Apple released the third public beta for iOS 13.5 today, Wednesday, May 6. This latest public beta update comes exactly one week after Apple released iOS 13.5 public beta 2, which, among other things, introduced Apple and Google's joint COVID-19 exposure notification API. Public beta 3 updates that settings page to show a more detailed "Exposure Logging" option instead.
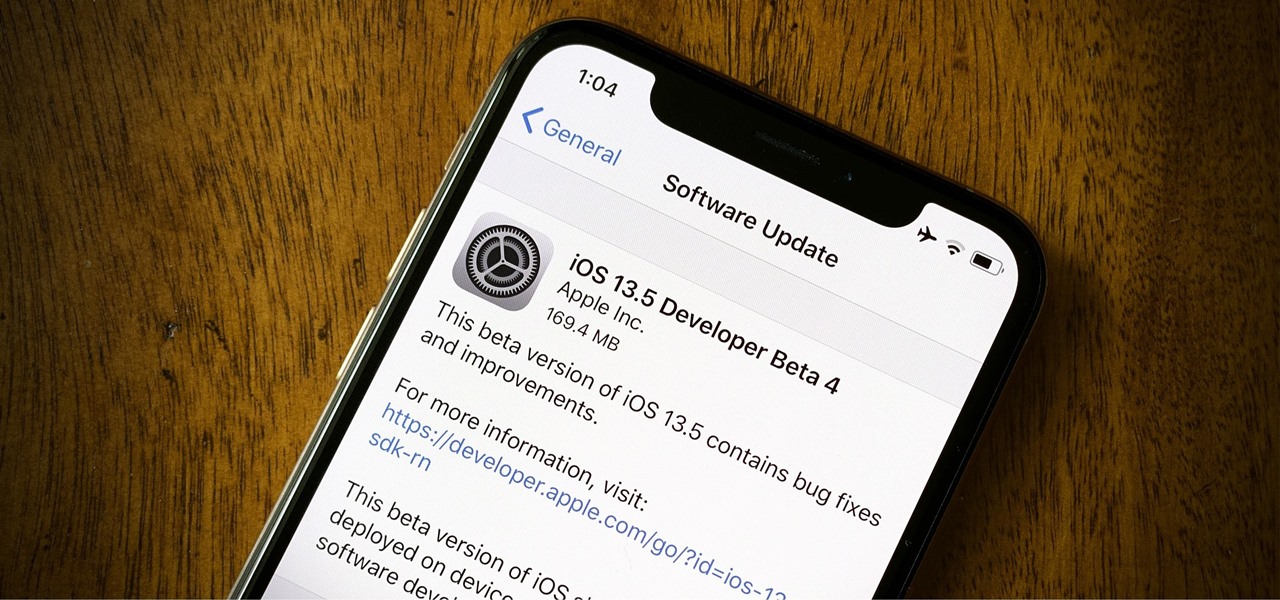
Apple released the fourth developer beta for iOS 13.5 today, Wednesday, May 6. This update comes one week after the release of iOS 13.5 dev beta 3, which introduced Apple and Google's joint COVID-19 exposure notification API to iOS for the first time. Apple updated that settings page to now include an "Exposure Logging" setting instead.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

There are few things more satisfying than fulfilling a craving with instant gratification. Companies like Pillsbury and have made this possible with the introduction of their famous Ready to Bake Cookies line: just rip open the package, break off the cookies along the creased lines, place on a cookie sheet, and bake.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

This tutorial shows you how to get through the laser traps you'll encounter in Chapter 7 of Dead Space 2. The game in this walkthrough has been set to Normal difficulty, and also shows you where to find the logs on this level.

Use the AutoFill feature in Safari to quickly fill in web forms for sites that you visit again and again and save time when logging in. Form entry data is stored in your address book contacts, and from information you have filled out in web forms before. You can see the passwords used by AutoFill in the OS X keychain, and you can also specify and limit general access to those passwords.

