Linking your social networking activity together has never been so easy. Randy Ksar shows us the simple process of linking your Facebook and Flickr accountstogether so you and your friends can view your them both easily without navigating from site to site. First, you should log into your Facebook page click on Profile, select settings and you should see Activity. All you need to do is simply click on the Flickr link and type your Flickr user account name and you're done. Note that your Flick...
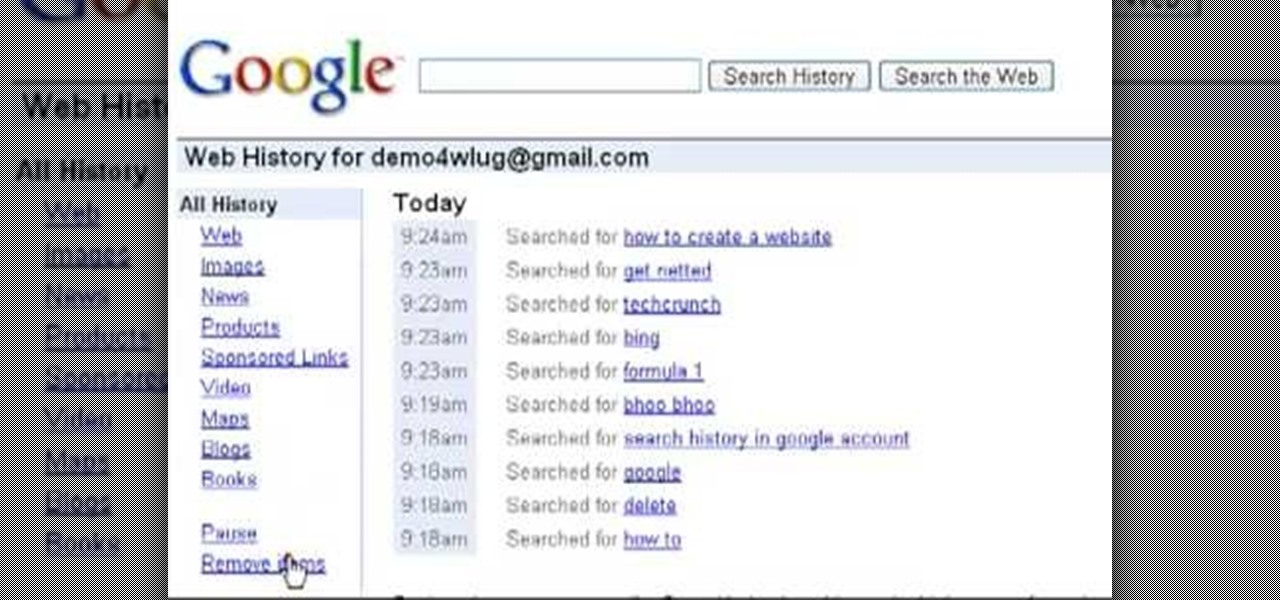
Want to clear the search history from your Google account? Well follow these simple instructions and return your history to the original settings! First log into your Google History Account at google.com/history. Next scroll down and locate "Remove Items" on the left hand side tool bar. Click on this. Next locate "Clear entire Web History" towards the top right of the screen. Then the final step is to click "Clear History". Follow through the tutorial video to get rid of all of the annoying s...

In this video tutorial you will see how to Pandora a PSP slim battery. You will need a knife for this. When the normal battery is in the PSP, when you switch it on, it will log on just normal. Now remove the battery, put the knife in the joint of the battery case and move it up and down and slit open the case. Then pry it open and remove one half of the case. Then flip open the flap on the battery and cut off one connection on the battery as demonstrated in the video. Now put the battery back...

Is there anyone on your list of Facebook friends that you no longer wish to have access to your profile? This concise video shows how to remove "friend" statuses from unwanted Facebook friends. First, you must log into your Facebook profile. Near the top of the opening page you will see a tab called "friends". Click on it, then click on "all connections". This page will list all of the people that you are currently friends with. On the left is each person's profile picture and name, and on th...

