Samsung introduced a wave of seriously unique and innovative features on the Galaxy S4, including air gestures and weather sensors, but a lot of the features are actually just updated ones from the Galaxy S3. Unfortunately, one of those that returned was the dreaded increasing ringtone. In their increasing ringtone system, the ringtone will start off on a low volume and increase until it reaches your set volume. In theory, this is useful for not shocking the user with a sudden, blaring ringto...

A couple of months ago we showed you Foldify, an iOS app that allows you to create your own custom, foldable, 3D papercraft files. Your designs could then be sent to your printer, cut out, and assembled.

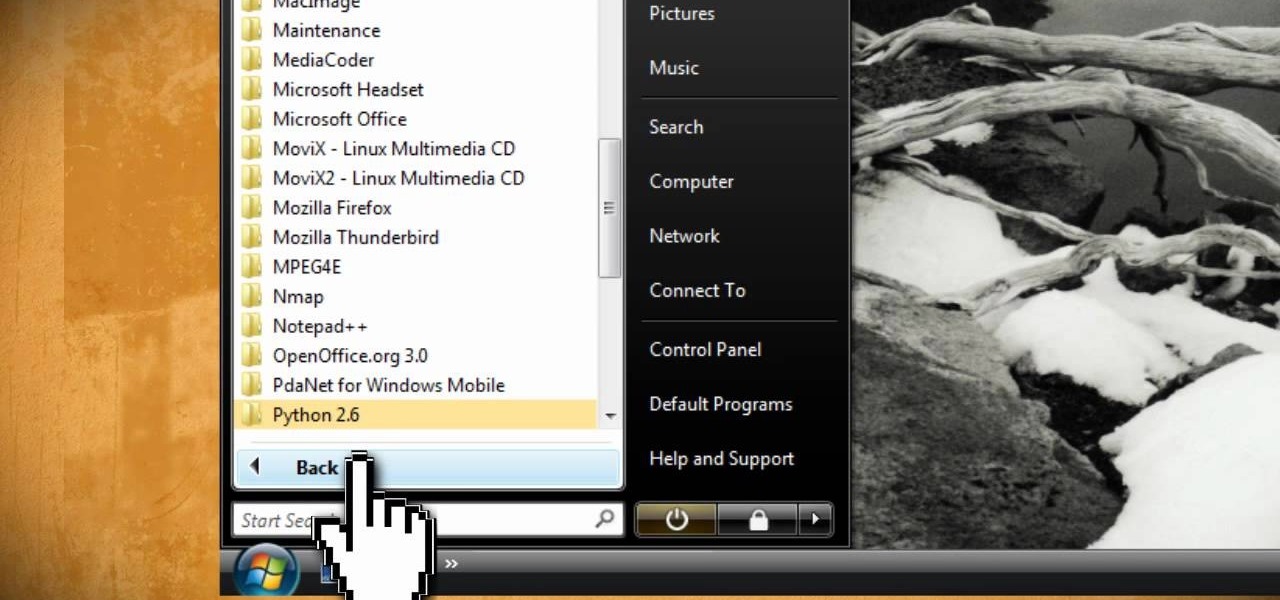
Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!

Think your roommate's been using your computer while you're not around, but don't have any proof? Worried your little brother or significant other is snooping through your stuff? Here's how to check on both Windows and Mac OS X so you can catch and confront anyone who's logging onto your computer without your permission.

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf

Hello, today I will tell you about how you can create a page through wordpress. this is a performance for those who have scarcely been touched wordpress. This guide will put you through basis and create a user and a website among millions of people.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

It seems like everyone is getting in shape these days (or at least trying to improve their fitness), and as a result, there's an endless supply of fitness trackers and smartwatches hitting the market. This is all very wonderful, unless of course, you're broke and can barely afford a decent pair of running shoes.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

