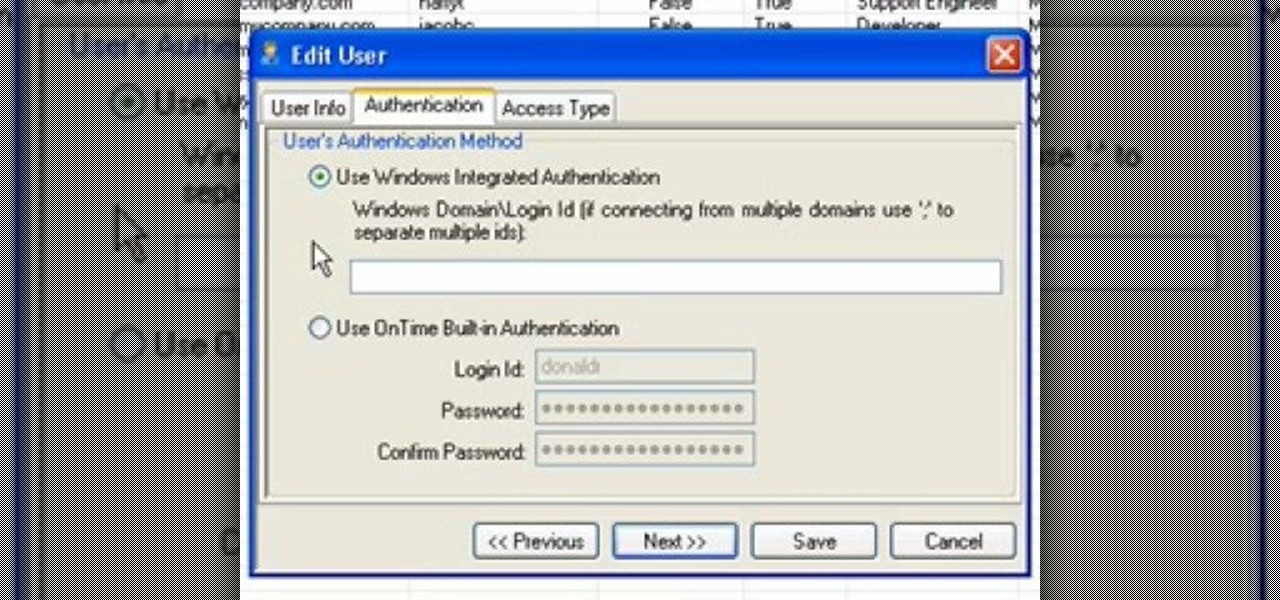
There are two different methods of Authentication in OnTime, and each method has two different ways that the authentication can take place. In this installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite you'll learn about these forms of authentication.
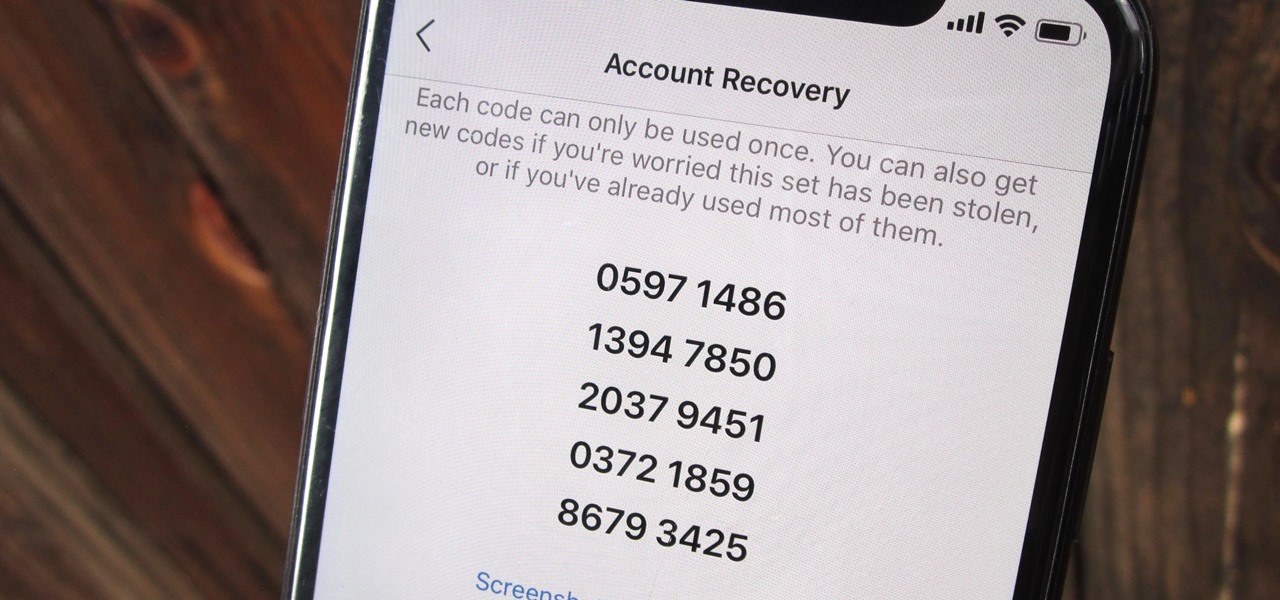
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.
In this free video programming lesson, we learn how to get started using authentication when coding in Ruby on Rails 3. Whether you're entirely new to Ruby on Rails 3 or are a seasoned developer merely looking to brush up on a few of the basics, you're sure to find much to take away. For more information, take a look!
In this clip, you'll learn how to code a simple user authentication system with PHP. Whether you're new to the PHP: Hypertext Preprocessor scripting language or are a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free video programming lesson. For more information, including detailed, step-by-step instructions, take a look.

