Password protect your files and folders in Mac OS X. This free video tutorial from CNET TV will show you how. Thwart would-be snoopers with this home cryptography guide, which presents easy-to-follow, step-by-step instructions on how to protect your privacy by encrypting your sensitive data.
Password protect your files and folders in Microsoft Windows XP or Vista. This free video tutorial from CNET TV will show you how. Thwart would-be snoopers with this home cryptography guide, which presents easy-to-follow, step-by-step instructions on how to protect your privacy by encrypting your sensitive data.
In this video, learn how to view private MySpace profile pictures. The process is easy & quick. In no time you will surfing MySpace freely with no privacy preferences to stop you.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.
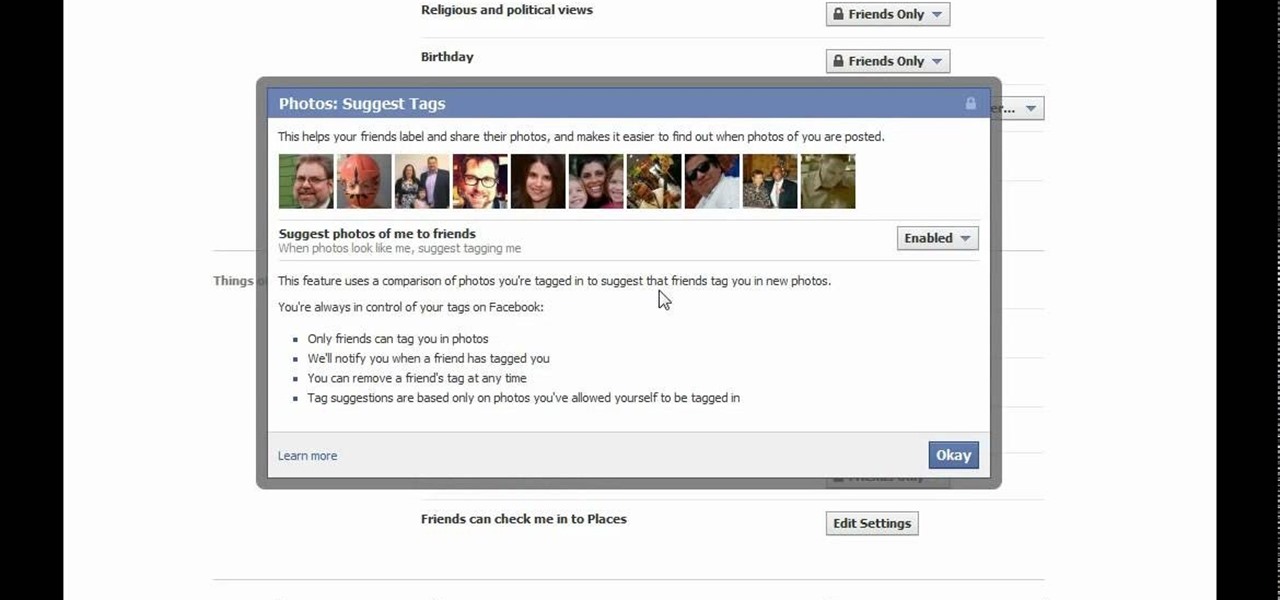
Don't like the idea that Facebook could recognize your face in a friend's photo and suggest they tag you? Take control of your privacy and learn how to disable Facebook's facial recognition feature for photos. You should know when you're going to be tagged in a photo.

Privacy is important. If having your own Minecraft world isn't enough, build yourself a secret room in your Minecraft world. Watch this video to learn how to build a hidden room, perfect for storage of the most valuable items in Minecraft beta.

Sometimes it's necessary to do a complete restore of a device, even an Android one like the Samsung Galaxy Tab. To reset the Galaxy Tab to its factory settings, hit MENU < SETTINGS < PRIVACY and click on FACTORY DATA RESET. Lastly, click on RESET PHONE (it's okay that it's not a phone) and then ERASE EVERYTHING.

