
News: Apple Developing New iPhone Graphics Chip
Apple is in the process of developing its own graphics processors for future iPhones, according to recent reports.


Apple is in the process of developing its own graphics processors for future iPhones, according to recent reports.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

"Necessity, not novelty," is a phrase I use often when it comes to HoloLens development. It would be fair to call it my mantra, or mission statement, as I prototype and explore software creation on this new frontier of mixed reality.

If you've played the game Portal by Valve before, you've most likely popped one portal onto the ceiling and another directly below it on the floor, dropped your Companion Cube in, and then watched it fall forever. Well, now it has been done in real life, in an actual hallway, not in a rendered world.
Emoji, emojis, smilies, or smileys—whatever you want to call them, those little yellow icons have firmly implanted themselves in the human lexicon. However, just like with localized languages and dialects, emoji can be very different from one another depending on the device or operating system you're using.
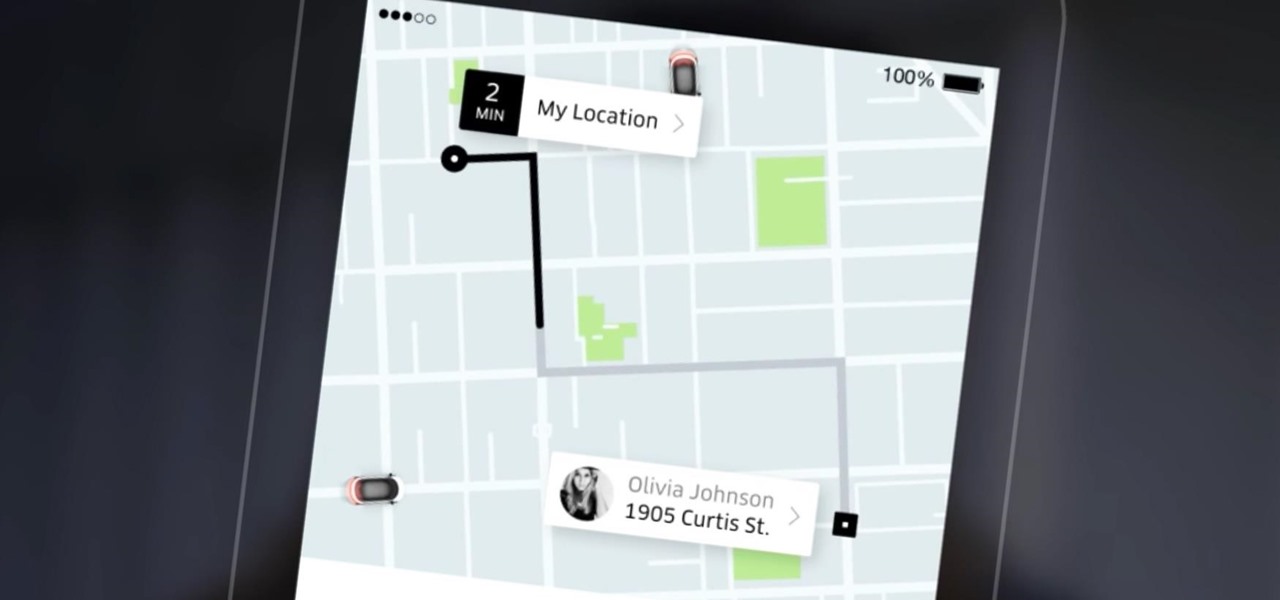
Uber has recently been updating their app on a weekly basis to ensure that users have the smoothest travel experience possible. The entire UI was recently redesigned to increase user-friendliness, the total app size was reduced to improve performance, and an intelligent shortcuts feature was added which tries to guess your next destination.

The OnePlus 3T was released about five months after the OnePlus 3 with several noticeable upgrades. Firstly, it has a new processor, the Qualcomm Snapdragon 821, which is the same one that the Pixel and Pixel XL sport. Second is the 16 MP front-facing camera with a different sensor. And the next big change was a slightly larger 3,400 mAh capacity battery.

