
Addict Understands Search Results


How to Train Your Python: Part 1, Introduction
Recently I've been looking around our wonderful community and I've seen some absolutely hands-down fantastic python scripting articles. But, in the end, these series weren't very extensive. I've been wanting to do a series on teaching python for a while now, and I don't mean just the basics, I mean to make an extensive series that takes it all the way from "Hello, World!" to popular third party modules, and everything in between!

News: The Cruel Crypto Game; How to Beat CryptoLocker Ransomware
It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

How To: Build a Stealth Port Scanner with Scapy and Python
As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

How To: Hack Metasploitable 2 Part 2
In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

News: How to Write Better Code
Programming is an essential thing in hacking/pentesting, and at times, I do not feel that it is being addressed enough here, at Null-byte. I understand that this is a forum dedicated for hacking, but I'll address some of the stuff I feel is muy importante about programming. I am not a professional programmer, but I do have experience and I do want to share some of the stuff professionals have taught me.

How To: You're Tying Your Shoes Wrong—Here's How to Lace Them for Hurt-Free Feet
Upgrading from velcro-only shoes to laced-up sneakers is an important step in life. Days are spent practicing the perfect bow-tying method, and people even argue as adults over tying with the bunny ear method versus the loop-and-wrap trick.

Food Tool Friday: This $9 Idiot-Proof Knife Sharpener Gets Amazing Results
When I finally saved up some cash and got my first good chef's knife, I vowed to do everything by the book: clean it properly, hone it regularly, sharpen it faithfully, stand by it in sickness and in health, blah blah blabbity blah.

How To: Take Your Cocktails to the Next Level with Egg Whites
Most primary cocktail ingredients just sound delicious. Lime and tonic water? Yes, please. Bitters and simple syrup? Sign me up. Egg whites and... wait... egg whites? In a cocktail?

How To: 4 Reasons Why Your Stand Mixer Is More Versatile Than You Ever Imagined
A lot of people like to trash stand mixers for being overpriced and rarely used kitchen appliances. As an avid bread baker I certainly don't agree with that assessment, but I understand where people are coming from. A good Kitchen Aid stand mixer costs a few hundred dollars, and if you only occasionally bake, you probably don't use it much, and therefore aren't getting your money's worth. But what most people don't know is that stand mixers are one of the most versatile appliances in the kitc...

Hack Like a Pro: How to Use Hacking Team's Adobe Flash Exploit
Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

How To: 3 Brilliant Culinary Uses for Bad-Tasting Vodka
In my opinion, vodka gets a lot of undeserved flak. It seems like most people have a bad experience in college with a plastic bottle of vodka and never go back. I can't blame them; it took me a few years after graduating college to start to enjoy vodka again—but now I adore it.

How To: Make a Locked File Cracker with Python
Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

SEToolkit: Metasploit's Best Friend
If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

How To: Fun with OSX Terminal
Disclaimer: All information in this tutorial is for entertainment and educational purposes ONLY. You pesky teenagers.

How To: The Trick to Cutting Onions Without Making You Cry
Even though you may love onions, cutting them is probably a completely different story. You've really got to be a pro at slicing and dicing them without getting frustrated, and even then they can still make your cry—literally. But if you don't want to wear a pair of goggles to keep those tears from falling, you have to cut your onions in a very special way.

How To: Create Backdoor on OSX
Hello, ladies and gents! Today I will be discussing the fun and excitement of backdoor on an OSX system.

How To: Max Out Your Clash of Clans Village Faster on Android
It would be an understatement to say that Supercell hit it big with Clash of Clans. The game has topped both Google Play and the iOS App Store for years and shows no signs of ever slowing down.

How To: Links to Help You Hacking
This is a collection of various guides and tools available on the internet. Instead of searching for 1 you can easily find whaht your looking for here.

How To: Make Amazing Garlic Paste Without a Clunky Garlic Press
There may be no kitchen appliance as controversial as the garlic press. Professional kitchens and many avid cooks despise it, while others staunchly defend it.
How To: Mute Shutter Sounds, Schedule Texts, Disable Status Bar Icons, & More on Your Galaxy S6
Carriers like to distinguish their Android phones from the competition by making small changes to the interface here and there. This practice is so common that Android now has a built-in system for managing these small tweaks.

