These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

A new augmented reality cloud platform from German startup Visualix is working to give enterprises the capability to scan their own warehouses, factories, and stores and create maps for augmented reality navigation.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

For the second time in a row, Apple pushed out a new iOS 12 developer beta on a Monday, and for the first time this round, they've done it only one week after the last one. While the August 6 release of iOS 12 developer beta 6 doesn't contain a wealth of updates, there are still a few things you'll want to know about.
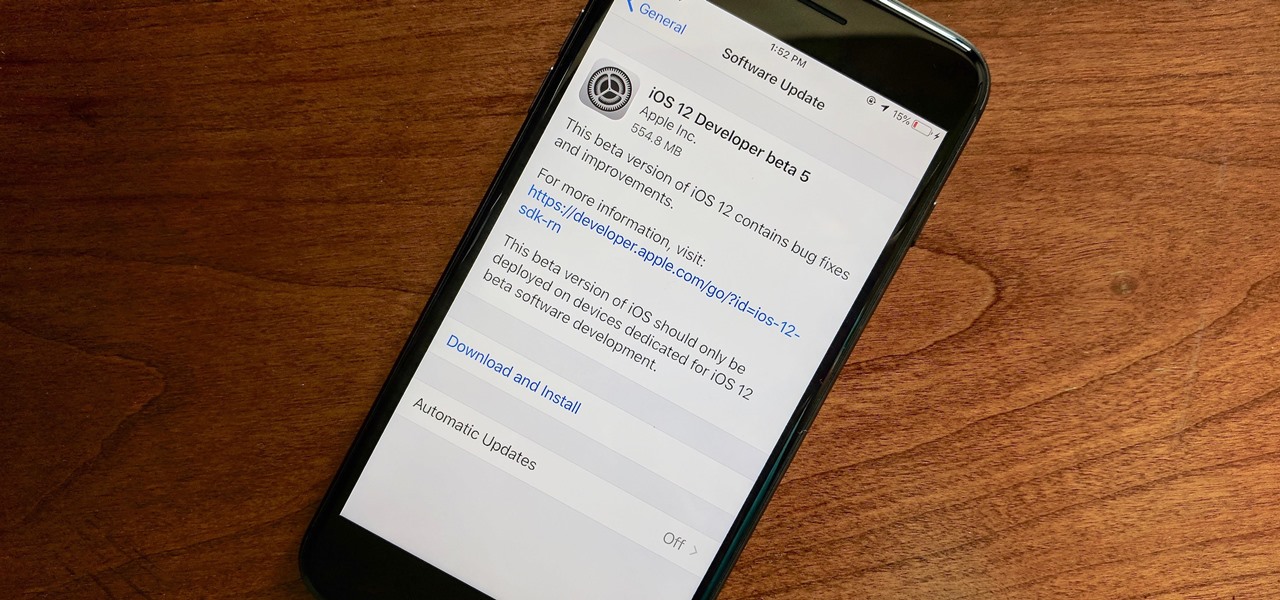
Apple released the fifth developer beta for iOS 12 on Monday, July 30, only 13 days after the release of dev beta 4 and 12 days after public beta 3. Until this release, Apple kept a consistent two-week schedule for developer beta updates, so we were a little surprised to see this one drop one day early.

There's a growing sentiment around the web that when it comes to Android, stock is best. Many people prefer the clean look of Google's vision for Android, but manufacturers like LG will add features and themes on top of this base to differentiate themselves from the pack. But these OEM skins, as they're called, aren't always as overbearing as you might think.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

With all the recent activity around augmented reality, the possibilities involving immersive computing and commerce are quickly becoming obvious, and digital payments giant PayPal has no plans to sit on the sidelines

As the week of the Game Developer's Conference hits the mid-point, we've already had some major announcements hit the AR space. The specific timing of these announcements are thanks in part to a conference within a conference called VRDC, aimed at VR, AR, and MR developers. And while the week is hardly over, the announcement that is still having a big effect on the developer population is the reveal of the Creator Portal for the long-awaited Magic Leap One device.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

In the not so distant past, you had to actually go meet someone in person to repay money you owed them. Say they covered your half of dinner or picked up movie tickets — they wouldn't get their money back at least until the next time you saw them. Thankfully, Venmo has effectively eliminated this inconvenience.

