A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

At any moment, you can open up Meerkat and start live-streaming a video from your smartphone, available for anyone to watch. Thanks to its popularity at SXSW and the backing of several big Hollywood players, the app just announced that it's receiving $14 million in funding.

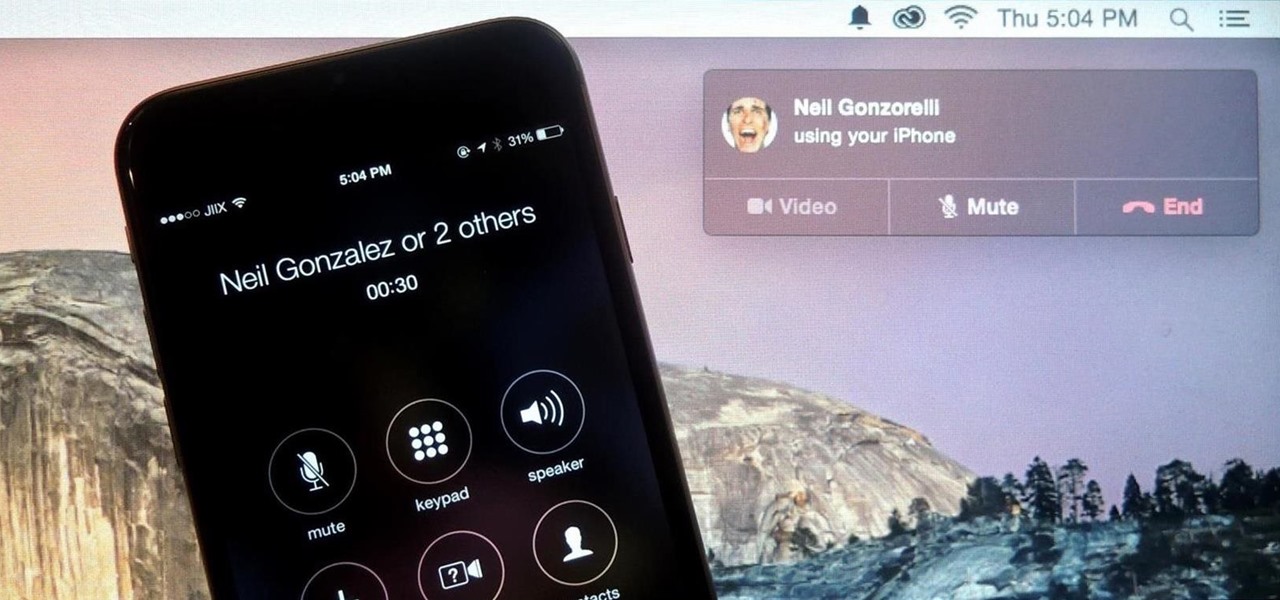
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

