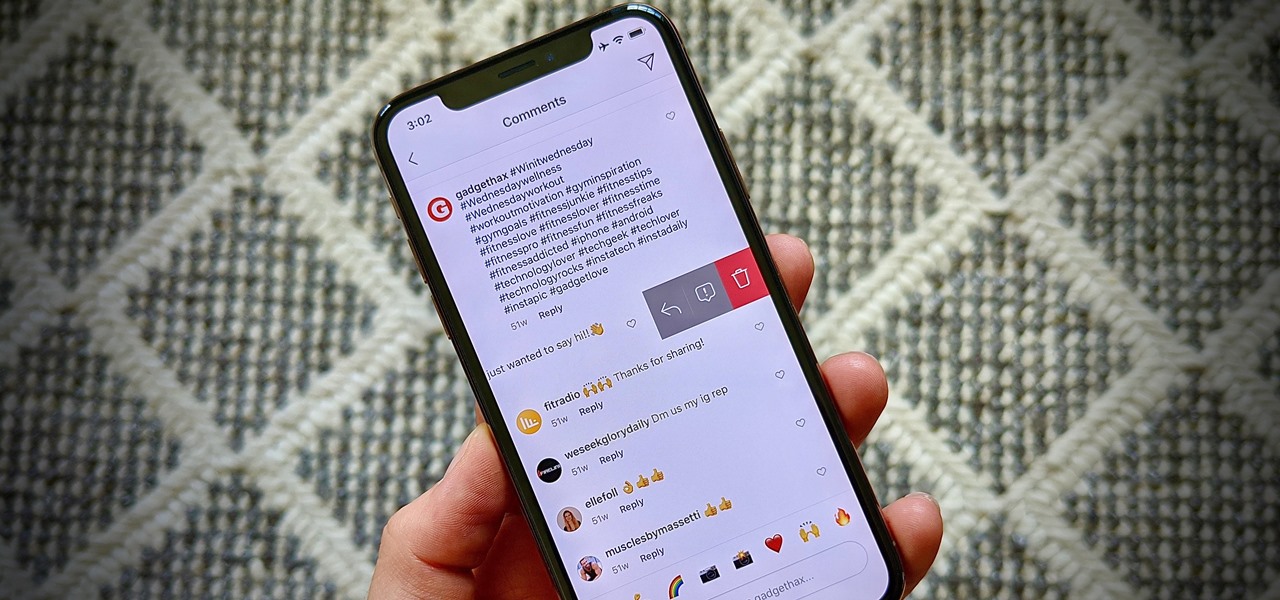
When you post a photo or video on Instagram, it's always nice to see positive comments from friends, family, and even fans. On the other hand, it's never fun to see spam or hate messages underneath your posts. Before, you'd have to delete these comments one by one, but now you can delete comments in bulk.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

Badges? We don't need no stinkin' badges! That is, unless they have augmented reality content embedded in them and give us full access to Facebook's annual F8 developers conference — in that case, yes, we'll take all the badges.

Google might be taking the lead on artificial intelligence in smartphones with their latest announcement, MobileNets. MobileNets is a series of TensorFlow vision models built for mobile devices, described by Google as "mobile-first."

Verizon customers who use the Samsung Galaxy S7, beware: a recent update installs new bloatware over your existing bloatware that installs new bloatware. Confused or pissed off? You should be, as this app can install new apps onto your phone without you knowing.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Free online dancehall step tutorials every wednesday at 10am for the entire summer! Learn your favorite dancehall steps in the privacy of your own home! This one covers the Nuh Linga steps.

We know that Facebook is a very useful social media sites. This video will help you how to hide friends list on Facebook from others.

You've worked hard to get your garden in shape— the tilling, the planting, the watering, so when pests and weeds threaten your garden, you'll want to take action. But if you don't want to use chemicals, there are effective organic alternatives. Lowe's has the advice you need for keeping those unwanted enemies out.

It doesn't matter if you can do 1,000 classic situps in one go if you're not doing them correctly. Additionally, if you're trying to lose weight or firm up there are ab workouts significantly more effective than sit ups for toning your abs. Doing just a few of these ab exercises gives you the results equivalent of lots of sit ups.

Katy Perry doesn't leave the house without first filling in her eyebrows. Why? Well, other than curling your eyelashes, it's the one big - yet easy - thing you can do to instantly make yourself look more awake and youthful. Additionally, drawing in your brows makes your face look more structured as it adds face-framing and slimming lines.

