The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

When Apple acquired the popular Workflow app in 2017, many were worried that it would either get replaced with something much worse, or just disappear entirely. Thankfully, Apple put these concerns to rest with the launch of Shortcuts. In iOS 13, Shortcuts is becoming more powerful than ever, providing functionality on the iPhone that the original Workflow team could only dream of.
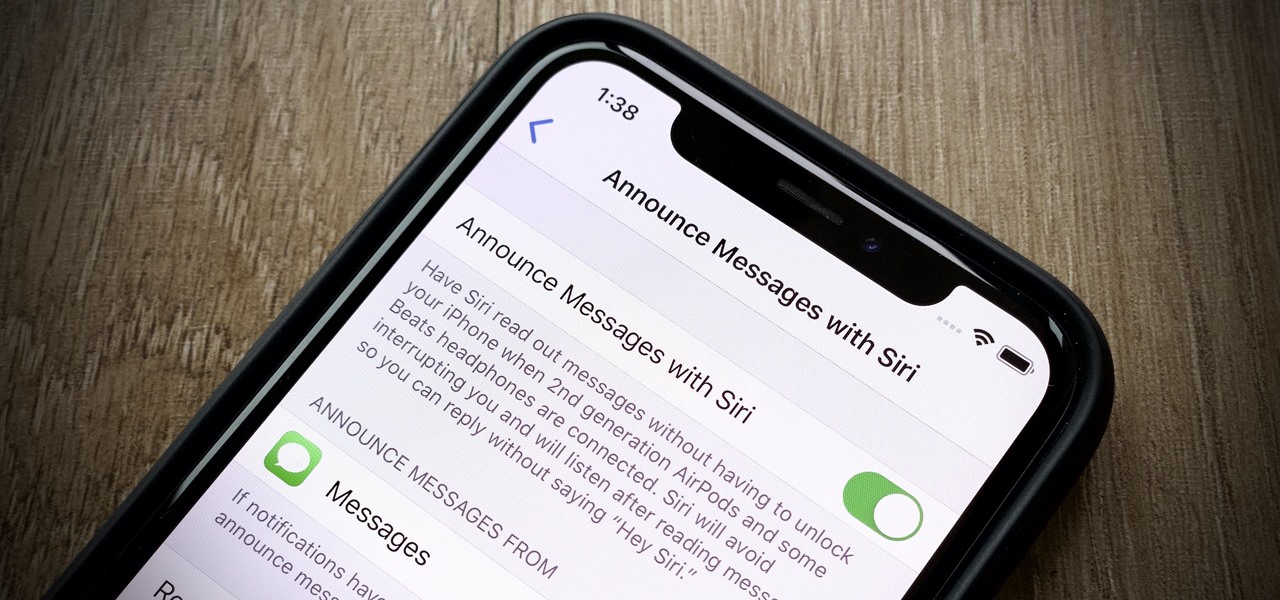
Apple's iOS 13 has been quite the disrupter. The initial update featured over 200 new features and changes, while its successor, iOS 13.1, brought another 22 to the mix. With the company's latest update, iOS 13.2, you'll see an extra 22 amendments on your iPhone, including new emojis, Deep Fusion on iPhone 11, 11 Pro, and 11 Pro Max, and Announce Messages with Siri, just to name a few.

To be honest, the Mail app for iPhone had always been somewhat forgettable. It lacked many of the features that made third-party clients like Spark and Edison better, but with iOS 13, the gap between Mail and its competitors is much smaller. Apple updated the layout and added many new features to its native emailing app, and that may be just enough to get you to switch back.
Yesterday showed us our first look at the iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. But it wasn't all about hardware. Apple also released the iOS 13 Golden Master, making iOS 13.1 the main focus for us beta testers. Now, Apple just seeded the third public beta, following yesterday's release of 13.1 dev beta 3.