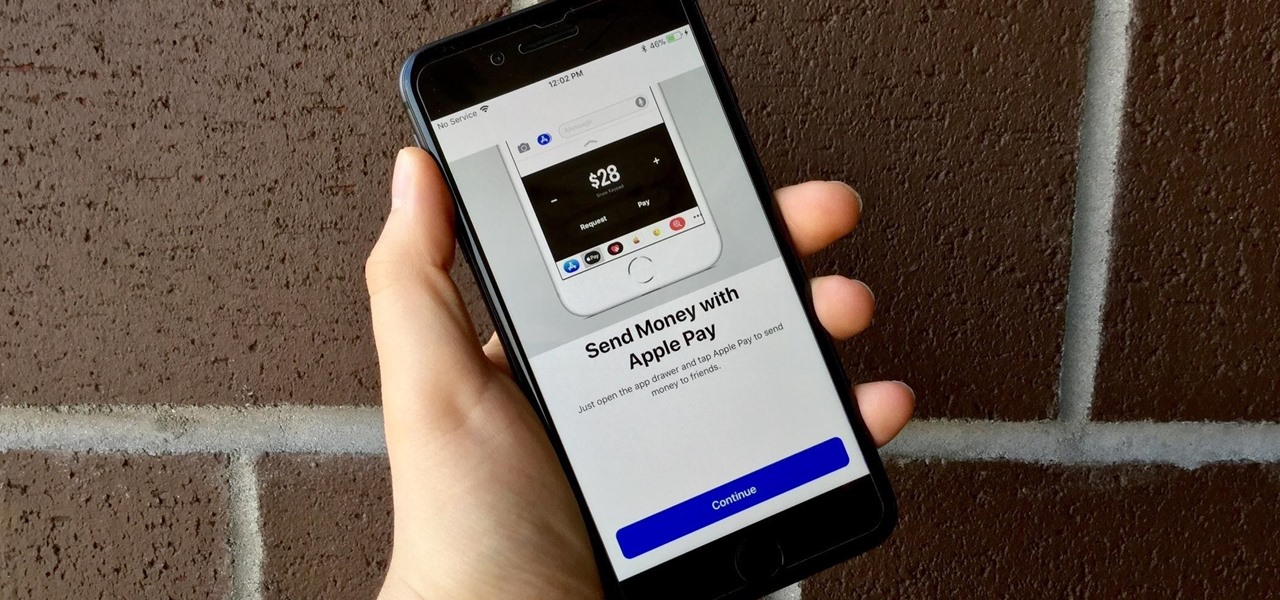
Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Not everyone digs Siri. Some of you probably can't live without the personal assistant on your iPhone, and some of you probably never even use it — and likely never will. If you fall into the latter category of iPhone users, you can simply disable the feature altogether, which will prevent accidentally triggering her or him anymore and will keep your iPhone nice and secure overall.

Reigns recently went on sale on the Google Play Store (sorry, iPhone users), and that inspired me to give it a go. I've wanted to try this one out for a while now, but the steep price tag kept me away. ($2.99 is a lot for me, okay?)

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

In the music world, it's safe to say electric instruments are more versatile, but they lack the portability of their acoustic counterparts. However, with the aid of your smartphone plus an audio interface, you can play your electric instrument anywhere — with all the pedal effects you please — and even record your efforts.