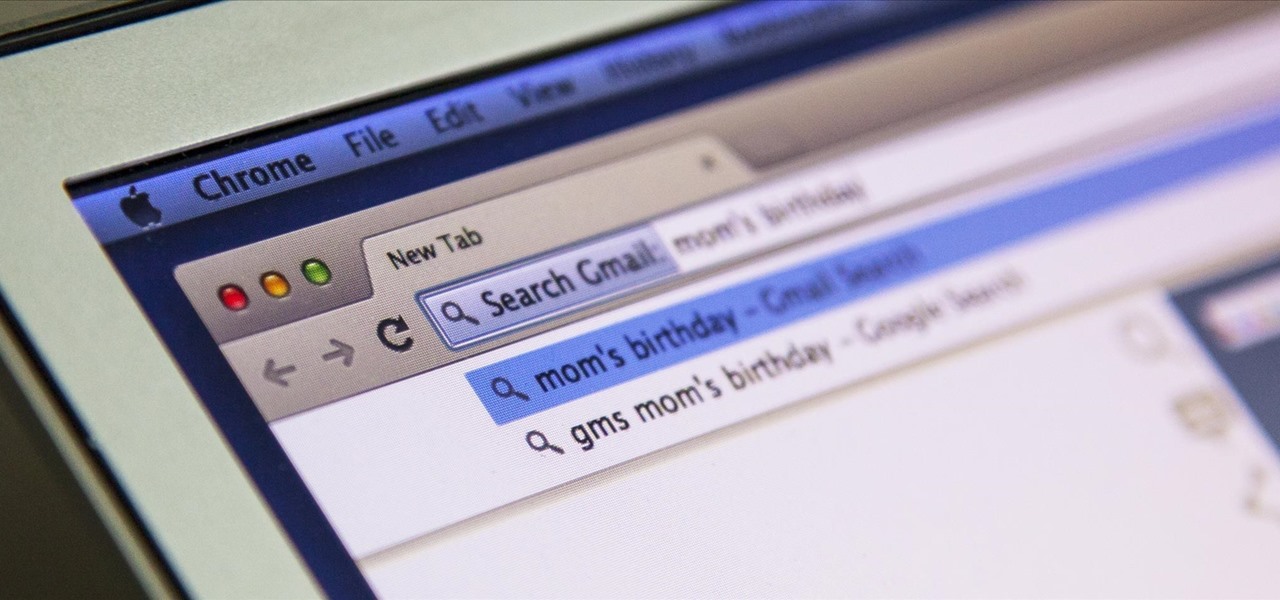
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

BD Quikheel Safety Lancet The BD Quikheel Lancet is a safety-engineered product designed for heel sticks on infants and premature babies. It features a sweeping surgical blade that permanently retracts after creating an incision. Additionally, it offers a tapered window providing the healthcare worker with the ability to accurately position the lancet.

A side effect of the COVID-19 pandemic is that small businesses are suffering from forced closures and social distancing, but game developer Niantic has a solution.

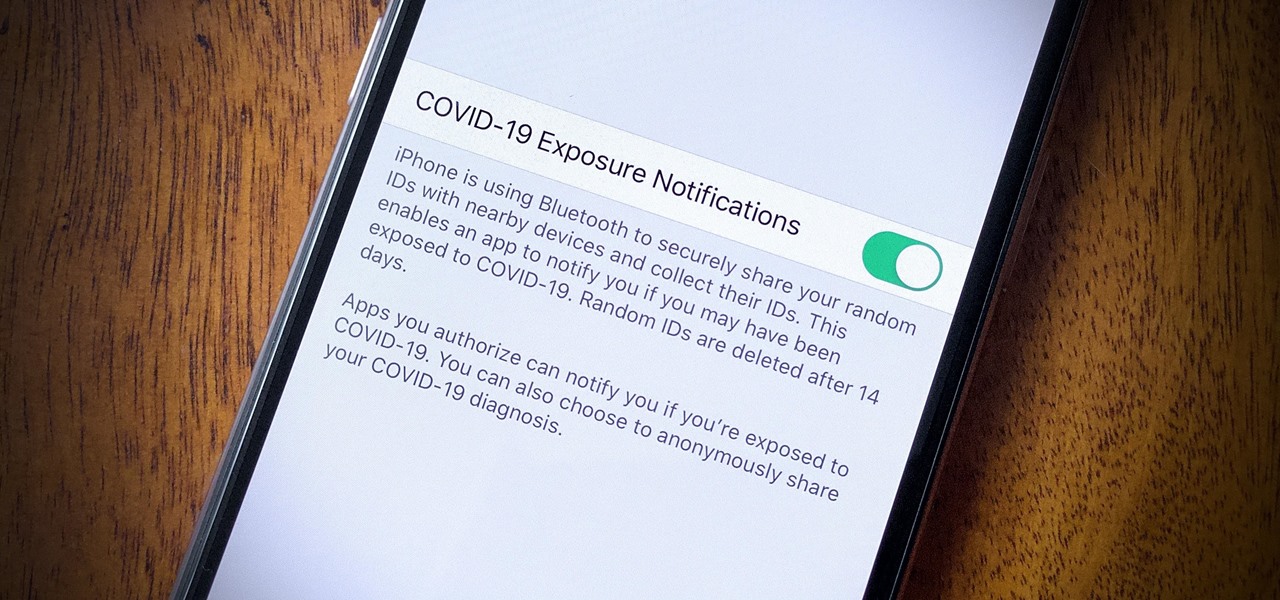
In iOS 13.5 and later, developers can create and release contact tracing apps for iPhone, which could help slow the spread of the novel coronavirus in the U.S. With these apps comes COVID-19 exposure notifications, which you may or may not want to receive. If you don't want to get these alerts, you can disable them.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