Watch how to configure LDAPS Authentication on the BIG-IP Edge Gateway with BIG-IP LTM functionality. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

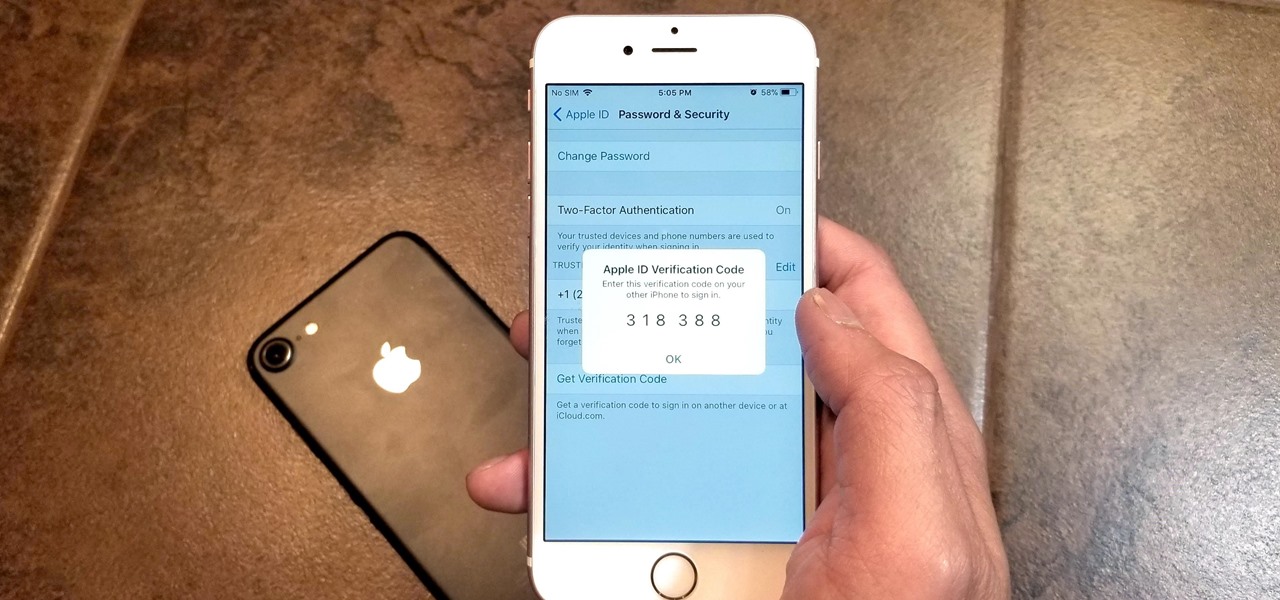
Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.

