To get to the actual tutorial, skip to 2:23. Bethany, oh Bethany. What would we do without you? Bethany's makeup tutorials are completely inspired. She covers everything from cartoon characters to action figures to tv show characters and manages to make totally cute eye makeup based on al of them! All of her pretty eye makeup looks are nostalgic of childhood memories and favorite bands. Be sure to check out the rest of Bethany's tutorials on WonderHowTo.

This tutorial video will show you how to contour and highlight your skin with makeup. Contours are "shadows" so you want to go darker than your actual skin tone.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

There once was a time in the Android rooting scene where we couldn't rely on using a custom recovery for all of our modding needs. Manual file flashing was very popular in the early days of Android before custom recoveries started taking over. With the rise of TWRP, it seemed like there was almost no need for manual file flashers; however, they appear to be making a welcomed return in a big way.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

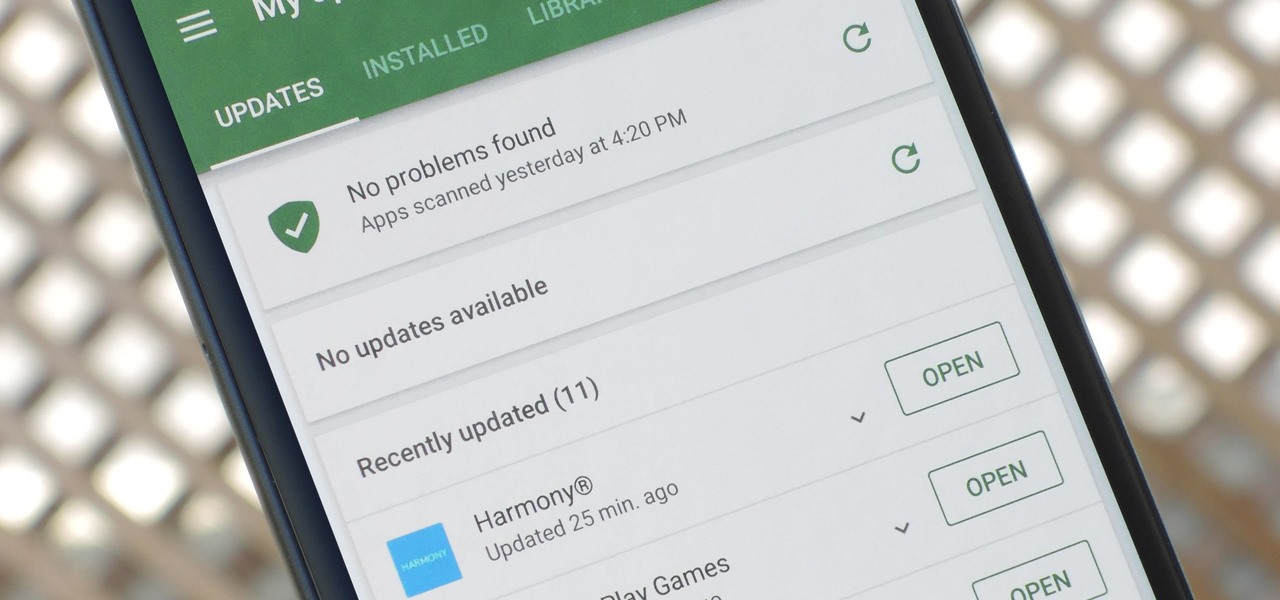
App updates bring new functionality, but they can also break old features or introduce changes no one wants. Unfortunately, if you're holding onto an older app version because you don't want to accept the update, it becomes a lot harder to keep the rest of your apps updated.

