Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

I've never understood the phrase "smooth as a baby's bottom" to describe a really close shave. I mean, have you ever touched a baby's cheek? It's even smoother and a lot more sanitary. It just doesn't spew off the tongue as nice.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm down.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

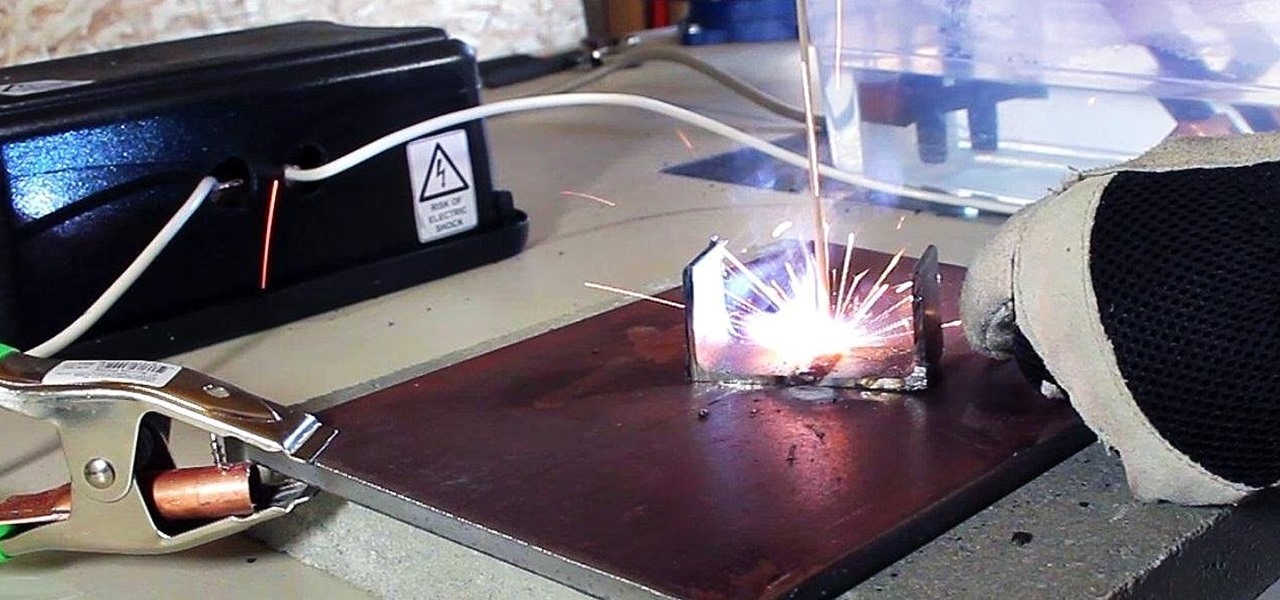
In a previous article, I demonstrated an Arc Welder made using parts from old microwave ovens. Video: .

I'm sure that there are plenty of people out there who have no idea what a plague doctor is/was, so I'll start with an explanation.

Anyone that has ever watched a member of the opposite sex play a video game knows that the other gender does it wrong.

Not that long ago I wrote an article discussing what it would be like, realistically, if you were to accidentally travel back in time to the Victorian era. At the end of that article, I mentioned that the best thing you could bring with you on a time-traveling adventure is a Kindle, or similar e-reader, stuffed full of the knowledge of the 21st century. Why a Kindle? Well, I own a Kindle, and I love it. However, there's far more to it than that.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

Steampunk music is an oft-debated genre, full of bands playing all sorts of different sounds. While this can make it difficult to generalize about the genre as a whole, it means that the average person is bound to like at least some Steampunk bands. That's why it's a great idea to support some independent Steampunk bands this holiday season by buying their music for yourself, or sharing it with someone else.

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.