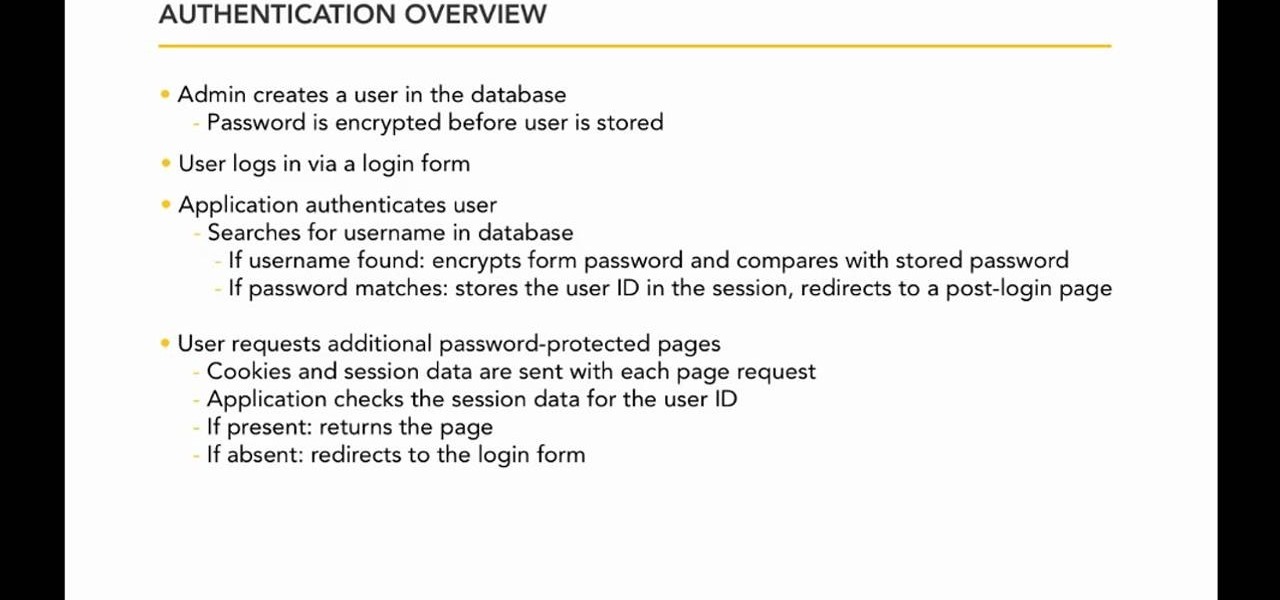
Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

Join Patrick Hynds as he demonstrates how to set up the SQL Membership Provider to add Forms authentication to your ASP.NET 2.0 Web site, in this video tutorial. There are a few tips and tricks involved, such as using the aspnet_regsql.exe utility, which are covered in the video.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

Haptic feedback is one of the iPhone's most underrated features. With Face ID, you'll feel a satisfying tap or two when buying something in the App Store or iTunes, unlocking protected notes, viewing saved passwords in Settings, and the list goes on. For the first time, Apple has added haptic feedback when unlocking your iPhone via Face ID, as well as a way to disable haptic feedback for Face ID entirely.

