Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

There are two options when it comes to a dent in your car — live with it, cringing each time it enters your view, or get rid of it. While the latter is obviously the best option, most of us will probably just live with dents and dings since spare money is better spent on the actual functionality of the vehicle. However, there is a way to knock out automobile dents yourself with relatively little cash in the bank.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

Tea has been around for thousands of years, and as a result, tons of customs and ceremonies have sprung up around its consumption. Some cultures take their tea plain, while others put things in it. Sometimes there are special tea-holding vessels, other times not. Maybe there will even be special foods meant to be eaten with tea. However, in America, our appreciation of tea has waned. For many, iced tea is their biggest source of tea consumption, and it's imbibed with no ceremony whatsoever in...

If you're too old to trick-or-treat (are you ever really?), throwing a Halloween party is the next best thing. You could always just serve beer and jungle juice like most other people will be doing, which will certainly get the job done, but where's the fun in that? Instead, impress (or gross out) your guests with one of these gruesome drinks.

Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.

There's nothing worse than holding an ice cold brewski on a hot summer day and having no way to open it. If you're a Bud fan, you'll have no problem opening the bottle because most mass-market beers have twist-off caps. But if you have a taste for finer, more expensive brews, you'll more than likely run into the pry-off caps. Pry-offs are used mainly because companies believe it provides a better seal against one of beer's greatest enemies—oxygen. Plus it's a cheaper alternative for craft bre...

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

Not everything that Facebook does is in the best interest of its users. Just look at past examples such as social ads, facial recognition, and instant personalization. Users were perfectly fine without these, and they still are. And now there's another annoying problem that Facebook users have to deal with—the ticker.

If you need to hack an Android device, try a remote administration tool. Known more familiarly as a RAT, there are open-source RATs that are barebones and exorbitantly priced RATs that are more polished. There are also low-cost and polished RATs that aren't intended to be RATs at all, such as Cerberus, an anti-theft solution available right on Google Play.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

It’s easy to gain a little extra weight in college but there are ways to defy this weight gain trend. It won’t work without will power but you can limit your unhealthy food intake and sneak in some unconventional exercise routines.

Ultimately a doctor’s note is the only necessary proof needed to show your boss that you really did go to the doctor’s but if you feel like making an airtight case you can always take a few extra steps to make sure there’s not a shadow of a doubt.

It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

I have always favored a neat and tidy Home Screen on my iPhone, and one of the best ways to achieve that is by removing all the app, folder, and widget names. With a few workarounds, you can do this on iOS 17, but Apple finally just gave us an official feature on iOS 18 to hide app, folder, and widget names on the Home Screen. And it also works for iPad on iPadOS 18.

A new software update for iPhone and iPad fixes a major Apple Books issue that upset users when iOS 16 and iPadOS 16 were first released last September. If you've fled Apple Books because of that blunder, it's safe to return.

If you're a normal, non-corporate video conferencing user, you may not have heard of BlueJeans, but in the corporate world, the software has long been a major staple when it comes to remote meetings.

The progress Tooz has been making in the smartglasses space has been mostly kept under wraps, but the company is slowly giving us a deeper look at what it has in store for smartglasses wearers.