The beauty of Android is that nearly everything can be customized. But sometimes, we get so caught up in tweaking functionality and other minutiae that one of the most important interfaces gets neglected—the home screen wallpaper.
One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.
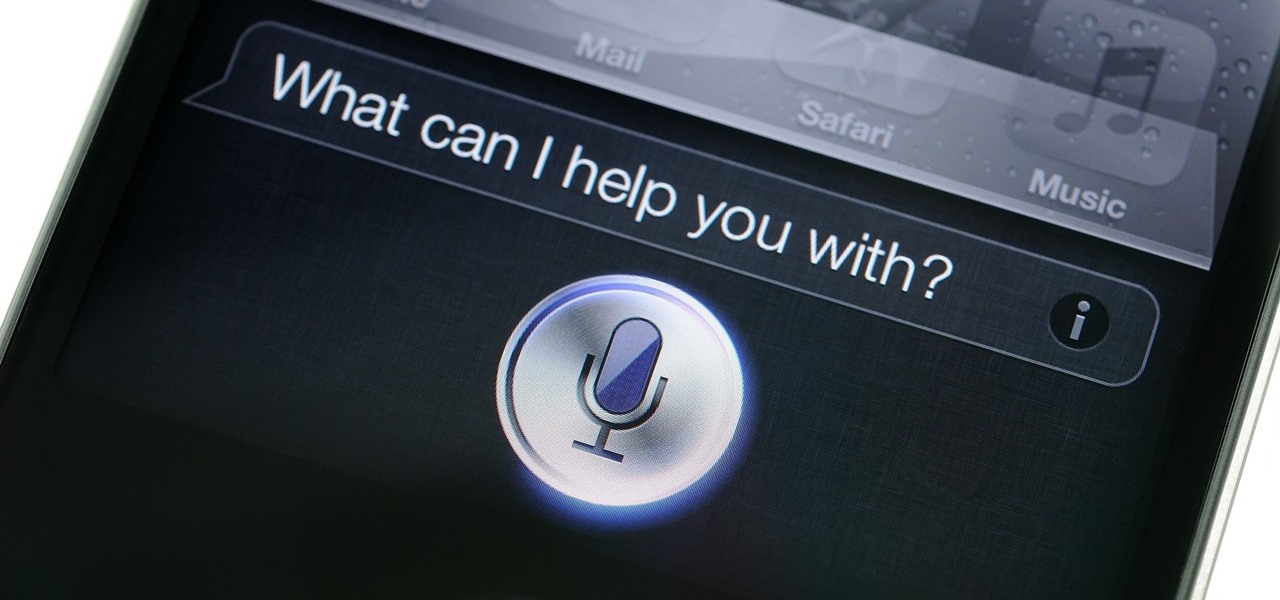
If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

The decadent, chewy, fresh-from-the-oven brownie is a classic American dessert. US History Scene states that the first brownies ever made were a result of socialite Bertha Potter Palmer's request of her chef at Chicago's Palmer House Hotel in 1893 "to create a dessert that could be tucked into a box lunch for ladies to eat while attending the Columbian Exposition."

Several Samsung phones have a feature that turns the screen black and white when the battery is getting low. This takes advantage of the AMOLED display in these devices, because unlike red, green, and blue pixels, no battery power is used to display black pixels on this type of screen.

Want to actually catch 'em all? Pokémon GO has long-teased the opportunity to hunt for Pokémon in the real world through augmented reality, but few have had the opportunity to actually see it in action.

Over the years, YouTube ads have become more and more integrated with the videos themselves, which means traditional Android ad blockers can no longer block the ads without blocking the videos. It's gotten to the point where the only ways to get rid of the ads are to either subscribe to Google Play Music and YouTube Red, or go through the complicated process of installing the Xposed Framework.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Greetings my fellow hackers.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?
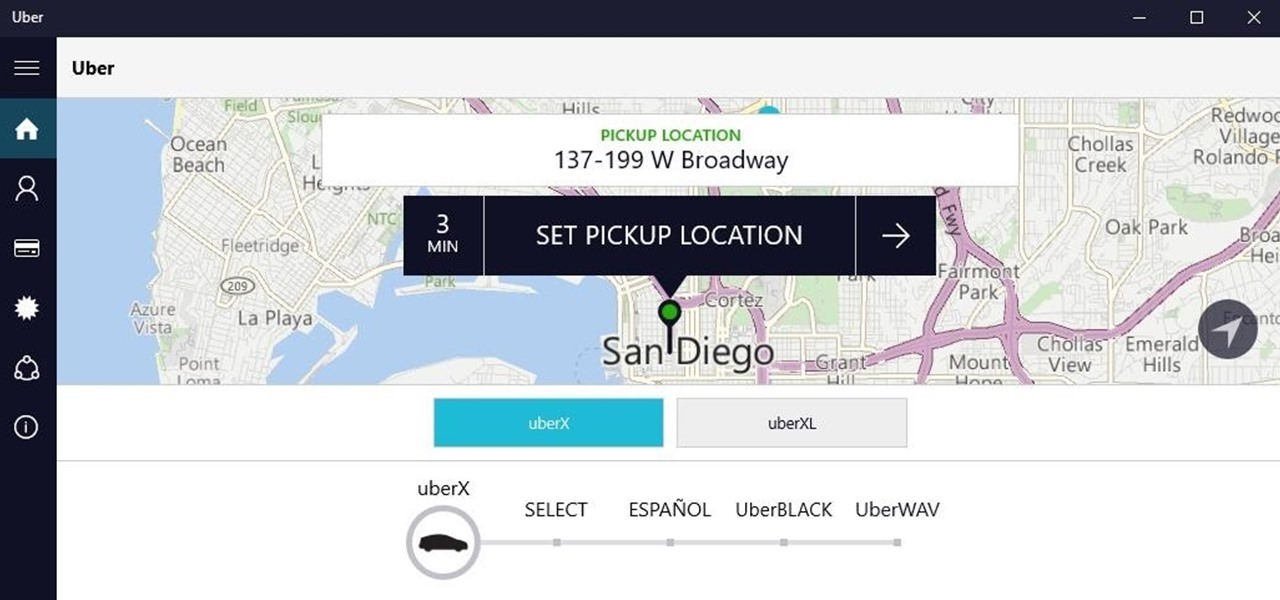
Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.