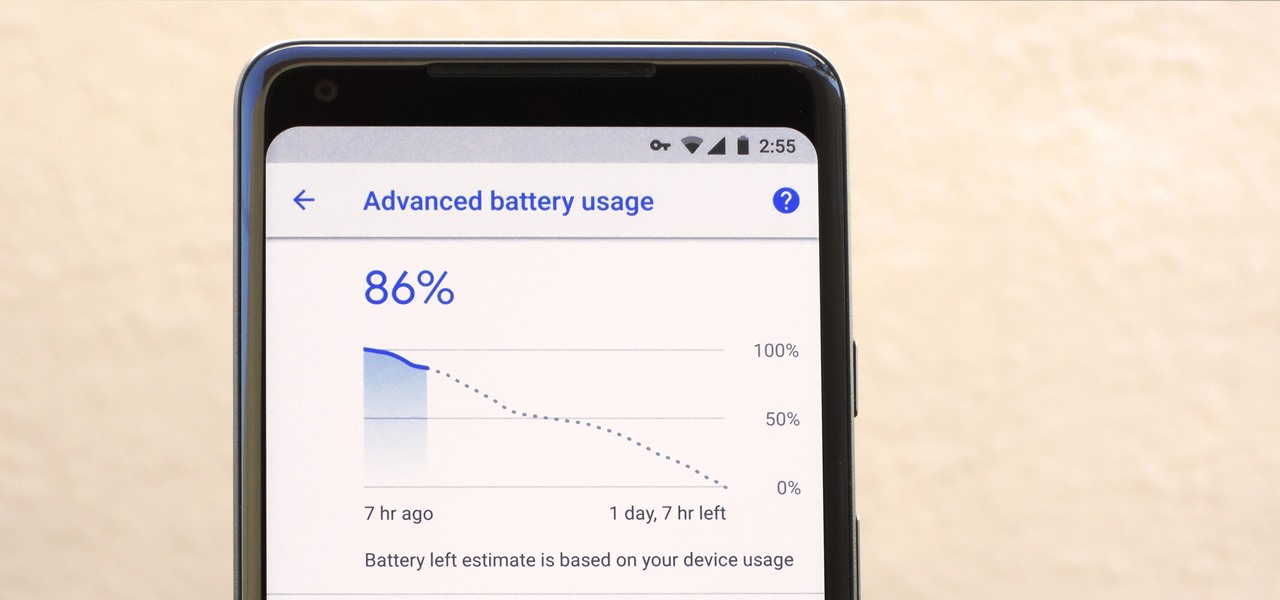
After Apple's recent fiasco, it's now common knowledge that smartphone batteries degrade over time. But aside from causing terrible battery life, a degraded battery can also trick your phone's software into thinking the device has more juice left than it actually does.

One of the biggest gripes we always hear about is the changes OEMs make to Android's notification shade. Icon styling and home screen layouts can be fixed with custom launchers like Nova and Action, but we're stuck with the tacky Quick Settings theme our phones came with. Today, we no longer have to envy Pixel 2 owners, as a new app will give you that clean stock Android look on any phone.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Android Oreo may not be the flashiest release, but it's got tons of under-the-hood changes. We recently discovered documentation in the AOSP source code that outlines one of these understated features, which has been dubbed "Rescue Party."

To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship.

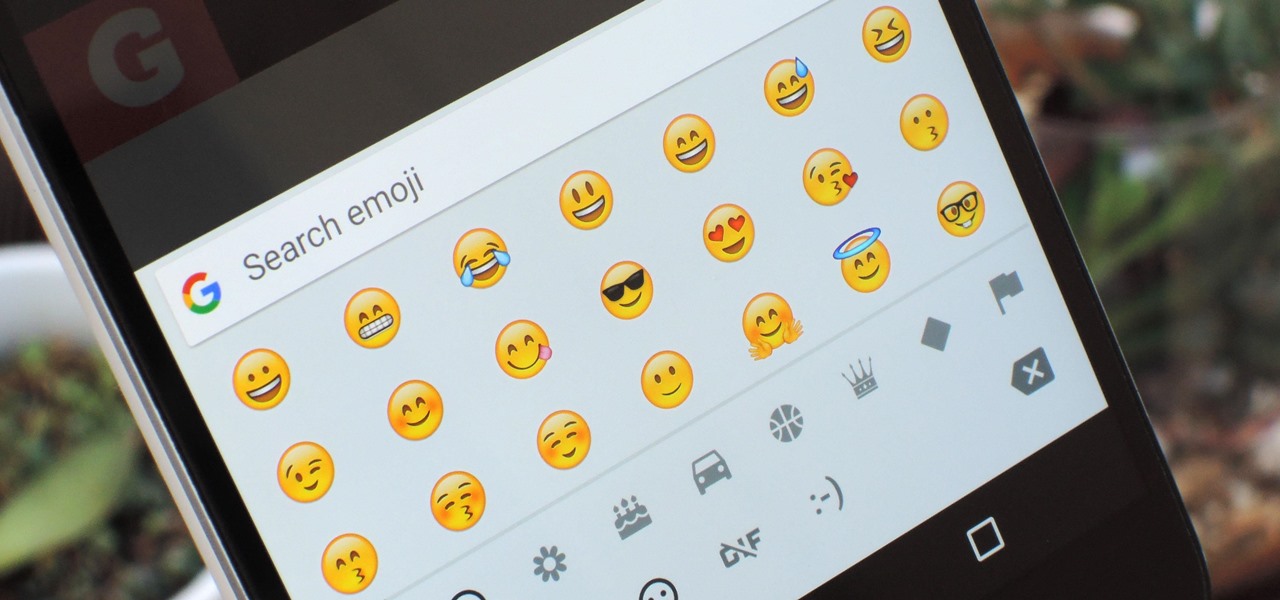
Everyone loves emojis, but some folks aren't quite happy with the way the little yellow guys look on their particular phone. In order to replace them, however, your device needs to be rooted, and you'll usually need to perform some complicated procedure that ends up making your phone hard to update since it modified a ton of files on your system partition.

LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader is absolutely pointless, as having it locked will not hinder normal device usage, which is kinda true.

For some strange reason, Google Now is unavailable in several countries across the globe. Users from Albania, China, Cyprus, Malta, Nepal, Puerto Rico, Tunisia, and many more big countries have reported for years that the service doesn't work in their area, mostly likely because Location Reporting is not available in their region. This is really a shame, because Google Now has some great features.

A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

It just got a whole lot easier to decide whether or not saving $50 on Amazon's new ad- and bloatware-subsidized smartphones is worth the headache of having to see an advertisement on the lock screen every time you wake the device.

As Android's official app provider, the Google Play Store is packed with thousands of useful programs. But Google's terms of service is extremely restrictive, which means that countless apps simply don't qualify to be hosted on the Google Play Store.

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started

This Video will Show you how to Prepare Yarn before you do your Yarn Wraps, Braids, Faux Locs....etc

One of the biggest gripes I initially had with the LG G3 was the lack of options for the Shortcut keys, which are the volume keys that allow you to launch the camera or the QuickMemo+ app directly from the lock screen. I never use QuickMemo+, so having it as a shortcut was a complete waste of functionality.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

When a migraine strikes, it can be crippling. Intense and sharp pain not only at the temples, but radiating throughout the entire head; feelings of nausea and digestive discontent; an unbearable aversion to light, sound, and even the smallest of movements.

As Android owners, we ultimately have to look at our device and ask the difficult question: "Where the hell did all these applications come from?"

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

Due to the way Android works, you normally need to be rooted to uninstall the pre-loaded system apps, aka bloatware, that came with your device. This is because the underlying files for these apps are stored on your system partition, which can only be modified with root-level access.

When you think about it, YouTube may actually have one of the largest music collections on the planet. This is why, at $10 per month, Google's new YouTube Music Key subscription is a solid value for many users, especially with its inclusion of Google Play Music.

In the realm of Android mods, none is more powerful than a custom recovery. This is installed in place of the stock offering, and it lets you back up your entire system, flash mods, and install custom ROMs.

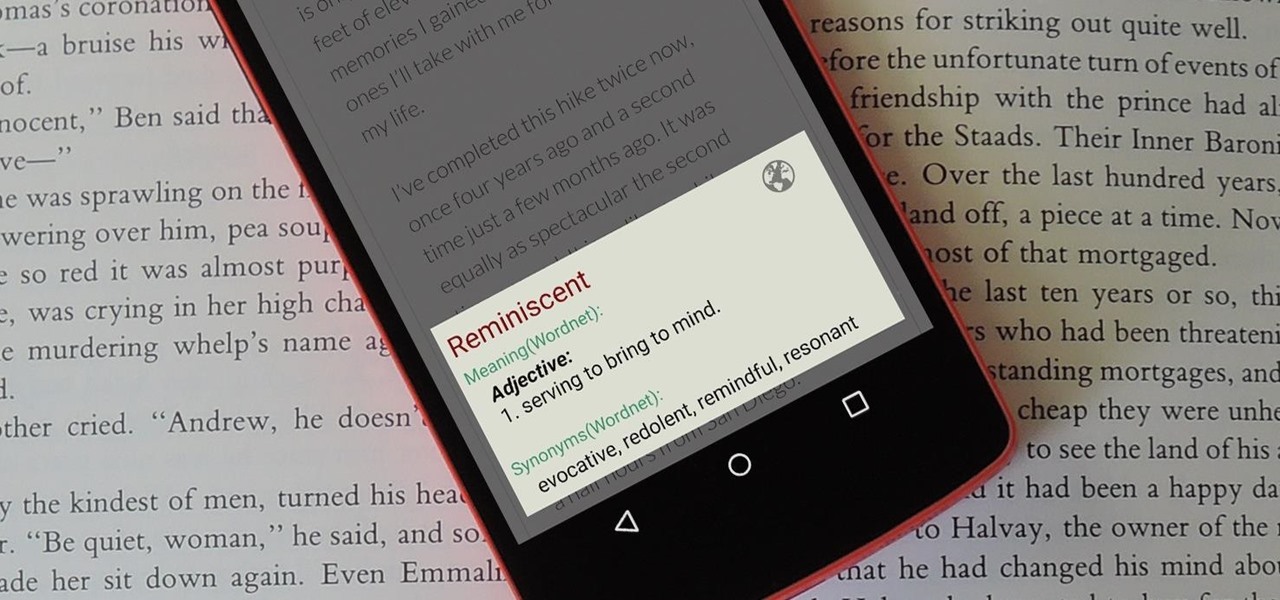
When you're browsing the web, going through emails, or reading a book or magazine, you'll occasionally come across a word or phrase that you haven't seen before. This would be a perfect time to have some sort of built-in dictionary lookup service, but most Android apps lack such a feature.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

