Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Edna shows us the basics of making buttercream frosting for professional, decorative cakes starting with the right ingredients. She uses a basic buttercream recipe, but makes sure that she does not over-mix the ingredients. She also explains how she used to use Crisco, but when the company changed its recipe to zero trans fat, she decided to started using real butter, which makes the frosting a lot less yellow. Additionally, use of Crisco, makes the frosting drier and much more crumbly. If yo...
In this tutorial, learn how to jailbreak your new iOS 4 on your iPhone or iPod. This jailbreak will let you take advantage of cool new features including the huge app superstore: Cydia. Enjoy!
Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

When it comes to the sub-$250 price range, the new Nokia 5.1 might be the perfect phone. Of all the new models announced at Nokia's event in Moscow, the Nokia 5.1 offers the most with the least compromises. For a third of the cost of a flagship, you get a phone with a premium build, solid specs, and good battery life.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

After two years of poor sales, LG decided to shake up its mobile division. New executives are at the helm, and changes to their flagship lineups are already underway. Specifically, the V series is expanding, as LG announced the second new device in the series, the LG V35 ThinQ.

HMD (the company currently making Nokia-branded phones) only released one flagship device last year, with the rest of the phones falling in the mid-range and entry-level tiers. However, at Mobile World Congress 2018, HMD announced their ambition to become a top five smartphone maker in 3–5 years. Meeting this goal will require penetration in all markets — especially the United States — and it looks like Nokia will get the ball rolling early this year.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

In this Arts & Crafts video tutorial you will learn how to use ICE Resin to make resin jewelry. ICE resin should be used in a well ventilated room and be sure to follow manufacturer's recommendations. The kit comes with mixing cups and sticks. Additionally you will need a paint brush, scissors, sponge and needles. Once you mix the resin and the hardener, you got to use it within 30 minutes. Curing time is 24 hours at 72 degrees Fahrenheit, which is the room temperature. You can make it faster...

In this video Krazyboy shares his method of creating a spiritual bath. Krazyboy suggests that while spiritual baths are often known to help cleanse the soul, you can also imbue it with an intent (such as love, luck, success). The idea behind a spiritual bath is cleansing and white. A nice feature of spiritual baths is being able to customize it, including ingredients that feel right to you. To begin, fill a large bowl about half way with holy water/new moon water/spring water. Next, add a cou...

This tutorial from Pink Ink shows you how to automate batch processes in Photoshop using actions.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Huawei's push into the US market has by no means stopped, even despite the recent US government pushback. Huawei has already released their top-notch flagship device from 2017, the Mate 10 Pro, and a couple great budget and midrange devices. Their latest release offers an upgrade to a past release.

Samsung and Apple are the two titans of the mobile phone industry. After Apple deployed the iPhone X in November, Samsung had three months to brood until Mobile World Congress, where they unveiled the Galaxy S9. Now that both phones are out, it's time to put them head-to-head.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

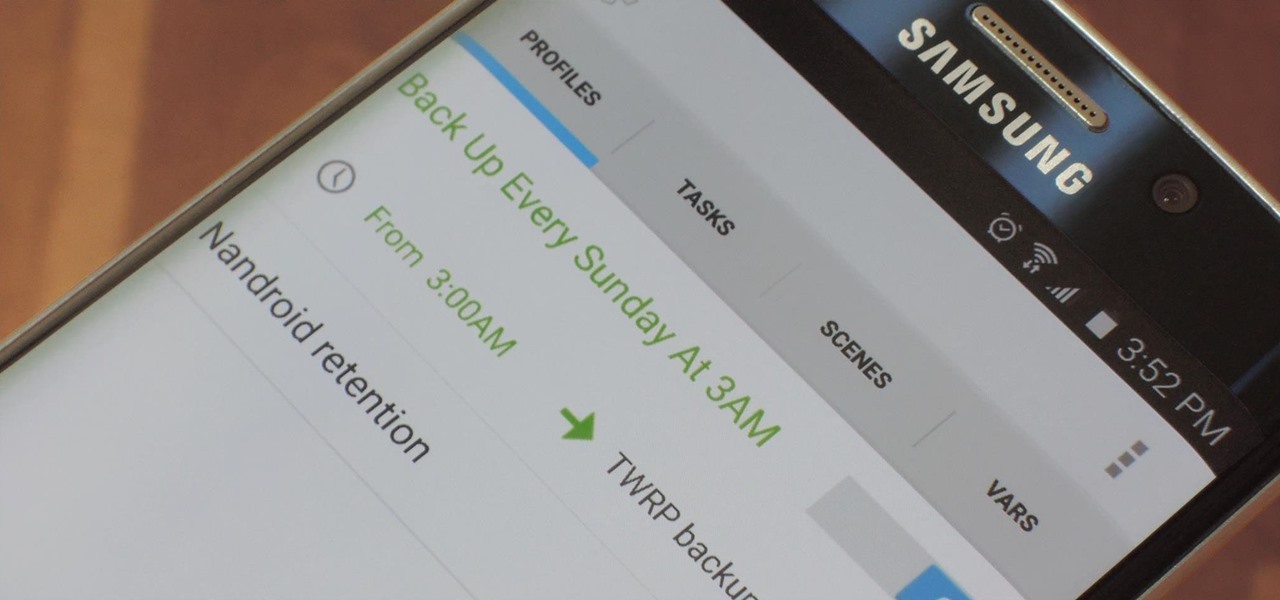
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