It's a big day for Apple. First, the company announced its new suite of phones: iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. Then, we get the iOS 13 Golden Master, the beta version of iOS 13 that will eventually release to the general public on Sept. 19. Now, it seems the company has dropped the third developer beta for iOS 13.1, set to release to all compatible iPhones on Sept. 30.

Apple has pulled quite the headscratcher in anticipation of its big iPhone unveiling next week. Its latest iPhone update, iOS 13.0, is just on the horizon, going through eight beta versions so far. And yet, before that software's official release, the company has started beta testing iOS 13.1, with no explanation why. And the second public beta for iOS 13.1 is now out, so let's see what's new.

When Apple takes the stage next week, we have no idea what version of iOS it will release. For months it seemed like a given that we would, of course, see iOS 13 seeded to our iPhones. Now, we aren't sure if Apple will tout iOS 13 or iOS 13.1, since the latter is now the focus of its beta testing. In fact, 13.1's second developer beta is now available to download and install.

After months of back and forth, ZTE is finally making their return to the United States. The last phone the Chinese company released here was the Axon 7 Pro, a low priced flagship phone that competed well against the OnePlus 3 and 3T at the time. Its successor is the Axon 10 Pro, which adopts the same strategy.

Beta testing certainly has its perks. While you do need to deal with bugs, you're introduced to new features before the general community. And if we're talking iPhones, there are over 200 new features in iOS 13 beta. If you're already on board with iOS 13 public beta 6 for iPhone, you can get an upgrade on that firmware as Apple just released public beta 7 today.

The fifth annual Amazon Prime Day is upon us. Starting July 15, Amazon will offer thousands of deals on products across its site, kicking off at 3 a.m. EDT. This year, it will only run for 48 hours, so you have even less time to act. To save you some of that time, we made a list of the best deals for smartphone accessories.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

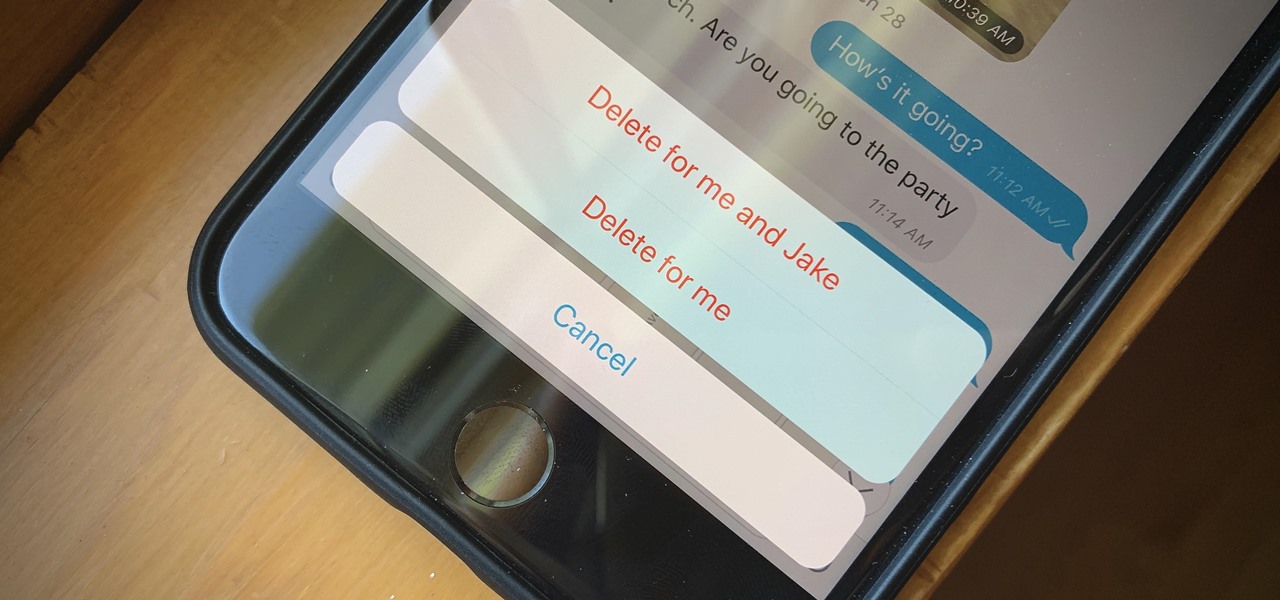
If you're looking to keep your conversations private, look no further than Telegram. Its cloud-based chats are secure and its optional end-to-end encrypted chats even more so, but you can't really prevent someone in the conversation from sharing your messages. However, you can lessen that chance by taking back your messages, deleting them for both you and the other end of the discussion.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.