One of the greatest consoles ever to exist in the world of gaming is the PlayStation 3, which even lets you do a million different things unrelated to games. But no matter how big of PS3 fan you are, you have to admit that the internal browser is not the greatest. Far from it. While you can access most websites from the PS3, a lot of those site's functions are limited, including Facebook. After reaching over one billion users earlier this month, Facebook is undoubtedly one of the most popular...

A continuation of my earlier science testing in Minecraft, I worked on a few things requested and retouched on TNT as there was suggestion of possible (and confirmed) altered circumstances.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

A car that needs to be jump started is going to make a clicking noise but things such as the lights and radio will not turn on. To jump start the car first you need to line the cars up so that the batteries are in line with each other. You will need a working car to jump the car that has the dead battery and a set of working jumper cables. Make sure both cars are completely turned off. Make sure that you keep the two sides of the jumper cables a part. You don't want the two sides of the cable...

Hacking flash games is the new coolest thing these days... now hackers can be anywhere, ever expanding, all thanks to a little cheating program called Cheat Engine. Check out this video tutorial to learn how to download and install Cheat Engine to hack flash games.

In this instructional video series, learn how to play a 6-2 defense. Understand how the game works, with an introduction to the basic rules and objectives, as well as a rundown of the offensive and defensive positions on the field. Lessons also include skills and techniques for beginner offensive and defensive players: how to carry the ball, throw a pass, block effectively, punt, and make a solid hand off.

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song. This series is a grea...

In these intermediate drawing lessons, learn how to transform simple shapes into an abstract creation. Our expert will help you understand how to use cubes and prisms, as well as bend the rules of perspective, to create a feeling of dynamic action in your drawings.

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert, Bill Macpherson, will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song. Thi...

With this video series you will be able to learn about the bass guitar and everything you need to know to start playing. Begin by learning the parts of the guitar. Our expert will break down the parts of the bass guitar so you understand what each part does.

In this video series, our expert will show you how to replace, repair and maintain your motorcycle brakes. You will get step-by-step instructions on disassembling your wheel, and brake components, cleaning the brake caliper and master cylinder, repairing broken parts, and finally, reassembling your motorcycle when you are finished. Our experts instruction will give you the knowledge to fix and maintain your own motorcycle brakes, as well as enhance the general understanding of your motorcycle...

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

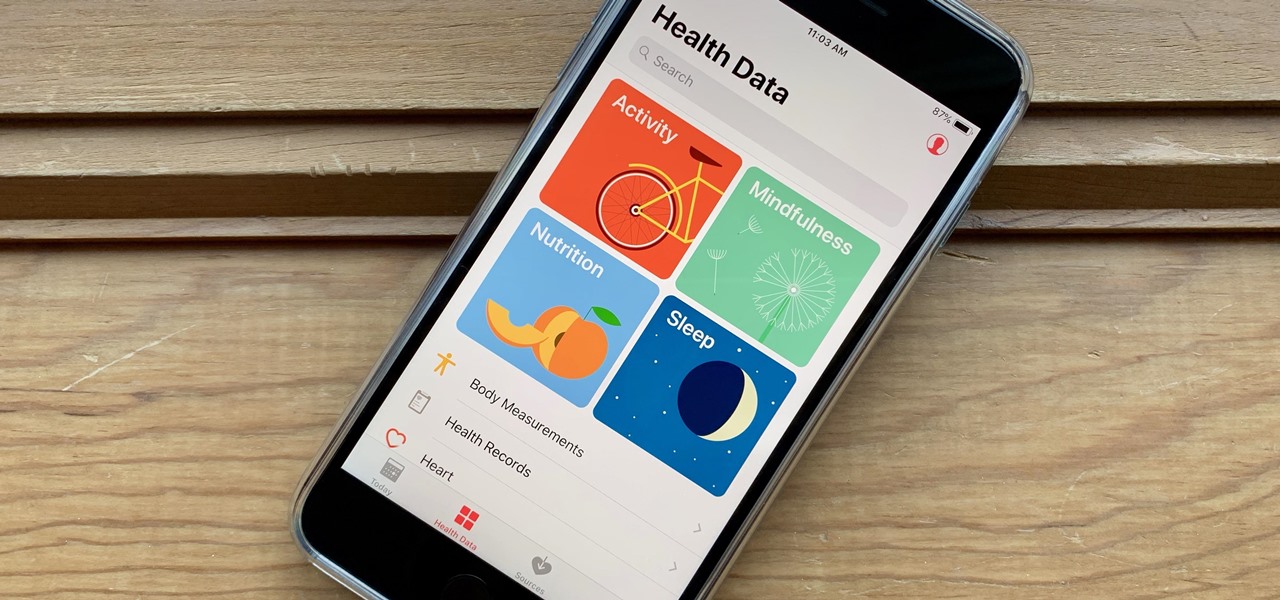
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