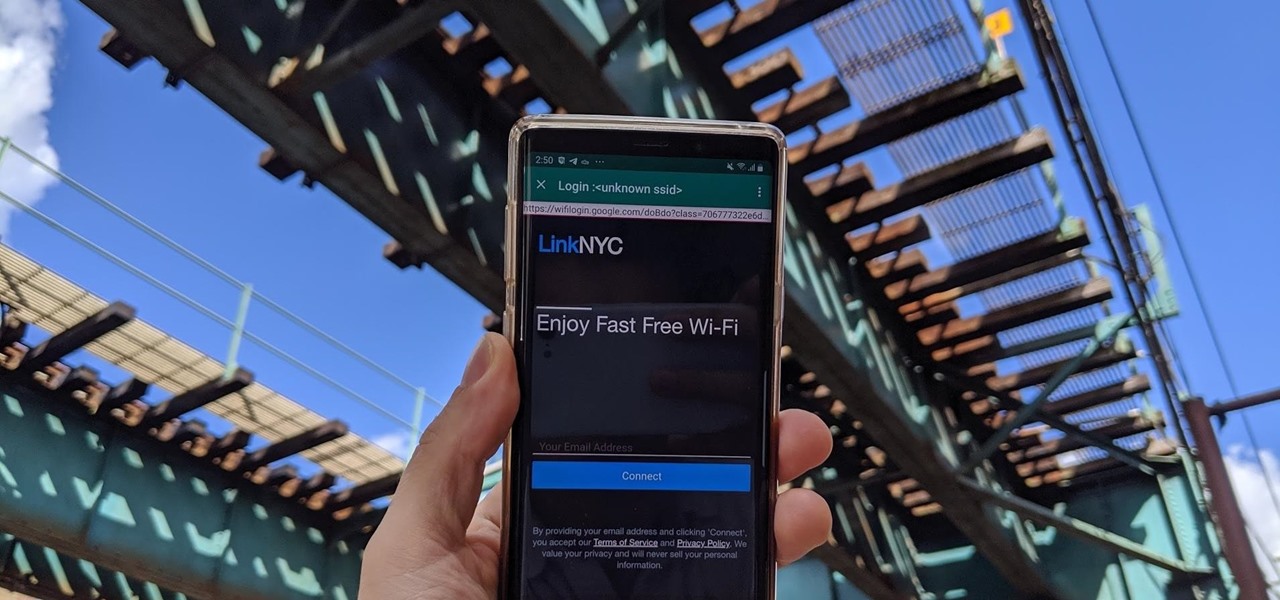
Public Wi-Fi networks that have a captive portal sign-in screen can sometimes be broken on Android. This seems to happen randomly and on some devices more than others. You'll get the "Sign into Wi-Fi network" notification, but it just doesn't work. If that's happening to you, you'll be glad to know an app can help fix the issue.

In recent days we've covered the marriage of augmented reality and top-tier music artists. This time, though, the music stars are showing off the tech rather than integrating it into their act.