JamesKesn teaches you how to hack a vending machine. You must use a very specific machine and an exact combination of button presses. For this it is: far left Pepsi, near right Mountain Dew, near left Pepsi, far right Mountain Dew. Then far left Pepsi, near right Mountain Dew. Again, far left Pepsi, near left Pepsi, near right Mountain Dew and far right Mountain Dew. This hack will allow you to see the stats, set the price and see error logs.
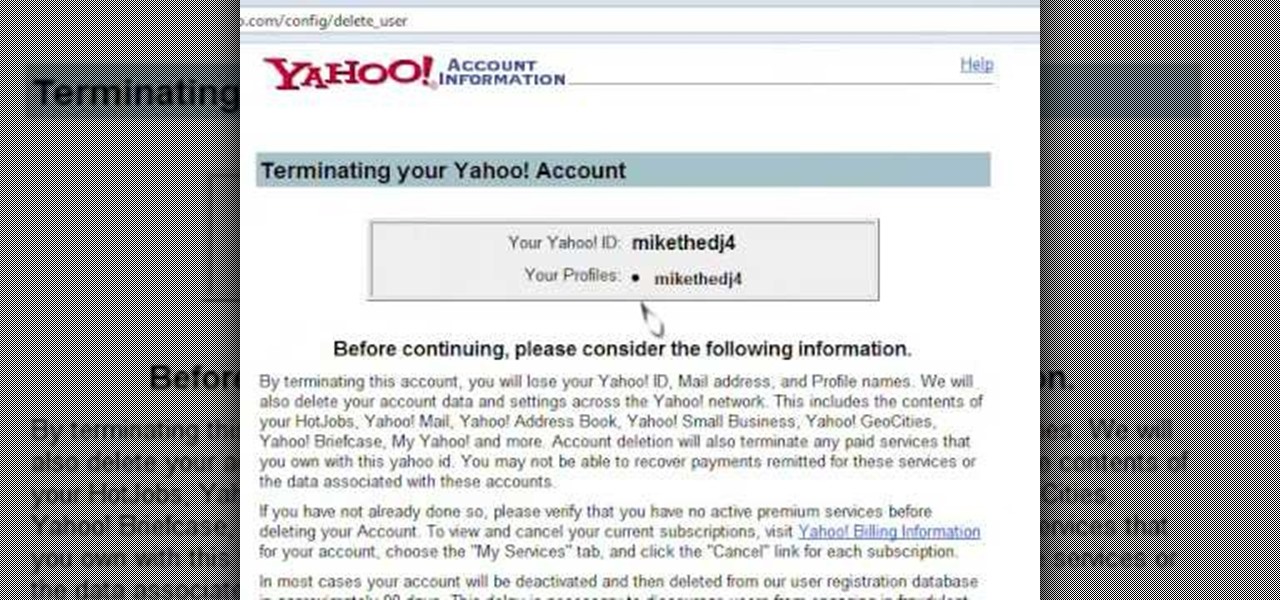
Learn how to delete your old Yahoo or Yahoo mail account in simple steps. First open your web browser and enter the web address for Yahoo to open it. Now log into your account using your Yahoo username and password. Go the account termination page, confirm your account termination and enter code give. Finally press 'Yes' and enter your password . Now your Yahoo or Yahoo mail account will be deleted.

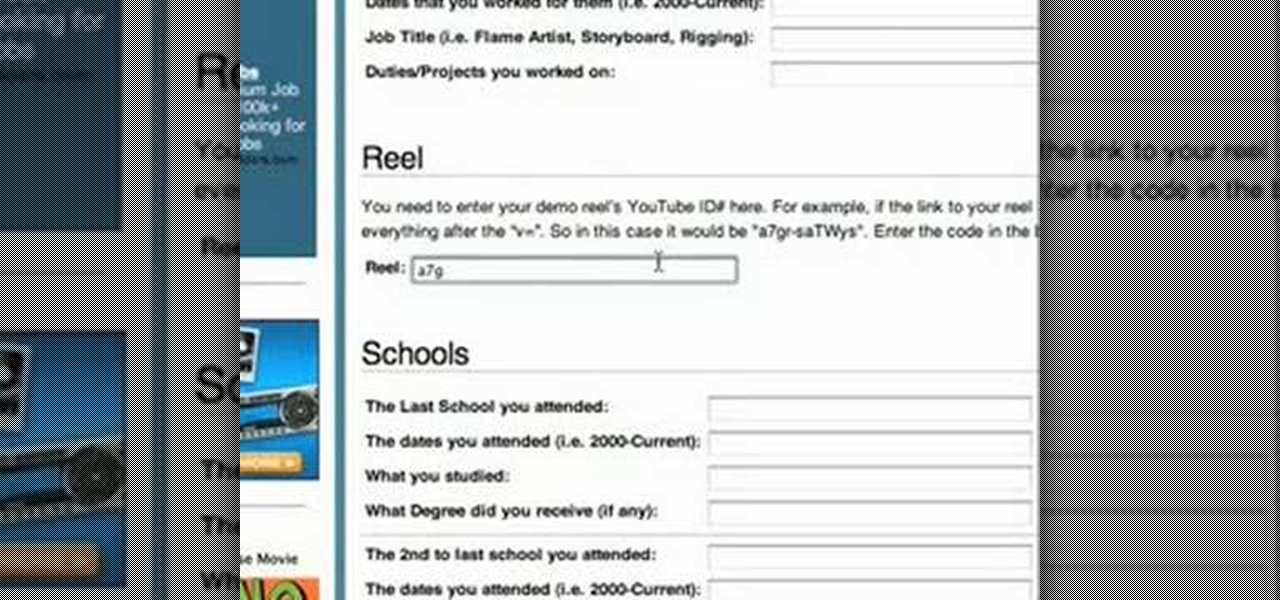
This video teaches the simple steps to make an animation resume at Ani-Jobs. An excellent summary is given below. First click on the Resume cafe tab on the top menu, log in or create an account if you don't have one. Select a suitable category like 2d Artist, click the Storyboard sub-category. Add your name to enter the resume building page and start to input your details. In the reel column give the number that comes after "v e" in the link. Upload your résumé, artwork and your comments, lea...