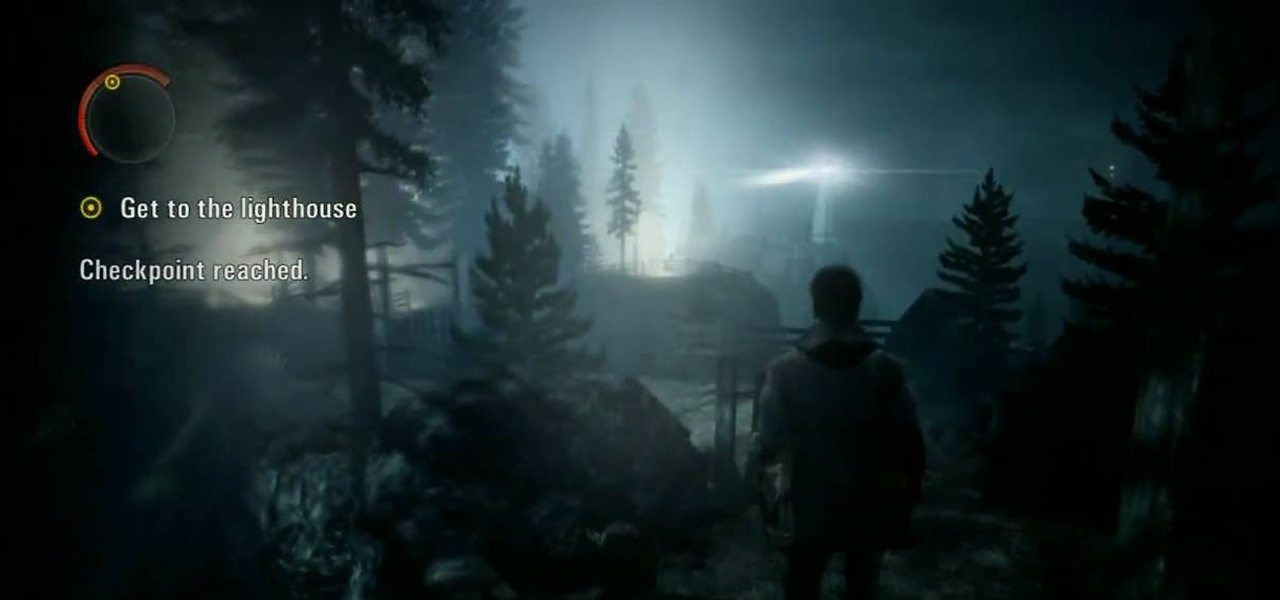
Help Alan Wake uncover the mysterious disappearance of his wife in the small town of Bright Falls. This isn't your ordinary video game, so be prepared for a different kind of gameplay! And these videos will help you get through the first episode in Alan Wake on the Xbox 360. Not just that, but you'll see how to beat Episode 1 on Nightmare Difficulty!

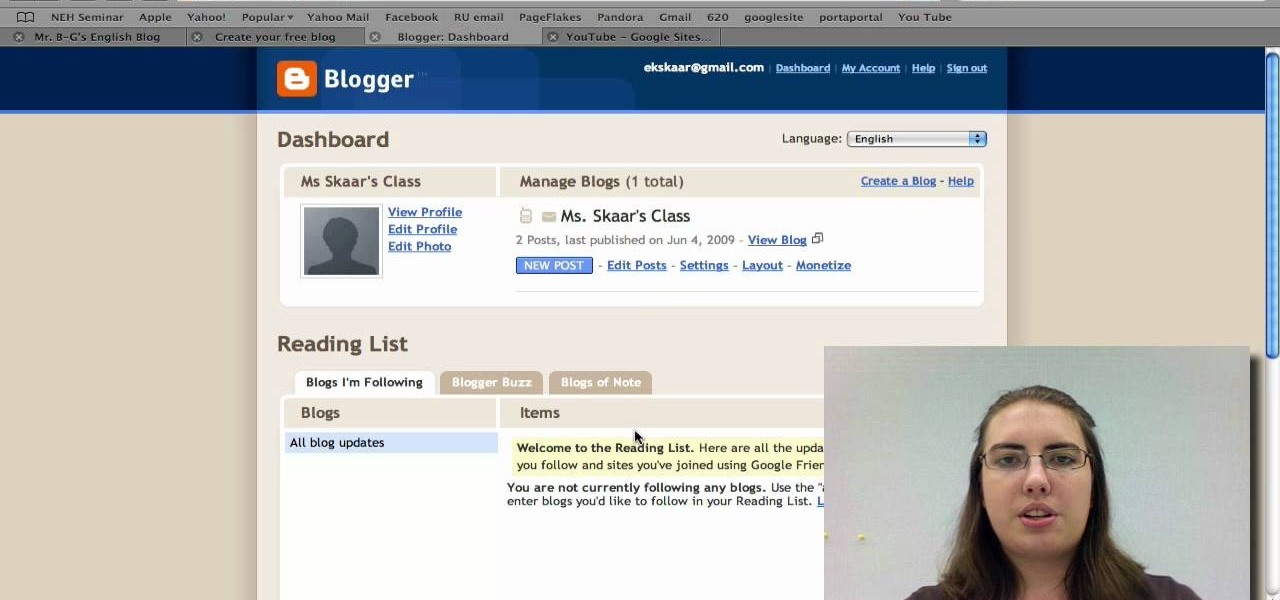
Radford University demonstrates how to upload pictures, embed videos and then publish them in Blogger. Log into blogger and go to your dashboard page. Click edit posts or create a new post. In the blog editor choose edit image from the toolbar. You can now add an image from a URL or upload one from your computer by choosing the choose file option. Next, choose your image position and size. Then, click the upload image button and then click done. Your image will now appear in your post. To emb...