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

Elementtatootech explains the various tools of the industry and their uses to novice tattoo artists and interested viewers. In this tutorial, Elementtatootech focuses on the old school tattoo tool known as grommets or nipples. Utilizing a single close up shot, the instructor quickly educates viewers on the purpose of the grommet in addition to the most common users of the device. The instructor additionally shows viewers how to set up and assemble using this tool and a simple trick utilizing ...

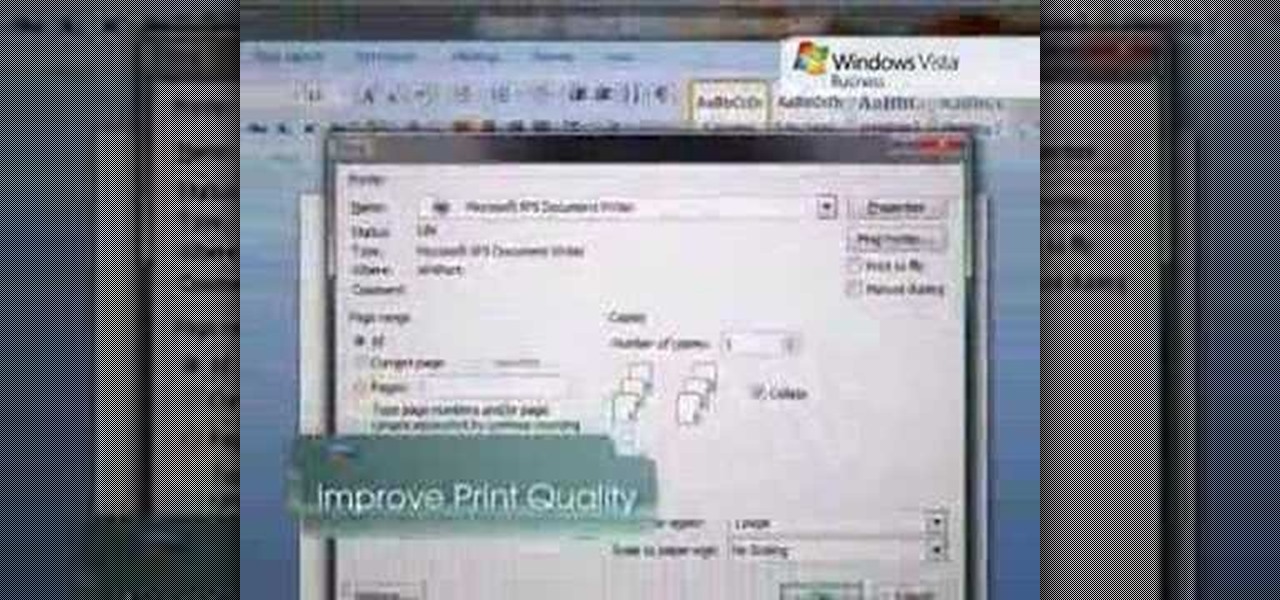
While printers are not normally considered to be at the leading edge of computer technology, these devices have evolved at a lightning pace over the years. Before today's low cost, high-quality inkjet and color laser printers, we used low-quality dot matrix printers and slow laser printers where quality and performance of printing was often questionable. Additionally, documents that looked correct on screen often came out looking differently on paper, due to differences between what the scree...

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

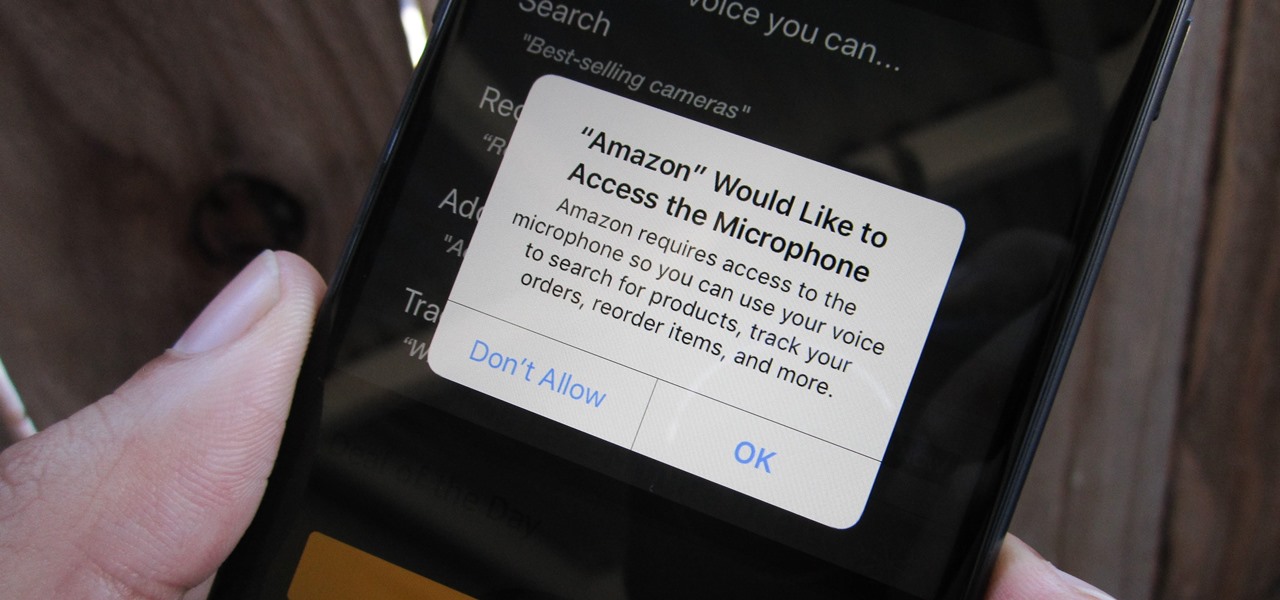
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