The standard way to make pasta requires a lot of water, and it takes a long time for that big pot of water to actually start boiling. For these reasons, as well as my hatred for washing large pots, I don't cook pasta at home very often—at least not the traditional way.

Keeping your OnePlus One running smoothly can be taxing, especially if you spend most of your day looking for ways to tweak performance settings like me. Sometimes I get lucky and end up with a faster phone, but because I experiment so much, I often end up restoring it back to stock. This process can get old really quick, but when I started using the Bacon Root Toolkit from WugFresh, it became exponentially easier.

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

Whether you're a celebrity or someone with something to hide, Facebook allows you to keep your "friends list" private so you can protect the identities of your Facebook friends. But it only kind of protects them.

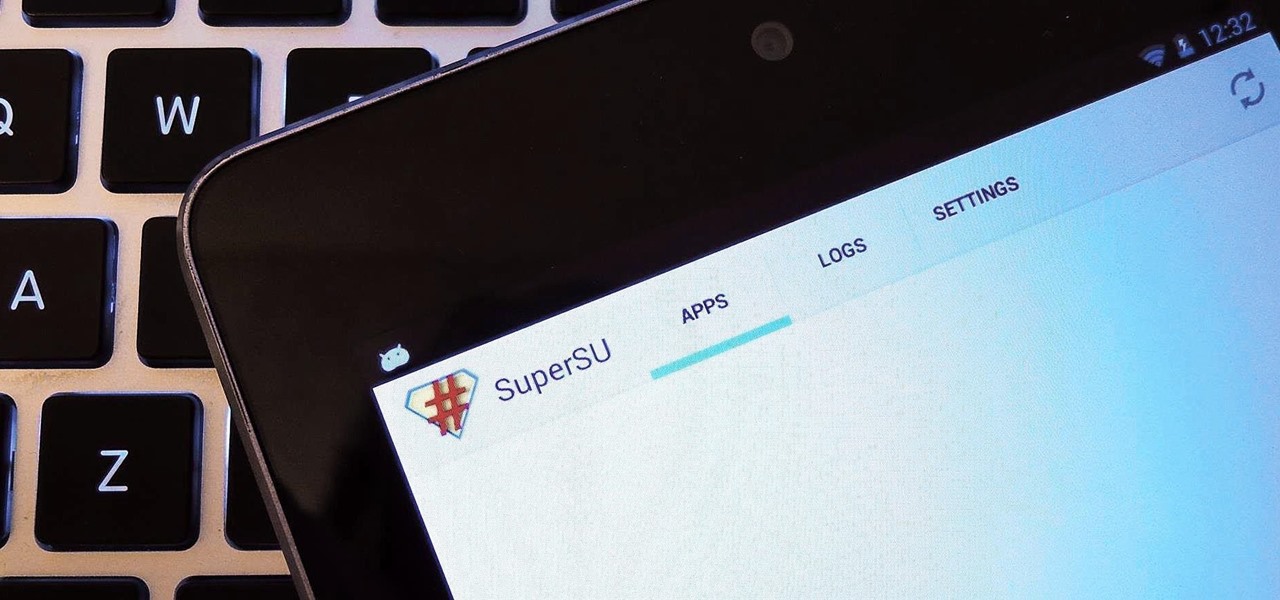
The new Jelly Bean is out in the wild, but if you've installed Android 4.3 from stock, you'll notice rooting is now not possible. If you miss the ad-blocking capabilities of AdBlock Plus, how Seeder made apps snappier, or the convenience of backing up with Titanium Backup, you'll need to get rooted.

Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.