When opening a link or sharing a photo, your Android device will bring up a list of possible applications that you can complete the action with. However, some of the apps included you never use or didn't even know existed, and this leads to unnecessary clutter. Fortunately, if you're rooted, there's an easy way to remove apps from the "Open with" and "Share via" lists.

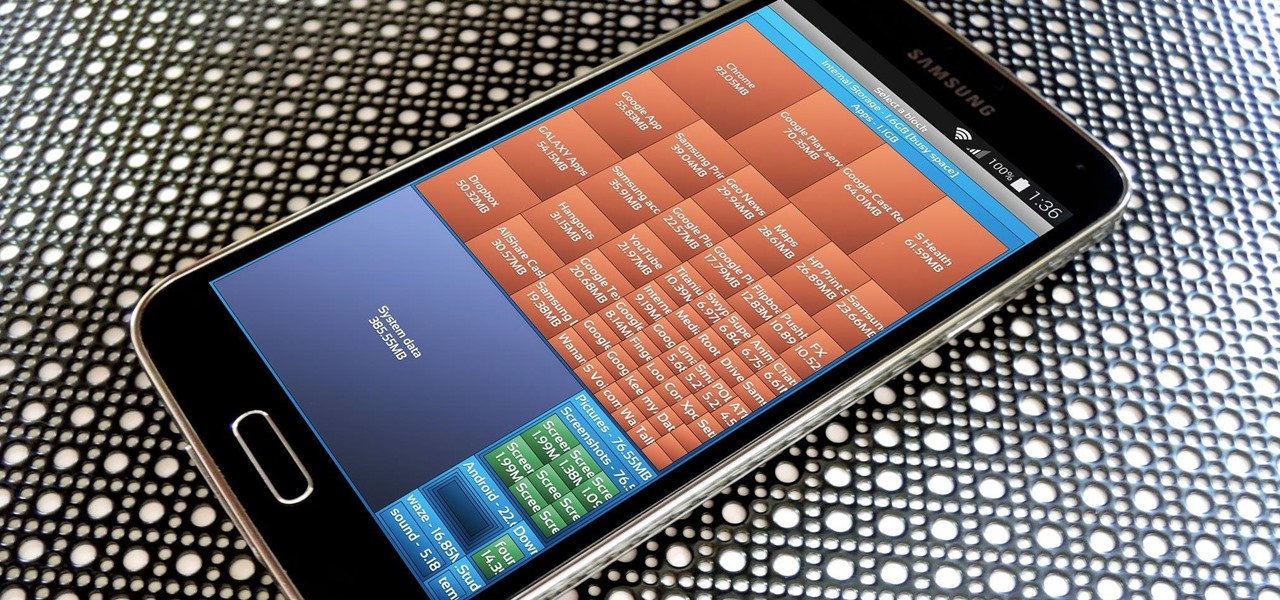
The more we use our smartphones, the more storage space becomes occupied—it's an inescapable fact. But as the data accumulates and chokes off our storage, it can become difficult to identify exactly which files are occupying the most space.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

When my Nexus 5 received the Lollipop update, one of the first things I noticed was how subtle and quiet the new lock and unlock sounds were. Sure, this is a minor quibble, but it's also an easy fix.