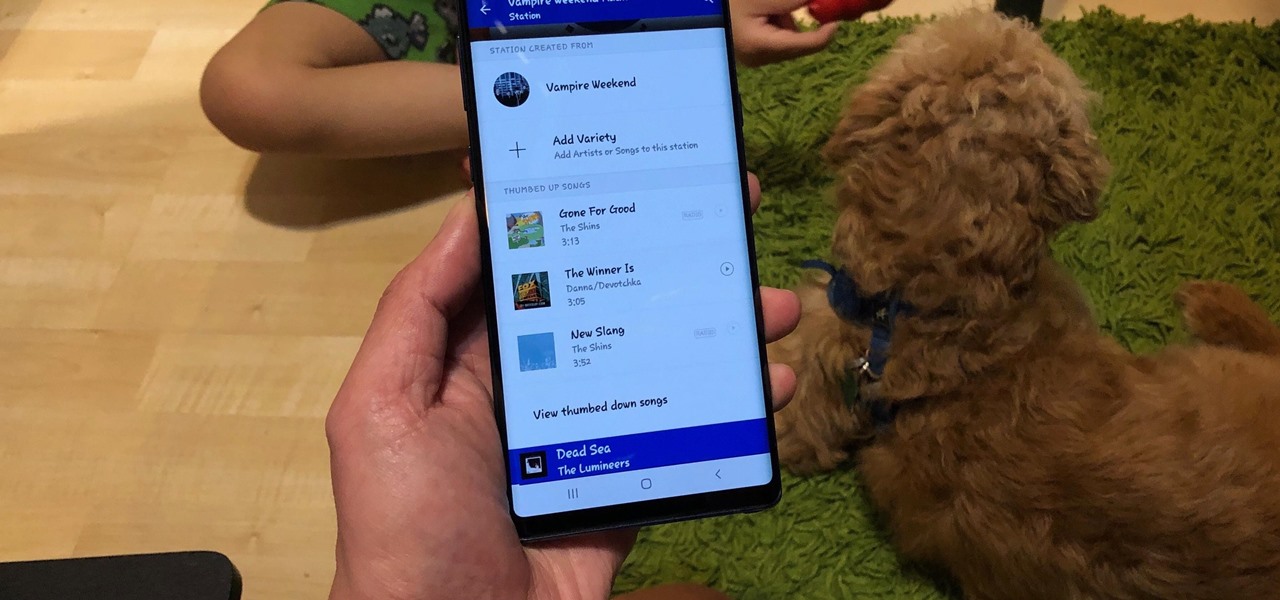
Pandora has a simple rating system that works by hitting either the thumbs-up or thumbs-down icon on a track that's playing on your station. If you choose the former, the song you like along with others similar to it will play with more frequency, while selecting the latter will prevent that song and others like it from playing in your station moving forward.

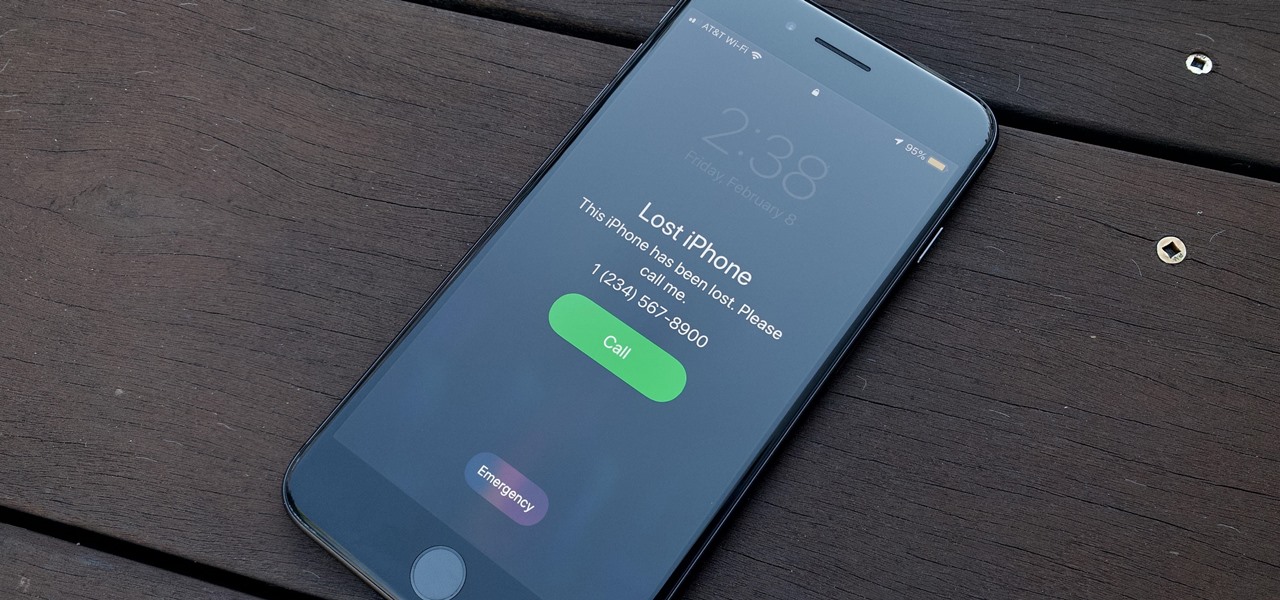
So, you're on the way back from a restaurant and realize you left your iPhone there, but you're late for a meeting and can't go back yet. You may as well kiss that iPhone goodbye, right? Not yet, as long as the right person gets their hands on it first. But that potential do-gooder won't know to contact you, and that's where Find My iPhone's "Lost Mode" comes in handy.