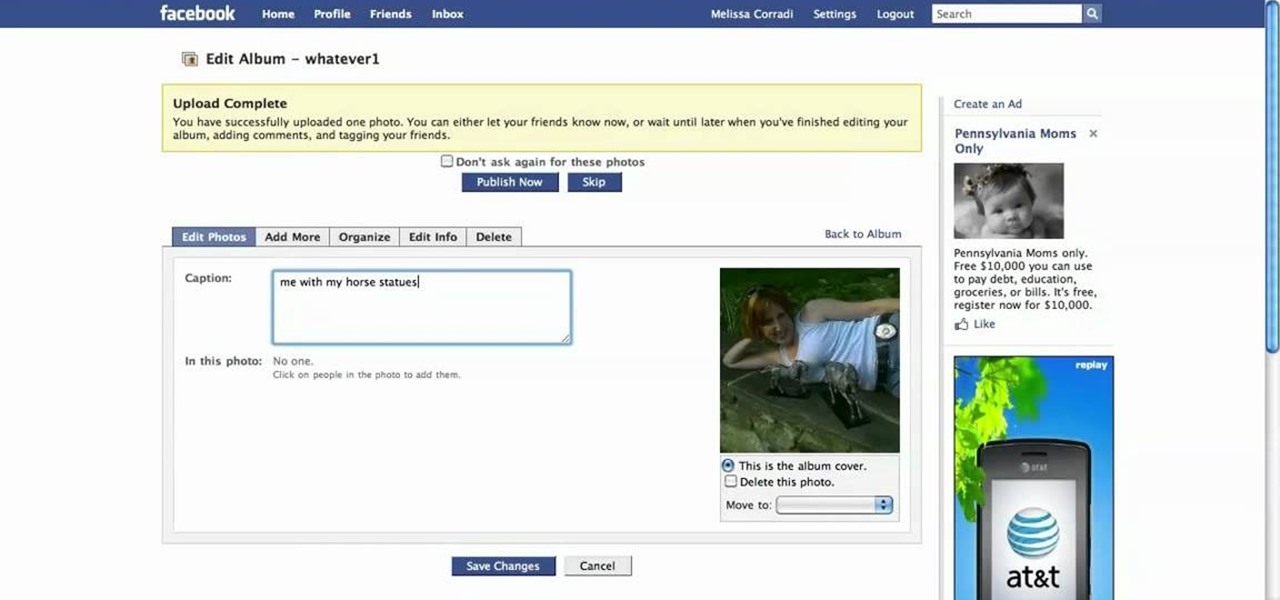
First log into your Facebook account and sign in. Then when you sign in click under your "profile". You will be redirected to another page. This will be your main page, with all of your information that you have put in and what not. Next click on 'Photos'. It will take you to another page. Once in your in there, you will click on 'create a photo album'. You need to name the new album and then create album. Next it will ask the location of the files. It will be located on your computer. Usuall...

Windows is a mess sometimes, full of problems. And your password just might be the biggest problem of all, if you've lost it, of course.

This video will show you how to record video on your Apple iPhone 3G for free! This is a complete guide to installing the iPhone Video Recorder on your iPhone 3G, which also works on the First Generation iPhone.

Instagram is one of the hottest mobile apps to date, yet they have no way to upload photos straight from your computer. You can log into the Instagram web app to like and comment on photos in your feed, but that's about it. Fortunately, there are third-party apps that let you do more on Instagram from your Mac or Windows computer, so you can enjoy Instagram pics on the big screen instead of your tiny iPhone or Android device.