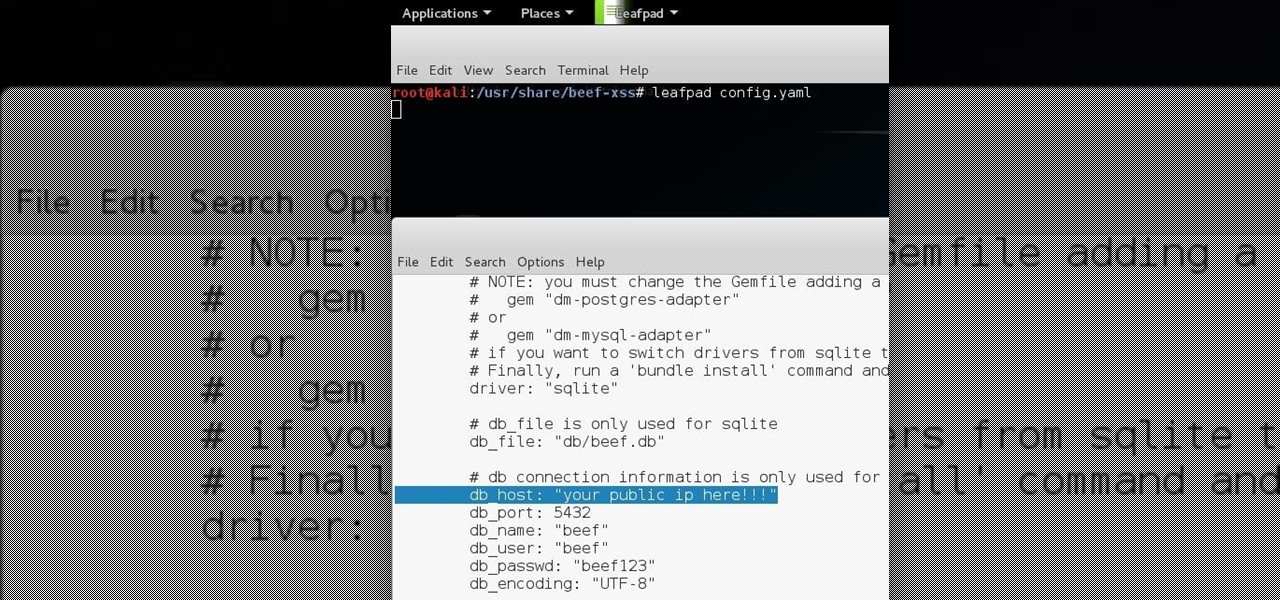
Hello all Just thought id share how ive managed to get beef working over the internet.

After you've published your site, you might decide you want to add additional pages over time. To add an additional page to my site, all I have to do is click the "Add Page" button in iWeb.

Do you need additional hard drives in your computer for additional drive or storage space? Learn how to install a second IDE hard drive in a desktop PC all by yourself, in just a few simple steps.

Among the many new changes ushered in by the iPhone 7, only one has the potential to completely change the way you interact with your smartphone—a new 3D Touch-enabled home button. Instead of the mechanical click we've grown accustomed to, your home button will now behave like the rest of the phone's touch screen interface.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

In this clip, we learn how to download additional Ovi Maps-compatible maps when using a Nokia C5 mobile phone. The C5 is the first offering in Nokia's new "C" series of mobile phones. It runs on Nokia's Symbian OS and features a 2.2-inch screen and 3.2-megapixel camera. Want more? Search WonderHowTo's sizable collection of C5 video tutorials.

In this Click Here Photography instructional video, learn how to photograph using a fill flash to produce a great photograph. Equipment, how to set-up, and additional props are gone over. Although a fill flash takes some time to set-up & is an additional item to carry, it will produce better photographic results in certain lighting situations. Learn how to experiment with your fill flash and maximize your photo's potential with the advice, tips, and information given here.

Take a look at this tutorial and learn how to get additional features on your iTUnes with Growltunes. On top of polling features, this application allows you to use various instant messagers such as amsn, msn, and skype.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional TTF fonts on Ubuntu Linux.

In this video tutorial, viewers learn how to use Flickr photos in their screen-saver. This task can only be done on the Windows computer. Users will need to download the program from the website provided in the video. Once downloaded and installed, there is an option in the Screen Saver Settings. Users are able to take photos from specific users or groups, or can search through tags and contacts. Further options include selecting the size of the photo and delay between switching the photos. U...