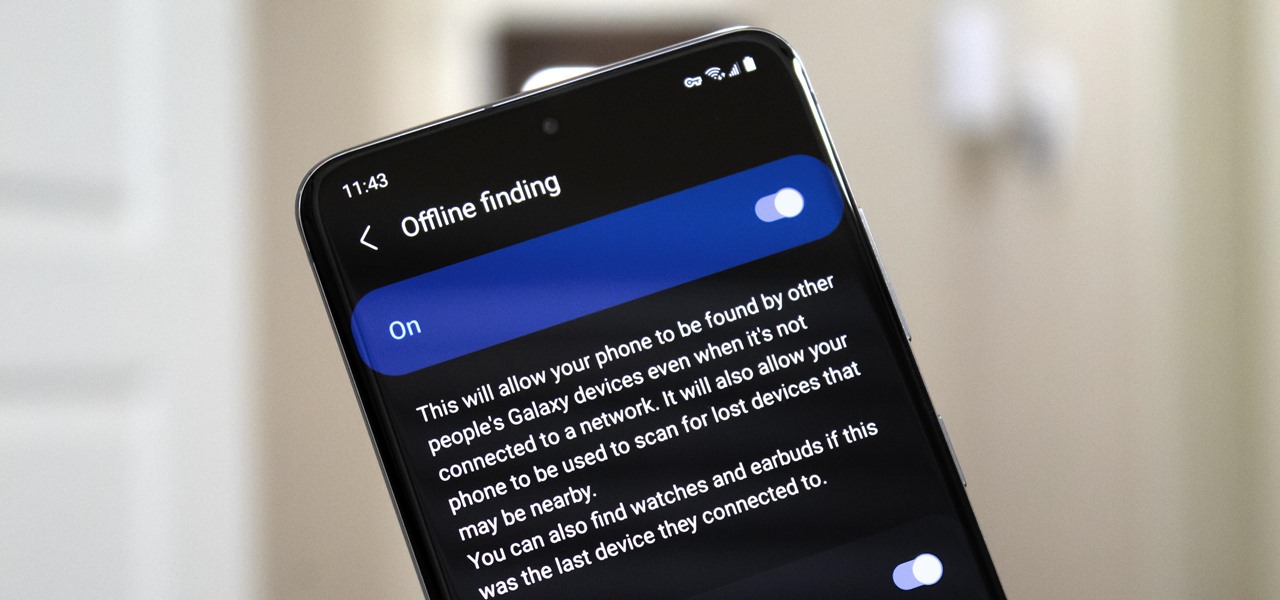
Nowadays, even the dumbest thieves know that the first thing you should do after you steal a phone is turn on airplane mode. Not only does this make it harder for police to track the phone through cell tower triangulation, but it also disables security features the person you stole it from may have implemented — for instance, Samsung's Find My Mobile service.

The true crime genre has long been popular on television and more recently on podcasts with shows like Serial.

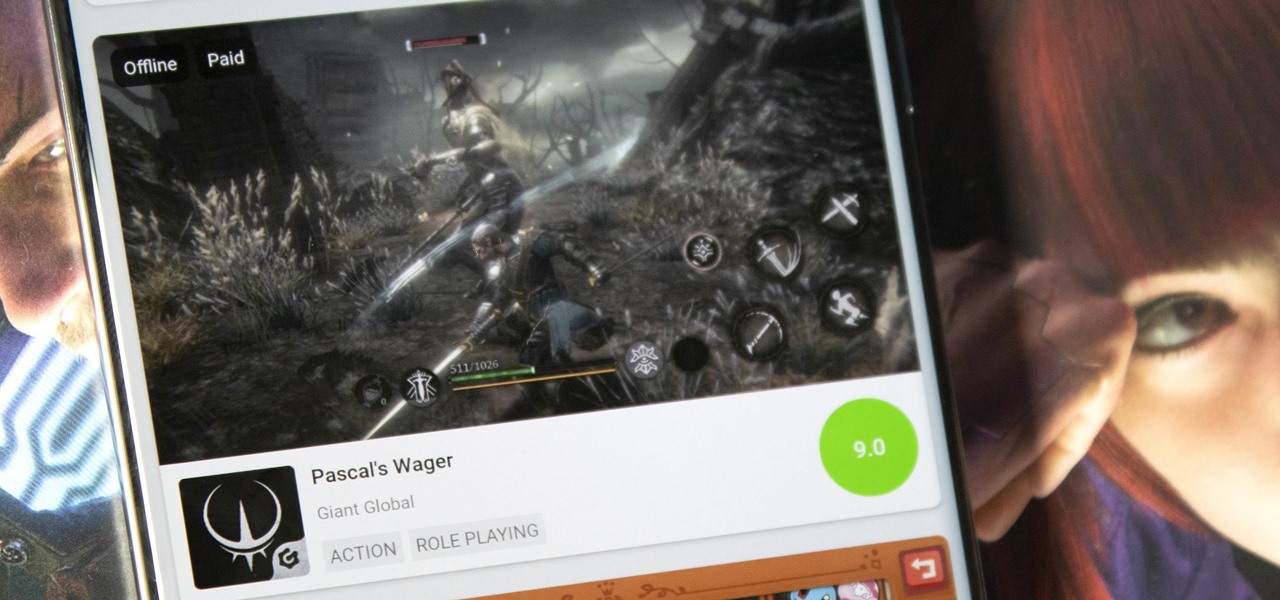
Discovering great mobile games is difficult. With over 300 thousand games on the Play Store — not including the hundreds more available by sideloading — finding the right one to invest your time and money in can be hard. The Play Store's rating system is helpful, but ratings are often skewed by external factors.