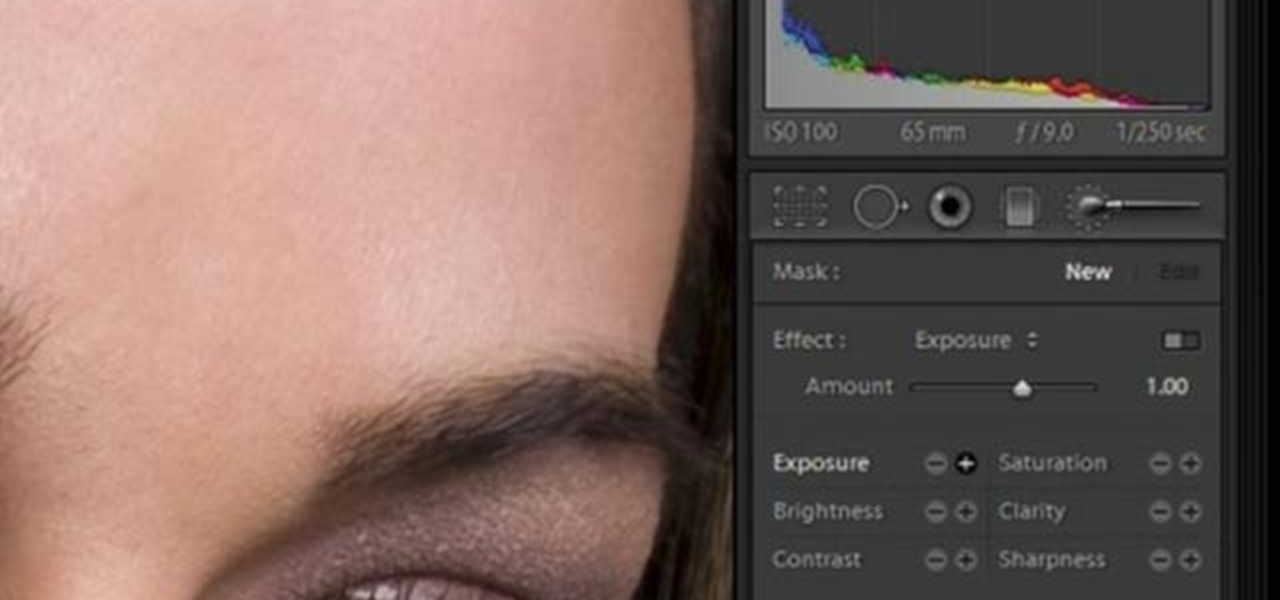
In this software video tutorial you will learn how to soften skin feature in Lightroom 2 in Yanik's Photo School. Select a photo and zoom in to the skin area. Click on the adjustment brush, or ctrl K. Here you can adjust 7 features; exposure, brightness, contrast, saturation, clarity, sharpness and color. But, if you click on the other 'exposure' dropdown menu, you will get these 7 options and additionally a 'soften skin' option. Click on 'soften skin' and it gives you the options to add nega...

The Wicca stones in question may be dried in either sunlight for a full twenty four hours, or the item may be wrapped in a dark black cloth to dry. The stones may also be cleaned in water as well. Another method would be bury the stones in a pot covered with dirt. If unsure if water would damage the stone, however do not submerge the item in water if you are unsure Additionally salt water may be used to cleanse the stone.