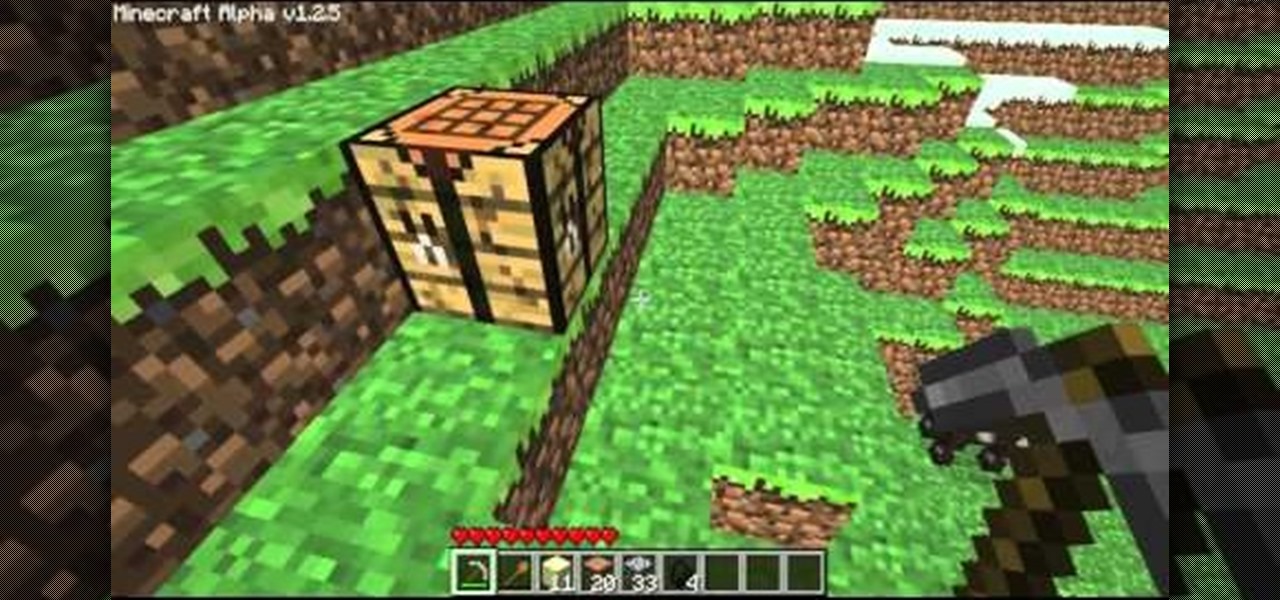
This tutorial shows you a few good tips on how you can manage your multiplayer Minecraft game. There's a special focus on how you can mine for diamonds and other rare commodities when you've logged on to a multiplayer server.

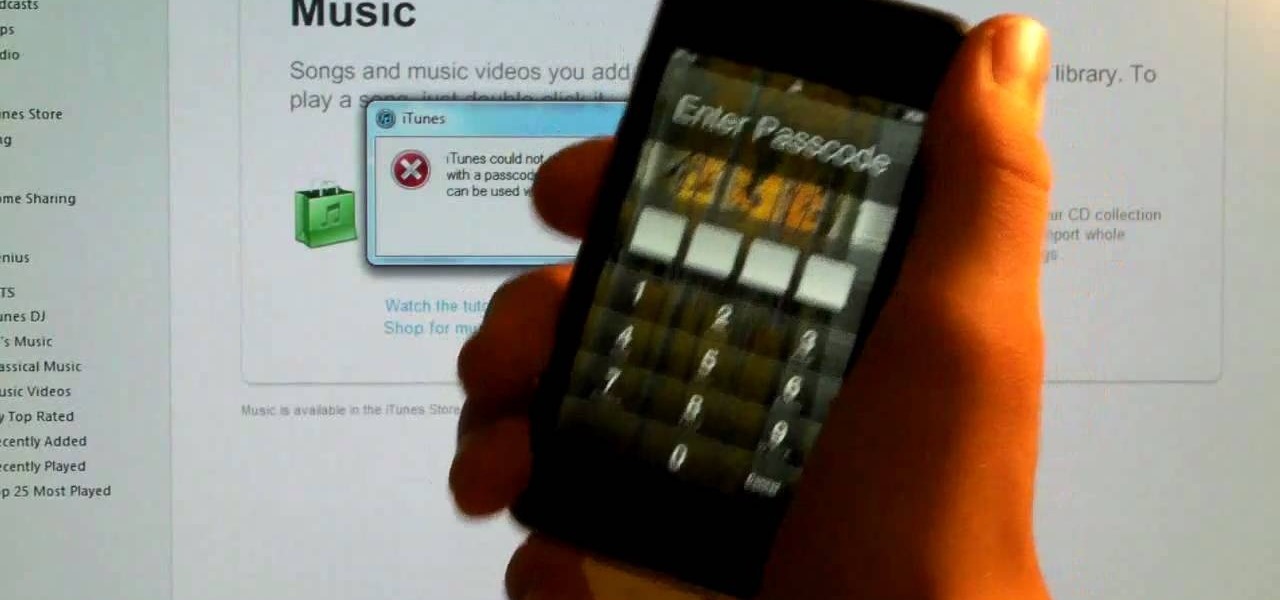
Remove the password on any iOS mobile device! This video will teach you everything you need to know to remove the log-in pass code from your iPhone, iPad or iPod Touch. For more information, including detailed, step-by-step instructions, and to try it out for yourself, watch this hacker's how-to.