Samsung's Android Pie update — known as One UI — is bringing major changes to the Galaxy S8, Galaxy S9, and Galaxy Note 9. The main interface has received a visual overhaul, and this is no more evident than it is with notifications.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

Microsoft has informed HoloLens users that the company will begin rolling out a mandatory update for HoloLens as part of its Windows 10 October 2018 release that brings a number of new features and quality-of-life improvements to the headset.

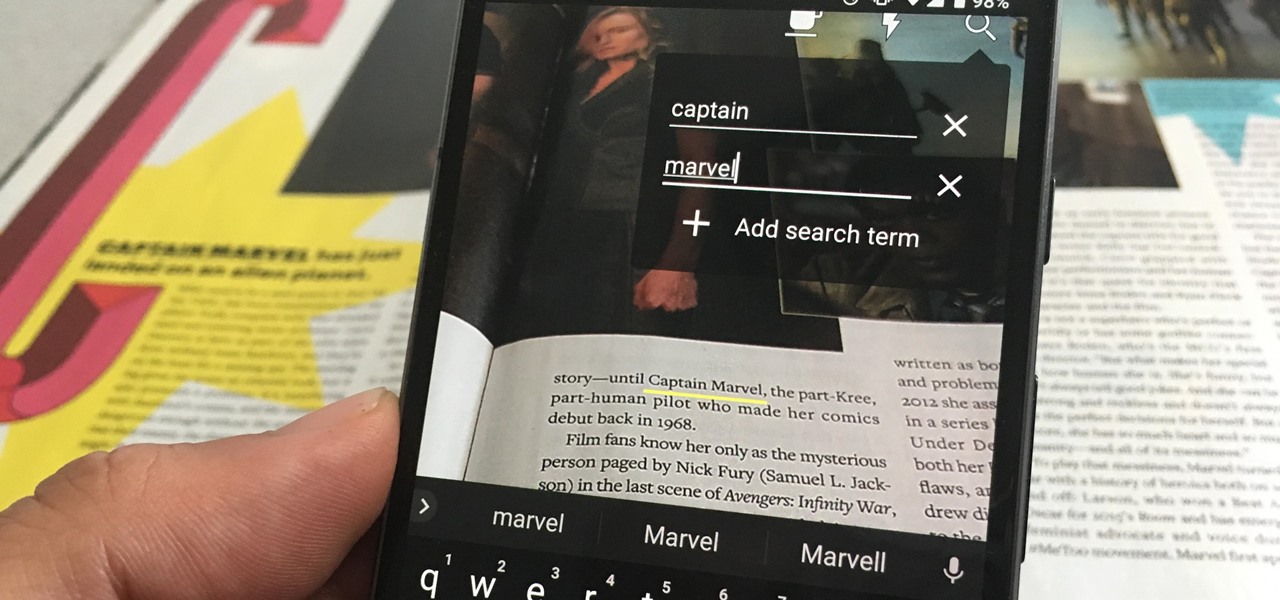
One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

With iOS 12, Apple is offering users more options than ever to create, store, and manage their saved passwords. Not only can iOS 12 make you new passwords via the AutoFill feature, you can quickly and efficiently access your entire iCloud Keychain using Siri. Why go hunting for the passwords yourself when you can ask your iOS assistant to find them for you?

