There are plenty of reasons to upgrade to the iPhone 12 mini. Maybe you want to take advantage of the improved camera system, or you're intrigued by the return to a smaller form factor. But one of its coolest features might be MagSafe, a completely different way to charge and accessorize your iPhone.

The new iPhone 12 Pro Max is equipped with MagSafe, the iPhone 12 lineup's most talked-about feature. While Apple previously used MagSafe for its magnetic charging connectors on older MacBook models, it's given new life to it on the iPhone, and in a much better way. But can it do for you exactly?

If you're getting or already have a new iPhone 12 or 12 Pro, its big-ticket feature is MagSafe, something you'll definitely want to explore. While the technology is new to iPhone, Apple used the MagSafe name for its magnetic charging connectors on older MacBook models until USB-C replaced it. Apple's reenvisioning of MagSafe for iPhone is completely different and much more useful.
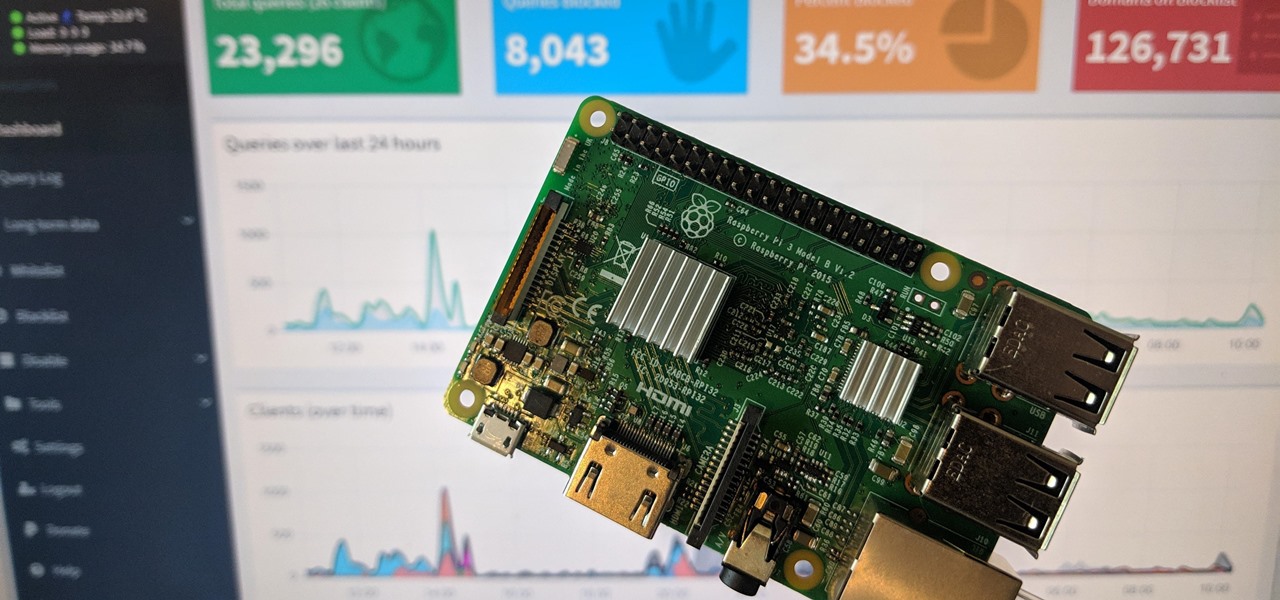
The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

After learning that you'll need to spend at least $74 on a special charger and a USB Type-C Lightning cable to enable fast charging on the new iPhone X and iPhone 8 models, you may be wondering why you can't just use the standard Lightning cable. While we can't answer why Apple didn't include the USB-C cable in the box with their new phones, we can explain why you need USB-C to enable fast charging.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Hi there again, aspiring hackers (and veterans as well)! I'm going to explain how to perform a dictionary attack on a WPA/WPA2 protected network with Wifite. Please note that this doesn't work with WPA Enterprise For that end, you'd have to use an Evil Twin to get the "Enterprise" auth attempt, and then crack it.