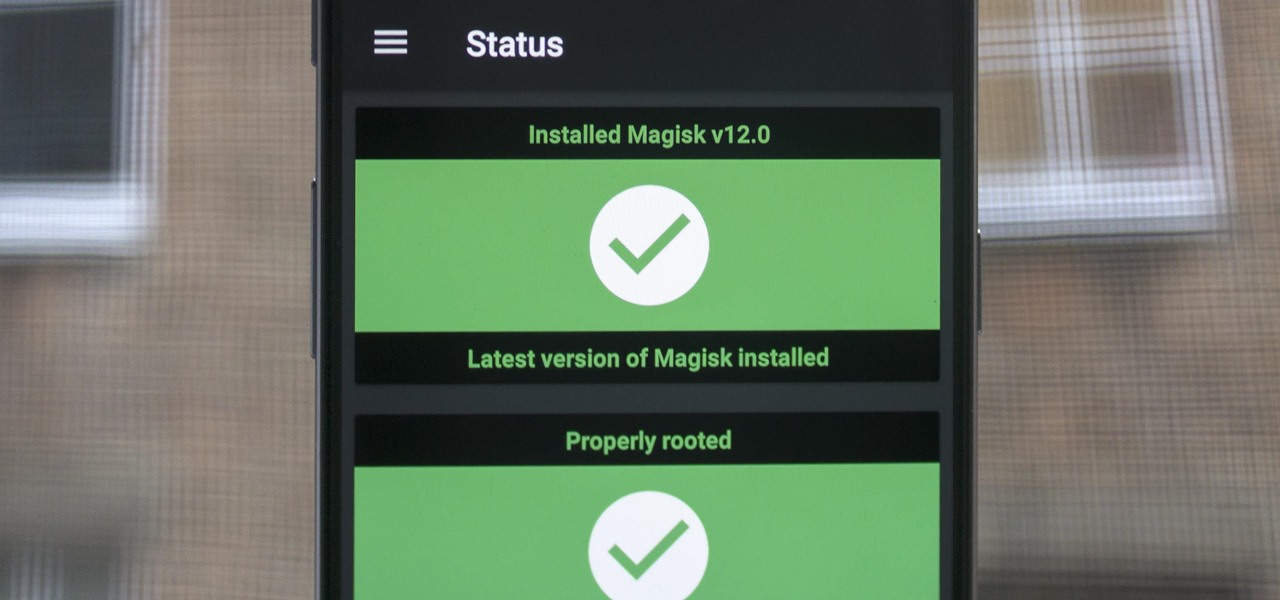
When Google added new security measures to Android Marshmallow, it had a lasting impact on the entire process of rooting. These measures prevent the the Superuser daemon (the process that handles requests for root access) from getting the permissions it needs to do its job at boot. In order to get around these issues, Chainfire created the systemless root method.

Being able to take screenshots on Android isn't something we were always able to do. It was added to stock Android in Ice Cream Sandwich 4.0 (Gingerbread 2.3, if you were a Samsung TouchWiz user) as a simple full screen screenshot, and that's the way it's remained ever since—until now.

Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

To serve as a framework for the "Nexus Imprint" feature in their new Nexus 5X and Nexus 6P smartphones, Google added native fingerprint scanner support to Android 6.0. Sure, Android devices have had fingerprint scanners in the past, but this is a unified, system-wide implementation that all devices can use—meaning that in the near future, we may finally start to see apps that let you log in to your account with your fingerprint instead of a password.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

In my last how-to, we built a man-in-the-middle tool. The aforementioned script only established a man-in-the-middle. Today we'll be building a tool to utilize it. We'll be building a DNS packet sniffer. In a nutshell, this listens for DNS queries from the victim and shows them to us. This allows us to track the victims activity and perform some useful recon.