In this tutorial, we learn how to keep personal information private when using Facebook. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

Google calls it "Incognito," Microsoft says "InPrivate," the other browsers call it "Private Mode," and colloquially it's known as "porn mode." Whatever you call the tracks-free way to browse, here's a trick to force your favorite browser to always start with its privacy protocols activated.

Protect your privacy by editing or completely erasing your Amazon search history. It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started managing your own web pages with Google Sites, take a look.

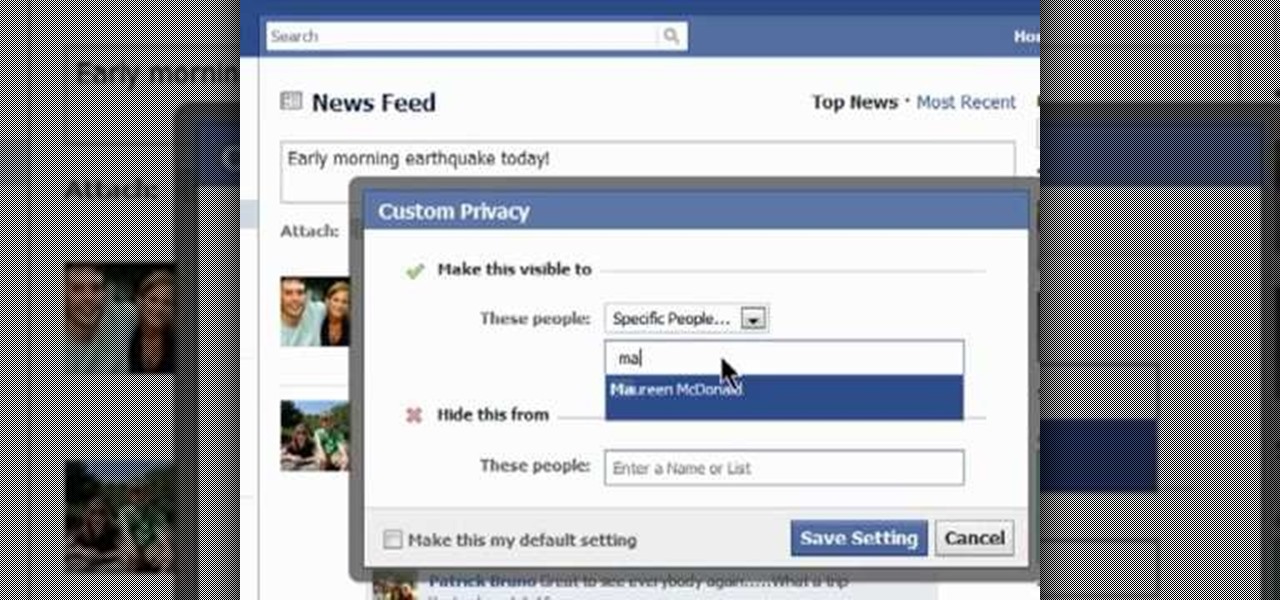
This clip offers easy-to-follow instructions on how to adjust your Facebook privacy settings to prevent your friends (and others) from checking you into locations through of Facebook's Places feature. For more information, and to see how to turn off Places yourself, watch this helpful video guide.

Protect your privacy by using Google Search over SSL. With Firefox, it's easy! And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started using Google Search in SSL mode yourself, take a look.

Protect your Facebook posts! This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

