Two years ago, the 50th anniversary of the moon landing gave flight to a handful of Apollo 11 augmented reality apps and experiences, including one from the Smithsonian Channel.

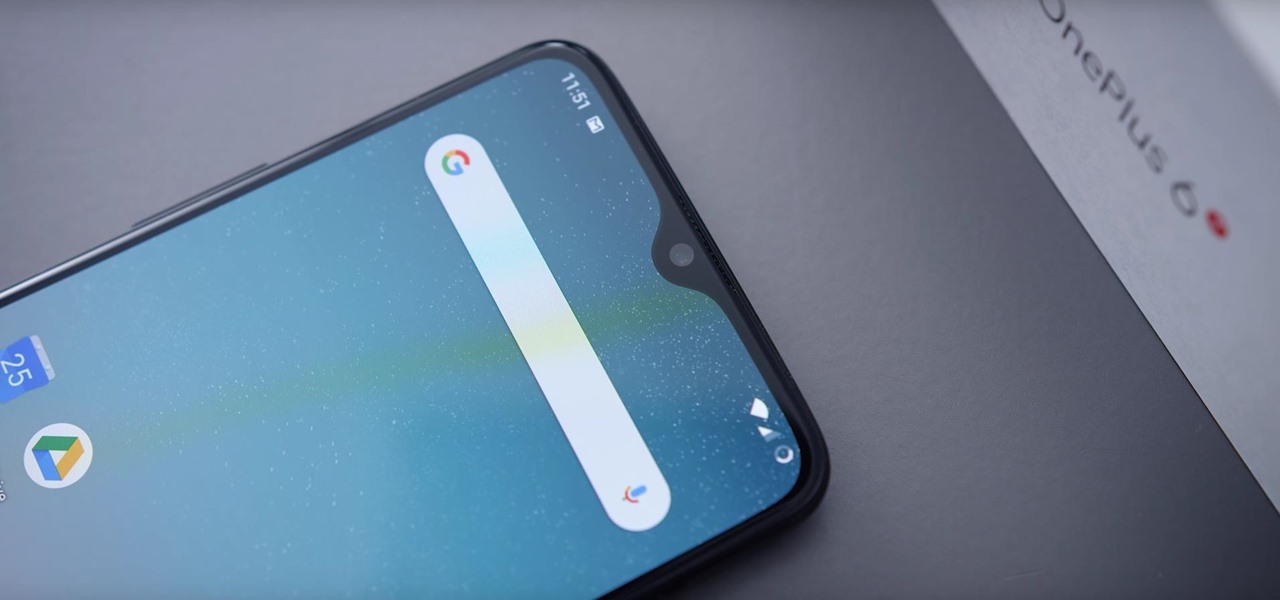
Spotlight, Apple's system-wide search feature, lets you search for apps, contacts, messages, webpages, music, notes, and other content that's on and off your iPhone. On iOS, it's known as "Search," and you can access it by swiping your home screen down or swiping open the Today View screen. It's not exactly convenient, but an accessibility feature can unlock Search so you could open it from anywhere.

What does it mean when a software company obsessively focused on innovating the way we use our mobile devices to see and communicate with the world adds virtual voice agents? Possibly e-commerce magic, with a powerful layer of augmented reality.