For those of us living in any of the 49 states other than New York on Thanksgiving Day, checking out the famous Macy's Thanksgiving Day parade at New York is more a dream than reality. While the parade airs every Thanksgiving on television, it's also possible to catch the festivities online.

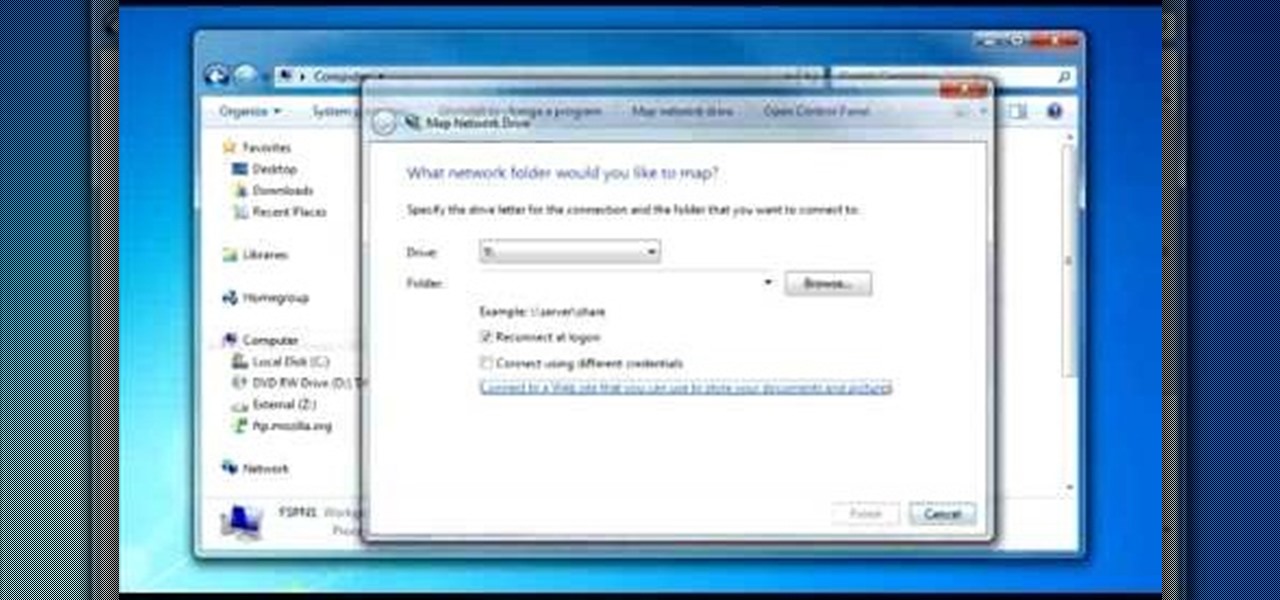
To do that click on tools in windows explorer and choose map network drive. Now click on "connect to a web site that you can use to store your documents and pictures" and then click on next and next. Now you have to type your internet or network address for example you type ftp://ftp.mozilla.org. This is a public server and it does not require a user name or password. Now click on next and there make sure you selected "log on anonymously" but if your server require a password then you have to...

If you would like to use Google AdSense on your website, in order to make money from your site, you will need to get a Google account. Click "sign in" on the Google home page: www.Google.com. Next, scroll down to the bottom of the page and click on "create an account now. Fill it out. It will send you an email to verify your account. You'll need to open your email to confirm.