Your first night in Minecraft is the most perilous one, and you don't have to build just a simple shelter. There's enough time to build a complete house out of twenty-three logs, twenty-three blocks of sand, four blocks of coal and eighty-one blocks of stone.

Add a small bit of content which appears whenever visitors to your website mouse over a specific area of your website - such as having your company's slogan appear in a small text box when users hover their mouse over the log.

The Sparkle app for your iPhone or iPod Touch is a client which allows you to message your friends in Second Life without having to log fully into Second Life. Great if all you want to do is send someone a quick chat message without playing the game.

Looking for the easiest method of customizing the login screen on a Microsoft Windows PC? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, and to get started personalizing your own log-on screen, take a look.

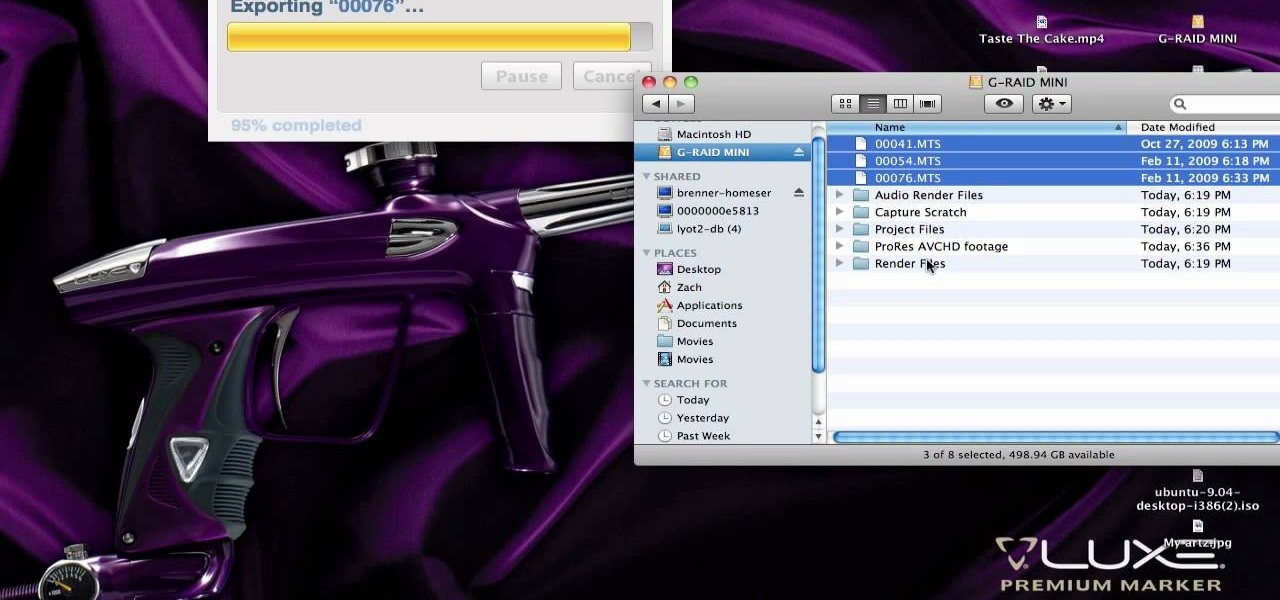
In this clip, you'll learn how to work with AVCHD files that can't be logged and transferred like MTS files. Whether you're new to Apple's Final Cut Pro non-linear video editor or just want to better acquaint yourself with the popular video editing program, you're sure to benefit from this video tutorial. For more information, including detailed, step-by-step instructions, watch this tutorial.