Apple released iOS 12.3, the latest version iOS 12 for iPhone, on May 13. Great features to know about include Apple TV Channels such as HBO and Showtime that you can subscribe to in the TV app, support for audio, image, and video streaming to AirPlay 2-enabled TVs, and the ability to use Apple Pay to pay for content and subscriptions inside Apple's own apps.

The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

In 2019, Sony is mixing up its design, attempting to stand out among the sea of familiarity. Instead of emulating Samsung with punch hole cameras, they decided to target a rare section of the market, content consumers. There's the Xperia 1 for those who want the best, and the Xperia 10 and 10 Plus for the budget crowd.

After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.

Once again, LG is mixing up its launch. Instead of the announcing the latest entry in G series later in the year, the LG G8 ThinQ was announced at Mobile World Congress 2019, shortly after Samsung's Galaxy S10 event. And instead of trying to match what other OEMs are doing, LG is once again trying to be different.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

When Facebook introduced Stories in 2017, many users despised the Snapchat-like feature on their main page. However, despite the outcry, Facebook doesn't plan to let you remove it. But you don't have to settle for this. With the help of some third-party apps, you no longer have to deal with Stories.

Google's next-gen cellular carrier, Google Fi, which replaces Project Fi, is making waves across the mobile industry. With super-cheap plans starting at only $20 and the ability to connect to millions of Wi-Fi hotspots across the globe, it's tempting many users to make the switch from AT&T, Sprint, T-Mobile, and Verizon Wireless.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

In this jam-packed October, the Huawei Mate 20 Pro has flown under the radar in the US. Due to Huawei's lack of presence in the States, many are unfamiliar with the second largest OEM in the world. Huawei has continuously put out amazing mobile devices, and this year they released a phone that's nearly perfect on paper.

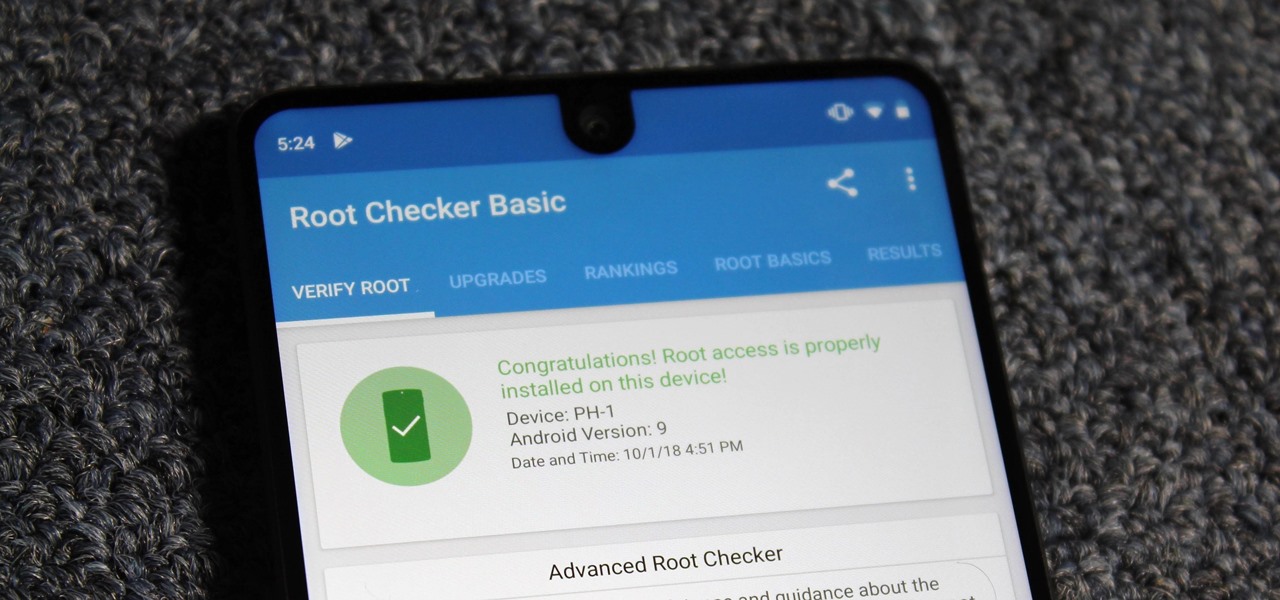
Despite its rocky start, the Essential PH-1 has a lot going for it. Not only does it get consistent security patches and system updates hours after the Pixels, but like the Google-developed lineup, it's also great for rooting. Not only is your warranty not void with rooting, but the process is pretty straightforward.