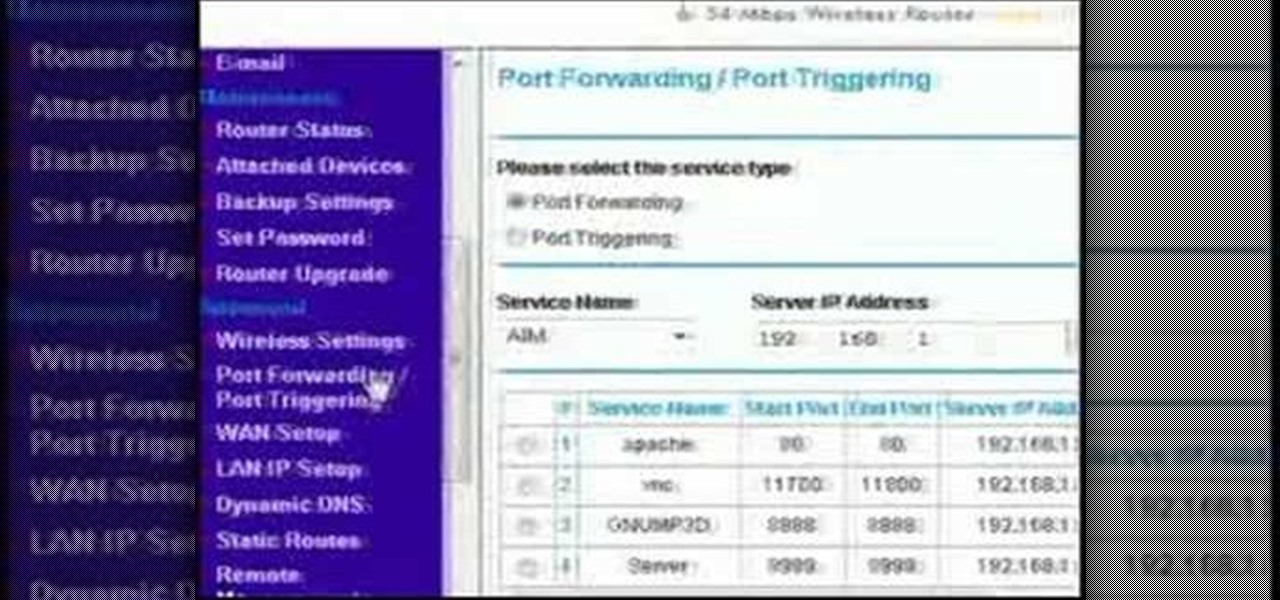
This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...

In this video the instructor shows how to set parental controls for a user ID account in Windows 7. To do this go to the 'Start Menu' and go to 'Control Panel'. In the Control Panel window select the 'User accounts and Family Safety' link. There is an option called 'Set up parental controls for any user'. Select that link and it opens a window where it asks you to Choose a user and set up parental controls. There you are presented with some user accounts that are currently active on that syst...

This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...

Love kalamata olives? Love butter? Are you thinking what I'm thinking? In this cooking lesson from chef Jason Hill, you'll learn how to prepare a simple kalamata olive butter spread perfect for entertaining.

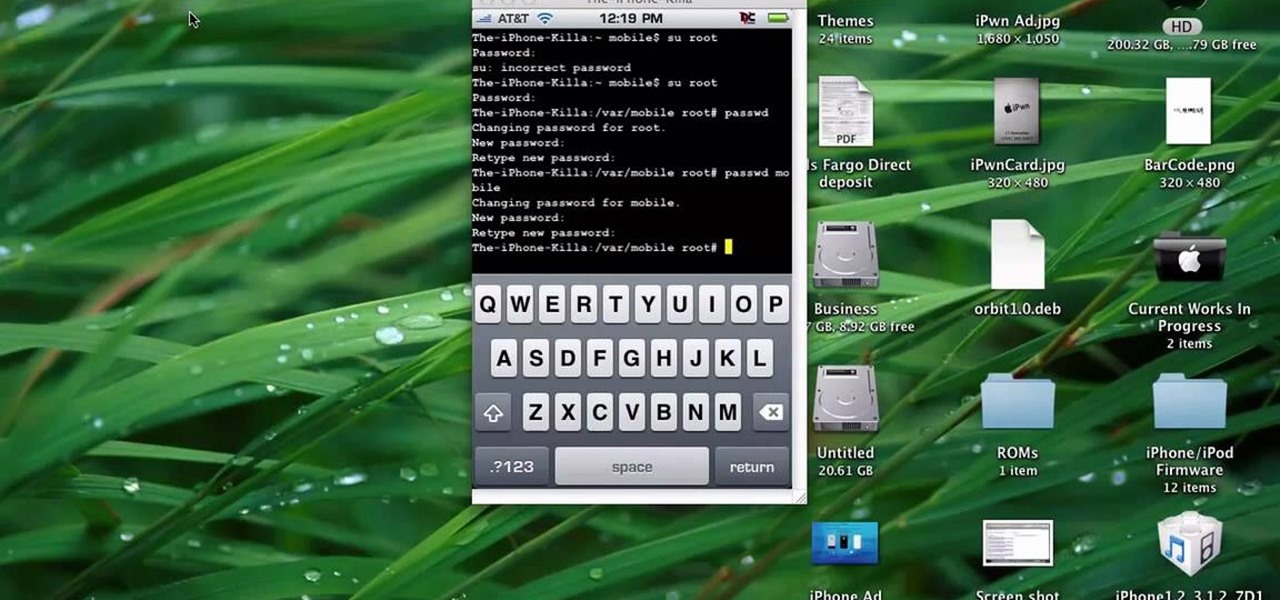
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to broadcast live online.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