How To: Linux Basics Tips
Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Hack Like a Pro: Digital Forensics for the Aspiring Hacker, Part 6 (Using IDA Pro)
Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

How To: Writing 64-Bit Shellcode - Part 1 (Beginner Assembly)
In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Hack Like a Pro: Linux Basics for the Aspiring Hacker, Part 24 (The Linux Philosophy)
Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

How To: Make a Fake Identity
Inspiration for tutorial: Foxtrot's "How to Trap a Tracker"
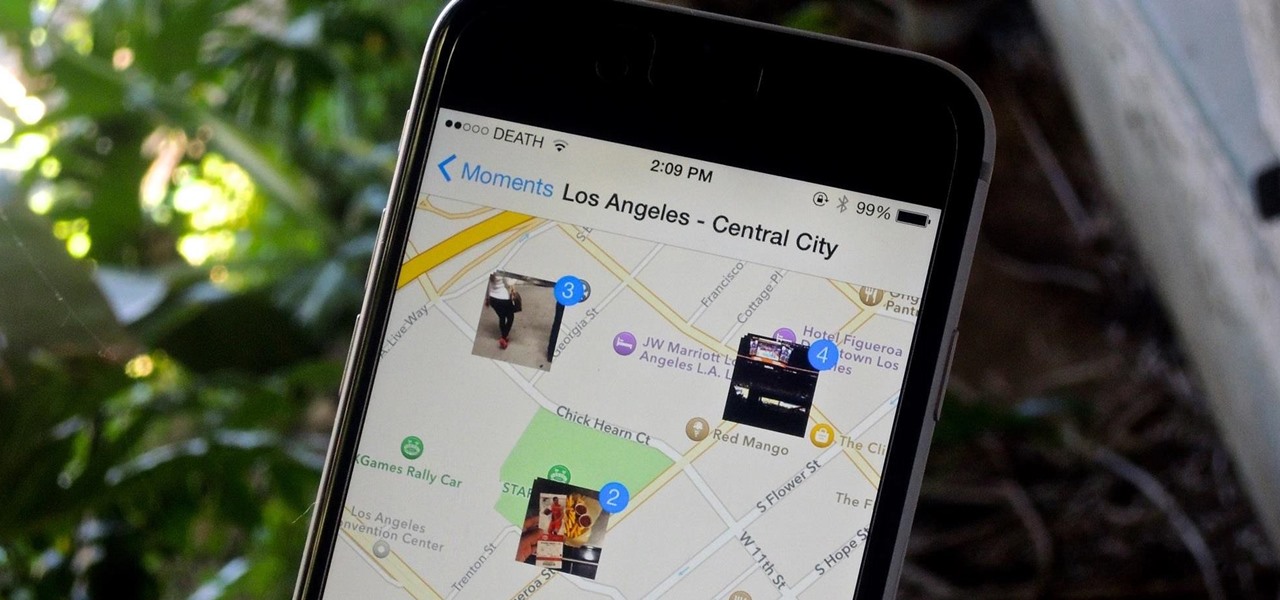
How To: Your Photo Texts Might Be Giving Away Your Location (Here's How to Prevent It on iPhones)
Location Services, a native feature on iPhones since iOS 6, is used to pinpoint your approximate location using a combination of GPS, Bluetooth, Wi-Fi, and cell tower information. Apple uses this on their smartphones for many useful reasons: so that you can tag locations in Instagram, get better directions in Maps, and check for matches based on your location in Tinder.

HIOB: WebSite Hacking Series Part 2: Hacking WebSites Using The DotNetNuke Vulnerability
Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.
How To: Properly Assist Someone as a Xbox Ambassador
Welcome back for another How-To on the Xbox Community Ambassadors World! In this How-To, we are going to tell you how to help someone the right way so you can get a 9/9 rating when your finished assisting someone! Lets begin, shall we?

How To: Creating a (Almost) Fully Undetectable EXE Using Kali & GCC
First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

Feet Don't Lie: Look Down to Tell What Others Are Really Thinking
The importance of body language is stressed from an early age: watch those around you, and you'll know what they're thinking. While you might be skilled at deciphering the messages of crossed arms, slouched sitting, eye movements, and hand gestures, the key to understanding those around you is a little less obvious.

How To: Clean Up Liquid Spills More Easily with Flour
Spills happen in the kitchen, and while every good cook knows to clean as you go, not every cook has an endless supply of cleaning materials. Besides, one spill can exhaust your entire stockpile of sponges, paper towels, and rags in a matter of minutes. Particularly egregious mishaps can make everything they touch feel sticky and gross.

