
How To: Lurk on Instagram Without Getting Caught
It might be difficult to admit, but a lot of us are probably guilty of lurking on Instagram profiles, whether it be an ex you've been keeping tabs on or someone cute you literally just met.


It might be difficult to admit, but a lot of us are probably guilty of lurking on Instagram profiles, whether it be an ex you've been keeping tabs on or someone cute you literally just met.

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

There is much to be learned about Apple Music and the revamped Music application introduced in iOS 8.4. Throwing their hat into an already competitive field with other companies like Spotify, Tidal, or Rdio, this is a bold move on Apple's part. So, before you consider signing up for the new streaming service, let's take you through all the changes and features you should know about before doing so.
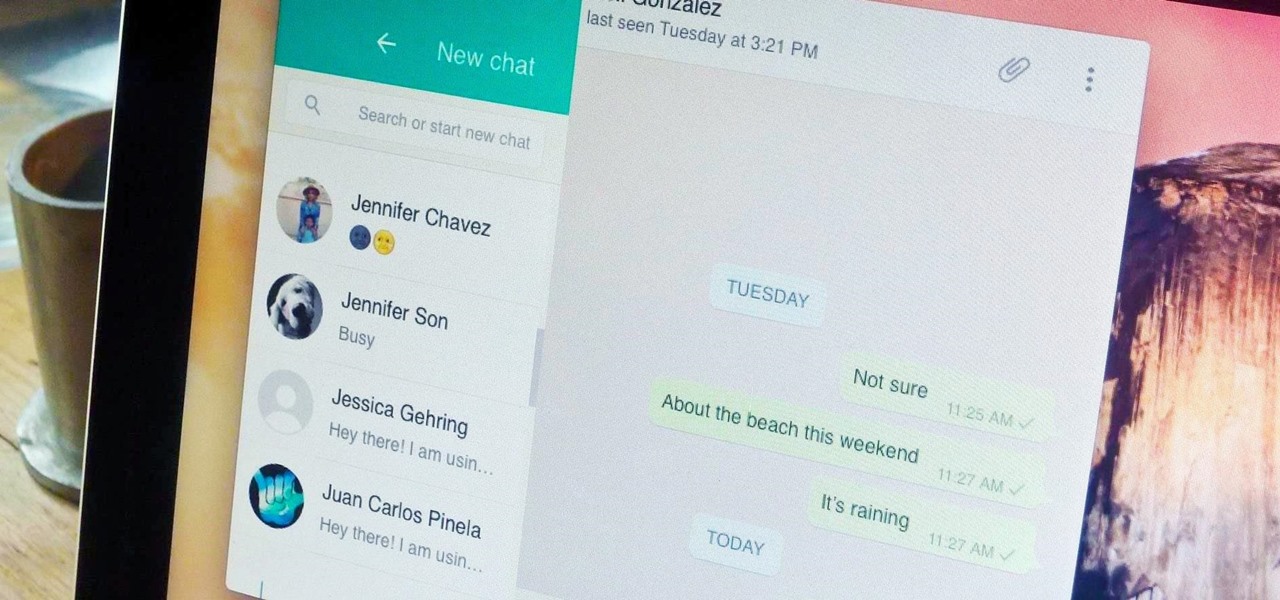
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

Make no bones about it—Google is an advertisement company first and foremost. Nearly everything they do is geared towards targeting the right people with the right ads.

Hi everyone! Last time we finished analyzing the assembly representation of our vulnerable piece of code (have I ever told you it is vulnerable?). This time we are going to introduce some fundaments about exploitation by demonstrating how to crash a program's execution. If that sounds lame, next time we will see how this crash can in fact be useful to control the program's execution, achieving remote code execution!

Hi everyone! After messing around a little bit with IDA and Hopper disassemblers and briefly introducing you to memory, registers and Assembly, we are going to understand what happens when a process is running, which variables join the play and especially what happens when a function is called and why is this procedure-logic so interesting and useful along with the concept of stack.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have already been ported over, but any type of lock screen customization has been noticeably absent.