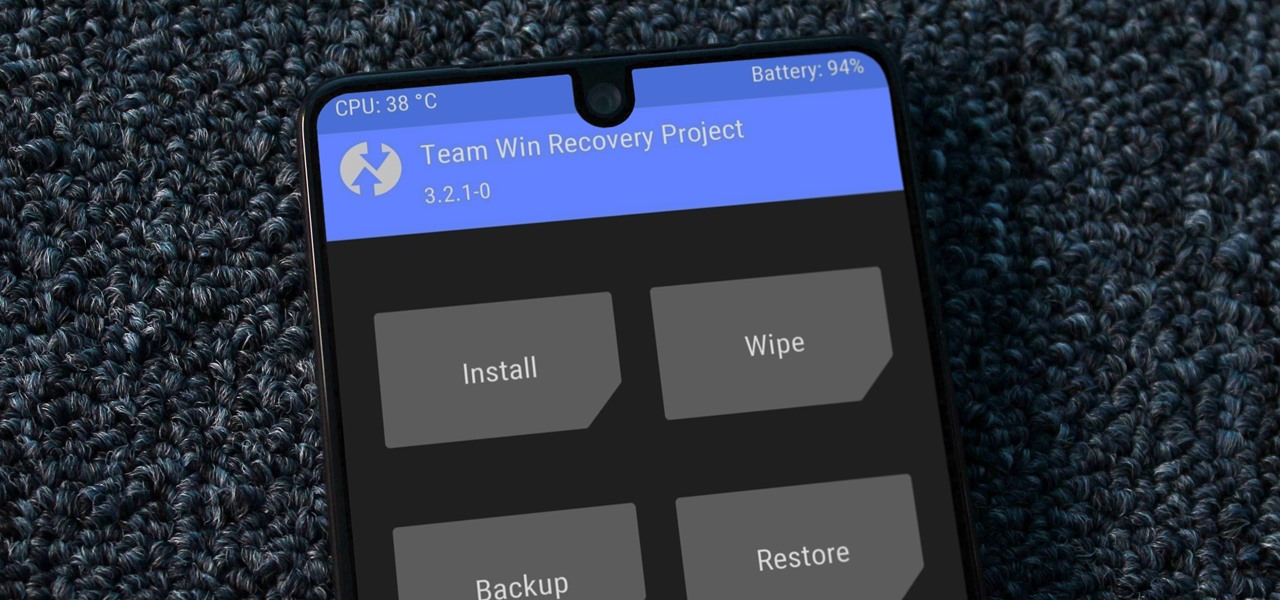
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we'll be digging into the Create app, the experience that allows you to fill the real world with objects that transform the nature of your local reality.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.