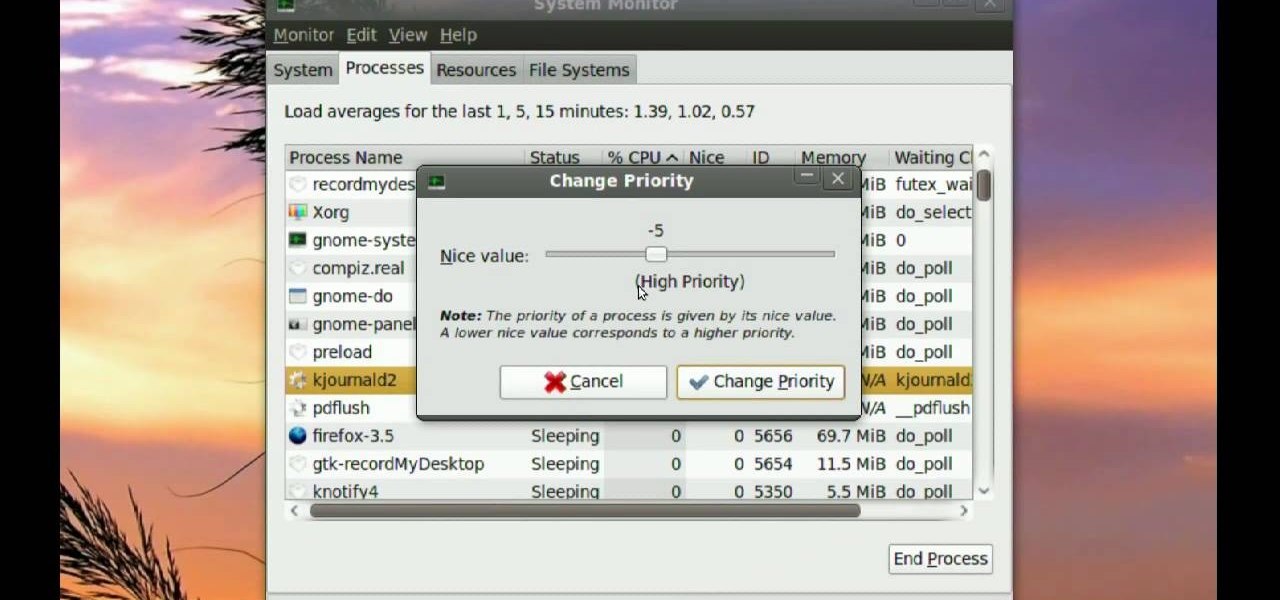
Ubuntu comes with pre-installed tools that can help solve problems you may encounter when using Ubuntu Linux. This video tutorial shows how to identify and address common problems in Ubuntu Linux. Such tools discussed include the system monitor, the log file viewer and the network tools.

In this video lesson of LEARN TO DRAW with Tom Gammill, where the creator of The Doozies discusses cartooning and the spirit of Christmas. Learn how to draw a cartoon santa claus using mostly circles and half circles. Towards the end of the video Tom teaches you how to make a holiday yule log too. Follow along and learn how to draw an easy cartoon Santa Claus.

Find lyrics to an unknown song by logging on to the Internet and typing in a few words from that song into a search engine. Locate lyrics to an unknown song with tips from a professional musician in this free video on music.

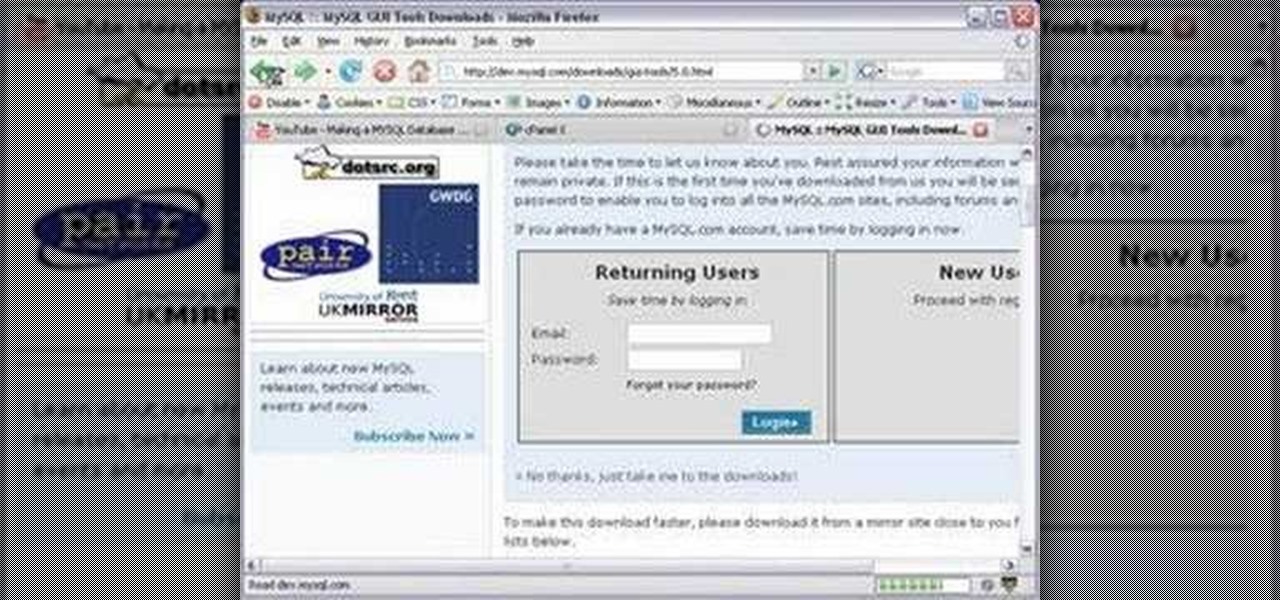
In this tutorial we show you where to download MySQL Query Browser and how to access and edit your databases. MySQL Query Browser is an easy way to access database information remotely from your desktop without having to log in to your server. Learn where to get MySQL Query Browser, and how to use it to access and edit your databases.