AllCast, from renowned developer Koushik Dutta (better known as Koush), allows users to stream personal media, such as movies, photos, and music from mobile devices to Chromecast and other streaming devices.
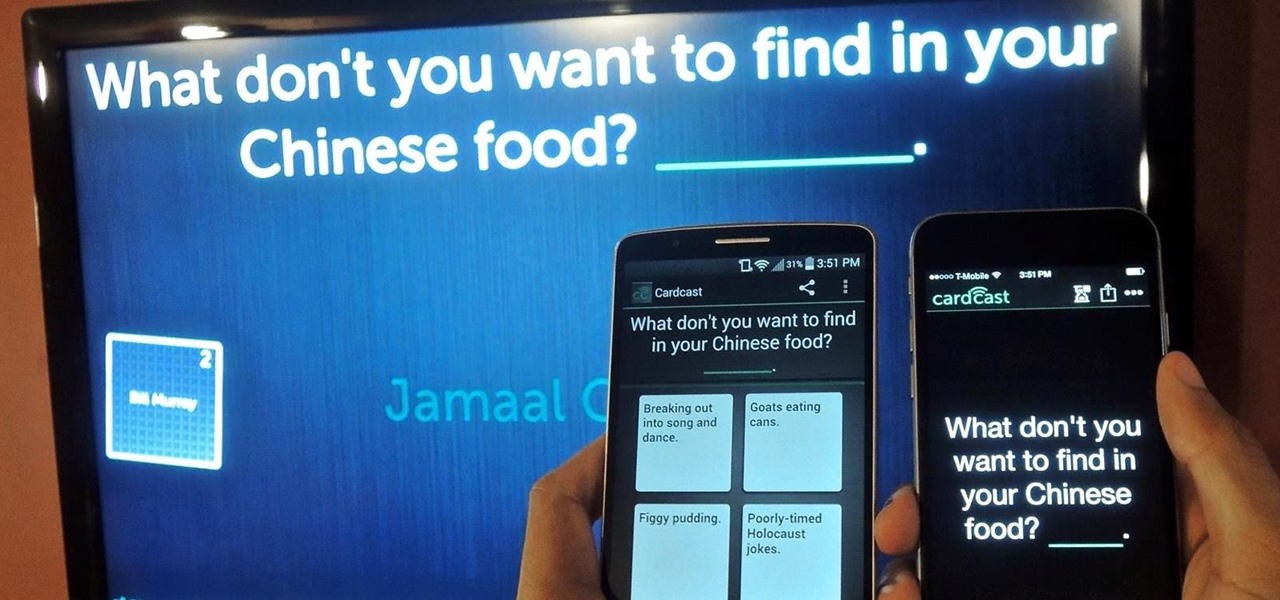
The future of game night is digital. Your Chromecast is great for watching Netflix or YouTube, but get more use out of it by making it the centerpiece for your next fun get-together.

Linux may not be the most popular consumer operating system out there, but what it lacks in consumer app variety, it definitely makes up for in flexibility and security. And if you've ever tinkered with a Linux distro, you know how easy they are to install—most of the time, I skip standard installation and boot directly from a CD.

How many times do you misplace your phone? Once a day? Twice? As much as you may hate losing your phone, it always seems to happen, and finding it isn't very easy if you left it on silent mode.

Of the sixty or so "must-have" apps that are installed on my Samsung Galaxy Note 3, there's only one that I need to use and hate with a passion. Skype. Whenever using it, I'm consumed by dropped calls, mic issues, poor quality, and random crashes, among other things—and I'm not the only one.

While FIFA may be one of the most corrupt organizations in the world (depending on who you talk to), that won't stop millions of us from tuning in this Thursday, June 12th, to watch the first game of what's going to be a month-long World Cup affair.

I'll freely admit that I'm a SwiftKey diehard. I've used the keyboard since its inception in 2010, and it was one of the first apps I ever paid for back in the days of my beloved Sprint Evo 4G. Since then, I've kept up with all its beta iterations, and have unabashedly installed it on various friend's devices.
Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.

Facebook is a black hole. The constant stream of baby photos, #hashtags, BuzzFeed quiz results, and unintelligible status updates is mind-numbing. I know too much about too many people I hardly know.

Silence can therapeutic at times, but unsettling at others. When I'm in bed at night, I need some sort of background or white noise to help me fall asleep. Pure silence just does not do it for me. Whether it's a fan oscillating left to right, or the TV playing, I need background noise to soothe me to sleep.

Online gaming is nothing new, and with live YouTube streams becoming ever more popular, there always seems to be a way to watch people play video games. Twitch TV offers the same spectator experience you've come to know and love, but the people over at TwitchPlaysPokémon have gone a step further and made it so that the spectators are the ones playing the game.