How to hack Yoville! Yoville cheats, tricks, hacks. Yoville is a game that can be played on Facebook or MySpace. In the words of Yoville's Facebook app, YoVille is a world where you can buy new clothes for your player, purchase items for your apartment, go to work, and meet new friends. Yoville is a city building simulation game.

In this video series, our expert will take another look at the traditional yule log cake, and make yule log cookies. Learn how to cream the butter, add the sugar, flour and wet ingredients for the Yule Log cookie dough.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Huawei's push into the US market has by no means stopped, even despite the recent US government pushback. Huawei has already released their top-notch flagship device from 2017, the Mate 10 Pro, and a couple great budget and midrange devices. Their latest release offers an upgrade to a past release.

After two years of poor sales, LG decided to shake up its mobile division. New executives are at the helm, and changes to their flagship lineups are already underway. Specifically, the V series is expanding, as LG announced the second new device in the series, the LG V35 ThinQ.

Samsung and Apple are the two titans of the mobile phone industry. After Apple deployed the iPhone X in November, Samsung had three months to brood until Mobile World Congress, where they unveiled the Galaxy S9. Now that both phones are out, it's time to put them head-to-head.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

The standard way to make pasta requires a lot of water, and it takes a long time for that big pot of water to actually start boiling. For these reasons, as well as my hatred for washing large pots, I don't cook pasta at home very often—at least not the traditional way.

Bad news first: It's not out yet, but it's coming really soon. The premise for the game is this:

We recently showed you the Misfit Shine, a no-charge, app-oriented fitness tracker that you can grab for a hundred bucks. Sony has also decided to get in on the action with their Smartband SWR10—but this thing is so much more than a fitness tracker...the Smartband wants to "log your day, every day".

In this Arts & Crafts video tutorial you will learn how to use ICE Resin to make resin jewelry. ICE resin should be used in a well ventilated room and be sure to follow manufacturer's recommendations. The kit comes with mixing cups and sticks. Additionally you will need a paint brush, scissors, sponge and needles. Once you mix the resin and the hardener, you got to use it within 30 minutes. Curing time is 24 hours at 72 degrees Fahrenheit, which is the room temperature. You can make it faster...

In this video Krazyboy shares his method of creating a spiritual bath. Krazyboy suggests that while spiritual baths are often known to help cleanse the soul, you can also imbue it with an intent (such as love, luck, success). The idea behind a spiritual bath is cleansing and white. A nice feature of spiritual baths is being able to customize it, including ingredients that feel right to you. To begin, fill a large bowl about half way with holy water/new moon water/spring water. Next, add a cou...

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

Stop throwing out the rolls when the paper towels are gone. There are dozens of good uses for them. You Will Need

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

If you have devices that run different operating systems, you know how frustrating it is that Apple's Calendar app isn't available on other platforms. If you use Siri to quickly create an event on your iPhone or Mac, you're not going to see that event on your PC or Android tablet unless you sync your calendar to another service.