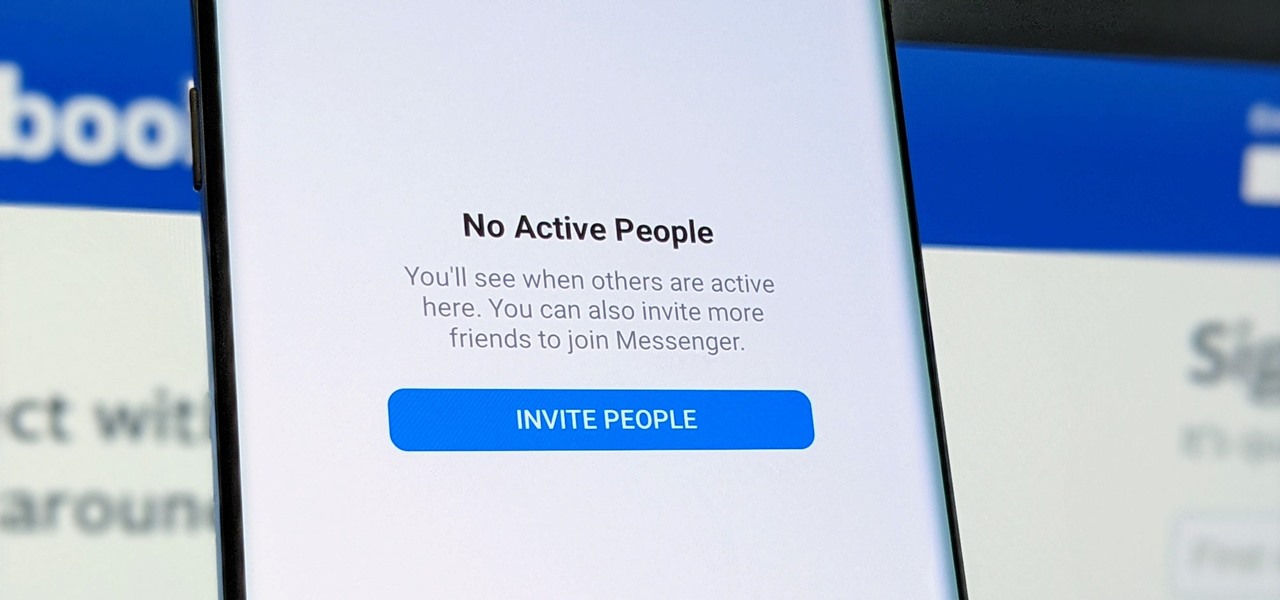
Facebook Messenger's user base has grown so much that it has taken over text messaging as the primary contact method for many people. However, sometimes you might want to hide your online status from specific contacts and appear offline to others. There's a neat little trick you should know that can help you achieve this.

The COVID-19 pandemic has practically shut down all sports except for World Wrestling Entertainment, which has continued staging matches without an audience, leaving us sports fans with nothing much to cheer for. While they can't replace live games, smartphone games provide an alternate reality to live out our competitive entertainment in the absence of the real thing.

Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new "heads up" alerts, but you can still bring them back.