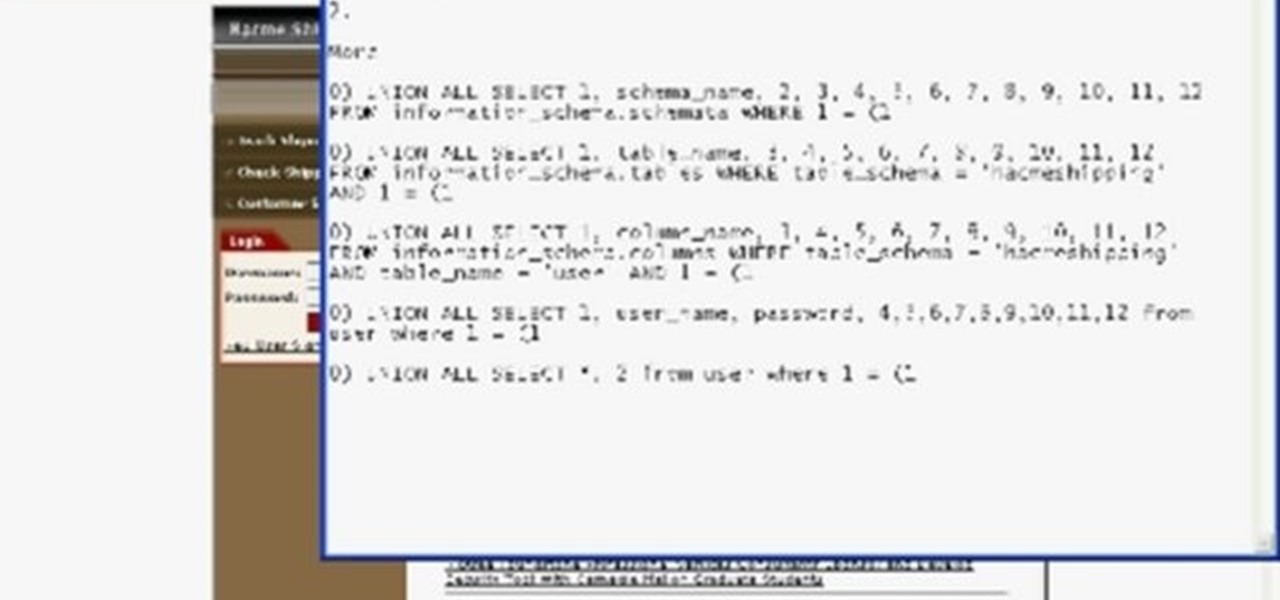
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