No need to spend money on fire starter logs and such items, with free lint from your dryer and some wax from a candle you can create a great item to start fires while camping, hiking and so on. Dryer lint and wax are both small and lightweight so they're easy to pack and carry around. Watch this video training tutorial and learn how to make flame fuel from dryer lint and wax.

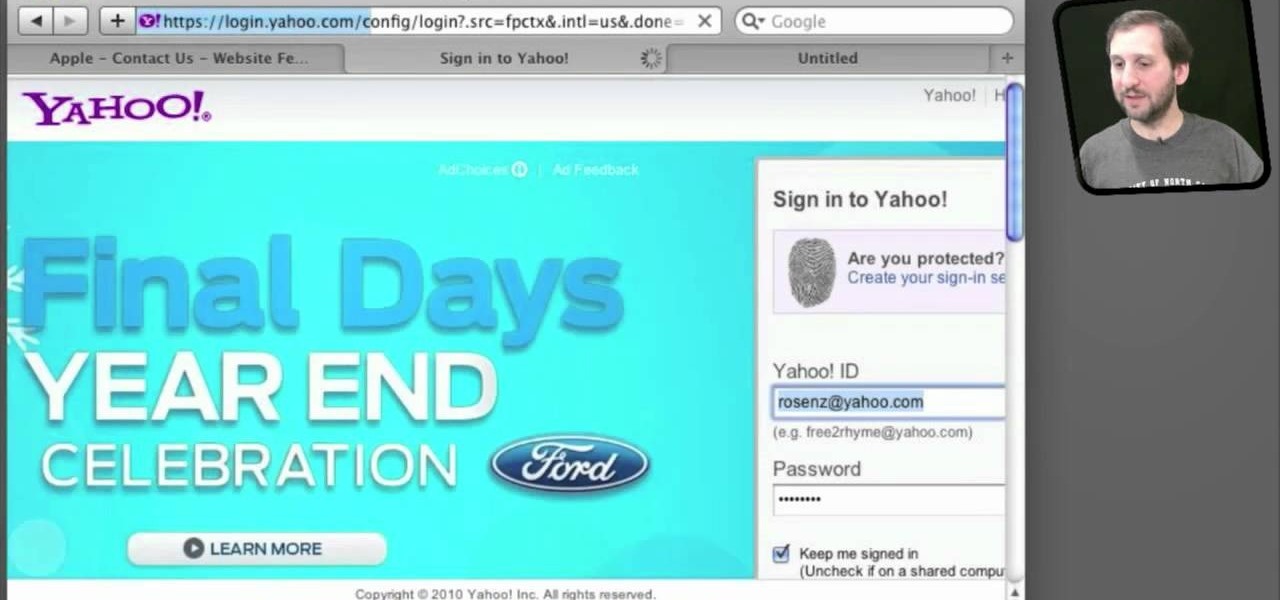
Applications on the blink? In this tutorial, Gary Rosenzweig looks at various ways to force broken applications to quit. He also shows some handy keyboard shortcuts for logging out, restarting, shutting down and quitting instantly.

Epicurious Editor-in-Chief Tanya Wenman Steel demonstrates how to fill and roll up a genoise cake to make a jelly roll, a Yule log cake or bûche de Noël.

Learn how to log and capture movie footage in Apple iMovie so you can begin to transform your raw footage into a completed movie.

Don Schechter explains how to capture your footage from your camera to your computer and log it for easy access later on. You can use Adobe Premiere to capture your movie, but you can not forget to put your tape in your camera.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

For the past three or four months, Microsoft has been pushing advertisements onto the lock screens of some Windows 10 users as part of its "Windows Spotlight" feature. This feature normally shows you scenic photographs and gives you the option to learn more about them by launching an Edge window once you log in. However, the aforementioned users have reported seeing the image below for the new Rise of the Tomb Raider game. Rather than taking you online in Edge to learn about it, you're given ...