Samsung's exclusive music streaming service, Milk Music, has been making waves across the web thanks to its peculiar name and ad-free stations.
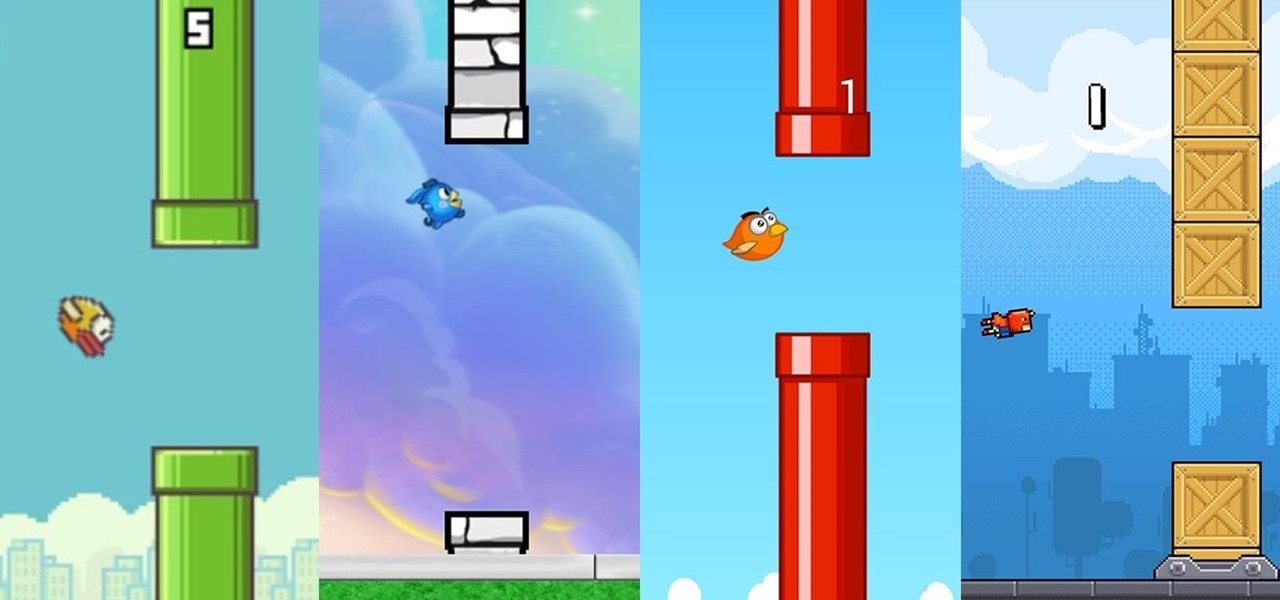
In a much-hated move, Flappy Bird developer Dong Nguyen removed his incredibly popular, yet extremely frustrating app from both Google Play and the iOS App Store. The jury is still out on the exact reason behind the move, though we can rule out pressure from Nintendo, but one thing is for sure—Flappy Bird has fallen for good.

With a 5-inch screen, it's possible that the Samsung Galaxy S4 can be a bit large for our hands. While my grubby hands let me navigate the phone pretty easily, the same can't be said for everyone. A lot of us use two hands to type on the phone, play games, and perform tap or swipe gestures.
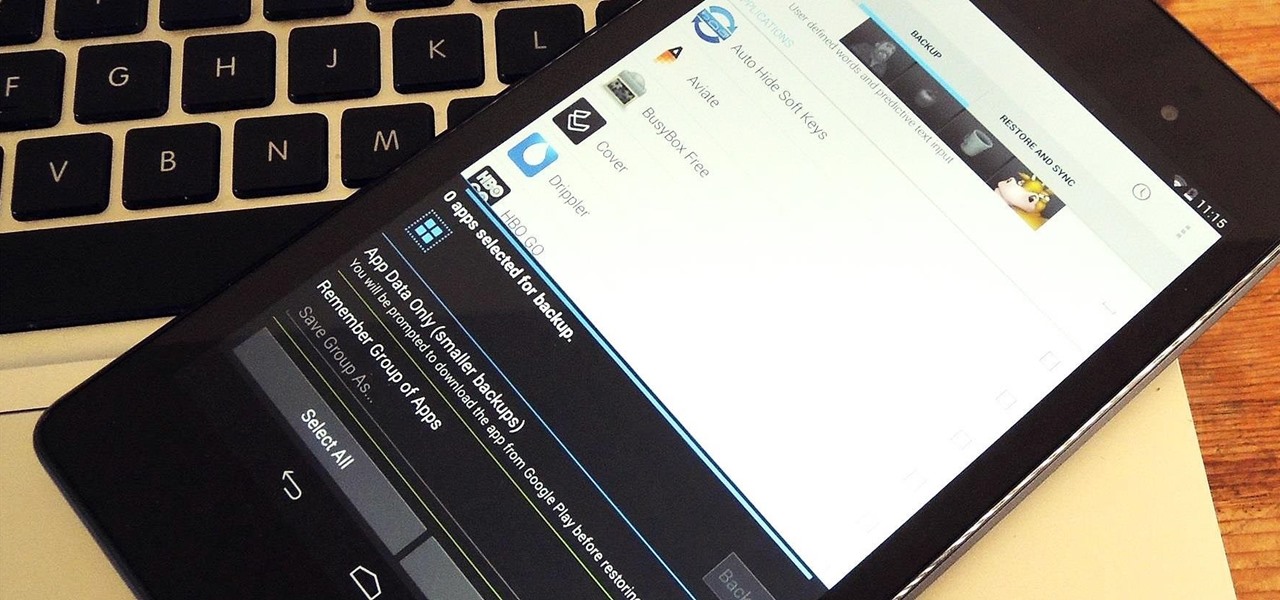
At some point, we all need to back up our device. Maybe it's time to take it in for repairs or maybe you're just cautious and paranoid. Maybe you're trying out a new ROM on your Nexus 7—then you definitely need to back up. The most secure way would be to use a custom recovery like ClockworkMod or TWRP, but if you're not rooted or planning to root, then you'll need an easy alternative.