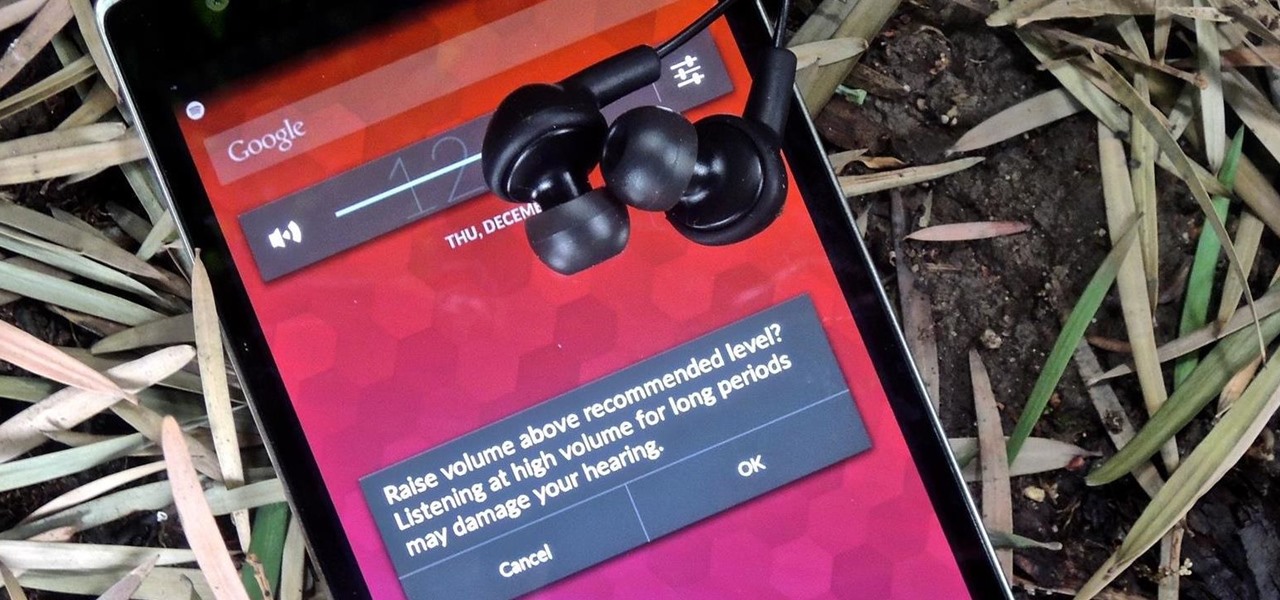
Maybe it was the years of concerts with deafening speakers blasting music into my ears, but I always listen to my tunes as loud as the volume allows me. So, it's pretty annoying when I get a "high volume" warning every time I listen to music on my OnePlus One with my headphones on. We've previously shown you how to remove this same warning by using the NoSafeVolumeWarning, an Xposed module that required root access. Thankfully, the very liberal OnePlus One has a built-in feature that lets you...