Whether you've made a resolution to try and read more books this year or are just looking to set time aside to listen to an audiobook a little bit each day, building good reading habits can be tough with a busy life. However, with iOS 13, Apple Books includes reading goals, which might give you that little extra bit of encouragement and accountability to help you reach your goals.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

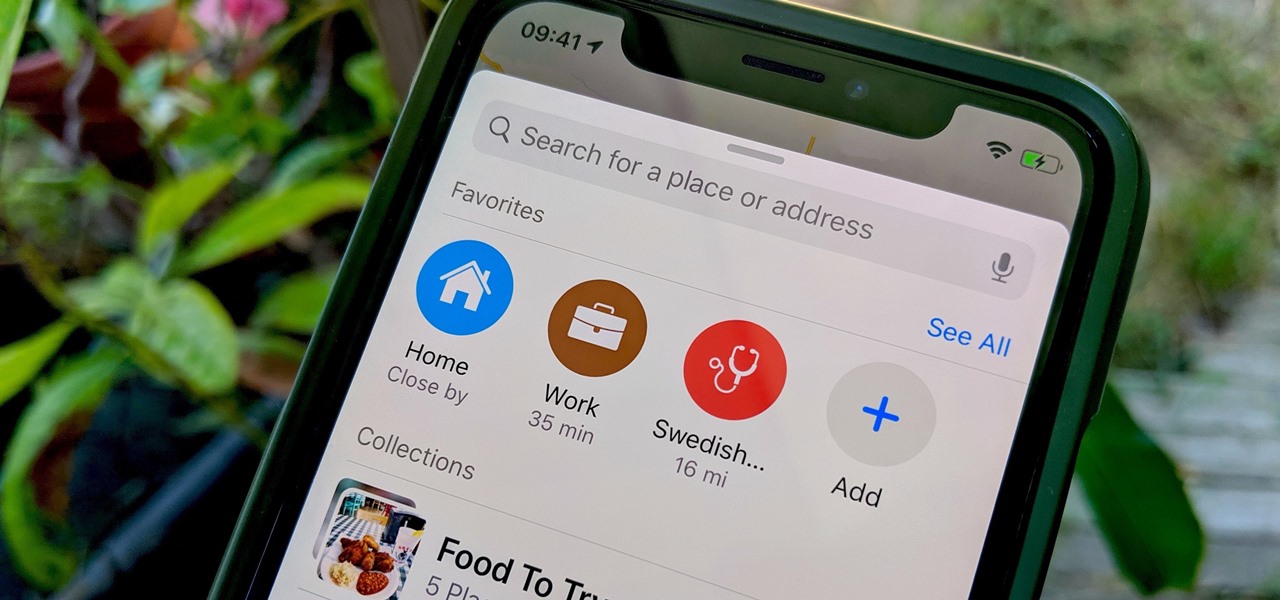
In iOS 13, Apple Maps makes it easier for you to organize essential places on your iPhone, allowing you to save locations as favorites that you can access at a glance.

The long wait is over — the best augmented reality device on the planet is finally available.