The notification light on phones and tablets is slowly disappearing. The once staple feature is now only found on a few devices, and a bevy of other notification systems have sought to fill the gap. The most popular of these systems is Ambient Display, which has grown in popularity with OEMs over the last couple of years; even Google's own Nexus line of phones have made the plunge.
Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

While the app switcher in iOS makes it easy to go from one open app to another fairly quickly, it's still not a great option if all you want to do is return to the previous app you were in.

SoundHound, the Shazam-like song-matching service, recently announced a new mobile app called Hound, which wants to be your one and only intelligent personal assistant.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

Video: . Project Overview
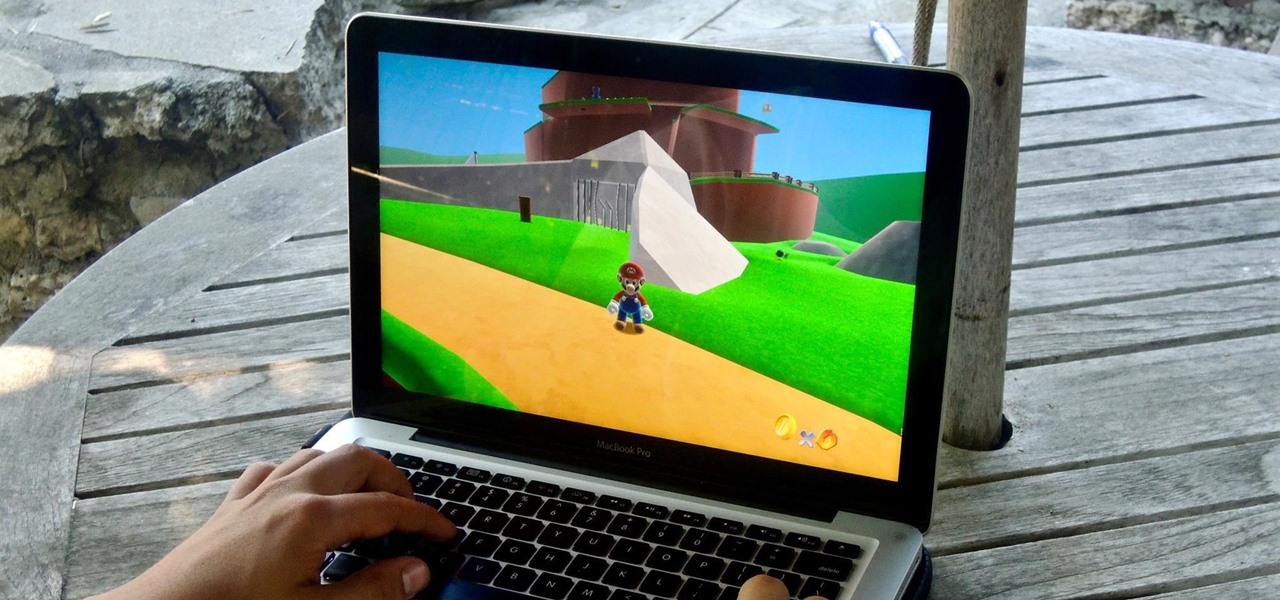
Yup, you read that right. As of now, you can actually play the first level of one of the most popular video games of all time—Super Mario 64—directly in your web browser.