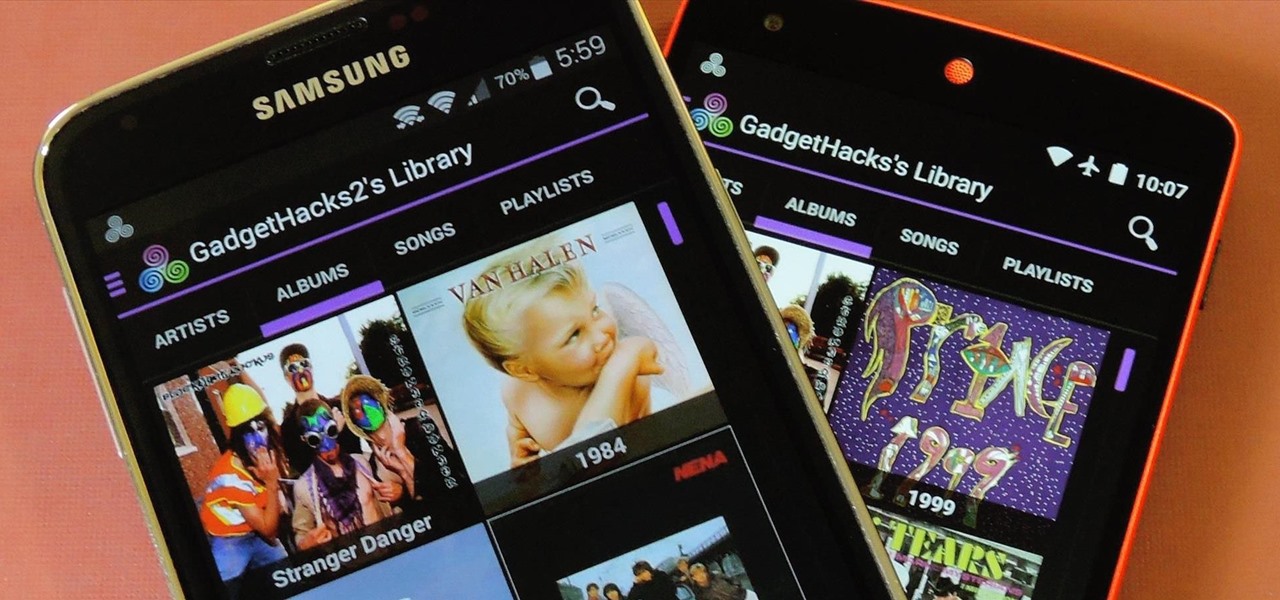
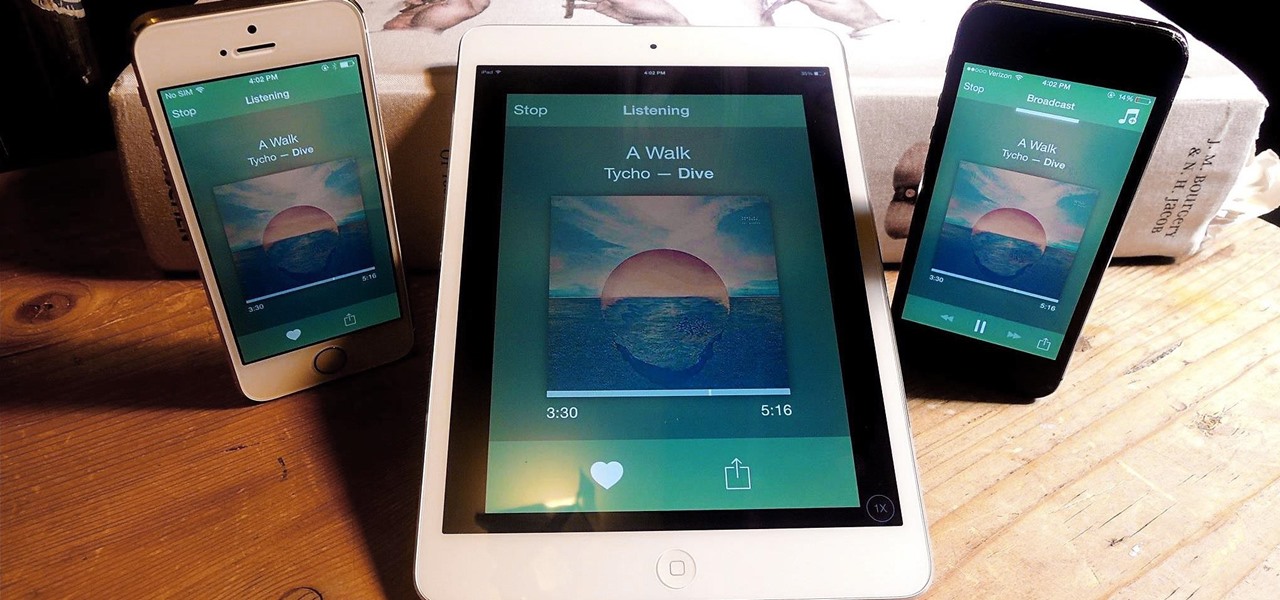
If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Audibly, from iOS developer Nick Frey, allows you create playlists and sync your music across other iOS devices. Like the Samsung-exclusive Group Play or the older Seedio app, you can connect a slew of compatible devices to create a surround-sound stereo of sorts when playing your music.

Currently in its alpha stage, Facebook has pushed forward a redesigned mobile app for Android users that provides a flat user interface and rearranged navigation tools.

