You can very easily replace your normal light switch on the wall with a dimmer switch. The first step is to turn the power off at the circuit breaker. To prevent anyone from accidentally turning the circuit on put a piece of tape over the fuse switch so that it is clear that it is to stay turned off. Remove the screws that hold the switch plate and use a tester to make sure that none of the wires are still live with electricity. Remove the two screws that are holding the switch itself in plac...

The hardest part in the Ashland level of Darksiders on the Xbox 360 is probably the boss fight between you and Stygian. At the start of this battle, Stygian will be wearing a metal cage around its mouth. This prevents you from doing any damage to the beast so you'll have to remove it if you wish to kill the creature. As Stygian does circles around the field, ride Ruin along side its head so that you can swing your Chaoseater at the cage. Use Ruin's turbo to keep up with Stygian. Smash the loc...

Bedbug victim Mike tells us that even a $200 professional exterminator can not take the bugs off his bed for long. He shows you how you can use the Bedbug Powder to solve the problem of bedbugs for good.

In this six-part video tutorial, learn how to create an access database. The following six parts go over the following:
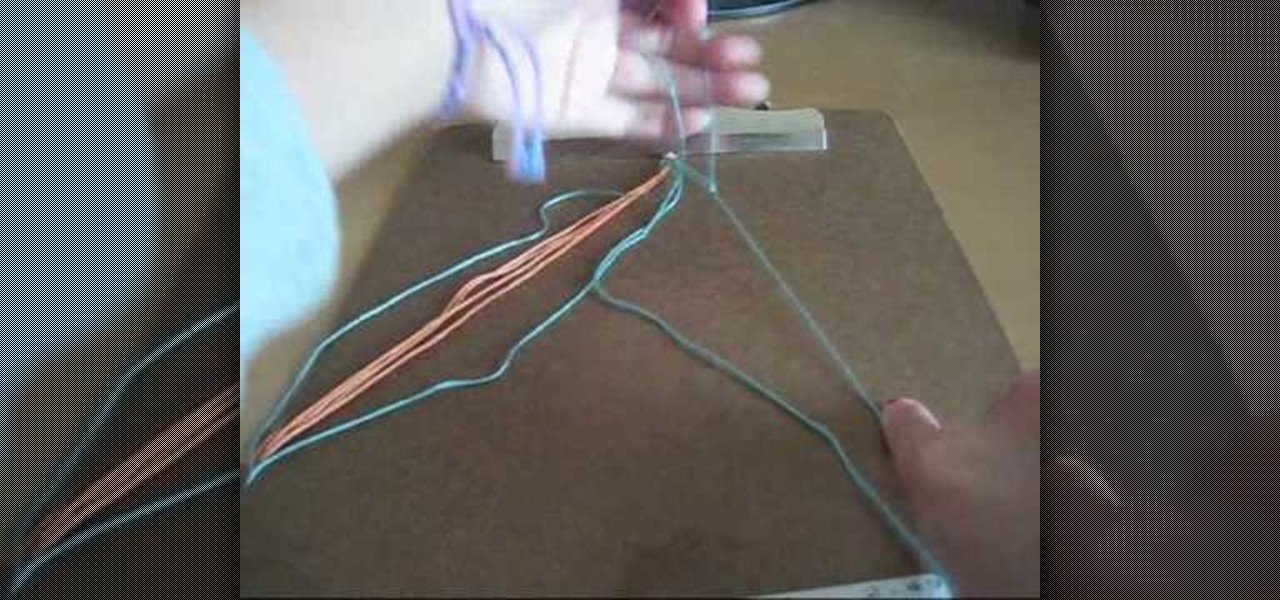
Showing a friend you really care is one reason to start making friendship bracelets. Not everybody wants to show off their friendship to everyone, but if you do, this video tutorial will show you how to make a friendship bracelet, specifically the alternating chevron friendship bracelet. This bracelet is the same concept as the regular chevron.

You can't go wrong with spaghetti and meatballs unless you are feeding a vegetarian! This awesome recipe will surely keep people wanting more.

Turn that dry, damaged ‘do into luscious locks for less at home. You Will Need:

Congratulations! You're the proud new owner of an Xbox 360. But before you can play, you need to hook it up.

With a little muscle and a powerful cleaner, even the filthiest oven can look new. Since it's best to let the cleaner sit overnight, try to start cleaning before bed.