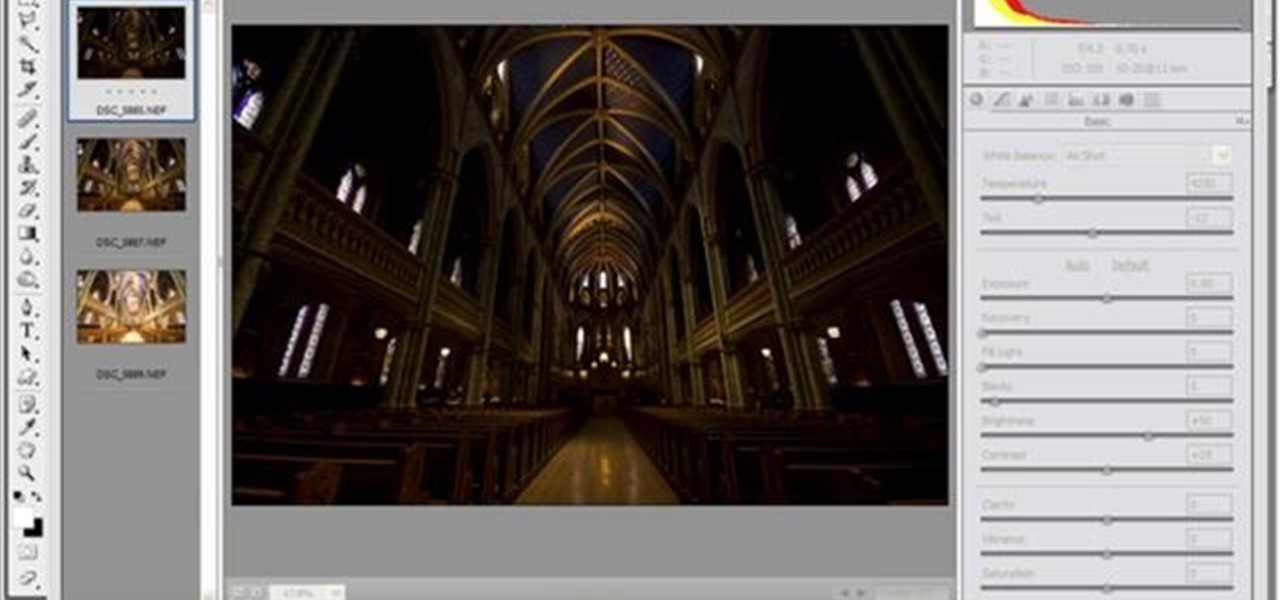
Yanick's Photo School demonstrates how to use Photoshop to make HDR images in Photoshop CS3. This tutorial first explains that HDR means "High Dynamic Range" which is a process to get details from a photo from both the highlights and shadows of a particular scene. The first thing that is necessary is to take multiple views of the same image with different exposures. To start off, you will take three exposures: one that is two stops down, one that is normal exposure, and one that is two stops ...

BD Quikheel Safety Lancet The BD Quikheel Lancet is a safety-engineered product designed for heel sticks on infants and premature babies. It features a sweeping surgical blade that permanently retracts after creating an incision. Additionally, it offers a tapered window providing the healthcare worker with the ability to accurately position the lancet.

In recent days we've covered the marriage of augmented reality and top-tier music artists. This time, though, the music stars are showing off the tech rather than integrating it into their act.

Samsung's Android Pie update — known as One UI — is bringing major changes to the Galaxy S8, Galaxy S9, and Galaxy Note 9. The main interface has received a visual overhaul, and this is no more evident than it is with notifications.

Microsoft has informed HoloLens users that the company will begin rolling out a mandatory update for HoloLens as part of its Windows 10 October 2018 release that brings a number of new features and quality-of-life improvements to the headset.