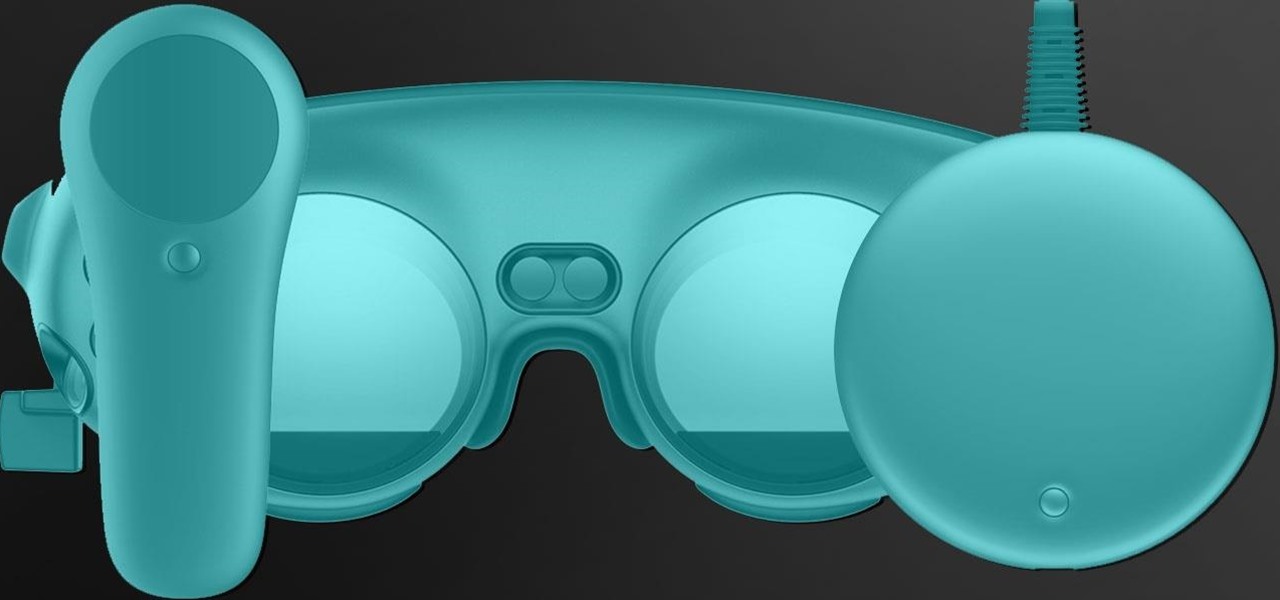
Last week, Magic Leap gave us an additional peek at its Lumin OS and more tutorials that show how its device works with virtual content. But details about the hardware wasn't included in the array of new information.

Hip-hop artist Drake once rapped that "goin' online...ain't part of (his) day," but that's not stopping him from promoting his new double album, Scorpion, via augmented reality on Snapchat.

Hearthstone, Blizzard's online card game, combines strategy with a fun spin on the World of Warcraft lore to create a unique experience. With the latest expansion (The Witchwood) on the horizon, you'll want to make sure your collection is ready for when the set drops in April. Fortunately, you can get free packs on iPhone or Android to help prepare.

It looks like the Huawei P20 has moved from rumor to all but confirmed. Thanks to a series of YouTube videos released by Huawei Mobile Netherlands, we now have a few confirmations about the latest entries in the flagship series.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Move over, Hype Williams, it looks like Snapchat is about to take some of your music video-making business, and pop rock group Maroon 5 is the proof.