The Google Now gesture included in the Google Now Launcher and on Nexus devices isn't something I regularly utilize, and you might not either. There is a way to disable it, which is a good idea if you were executing it accidentally, but what's even better than disabling it? Repurposing it!

If you've ever used a custom ROM on one of your devices, chances are it had a built-in feature that allowed you to kill any app by long-pressing the back button. This function comes in handy quite often, especially in situations where an app is acting up, since it stops all associated processes and clears the app from memory.
A new API in Android Lollipop allows apps to color the status bar to match their overall theme. Google billed this as a more immersive user experience that allows app developers to extend their color branding even further. It certainly seems like a win-win on the surface, but unfortunately, not many apps are using this feature yet.
Android Lollipop has an awesome feature called "Battery saver" mode that reduces power consumption through various tweaks in order to squeeze in an extra hour or two of standby time when your battery is running low. It does this by disabling background processes as well as location services and transition animations, so the phone is essentially running at half-throttle.
Looking back at my childhood in the '90s, I can't help but feel like I was deceived. Movies that took place in the "future," like in the year 2015, would showcase awesome technology. You know, self-driving or flying cars, hoverboards, and virtual displays controlled with hand gestures—so where are they?!

Using shortcuts to control the playback of your music on your computer makes life just a little bit easier. Instead of needing to open up an app, we've shown you how to use keyboard shortcuts, a Notification Center widget, and even Siri to control music on your Mac. Now we're going to show you how to use your iPad, iPhone, or iPod touch as a remote control.
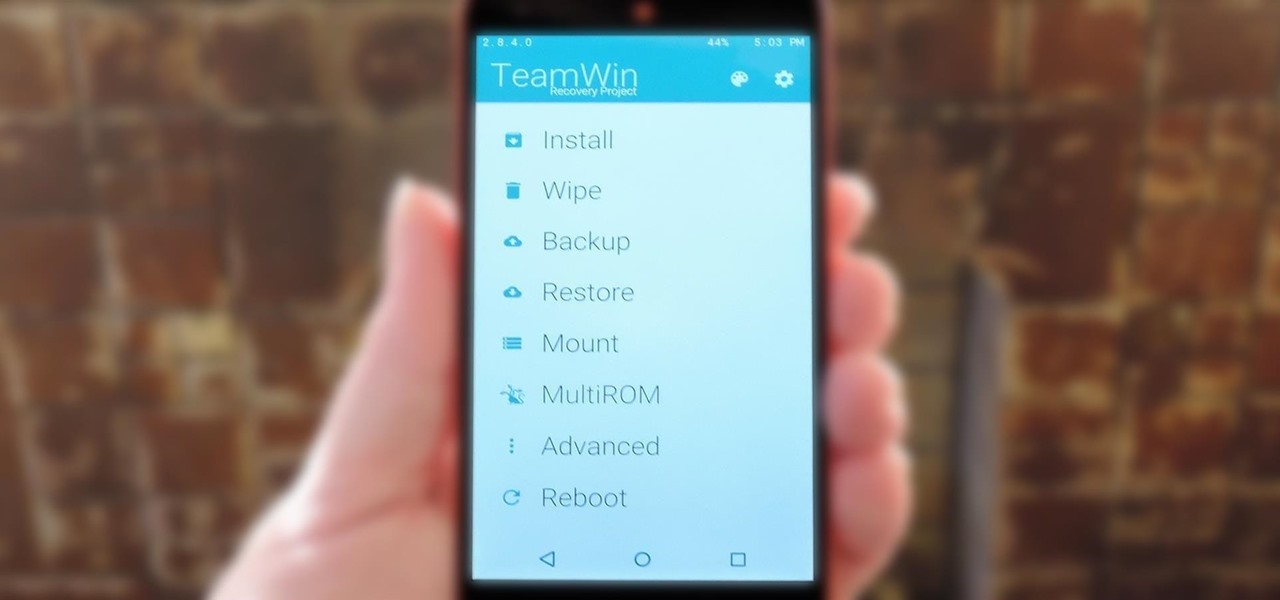
TWRP is hands-down the best custom recovery out there. Its interface, on the other hand, is... well, let's just call it utilitarian. The guys over at Team Win made sure that their product was robust, functional, and easy-to-use, but they didn't put a tremendous amount of effort into polishing the looks.