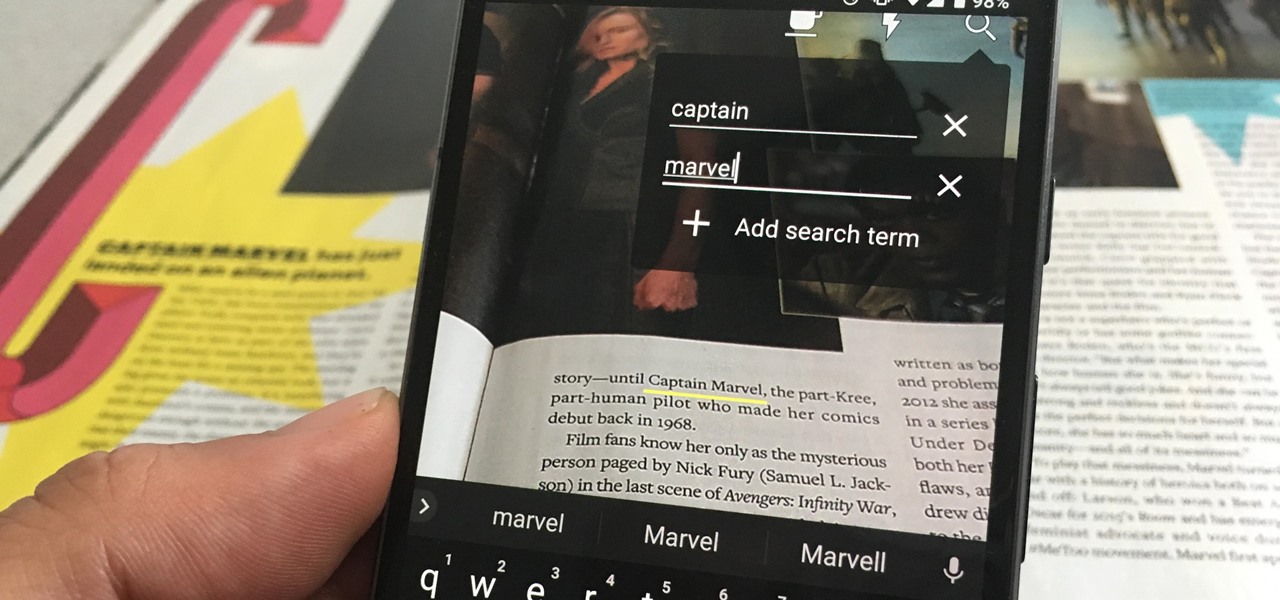
One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

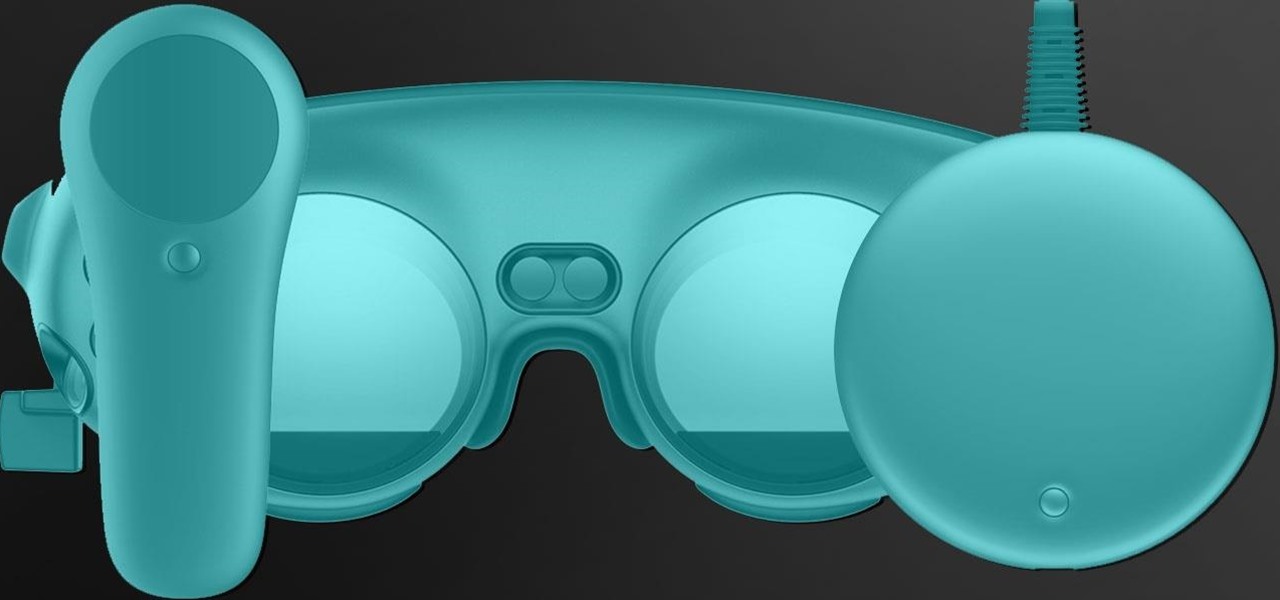
Last week, Magic Leap gave us an additional peek at its Lumin OS and more tutorials that show how its device works with virtual content. But details about the hardware wasn't included in the array of new information.

Hip-hop artist Drake once rapped that "goin' online...ain't part of (his) day," but that's not stopping him from promoting his new double album, Scorpion, via augmented reality on Snapchat.

It looks like the Huawei P20 has moved from rumor to all but confirmed. Thanks to a series of YouTube videos released by Huawei Mobile Netherlands, we now have a few confirmations about the latest entries in the flagship series.