When choosing a phone or tablet, I always take in to consideration what my music experience will be. Unfortunately, the Nexus 7 doesn't have Beats by Dre technology, which some may view as overrated, though it's definitely one of the better ways to get perfect-sounding tunes with headphones. But it's not all about the Beats. There are many other ways to make listening to music on your Nexus 7 tablet a better experience, and we'll highlight some of the options and add-ons that you can try out.

My favorite type of video game is first-person shooters, and the one that started it all for me was GoldenEye 007. There was just something about the controls, fast-paced action, and free-roaming environment that got me hooked.

The 8-bit NES may have ruled the late-eighties, but the SNES took over the early-nineties with its 16-bit graphics and 3D-like gameplay on titles like Star Fox and Dirt Racer. When 32- and 64-bit consoles came out in the mid-nineties, the Super Nintendo took a hit, but with the rise of the Internet, created a huge emulation community in the aftermath.

Starting on Android 4.2, a new feature called Quick Settings was integrated into the Notification tray, which allows you to quickly turn on and off certain device features such as Wi-Fi, Bluetooth, GPS, etc. These toggles also provides a shortcut to the feature's more advanced settings by long-pressing on the icon.
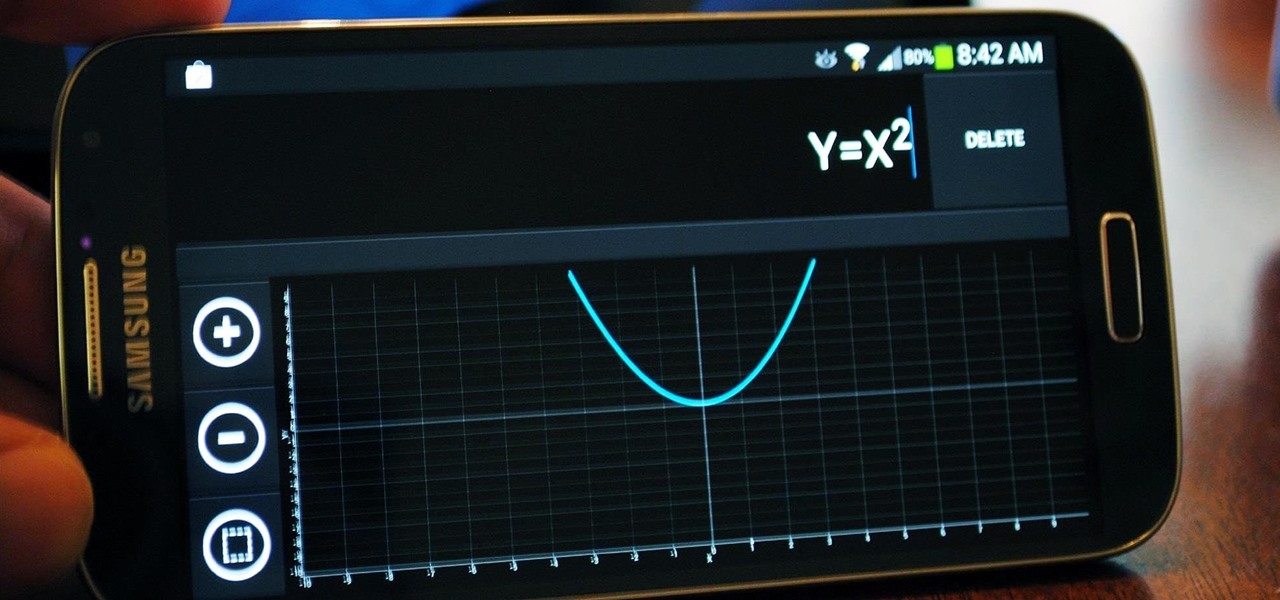
It's that time of the year again when scores of students are flocking to stores for school supplies. Pens, pencils, books, and for math students, calculators.

