Many tutorials show you how to use Cheat Engine to execute one function of one particular game - but not this one! This tutorial gives you a good understanding of what Cheat Engine can do, and how you can use it to hack nearly any game!

In this video we are given a brief history followed by an extremely detailed procedure on the art of tie dying. We are shown each step, everything from drawing your own designs to applying small amounts of alcohol to your artwork. After everything has been soaked in water a final tie shirt has been created. A project perfect for the kids considering it has a safe and easy to understand procedure that would finish with a beautiful piece of art in merely minutes.

Learn how to make cross friendship bracelets with this wonderful and informative video. The color of the threads is chosen to understand what is going on there. The watcher gets the basic knowledge of making thread bands or thread bracelets. The Cross Friendship Bracelets looks so colorful and makes great fashion accessories for anyone. The helical structure of the bracelets mentions the crossing of two friends.
In this tutorial, learn about the nuances and abilities of the HP10BII Financial Calculator and how to get it running properly and indefinitely.

This Photoshop software tutorial shows you how to create a shirt mockup so convincing, you'll have people emailing you asking where you got it printed! Take a look inside Go Media's Apparel Template pack in this video that shows how the layers are set up and demonstrates how to paste your artwork onto a tee shirt, mask it out, and change the color of the shirt all within Photoshop CS3. The tutorial has no verbal instruction but is clear enough to watch and understand.

Dom Famularo's infectious smile and drumming talents make him one of the most sought-after drummers and clincians in the world. In this installment from his video series dedicated to a wide variety of topics–from drum strokes to styles–, Dom discusses the finger-heavy French matched grip position.

Dom Famularo's infectious smile and drumming talents make him one of the most sought-after drummers and clincians in the world. In this installment from his video series dedicated to a wide variety of topics–from drum strokes to styles–, Dom explains the American matched grip, which, technically, resides somewhere between the French and German grips. Take a look!

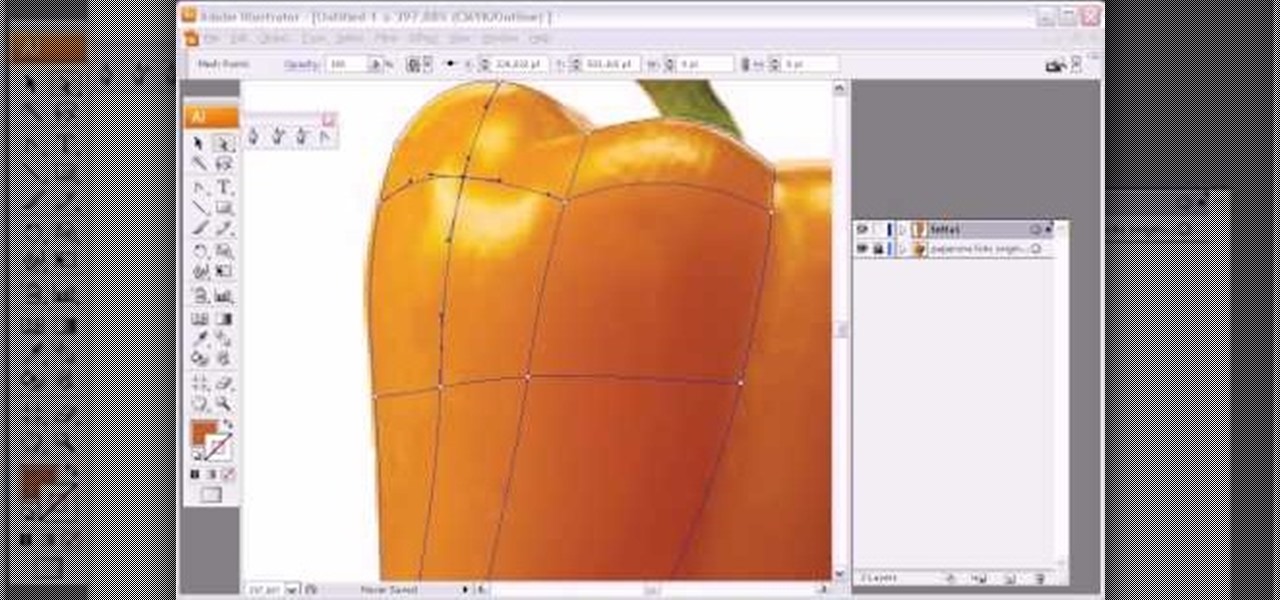
This software tutorial shows you how to create a photorealistic mesh shape in Illustrator. You should have a good understanding of Adobe Illustrator since the tutorial is visual only with no text or verbal instruction. If you want to use the mesh shape tool in Illustrator to give your objects realism, this tutorial will help.