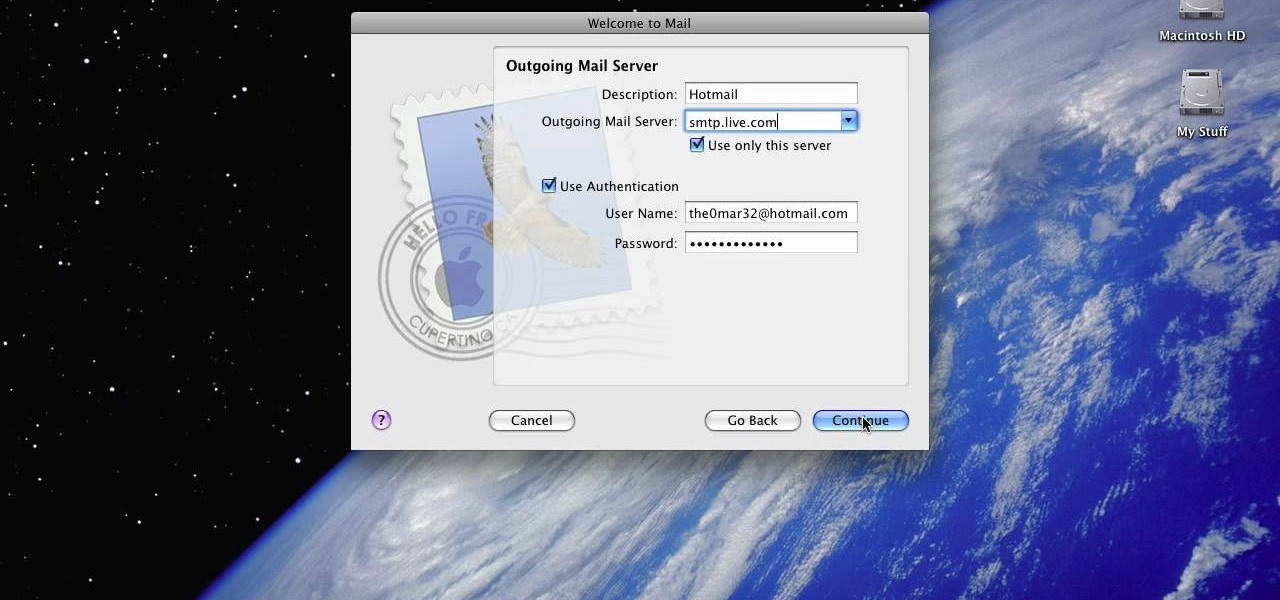
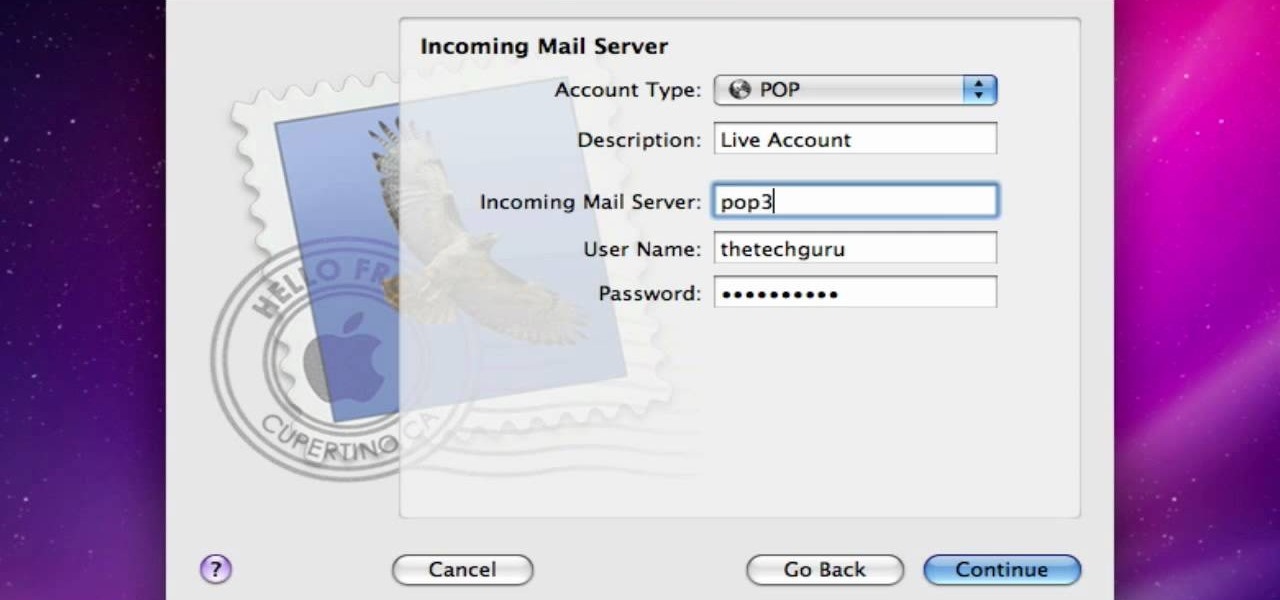
The video shows you how to link your hotmail account to your Mac. The person first asks you to open the mail and write down your full name, hotmail id and the password in the boxes given there. Then click on continue, and in the next option box, leave the account type as POP and then give a description as hotmail in the space provided. Then you have to type pop3. live.com in the box given for incoming mail server. Once done, click on continue and it will ask you for description of outgoing ma...