Every home is a little different, and for a smart home app to work, it has to be able to be customized to work with each person's unique setup. With the iPhone's Home app, everyone can set up a smart home just how they want, including the number and names of rooms, and where those rooms are in the house.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

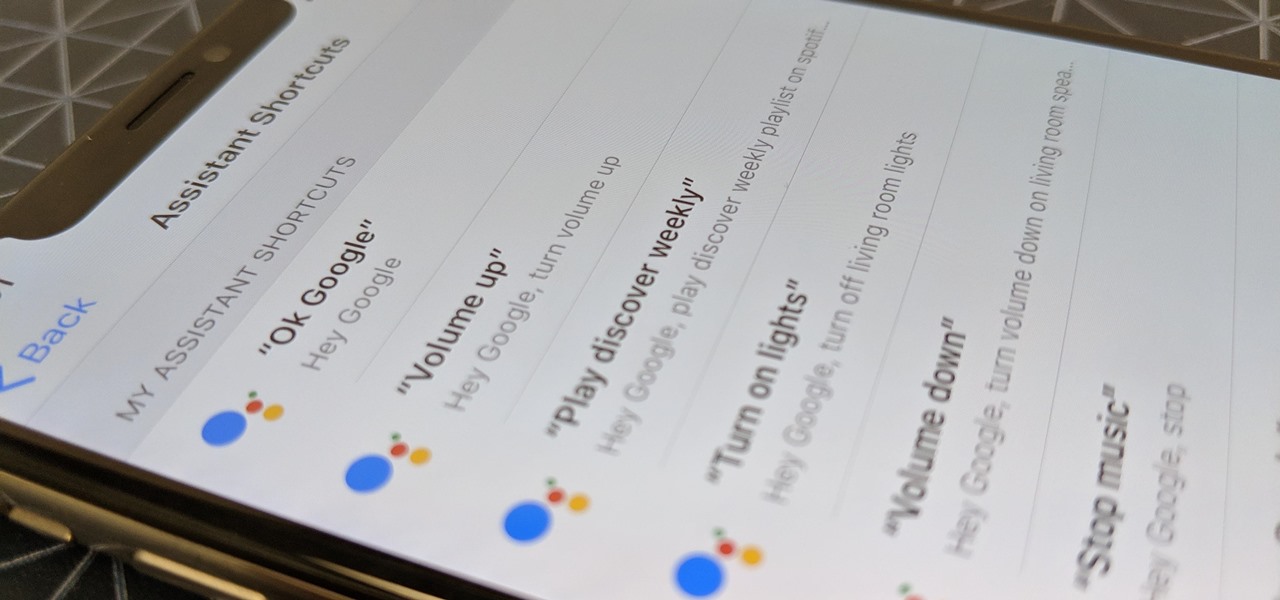
Using Siri to perform tasks on your Google Home device was never possible until Apple released Siri Shortcuts in iOS 12. Actually, it wasn't possible until Google added support for Siri Shortcuts for Google Assistant in Nov. 2018. No matter the timing, the important thing here is that you can use Siri to command Google Assistant which, in turn, can command Google Home.

Update: The LG G8 ThinQ has been announced. You can read all of the official specs at our full article on the new phone.

While iPhones may be more expensive than ever, it won't stop us from losing them or having them stolen. Whether you have an iPhone 5S or an iPhone XS Max, there's a good chance it'll go missing at some time during your ownership. It could end up in a couch cushion or in the hands of a pickpocket, but no matter what happens to it, you need to prepare it beforehand for the inevitable.

There's a growing sentiment around the web that when it comes to Android, stock is best. Many people prefer the clean look of Google's vision for Android, but manufacturers like LG will add features and themes on top of this base to differentiate themselves from the pack. But these OEM skins, as they're called, aren't always as overbearing as you might think.

There are more ways to finding your missing iPhone than using Apple's own "Find My iPhone" tool in iCloud. If you just need help tracking down your iPhone in your home or at a friend's house, Find My iPhone isn't necessarily the most convenient thing to do when you've got these other options to try out first.