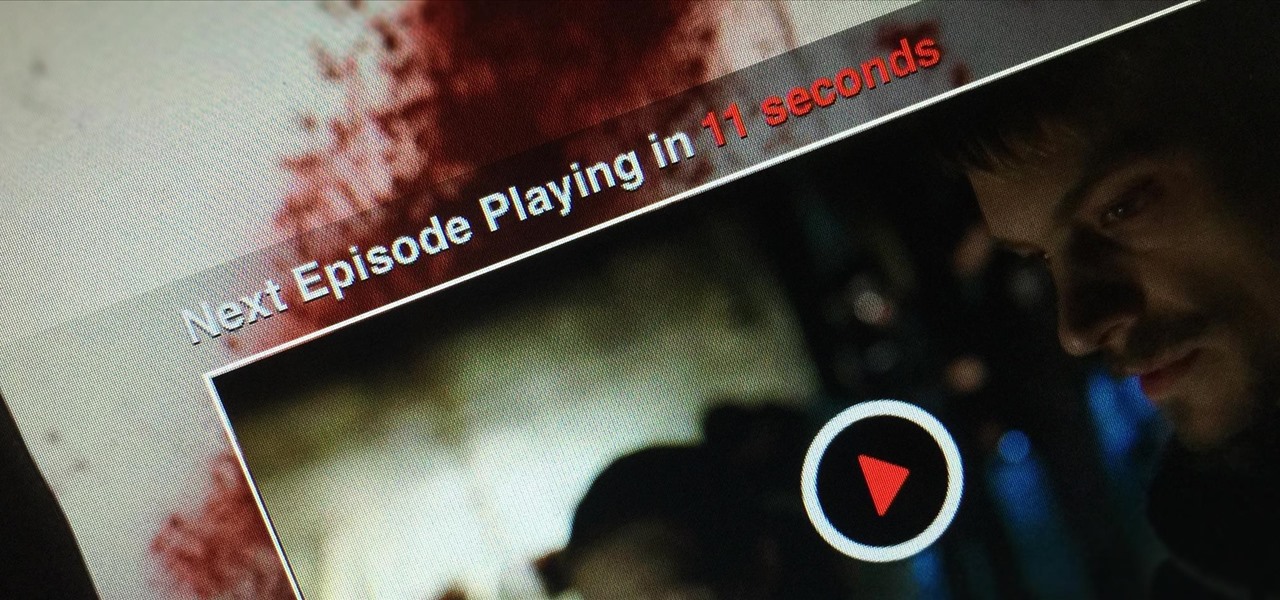
Netflix is an enabler. It creates a joy around binge-watching and couch potato-ness, and the major contributor to this epidemic is its built-in "Post-Play" feature.

A messaging app that blows your mind doesn't come along very often. Yeah, there's WhatsApp and Facebook Messenger, which are both good for what they are (web-based messaging platforms), but when it comes to interesting or unique features, they're somewhat lacking.