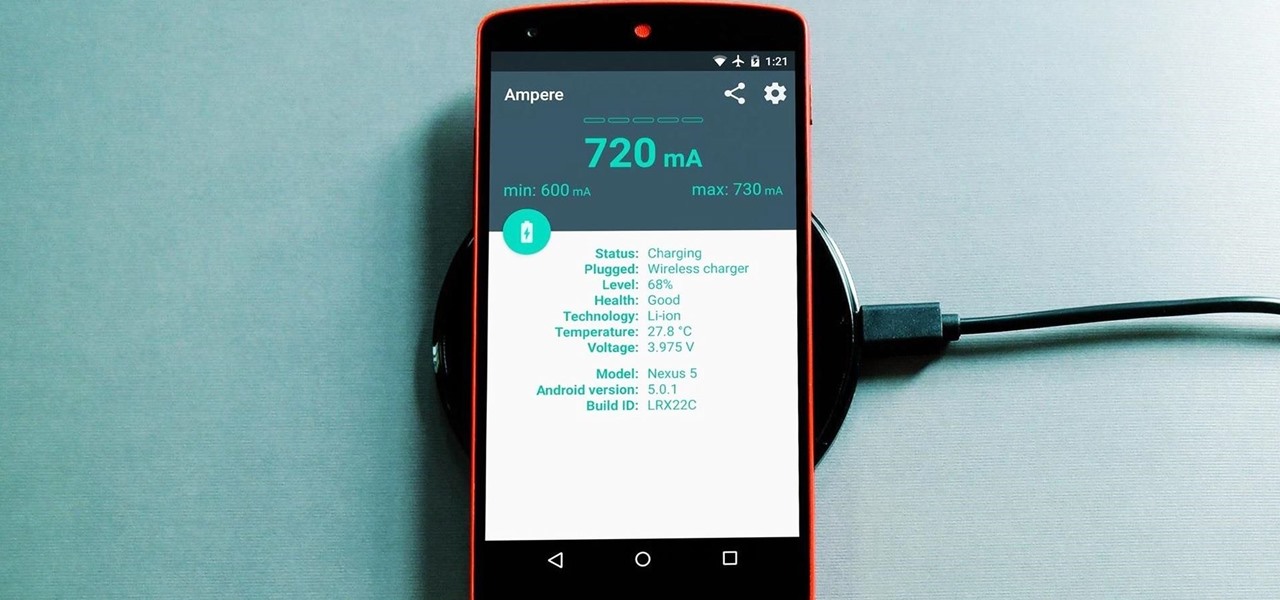
Not all smartphone chargers put out the same amount of current. The adapter in your car probably charges your phone a lot slower than the one plugged in at your bedside, and if you use wireless charging, it may be a bit slower still.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

The fact that this guide even exists is a downright shame, but that's neither here nor there. The truth of the matter is the iPhone 7 and 7 Plus don't have 3.5 mm headphone jacks, and since they use the Lightning connector to output audio, it's hard to charge your phone while your headphones are plugged in.

On May 17, Apple announced that Lossless Audio playback for Apple Music was finally coming to subscribers in June. The long-awaited option will let users stream songs at a much higher quality than ever before. Still, in the fine print, Apple noted that you wouldn't be able to listen to the best sound quality — Hi-Resolution Lossless — on your iPhone without a DAC.

So, someone on your shopping list has an iPhone. Lucky for you, Apple's line of smartphones are practically made for accessories. From AirPods to adapters, there's something for every iPhone user in your life. Are you feeling overwhelmed by the options? You've come to the right place.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Summer is here, and with the season comes more freedom and searing heat. It's the ultimate between-a-rock-and-a-hard-place situation. You want to be outside and enjoy the sun, but you don't want to be over-powered by it. Thankfully, you can create makeshift misters on the cheap to enjoy the summer heat right on your deck.

Headphone cords are one of those things we all deal with because it beats the alternative (no music). But they can be so obnoxious—they're always getting caught on things, and they seem to be perpetually tangled. If you have ear buds, you can make a simple a cord container to keep them organized, but over-ear headphones are a little more tricky.

Whether you're in high school or college, you no doubt will have your iPhone in your pocket all day long. To make your iPhone last the whole time and even help you out with your studies, these are the accessories you'll want to get your hands on.

Starting February 21, you can preorder your Galaxy S20, S20+, or S20 Ultra. Samsung includes everything you need to get started in the box, but probably not everything you'll want. Let's go ahead and bridge that gap.

Connecting your devices with a cable is the fastest and most reliable way to transfer files between them. Now that most Android devices have either USB Type-C or a Micro-USB port that supports USB OTG, phones are capable of importing media files directly from a camera using a simple (and cheap) adapter.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

With MP3 players all but dead, phones are now the dominant portable music devices. While smartphones have gotten better at this task over the years, they do have some glaring limitations when it comes to music. On the bright side, we can use these limitations to help find the perfect gifts for the audiophiles in our lives.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

If you want to follow Null Byte tutorials and try out Kali Linux, the Raspberry Pi is a perfect way to start. In 2018, the Raspberry Pi 3 Model B+ was released featuring a better CPU, Wi-Fi, Bluetooth, and Ethernet built in. Our recommended Kali Pi kit for beginners learning ethical hacking on a budget runs the "Re4son" Kali kernel and includes a compatible wireless network adapter and a USB Rubber Ducky.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

The headphone jack is becoming outdated technology in smartphones — that's what many manufacturers would have you believe. For the convenience of the audiophiles out there, we recently published our list of all phones that have removed the 3.5 mm jack. But what did each company gain inside their flagship phones by removing this supposedly antiquated port?