A lot of the English you hear in the real world isn't taught in the classroom. This ESL tutorial gives examples of how people use "messed up", "screwed up" and "f*d up". This is real life and you need to know how to respond if someone says these things to you. Watch this how to video and you will be speaking and understanding English in no time.

Watch this how to video guide for understanding the basic archetypes presented in the major arcana for tarot cards.

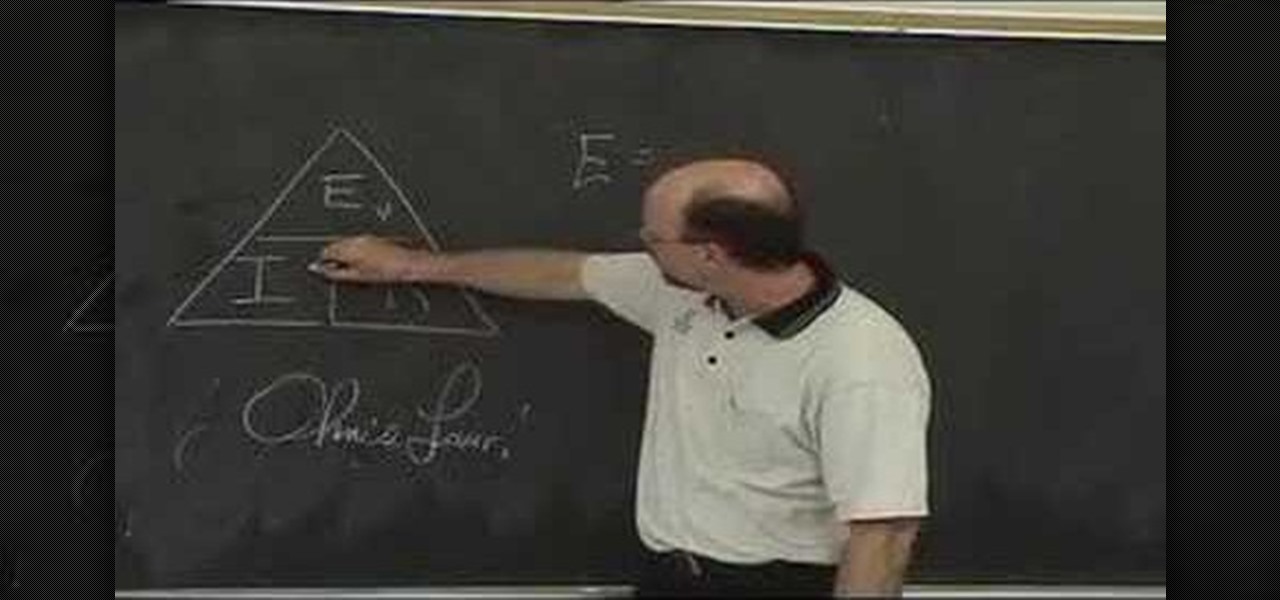
Watch this educational how to video to review Ohm's Law. This math and physics concept is derived from electric motive forces, intensity of current flow and resistance values of conductor. Watch and learn more about Ohm's Law.

Ever had a picture cube that you just couldn't fix the middles for? If you already understand the Rubik's Cube, then watch these two videos, if not, then watch something else, or read the "7 Step Solution Guide."