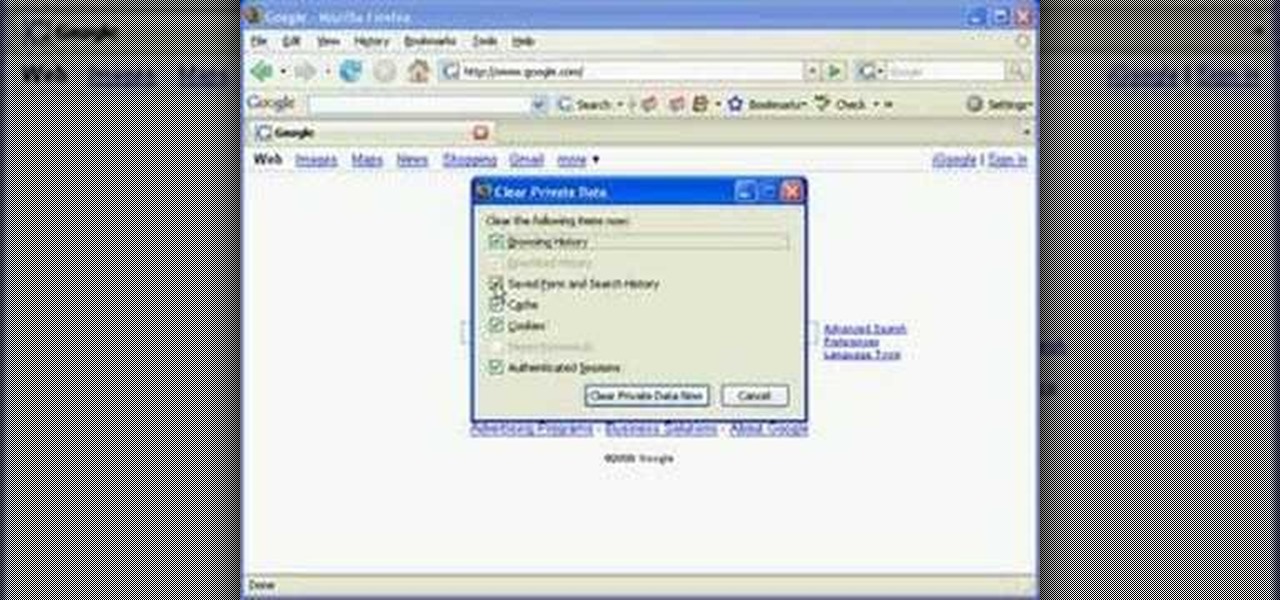
Protect your privacy. With this free video tutorial, you'll learn a method for clearing your Google search history in the Mozilla Firefox web browser. Note, however, that this only works locally and therefore will only prevent those who share the same computer as you from seeing your search history.

When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

When you do an internet search, you'll see ads that are relevant to your query mixed in with the rest of your results. Nothing surprising there—it's how the internet is funded. But then, when you click one of the search results, you'll also see ads that are related to your initial search. Now that's a bit creepy, because it demonstrates that one webpage knows what you typed into a different webpage.

If you're using Adobe Illustrator CS4, you know that cropping an image can be less than a simple task. This how-to walks you through the steps, not only showing how to place and move the image, but also how to crop it to the desired sized. Unlike Photoshop which allows you to work directly with pixels, Illustrator treats all images as whole objects. SO, watch this video and end the frustration that Adobe Illustrator can bring when you're cropping an image.

A lot of women mistakingly think that they can't do arm exercises or lift weights because they will bulk up like a classic chunkhead. But this logic is extremely false. If you're trying to lose weight, muscle burns more calories per unit than fat, which means gaining muscle is to your advantage.

This video demonstrates how to make a variety of ghillie suits. You can adapt your camouflage to many different environments to make yourself more invisible. Additionally, this series shows you how to make multiple types: rifle covers, partial suits, equipment covers, etc.

This video shows the viewer how to make a UNA box from pieces of hardwood, and 2 pieces of dowel. The box is made by building the normal box from the wood. The lid is then secured using a large piece of dowel so that it can pivot. Additionally to the first large dowel another smaller piece of dowel is secretly added to stop the box opening this has to be removed for it to open so makes it harder for intruders to open. The box can then be sanded, painted and used to hide small objects!

Thanks to its encrypted messaging, WhatsApp can be a platform for secure communication with friends and family. One drawback, however, is that the app would let anyone add you to a group chat, regardless of if you approved it or not. This lack of control over your own account is over, as WhatsApp now lets you decide who can add you to a group chat.

On Sunday, Apple CEO Tim Cook (the number one person on our NR30 list) made a rare television appearance to talk about and show off his current obsession: augmented reality.