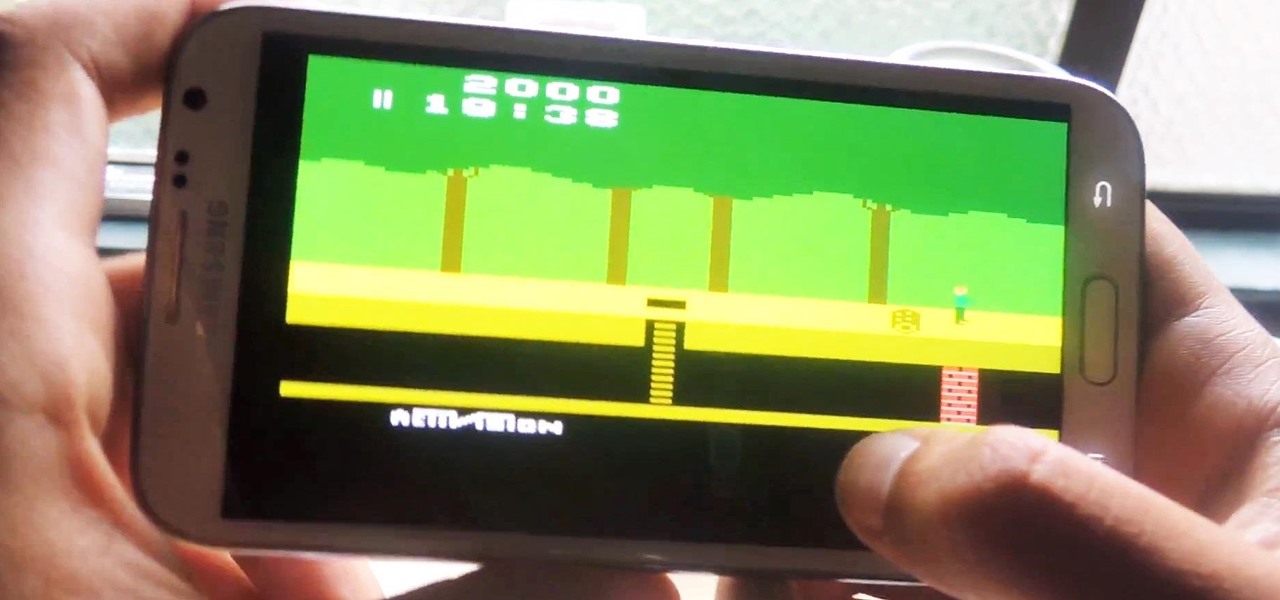
Atari—it's the home gaming console officially responsible for starting the trend of sleepless nights and malnutrition amongst kids and adults alike. If you think Call of Duty is addicting, try playing Space Invaders in the '80s on the old Atari 2600 (voted the second greatest console of all time by IGN).

Learn how to bend circuits, disassemble toy cases, unscrew circuit boards and test a circuit bend in this free video series that will help you understand how and when to utilize this unique way of making music.