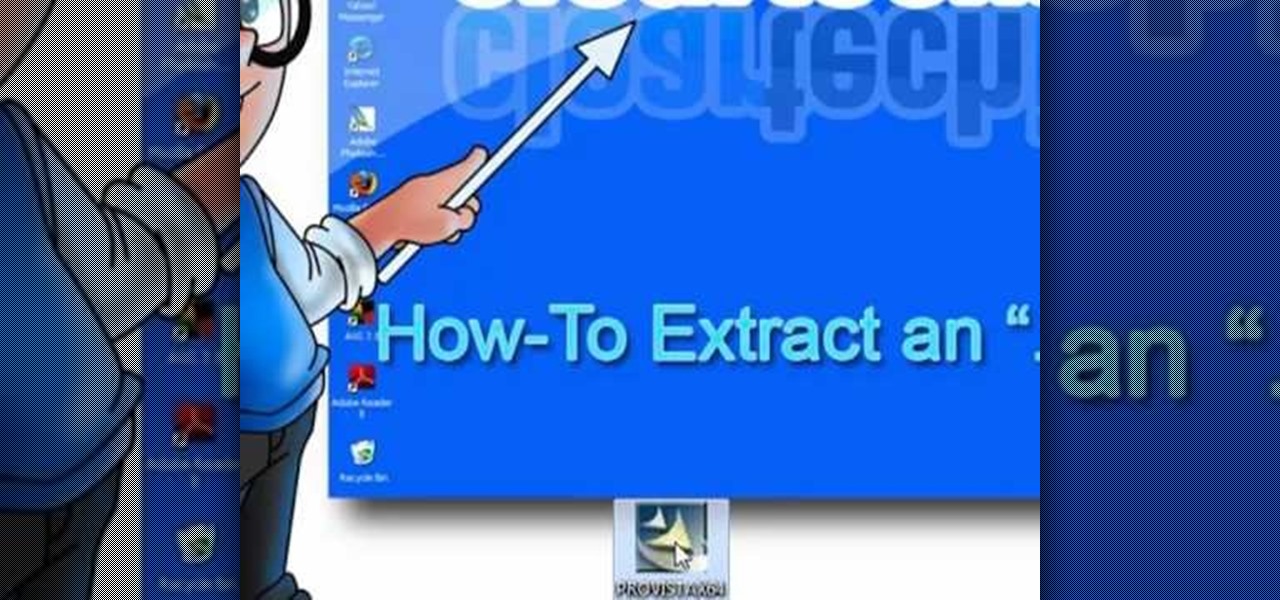
Looking to open an .exe file? In this video, learn specifically how to extract an exe file onto your desktop, but additionally where to find & download the free 7-zip file archiver.

Profisher has a rather unique method of ridding your kitchen of fruit flies. Make sure you start this after you have cleared your countertops of all food. Place any kind of juicy fruit on foil on the open rack of your oven. Leave open overnight. In the morning, close the oven door, set the temperature to 400 degrees and flies will be no more! This can, additionally, be performed in the microwave oven. Set plate of fresh fruit in the open microwave for about an hour. Close the door and set tim...

This video explains how to delete cookies in Windows XP, Mozilla Firefox, Internet Explorer and Opera. To delete cookies in Mozilla Firefox, choose the "tools" option from the tool bar, then choose "options", then choose "privacy". Many options will be given under the "privacy" menu, but make sure to choose the following options- "accept cookies from site" and "accept third party cookies", then choose the option "I close Firefox option" under "keep until" then choose "ok" to delete the cookie...

Starting to work at home? With more and more people trying to make a solid living at home, it's important to know the best way to set up a home office – even if you don't have a spare room. Learn how to set-up a solid work environment with tips from this video on how to create the perfect home office.

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

Thanks to the Freedom of Information and Privacy acts, we’re all entitled to see what the FBI has on us. Learn how to get your hands on your FBI file.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Ahhh! You're locked out of your bedroom, or your bathroom! Well, watch this video and you won't be locked out for long. Fortunately, interior privacy locks are very simple to pick. There are essentially two kinds: one that requires a blade, or knife and the other which requires a long sharp "pin" like object to insert into the handle. Check out this video and never be locked out again! You'll need something like a flat head screw driver for locks with a "slot" in them, and something long and ...

Free up space on your hard drive while protecting your privacy by deleting all of the temporary files on your MS Windows desktop computer or laptop. This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

We all have our reasons for erasing personal data from a phone. Whether you just ended a bad relationship whose face you never want to see again (lots of text messages) or just want to restore your privacy on the cell phone, erasing may be your only option.

If you like your privacy, you probably hate snoopy people, and when it comes to your briefcase, you don't want anyone's paws on it besides your own. To keep their hands off your precious belongings, you need to take some drastic measures…

Waxing should be as painless as possible, which is why girls turn to sugar waxing to remove their hair monthly. But don't shell out wads of cash having someone else rip thick-rooted hair from your hindquarters.