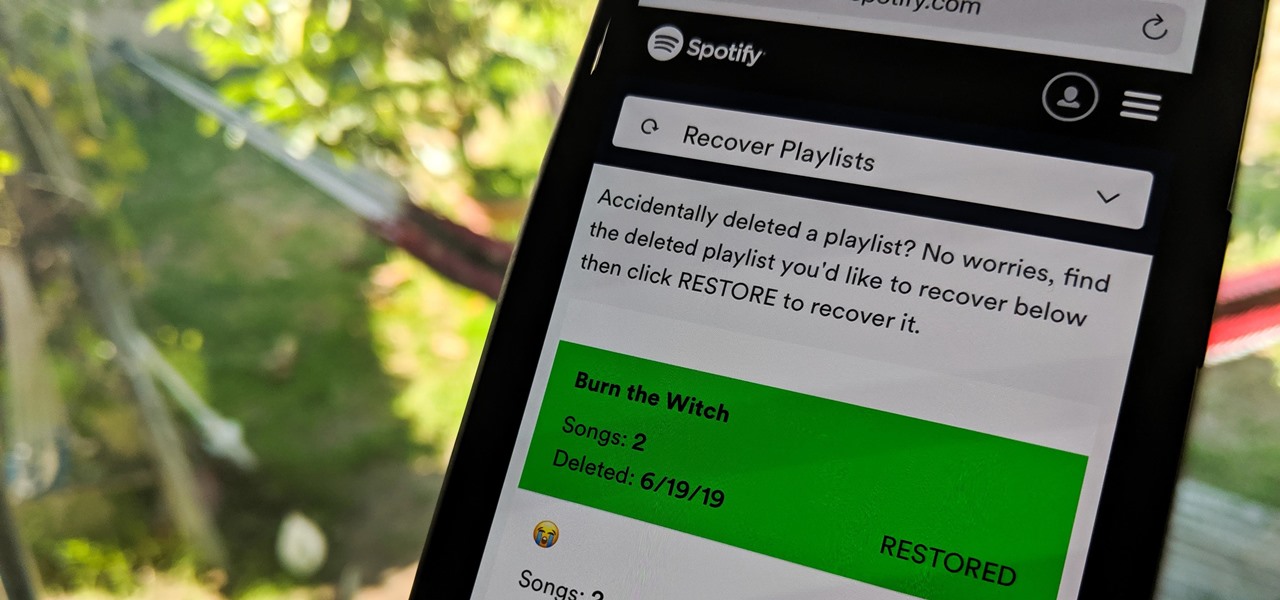
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

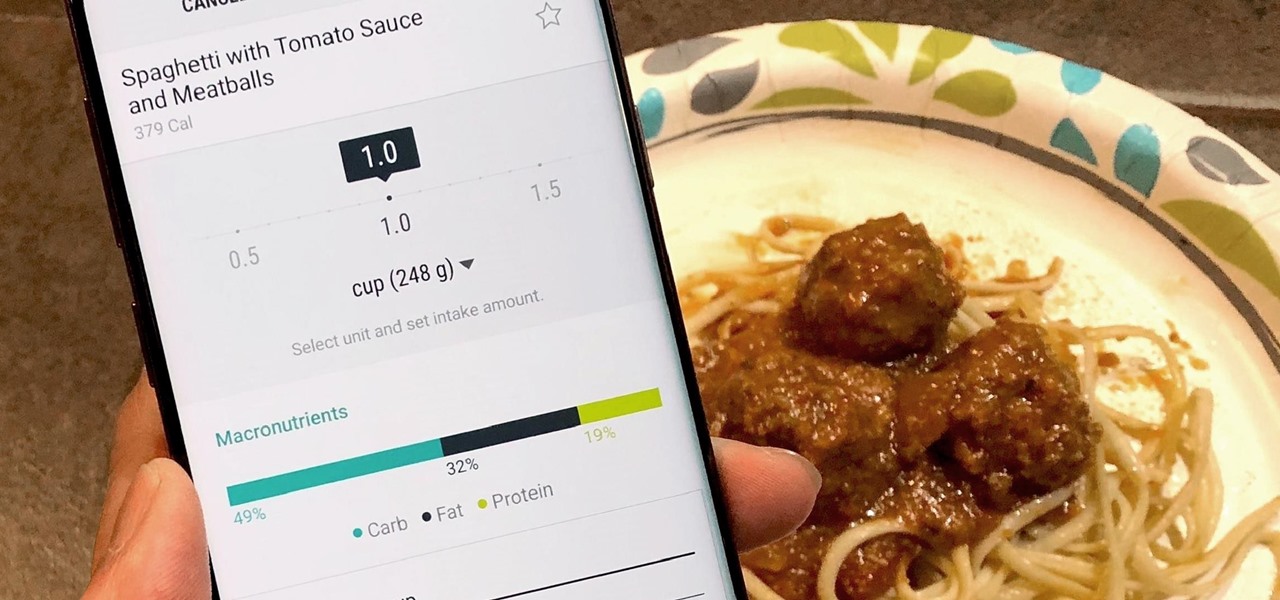
The most essential part of a healthy lifestyle is managing your diet — after all, what would be the point of a daily workout regimen if you were eating junk food? Thankfully, Samsung Health makes it easy to record your calorie and nutrient intake to get a clear picture of your dietary habits and how you can make them better.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

