder to keep the rest of your apps updated.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.

While everyone was marveling at the latest drama over at Magic Leap involving employees last week, a major rumor listed in one of the reports, related to the company's flagship device, was mostly overlooked.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Starting your morning right is an essential first step to a productive day. Whether you're running late, rushing to catch up on the day's news, or lagging behind with early emails, little hiccups like these can have a trickle-down effect and ultimately ruin your day. Like with many problems, though, your smartphone can help.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

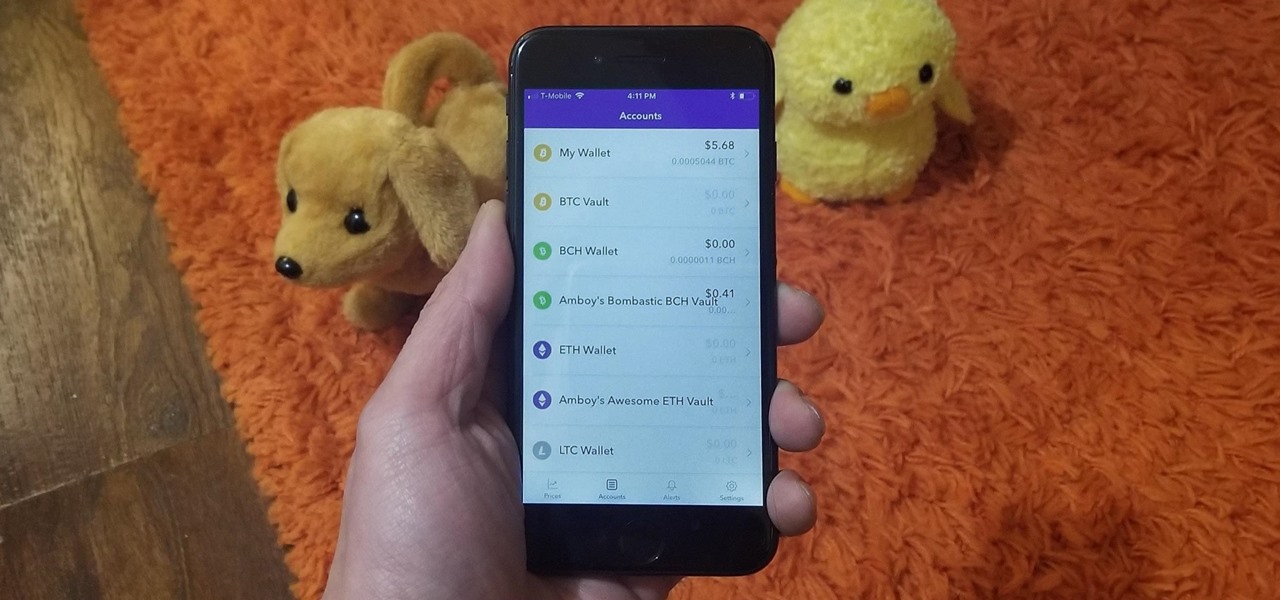
As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.