The sound I get when receiving a new text message is the camel from that Geico commercial yelling "Hump Day!" Sure, I could find a less obnoxious notification sound, but it makes me laugh every time, and that's important.
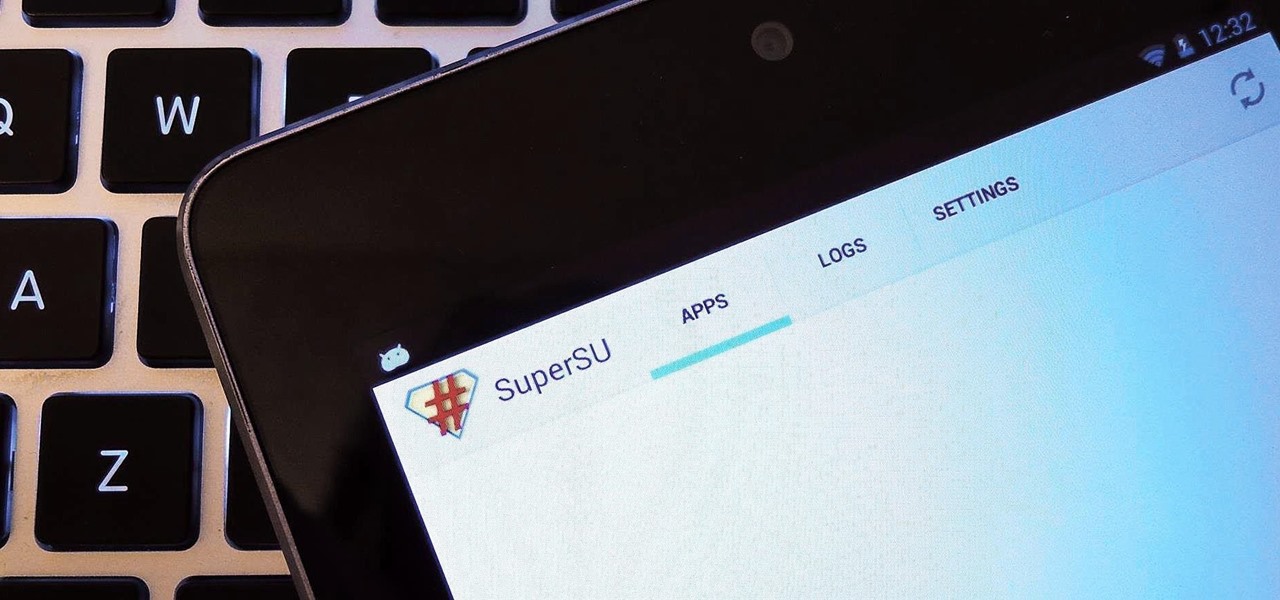
The new Jelly Bean is out in the wild, but if you've installed Android 4.3 from stock, you'll notice rooting is now not possible. If you miss the ad-blocking capabilities of AdBlock Plus, how Seeder made apps snappier, or the convenience of backing up with Titanium Backup, you'll need to get rooted.
I remember how fast my Nexus 7 was the first time I turned it on. Boy, do I miss it. Now my tablet is pretty buggy and crashes happen frequently, and I'm sure that goes for many of your Nexus 7s as well. Even if you upgrade to the new Nexus 7 next week, it will eventually develop similar issues.
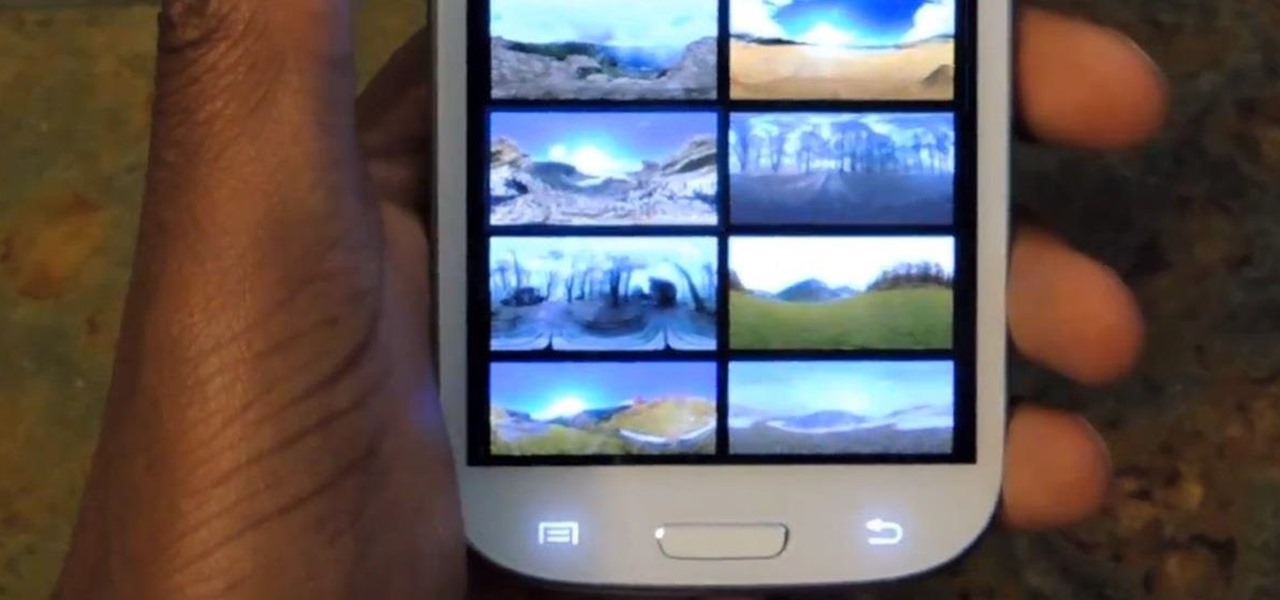
For the first time ever, iPhones will be getting live panoramic wallpapers in iOS 7, but it's something Android devices have always embraced.