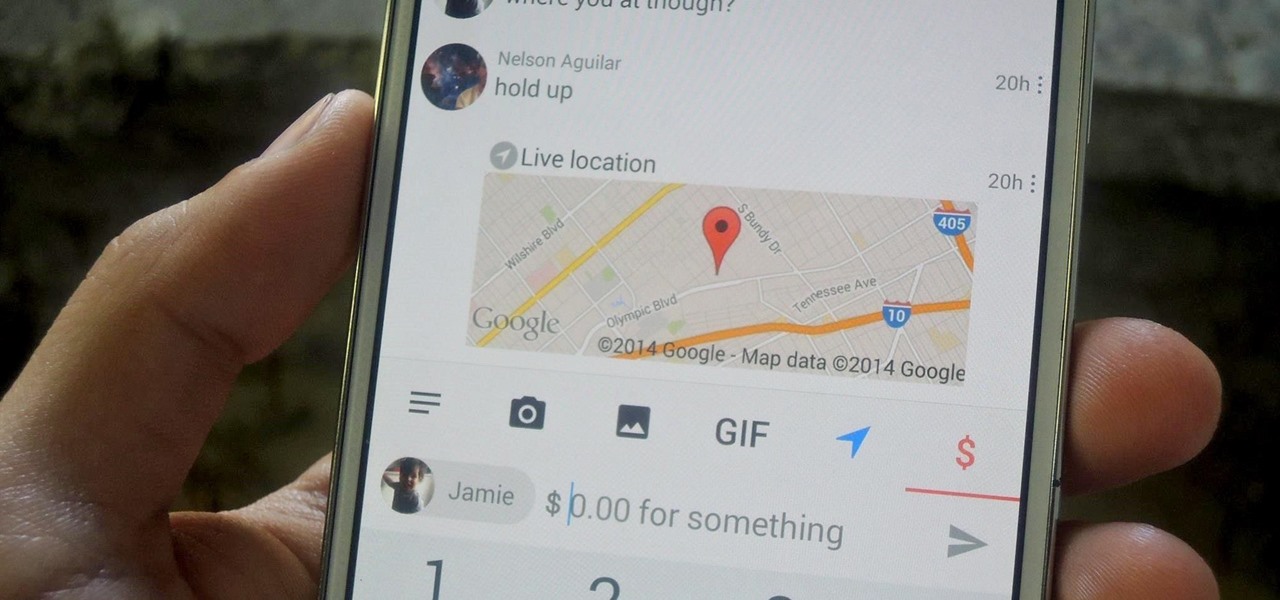
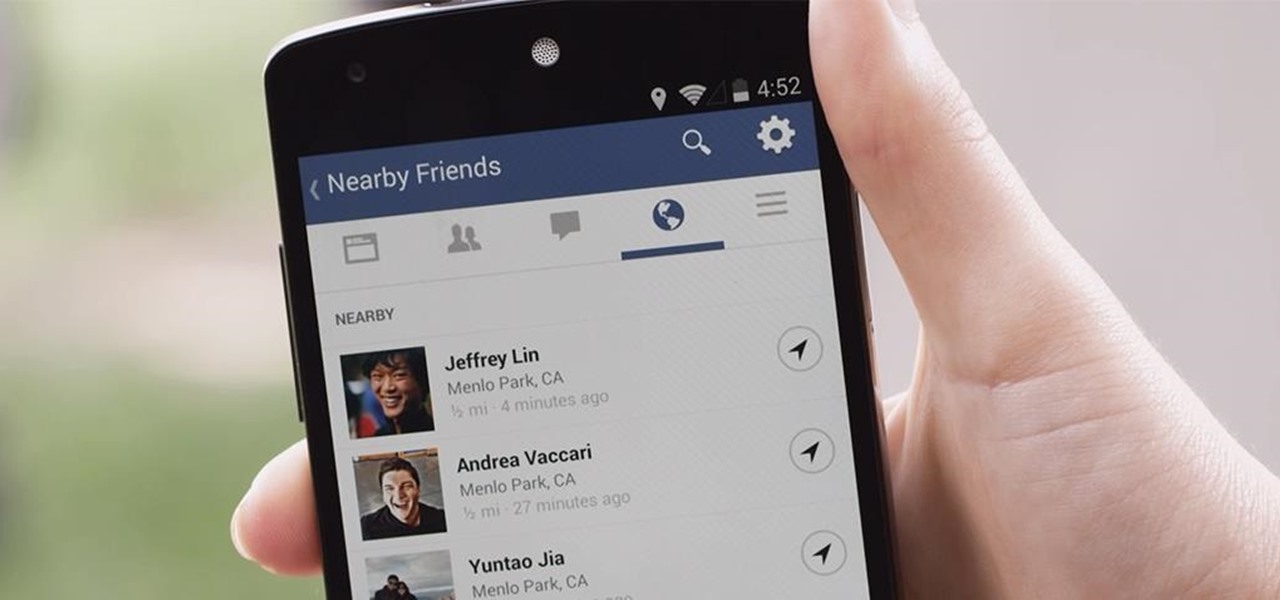
Facebook today has unleashed a new way to creep...er...keep in touch with "friends" using the official Facebook apps on Android and iOS.

While you may suck at Instagram, it's likely that you manage multiple Instagram accounts, whether strictly for personal use or for managing blog and business pages.

If I'm in a hurry, sometimes I'll just turn my computer off and rush out of the house. Sometimes, I'm in the middle of a long YouTube video when I dash off, only to come back and find that my video position has been tragically lost. Hopefully I don't lose my place in that motorcycle accident compilation video when I get ba... damn it.

Apps are now very much integrated with social media, especially with your Facebook profile. Pretty much every app these days lets you log in using Facebook, while some actually force you to, giving you no other option. But, the most annoying part is that these apps leave notifications all over your Facebook timeline, cluttering the hell out of it. So, how can you completely banish all of these apps from being able to access your Facebook?