If you've been keeping up with anything Android these days, you've no doubt heard about a little dandy called Xposed Framework kicking around. Xposed, by XDA developer rovo89, is a framework for Android devices that lets you easily modify your stock or custom ROM.

Has you rent check bounced again for no apparent reason? It happens to everyone, but if you're roommate needs the money fast, you need to fix it fast, and wire transfers are the fastest way to give money to someone else. Executing a wire transfer is as easy as making one phone call.

Is your Outlook inbox starting to seem overwhelming? No problem! In just a few minutes you can corral that growing pile of e-mail by using the 'archive' feature. Have a look at this video and learn how to use this handy option and clean up the mess in your inbox.

You've boxed up and shipped all your other possessions for the big move and all you're left with is the little issue of how your getting your car there. There are companies out there that will ship your car to you, just make sure your car is prepped for the journey.

Have you ever gotten a friend request on MySpace, Facebook, YouTube, or Twitter from a hot girl and thought, "Wow! This is almost too good to be true!" Well, chances are, it is. In this short tutorial, learn some tricks and tip-offs to spot a fake.

Most people on Facebook accept friend requests without thinking much of it. If you're one of those people and want to figure out how to get rid of a friend, this video is for you.

When we got our first look at US Army soldiers testing Microsoft's modified HoloLens 2 last year, it still looked very much like the commercial edition, with some additional sensors attached.

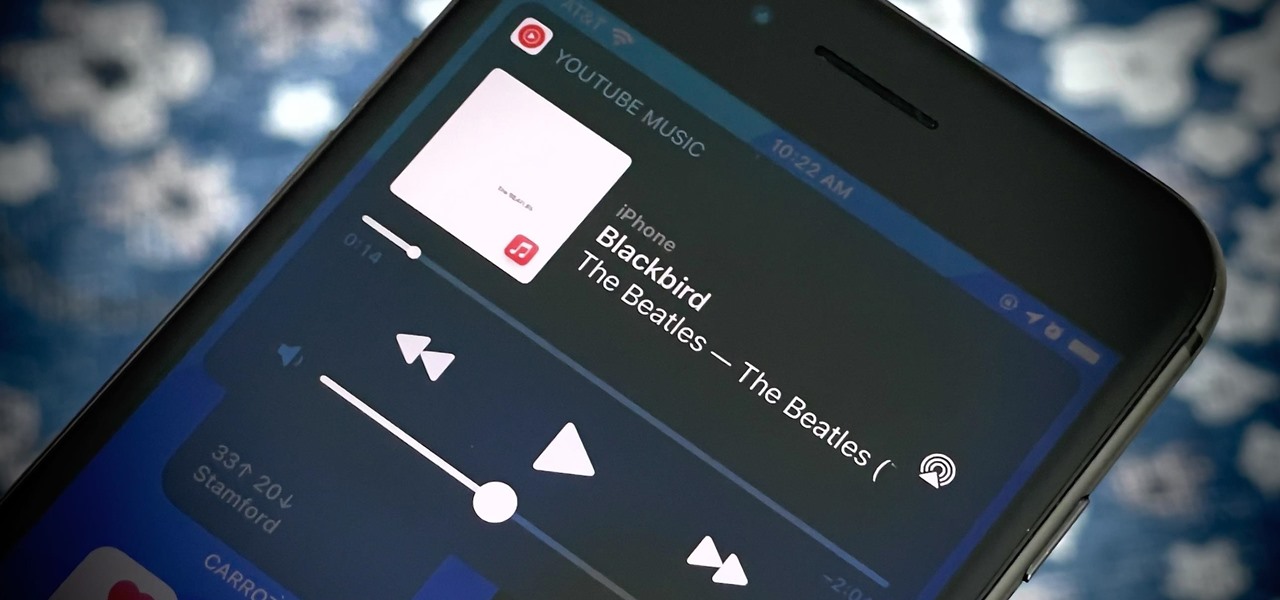
A new feature in iOS 14.5 lets you change your preferred music player for Siri requests. So if you primarily use YouTube Music over Apple Music and other services, Siri will learn so that you never have to tell the virtual assistant to play a song, artist, or album "on YouTube Music" again.