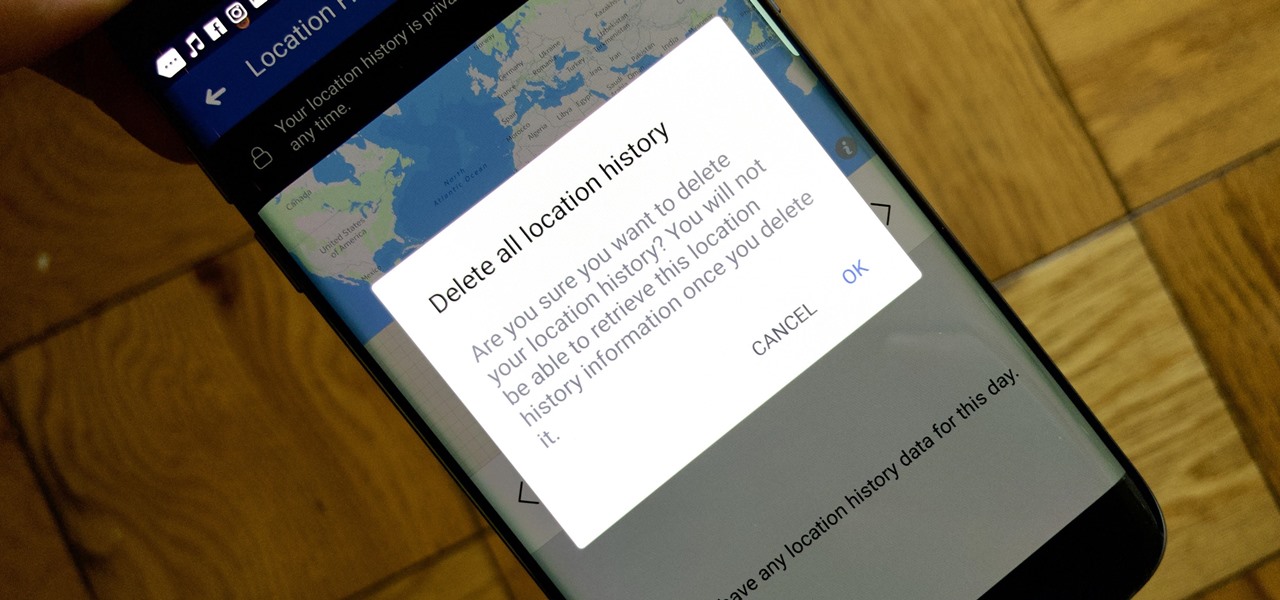
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.