Your iPad has a superpower that iPhone models don't and probably never will have (even though they could) — one that will make you want to take your iPad with you everywhere you go from now on.

There is a whole world of smartphone accessories out there, some of which are more quirky than others and don't get the recognition they deserve. But these sometimes strange, sometimes embarrassing products can really make life easier on your iPhone or Android phone.

There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?

Compared to Apple's products like the iPhone and iPad, Android phones and tablets are very flexible devices. For instance, you can set a new home screen, replace the lock screen, or even beam files using NFC — but that's just the software side of things, and the flexibility goes well beyond that.

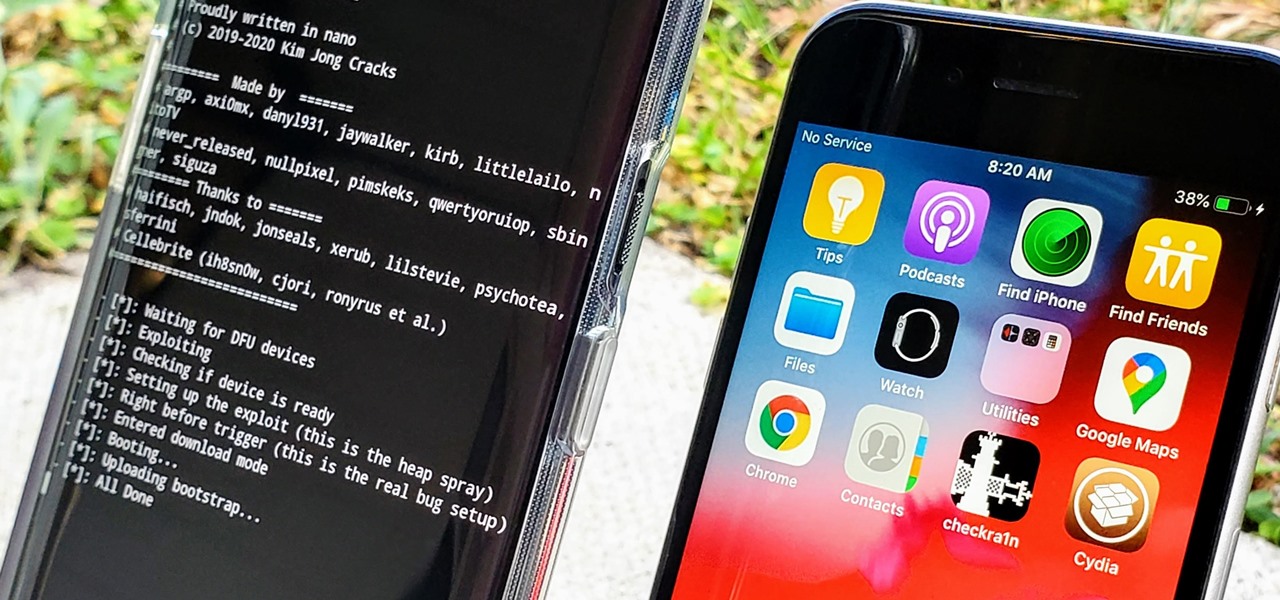
In the iPhone modding scene, the Checkm8 bootrom exploit, by developer axi0mX, led to a powerful jailbreaking tool known as Checkra1n. With it, you can jailbreak a variety of iPhone models without worrying about it getting patched later on. But in the past, it required you to have a macOS computer — but not anymore.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

The iPhone XR has touched down alongside the XS and XS Max, and it utilizes tried and tested materials found on the iPhone 8, while being molded in the same vein as the iPhone X. The budget-friendlier flagship comes with its own set of design elements to set it apart from its more expensive brethren, but is powered by the same SoC, making it is a solid choice if you're thinking of upgrading.

The hatred is almost universal—by now, even late night TV hosts are bashing Apple's move to ditch the headphone jack in the iPhone 7. It's not like the disdain is baseless, either, because there are plenty of problems that come along with removing the iPhone's only analog sound output.