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

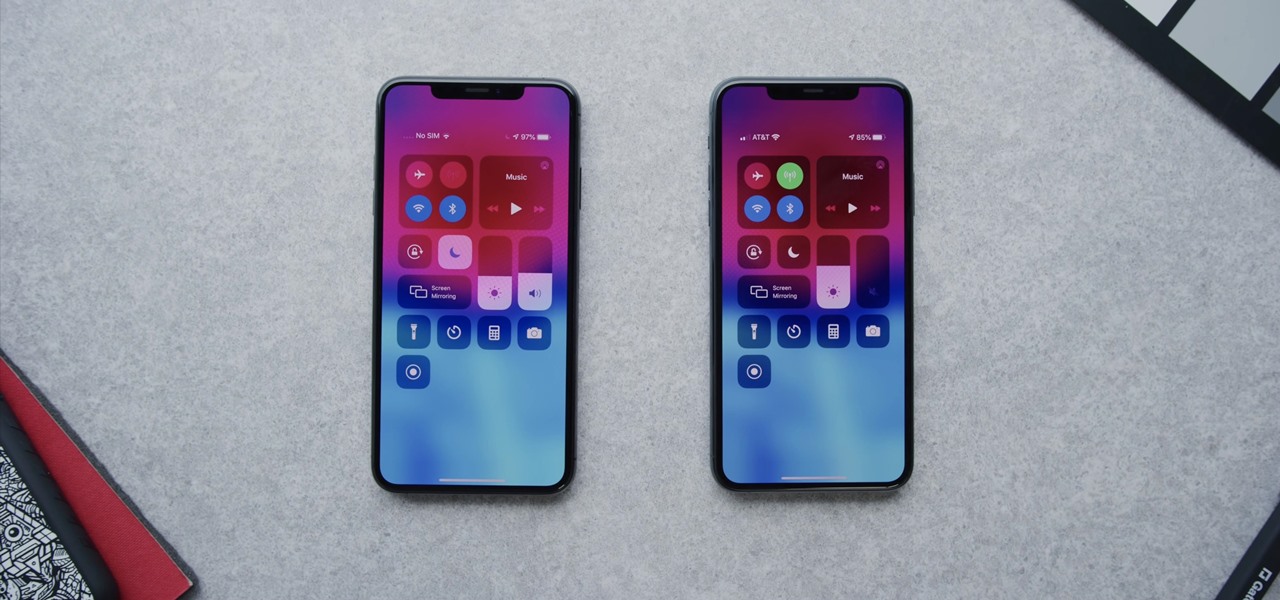
Apple just released iOS 13.5 for iPhone developers today, Monday, May 18. This GM (golden master) update comes 12 days after the release of iOS 13.5 dev beta 4, which introduced updated COVID-19 exposure notification logging settings and the ability to share your Medical ID with first responders when placing an emergency call.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.

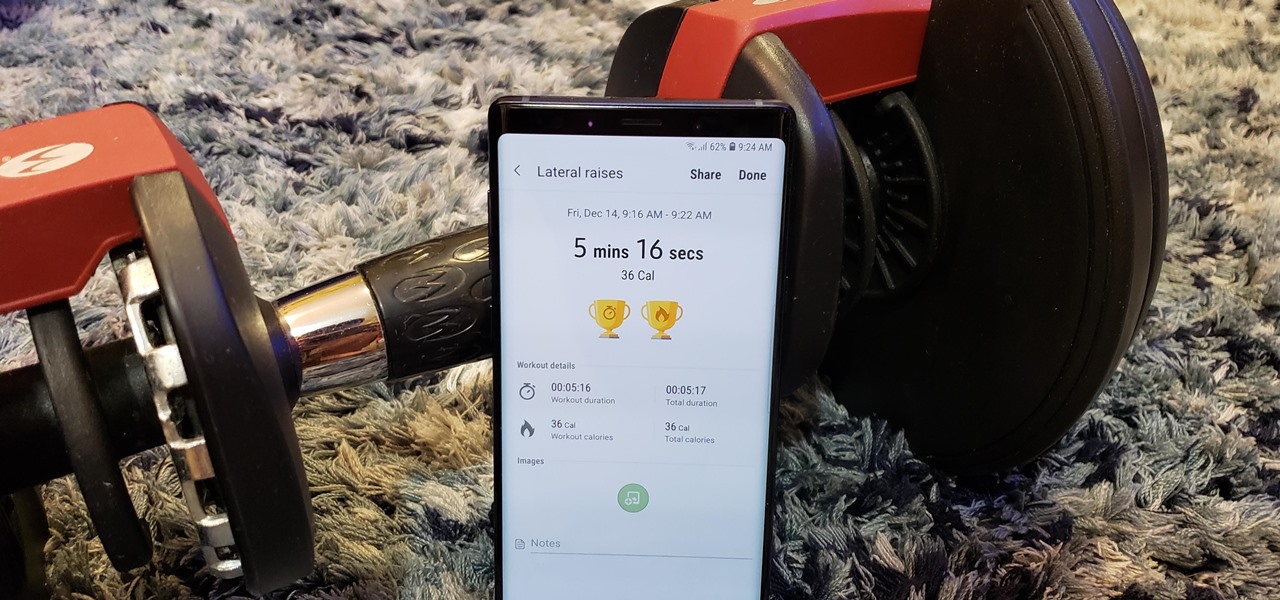
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.