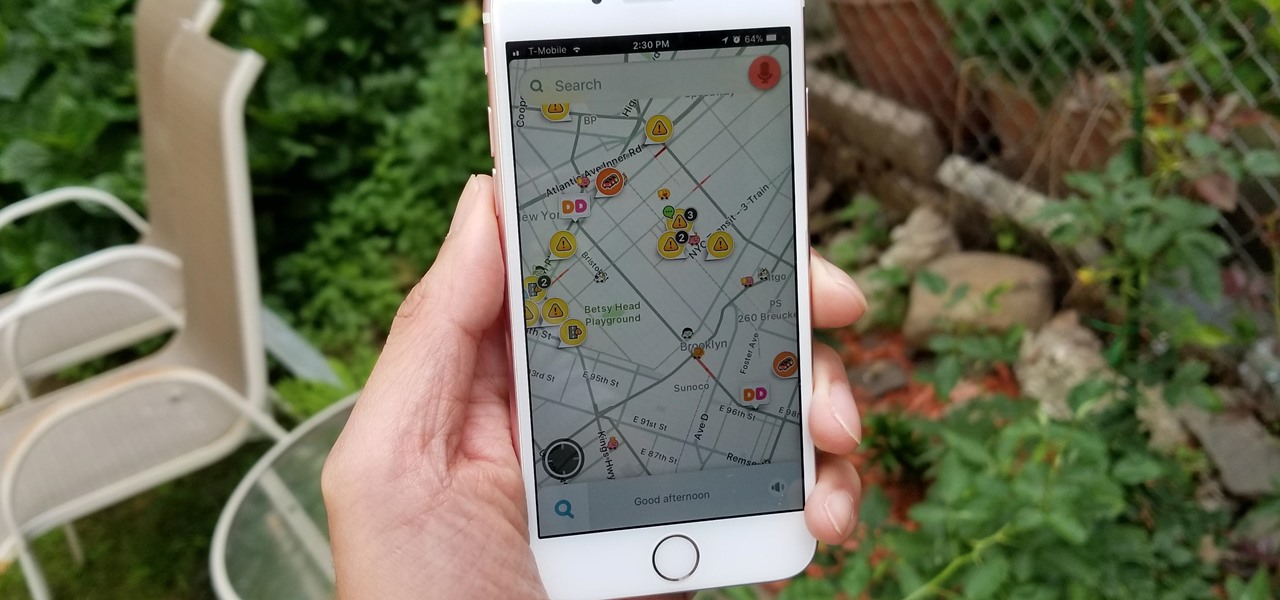
Some of the things that make Waze such a great navigation app are also its biggest downsides. Real-time data shows where individual users are, and the app automatically gathers traffic info that other drivers may encounter. These elements ensure that road conditions are as up-to-date as possible so that everyone gets to their destination safely, but it's certainly not ideal if you're a privacy-minded user.

Firefox Focus has been out for iOS for a while now, so it's about time Mozilla began porting the app over to Android. It's an amazingly private browser that protects you from trackers and ads when you're surfing the web. It blocks a wide range of online trackers, erases your browsing history, hides passwords, and deletes cookies. This essentially means ads won't be able to follow you around, in the sense that you won't see ads related to your last ten searches on Google.

Bose Corp is the latest company trying to make another dollar off of you without your permission. Bose Connect, the companion app to the swag $350 Bose headphones, is not the Jane to your Jack that maybe we all hoped it to be.

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.