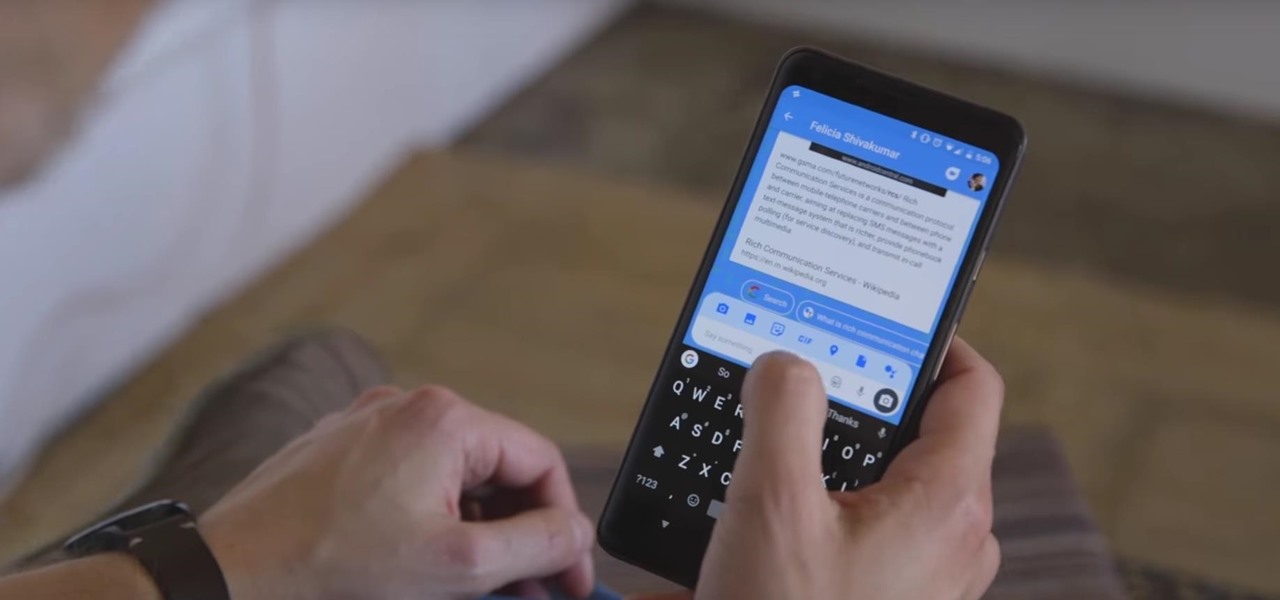
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

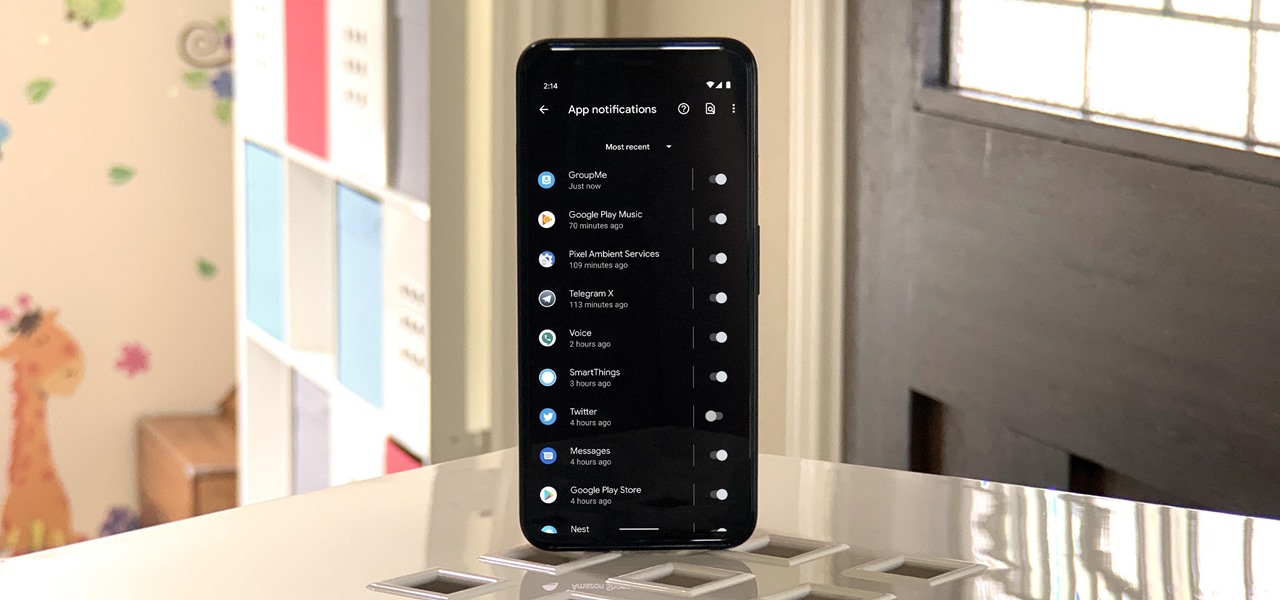
Sometimes you might find that a certain app keeps sending you notifications. What are you to do? There are plenty of useful apps that might send one too many push notifications, but that doesn't mean you should dump them. Luckily, Android gives you complete control over how each installed app handles notifications.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