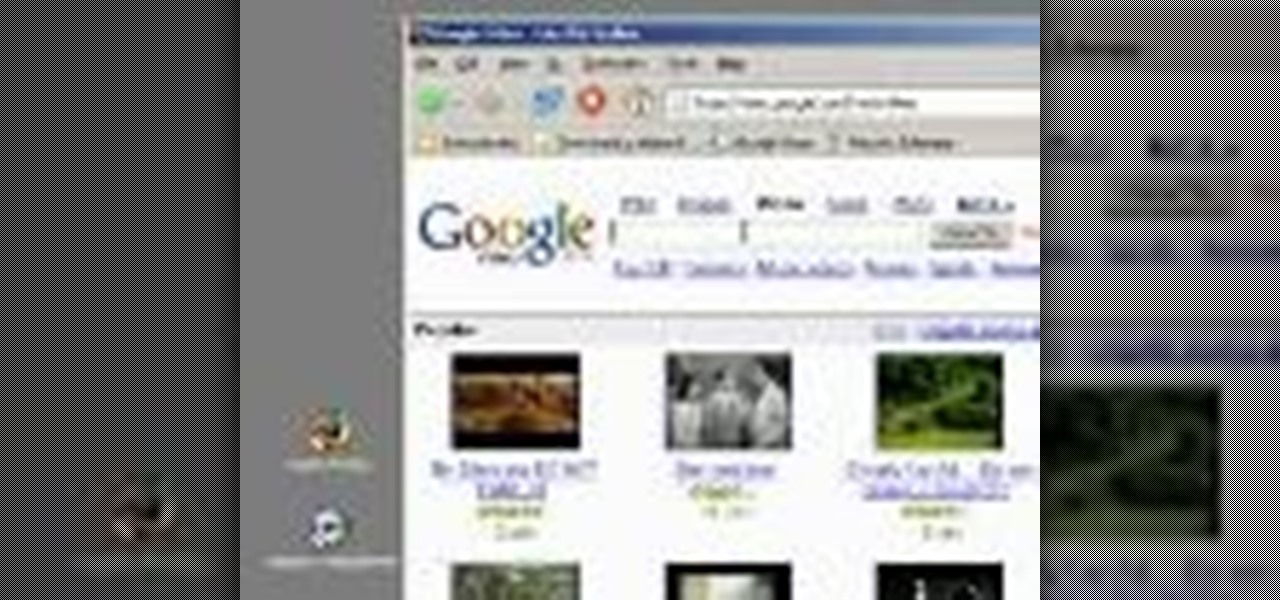
This video demonstrates how to download Google Video movies onto your computer and play them using Windows Media Player. The video walks you through downloading the right software, downloading the video you want, modifying the movie, and playing in Media Player. This video is silent and goes fast, so you will have to watch a few times to understand what is happening.

The amount of information we see on a daily basis is overwhelming. Then there's all the data we never even see. If your career depends on making sense of all of this information, you need to understand the programs that do the heavy lifting.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

When you have an infection, a doctor prescribes antibiotics to make the bacteria that causes it disappear. Sounds like a good idea, but the disappearance of microorganisms that have inhabited humans for millennia could be driving rising numbers of serious illness and debilitating conditions.

That soil under your feet is not just dirt. It is teeming with life that may not change as fast as we would like when challenged by global warming.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

MacBooks are built for creation and creativity. They're built to withstand our careers, our hobbies, and our everyday use. I use mine every day, and there's nothing I'd recommend more for computing needs.

Many people drink green tea for health reasons, and it's no wonder. This beverage is a superstar when it comes to antioxidant levels, and is being studied for its potentially curative properties on multiple health concerns, whether it's staving off the aging process or fighting cancer.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

James Williamson for Lynda demonstrates designing for multiple browsers. The most frustrating aspects of web design is constantly dealing with the settle and some times not so settle differences in browser rendering. While they moved to a standard spaced, CSS control presentations has made life infinitely easier for web designs. Dealing with bad browser behavior is one of most unfortunate side effects. All browsers render our pages same because each browser reads and renders the HTML and CSS ...

Step 1. Understand that opening a coconut requires a considerable use of precise force. Because you are using a knife or cleaver, it is very important that you keep your fingers and other body parts away from the blade. Step 2. Clear off a stable cutting surface. Step 3. Begin scraping off the white, sinewy upper layer around the pointed top of the coconut, using your knife. Scrape off the top layer until a brown ridge is revealed around the base of the pointed top. Right where this brown lay...

Expand on your knowledge! Trivial Pursuit is a great family game that can also teach you a lot in the process! If you want to learn how to play, check out this video.

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

Bridge is one of the most popular games in the world. The rules may seem overwhelming, but all you need are a few easy steps to learn the basics.