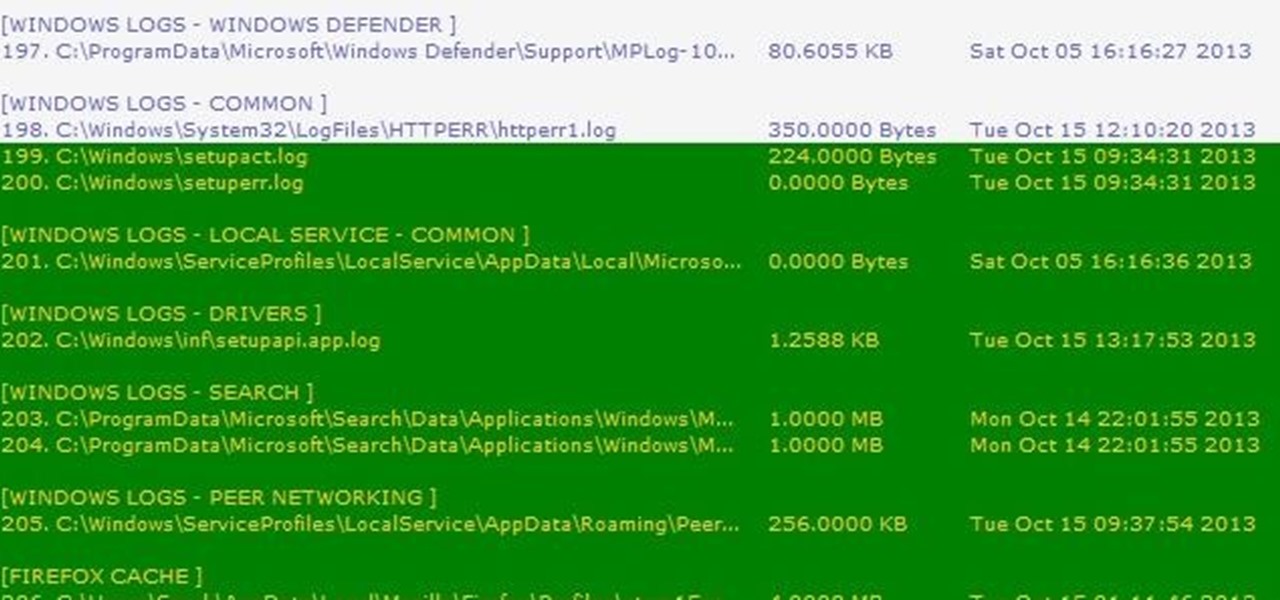
With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

QR codes allow you to quickly and easily store and retrieve data within a single image. Much like barcodes at grocery stores, QR codes are images that can be scanned to discover data, such as an online website URL. Additionally, they can also be created by inputting text data into a QR code generator. Try scanning some of the QR codes in this video with an app on your phone or tablet to see how they work!

When it comes to weights and lifting them, often people slack off or just forget about form because it's easy to do so. Additionally, it gets a little hard to think about sitting up straighter and rolling your shoulders down when you have a 100 pound weight above your head.

Why run in intervals rather than either slow, medium speed, or fast during your daily jog? Interval training, which alternates between slow, medium, and fast, surprises your body by constantly changing the pace. This makes your body work harder in the same amount of time as your usual run.

Being a professional DJ takes a studied ear and a technical mastery of your equipment. This video tutorial series covers beats, bars, and phrases, and how to incorporate beat and breakdown looping into your DJ set. Additionally, DJ Phil K shows how to insure audio frequencies blend together, and provides professional tips on how to approach your first DJ gig.

This video shows the viewer how to make Halloween style lanterns using commonly available items. The base lantern is a Chinese style paper lantern; these can be purchase from home retail stores. The general principal is too cut out the shapes of insects from black paper. These can then be fixed to the lantern to project the image. Additionally holes can be cut in the insects and covered with red tissue paper. The light will shine through the red tissue paper giving the appearance of blood. Th...

Watch as amazing make-up artist, Kandee Johnson transforms herself into Barbie with this step-by-step tutorial on how to apply the make-up and look of this famous blond bombshell doll! The following eyeshadows were used to achieve this look: MAC in Pen & Ink, Da Blng, Carbon, Vibrant Grape, Indian Ink, Fig 1, and Deep Damson. LARENIM mineral eye shadows in Bedazzle & Lust and Urban Decay's eyeshadow in Grifter were also used. Additionally used: Hot pink blush as eye shadow, Make-Up Forever ho...