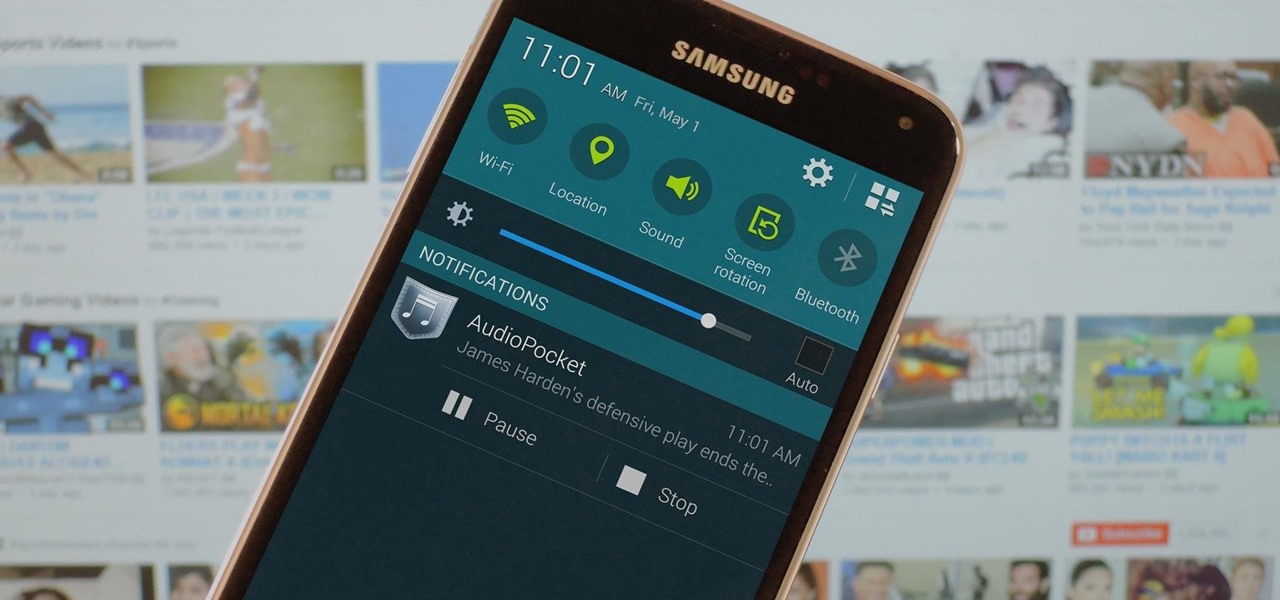
Before you head to class, work, or sleep, you're probably doing the same thing over and over again—toggling off system settings like Wi-Fi, sound, data, or brightness, depending on the circumstances. Schedules and routines can help increase efficiency, so while you abide to a particular schedule, so should your Android.

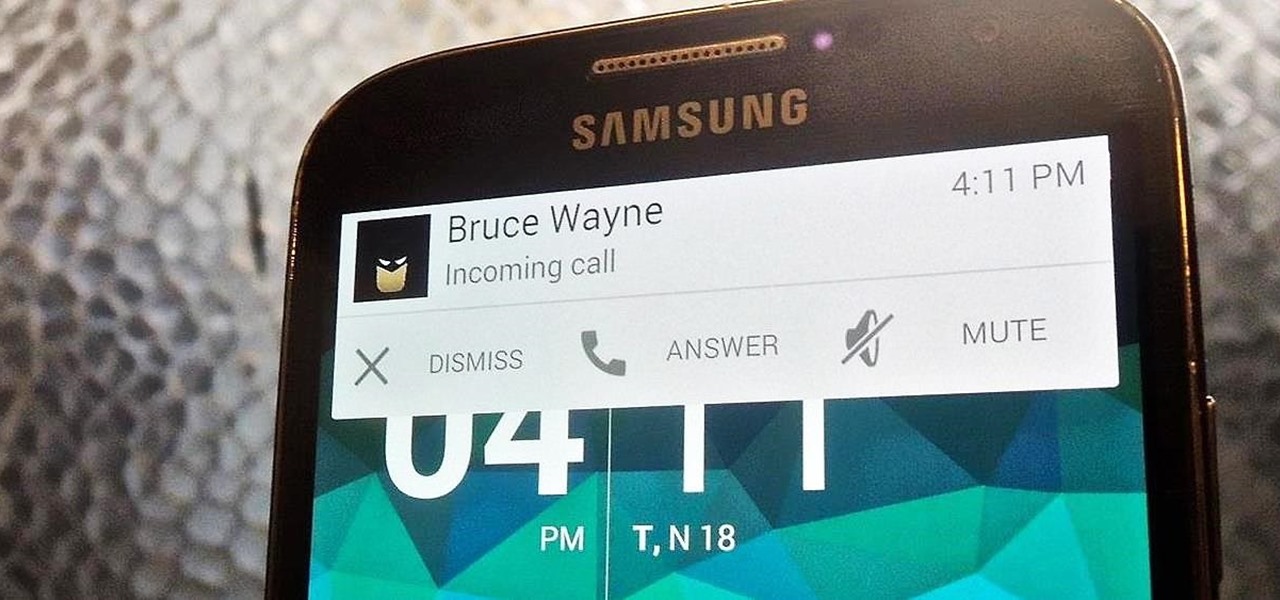
When playing a game or using an app, incoming call alerts can be extremely irritating on my Galaxy S4 because they insist on taking over the entire screen. The alert is a little different on other Android phones, depending on the manufacturer's skin, but all are fairly intrusive in one way or another.

Not every mod you add to your Android will revolutionize the way you use it, but many of them can make things a little more simple and convenient for you on a regular basis, like sliding across the status bar to adjust brightness or swiping the screen to put your display to sleep.