How To: 5 Easy Ways to Boost Your OnePlus One's Performance
The Snapdragon 801 processor inside the OnePlus One puts the device on par with other phones like the HTC One M8 and LG G3 in terms of power and speed. While the OPO is just as fast and responsive as many of the flagships currently available, there's no reason why we can't try to squeeze every last bit of speed and performance out of it.

How To: Protect Apps with a Secret Volume Button Code on Android
App-locking apps have been around for a while, but none have had quite the panache of developer Fazil Kunhamed's latest offering, Oops! AppLock. While others use a PIN or password to restrict access to apps that are installed on Android, AppLock uses a stealthy volume button combo.

How To: Acorns App Makes You a Better Saver Without You Even Noticing
Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

How To: Create Awesome Sweep Picking Licks While Improving Your Guitar Technique
If you are having problems playing your sweep picking arpeggios fast and clean then you are not alone. Many guitarists have the same problem. I suffered from the same problem, years ago. In fact, playing sweep picking arpeggios with poor technique is one of the most common problems that I encounter with my guitar students. After helping them overcome these challenges I have discovered 2 different approaches to improving your sweep picking technique. The first will keep you frustrated with bad...

Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 3 (Payloads)
Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.
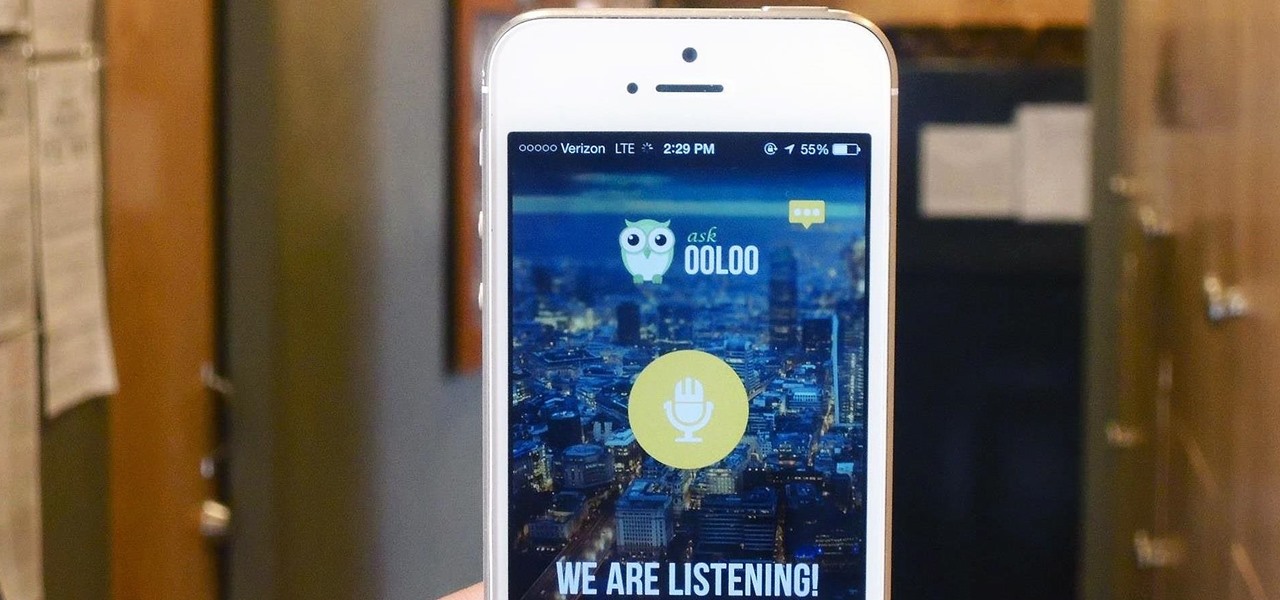
How To: Forget Siri—Get Your Questions Answered by Real People on Your iPhone
Apple has Siri, Google has its Now service, and Microsoft has Cortana. All of these voice-activated services can bring you information quickly and easily without having to type anything into your smartphone. Speak and within seconds you're provided with either an answer or somewhere you can find it.

Silence Is Golden: Why Keeping Quiet at Work Is Actually a Good Thing
Unless you're someone who's terrified of social situations, chances are you love to talk. But no matter how much you want to share you life story or take over the conversation, you shouldn't. Your socially awkward coworkers that keep their mouth shut might actually have a leg up on you at work, and here's why.

How To: Black Out System Apps on Your Samsung Galaxy S5 for Better Battery Life
As I've explained before, black app backgrounds save you a bit of battery life on your Samsung Galaxy S5. This is because the AMOLED display on your S5 does not have to power pixels or a backlight for portions of the screen that are black.