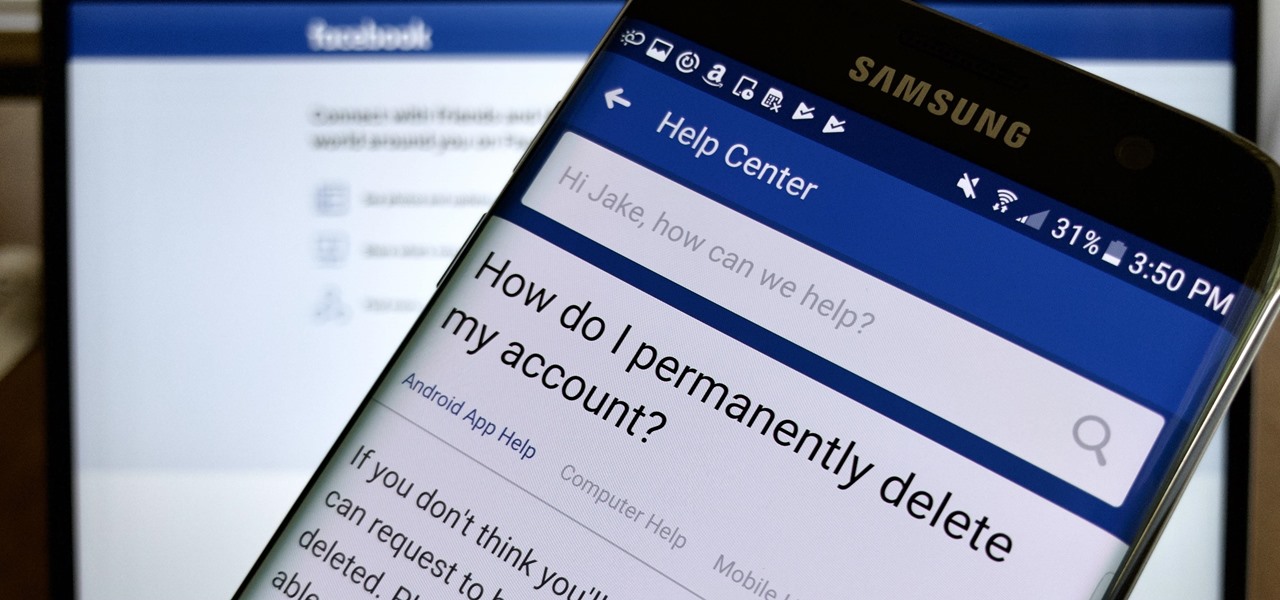
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account is actually a quick affair. You just need to know where to look.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

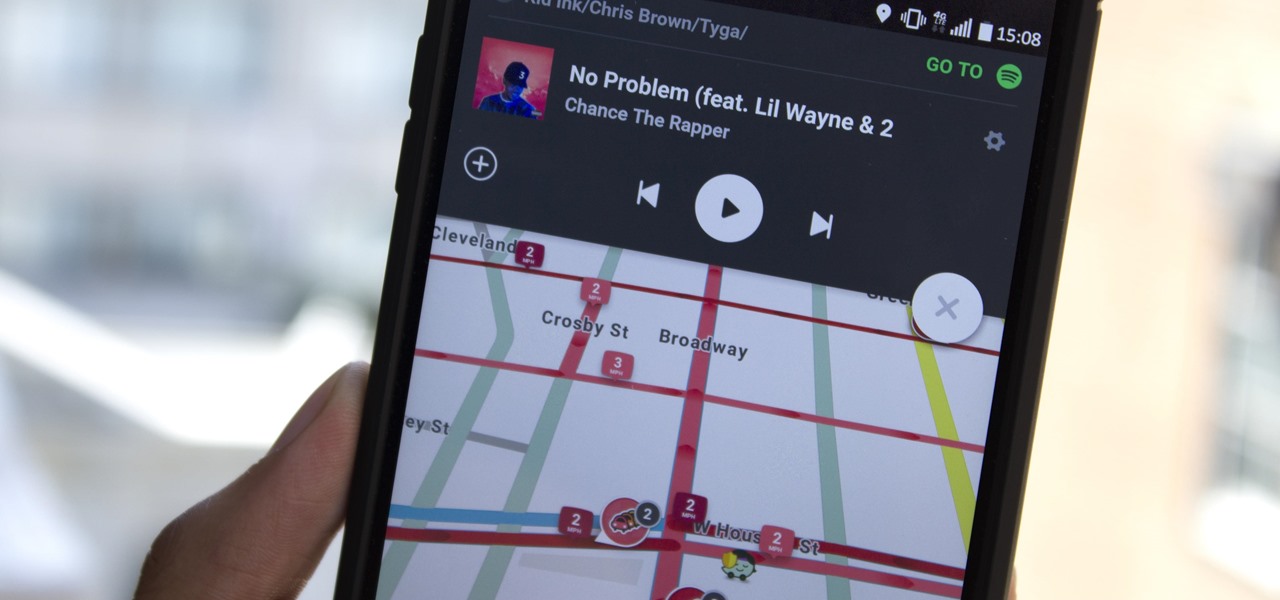
Who doesn't love listening to music or playlists when driving? The open road and an awesome playlist make for a perfect pairing, but it can become quite the challenge if you're trying to navigate at the same time. That's why Waze's built-in audio controls for compatible apps like Spotify and Pandora are so useful, so you can always keep your eyes on the map and road ahead of you.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.