Let me start out by saying that Steampunk isn't about being historically accurate, and that everything I'm about to tell you is entirely optional. That said, let's take a look at the history of screws! What many people don't realize is that before we had metal screws, wooden screws were in wide use for things like wine and oil presses. Generally, the invention of the screw is attributed to Archimedes in the 3rd century BC. That was a long, long time ago. Metal screws and even screwdrivers hav...

Megaupload was one of the very first file-sharing sites I ever used. But since 2005, the beloved (and pretty gangster) Kim Dotcom, has been in a legal battle with the U.S. Justice Department over copyright infringement.

Time-lapse videos are a recent phenomenon to the mainstream audience—in movies, on television shows, and even in commercial ads. These sped-up and blurred images are a microcosm of many of our lives in which we're constantly in a hurry to get somewhere. We like everything fast: our work, our coffee, and our news.

In this project, you'll learn step by step how to modify a microwave oven transformer into a high-current device that can pump out 800 amps of electrical current, which is enough amperage to melt metal. If you liked the Metal Melter you saw in my previous project, here's how you can make your own!

A man once told me to never complain about gas prices. With the average price of regular unleaded gas at $3.34 a gallon, it's hard not to, even if it is the holiday season. Since my car averages about 22 mpg, the man offered me this proposition: "If I offered you $3.34, would you walk 22 miles?"

Believe it or not, the 2012 Presidential Election is (finally) almost over. While most of us are breathing a collective sigh of relief (no more political ads!), it still seems like it hasn't been that long since the last election results were announced. This time, though, one of the biggest differences is how people will watch. Since traditional cable is on its way out, and mobile devices are getting more popular every day, a lot of people will be watching this year's election results online ...

RFID chips are everywhere. They're in passports, credit cards, and tons of items you've bought in the last 5 years or so. Big retailers like Walmart started using tracking products with RFID as early as 2004, and today, they're used in everything from mobile payments to hospital record systems. Chances are, unless you're a hermit (in which case you wouldn't be reading this anyway), there's an RFID tag within a few feet of you. Photo by sridgway