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

With 16 megapixels and optical image stabilization technology, it's safe to say that the Samsung Galaxy S6 is well-equipped to take badass pictures. Packed with additional camera modes, like Panorama, Selective focus, and Virtual shot, there's always a way to capture an image as intended.

This technique can be used to write answers for a question asked in the exam or can be used to write a paragraph while applying for a scholarship or while writing a brief letter. The main thing to be considered while writing the paragraph is having an outline, all we need to do is prepare an outline before starting the paragraph. First write the "main idea" that is to be delivered, then the main idea should be supported with additional details, there can be two to three additional points to s...

This video shows you how to install additional memory into a Power Mac G5 1.8 single processor system. You do need to install the memory in matched pairs so keep that in mind when you're buying the memory.

This tutorial shows you how to add an additional track for background music, voice over or any other audio assets when you already have existing audio in Sony Vegas 7.

In this video from AppleGenius0921 we learn how to enable a Live/Hotmail account on the Mail application on a Mac. Open Mail. In full name put your full name. Type in your email address and password and continue. Leave the account type on POP and name the description what you'd like. The incoming mail server is pop3.live.com. Type in your live.come username with @live.com in it! Click Continue. The outgoing mail server should be smtp.live.com. Check use only this server and check use authenti...

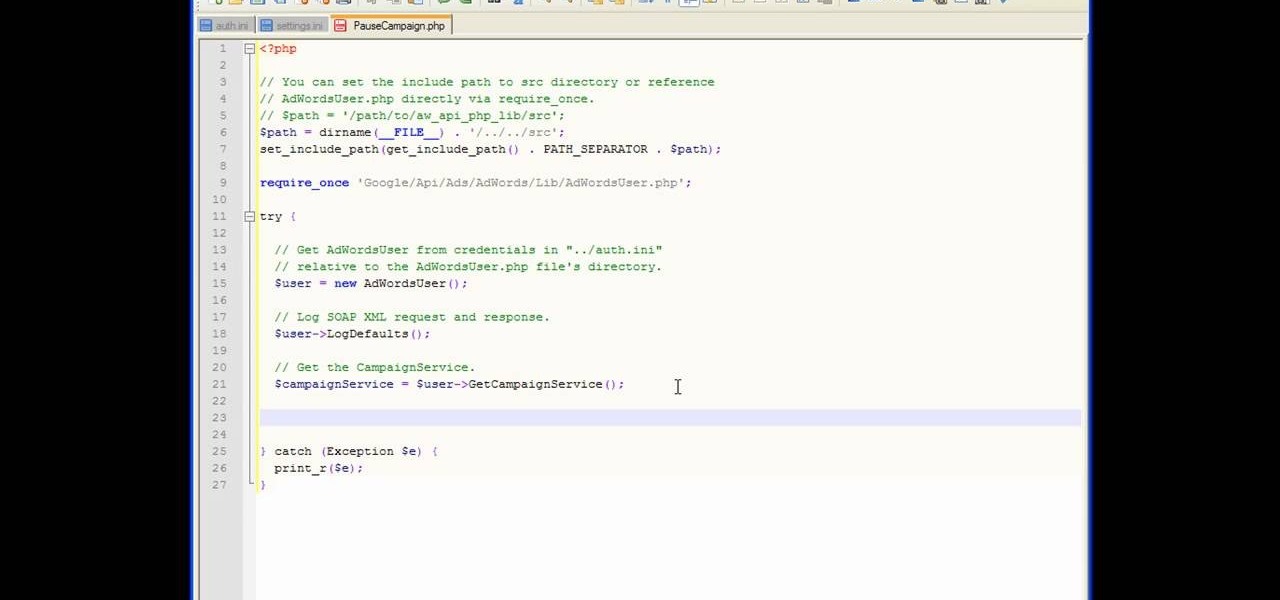
In this tutorial, we learn how to get started with the AdWords API PHP client library. First, download the library by going to the API documentation online. From here, set the authentication information and then open up the library. Now, save the changes to the file and use a sandbox environment. The examples folder has all versions that the API library supports. You can browse the campus folder with the search button, just type in the command of what you want to see. After you do this, you c...