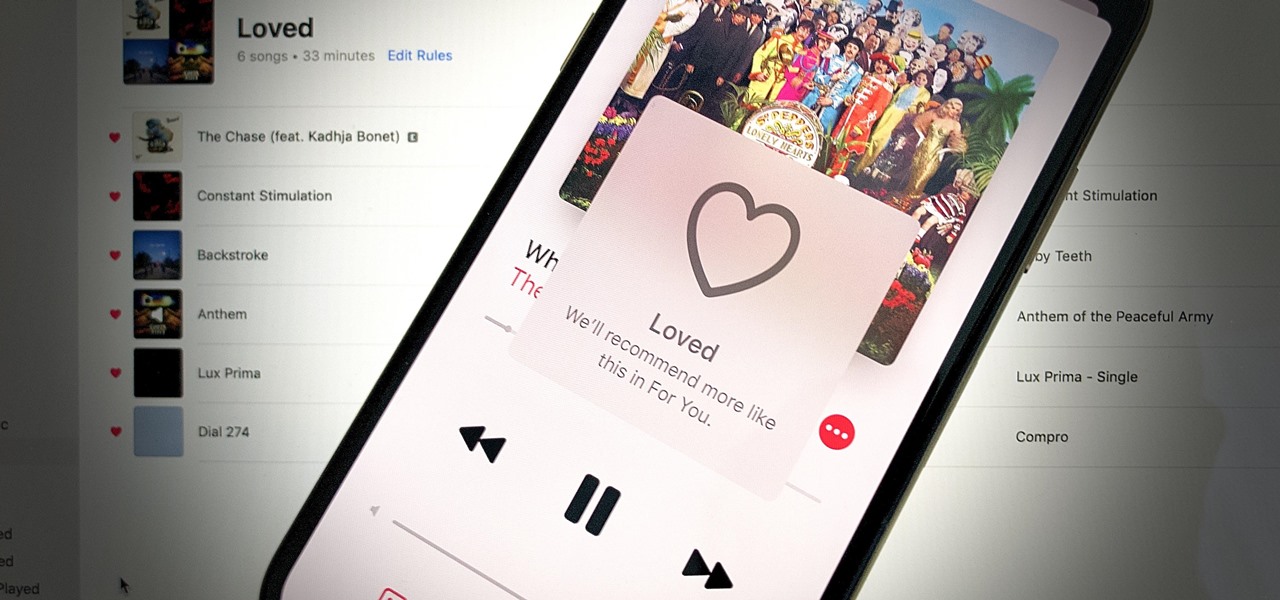
In Apple Music, loving and disliking songs is a great way to teach Apple's subscription service what type of tunes you like and which you don't. While it also seems like it should be an excellent way to keep track of songs you enjoy in the wild, there's no clear way to view all of your loved tracks in one convenient list. There is a way, however, but easy it is not.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

When you can't think of a way to respond in Messenger with words, emojis and stickers will do the trick. Since Facebook is all about the "likes," which use a thumbs-up icon, there's a shortcut to the symbol just to the right of the chat field. It's always there to send a quick like in response to something. But it doesn't have to be the standard Facebook thumbs-up sign — it can be any emoji you want.

Typography is an important aspect of the video editing process. You deal with it when adding captions to news clips, giving on-screen recipes in food videos, creating burned-in subtitles for short films, making no-sound-needed videos for social media, and so much more. Enlight Videoleap for iOS makes this all easy.

Update: The LG G8 ThinQ has been announced. You can read all of the official specs at our full article on the new phone.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.