Manu Ginobili shows how to do his PimP fake! This is best when you're on fire and got the defender worried about you getting three-pointers. If he falls for it, draw the contact and it can make your jumper from 2 to an and 1 situation. This is a Nike Signature Moves video.

If you're record player doesn't work anymore, but it still turns, then this is the perfect solution for you. The video show you how to make a cone record player. It's also a neat trick for playing your records with out a record player, instead of a regular phonograph needle.

Learn how to do power hang knee tucks. Presented by Real Jock Gay Fitness Health & Life. enefits

Learn how to do hang knee tucks. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do lower back extensions. Presented by Real Jock Gay Fitness Health & Life. Benefits

In this video clip series, our expert will demonstrate the basic knowledge you need before adding an outlet in your home. Which tools you will need, how and where to drill, safety instructions and box installation instructions are included. Additionally, you will learn how to strip a wire and test for connectivity.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

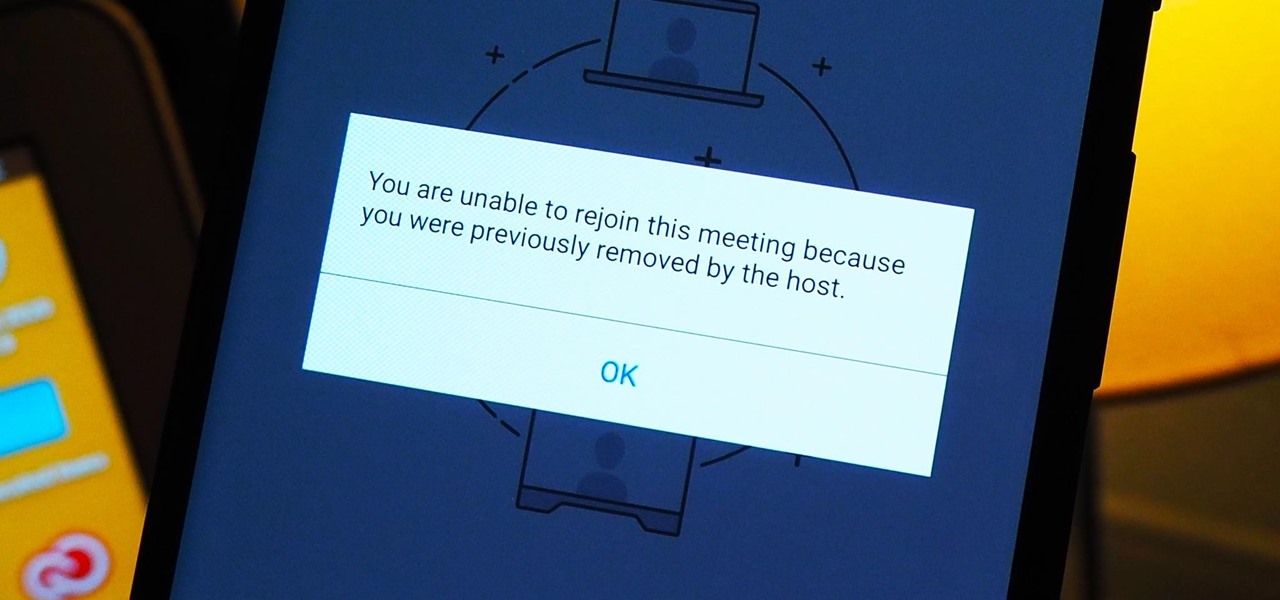
As more and more people use the video conferencing service Zoom, the chances of trolling behavior and attacks only increase. But it's not just "Zoombombers" you need to worry about. A heated discussion between family, friends, or colleagues could turn sideways real quick, and sometimes the best course of action is to remove the participant from the group video meeting altogether.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

When you receive a photo or video from a contact in WhatsApp, after you load it, it's automatically saved to your phone's local storage. That means all received content from WhatsApp is visible to anyone who gains access to your default photo gallery. Luckily, there's a new feature available for the Android version of the app that can prevent this from happening.

Whether you like to go swimming or jump in a hot shower with your Apple Watch on, the chance is pretty high that you'll get water inside its speaker. If you're a big runner, even sweat can get inside there. While there is no way to prevent water from getting inside your Apple Watch's speaker, there is an easy way to get it out so that your muffled speaker sounds brand new again.