One of the most highly-cited drawbacks to the HoloLens is its limited field of view (FOV), but now it appears that Microsoft has solved that problem.

The leaks and rumors surrounding the highly anticipated Galaxy Note 8 just keep coming. But none have suggested that the new Samsung phone might be powered by a different chipset than the Snapdragon 835, until now.

Single and living in NYC? Forget bars, the female-empowered dating app, Bumble, has just opened a place where you can meet up with your online lovers.

Apple made headlines last month when it announced it would acquire the popular application Workflow. Now, the company should be making waves again with the news that they will reimburse customers who purchased the app.

According to the National Safety Federation (NSF), pet bowls and toys carry coliform bacteria, including Staph bacteria, yeast, and mold. Additionally, an (unscientific) survey from Petco found that almost one-third of pet owners do not know the extent of contamination that their pet toys contain.

A bacterium which triggers respiratory disease has been detected in the water systems of two Pennsylvania nursing facilities.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Jurassic Park makes a great (and sometimes mediocre) action movie, but hopefully isn't the sort of thing we're dumb enough to actually make. Fortunately, on the HoloLens, you can now walk with the dinosaurs with no risk to your life and limbs.

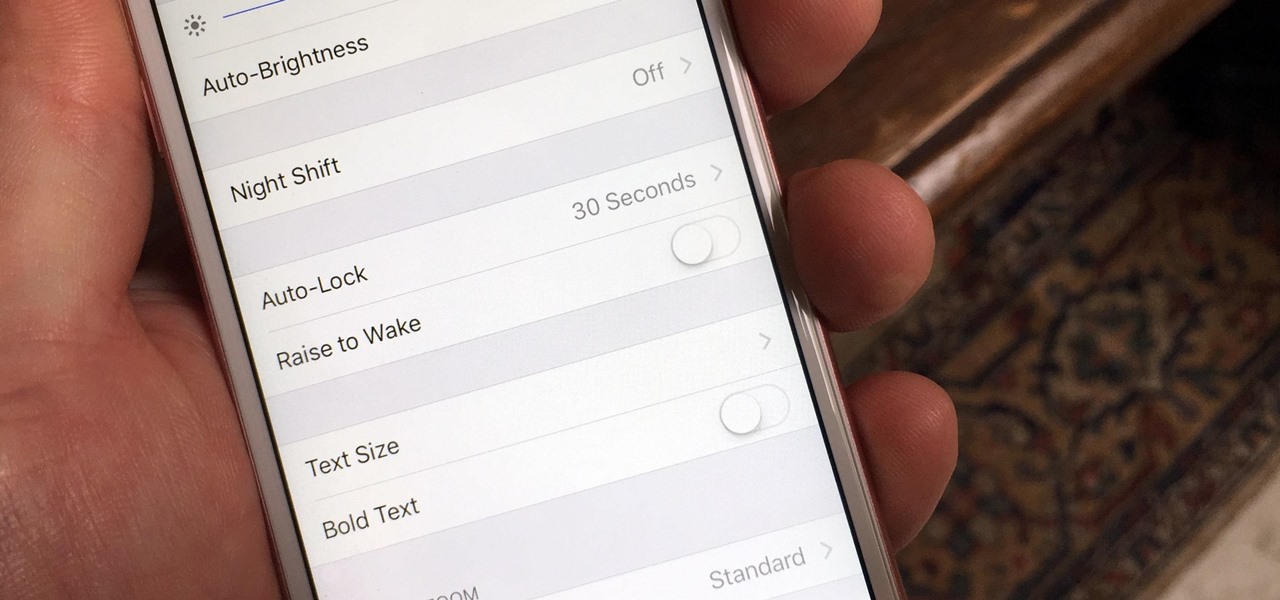
After updating your iPhone to iOS 10, you may have noticed that your screen will wake up whenever you pick up the device to look at it, or even when it's just in your pocket or dangling in your hand.