I've called 911 accidentally more than a few times on my iPhone using the Emergency SOS triggers, but it's also just as easy to trigger an unintentional call to emergency services using an Apple Watch. These accidental 911 calls can put a strain on local public-safety answering points, or call centers, as well as local authorities and emergency medical technicians.

In the Android community, Samsung's slow updates have long been the accepted norm. With the Note 8's recent Android Oreo update, Samsung completed annual version updates to their 2017 flagship lineup. Now is a great time to look back on how Samsung has fared with updates over the past few years. Hint: It's not pretty.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

WhatsApp comes with a ton of great features that make it the go-to messaging app for millions of people around the world. Among these is the ingeniously simple Read Receipts that let you know your message has been viewed. If you want to read a message without alerting the sender, however, there are simple tricks you can perform to give yourself plausible deniability.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

Recently, many manufacturers have started offering phones with a clean, stock Android UI. Motorola, Essential, Nokia, and OnePlus are probably the biggest names that have listened to user feedback and shifted more towards AOSP. But if your phone still has a bloated OEM skin, there are a few things you can do about it.

UPDATE April 4, 2019: We had high hopes for the ZTE Axon 9, but it won't be releasing in the United States. If you're in another area of the world, you can look into the ZTE Axon 9 Pro, but we cannot recommend this device to American readers due to carrier incompatibility. Below, we've saved the early rumored information on the Axon 9 for posterity.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

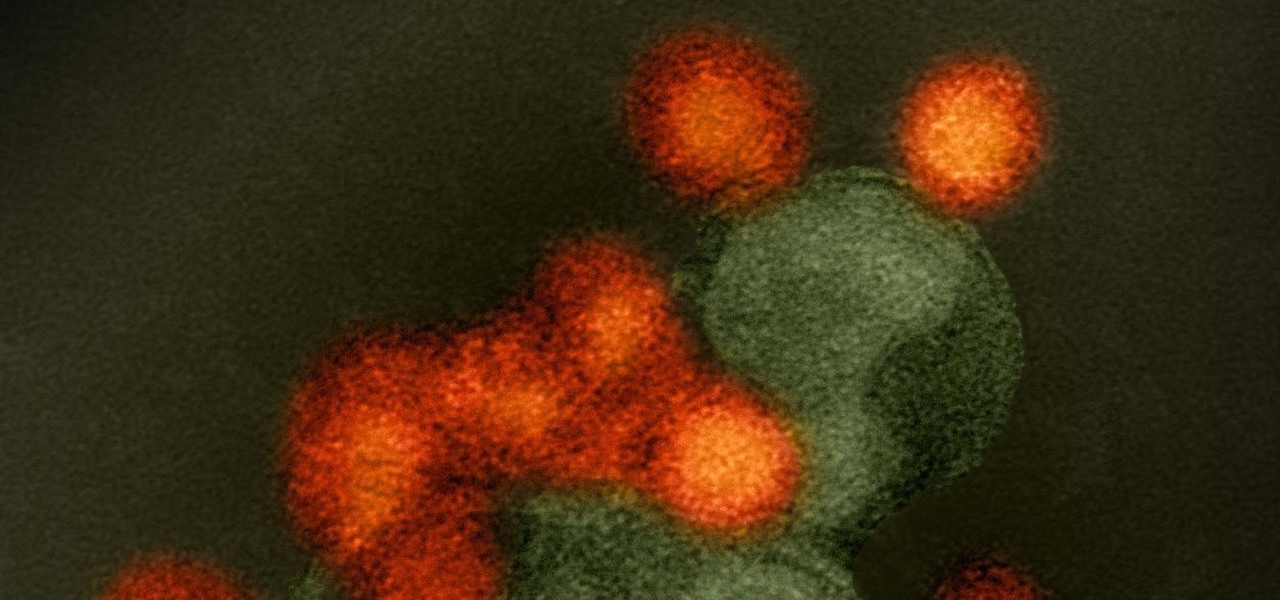
We might think of Zika as a mosquito-borne virus that effects developing fetuses, but, it also can be passed through sex by either a man or a woman, just like herpes and other STD viruses. New research has shown that vaginal bacteria can inhibit sexually transmitted Zika virus and Herpes Simplex Virus-2 in women.