In iOS 13 and under, whenever you were in an app or on the home screen, and a Phone or FaceTime call came in, the entire screen would be taken over by the incoming call. Apple changed it to a subtle banner notification in iOS 14 so that it doesn't wholly obfuscate what you're doing when the call happens. However, you can get the old design back if that works better for you.
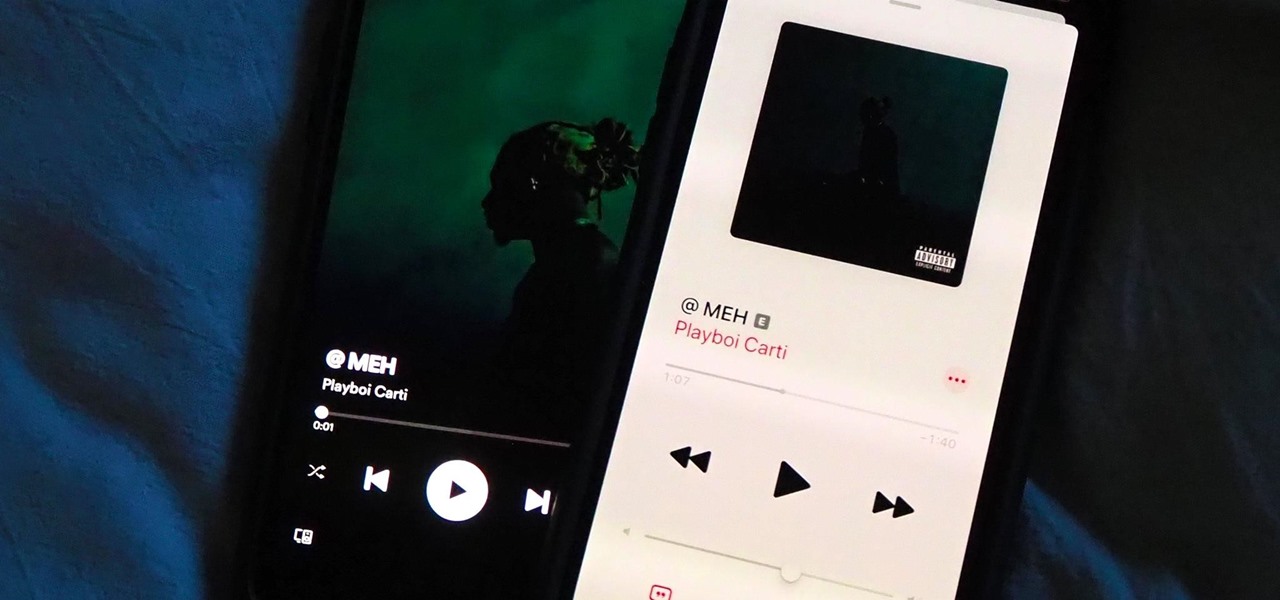
To share a song or album to family and friends, it's as easy as copying its link in the app and pasting that into a message. However, not everyone uses the same music streaming service, so a link to an Apple Music song won't do a Spotify, Tidal, Pandora, Deezer, or YouTube Music subscriber any good. If you're on an iPhone, though, there's an easy way to convert links from one service to another.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

If you made a resolution for 2020 to get healthier, it's essential to concentrate on your mental health just as much as you do on physical fitness. Running and exercising is great, but a sound mind is integral to a healthy and balanced life, and you can improve your emotional and physiological well-being with your smartphone.

Smartphone technology has become as ubiquitous as automobiles. In Austin, Texas, a city that is widely known as the "Live Music Capital of the World," smartphones have been embraced by the music community not just as a way to document and promote, but to create music.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Motorola is a shell of its former self. In 2010, it had just released the Motorola Droid, a phone so popular it led to all Android phones being called "Droids" by non-techies. But there have been some rough years between then and now, and Motorola's latest "flagship" doesn't look like it will help get them off this path.

Typography is an important aspect of the video editing process. You deal with it when adding captions to news clips, giving on-screen recipes in food videos, creating burned-in subtitles for short films, making no-sound-needed videos for social media, and so much more. Enlight Videoleap for iOS makes this all easy.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

In the battle for best stock Android flagships, there are really only two choices: Google Pixel phones and OnePlus phones. Although the latter isn't true stock Android, it is impressively close and usually paired with more impressive hardware than the Pixel lineup. The latest is the OnePlus 6T, which will be a bit controversial for fans this year.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

| Updated Aug. 22, 2019 with new phones. When will my phone get Android Pie? For the first time since Android's inception, this question shouldn't have an answer that lets you down. That's because Android Oreo introduced Project Treble, a new low-level arrangement that makes updating a lot easier. So with Pie, it's not if your phone will get it, but when.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.

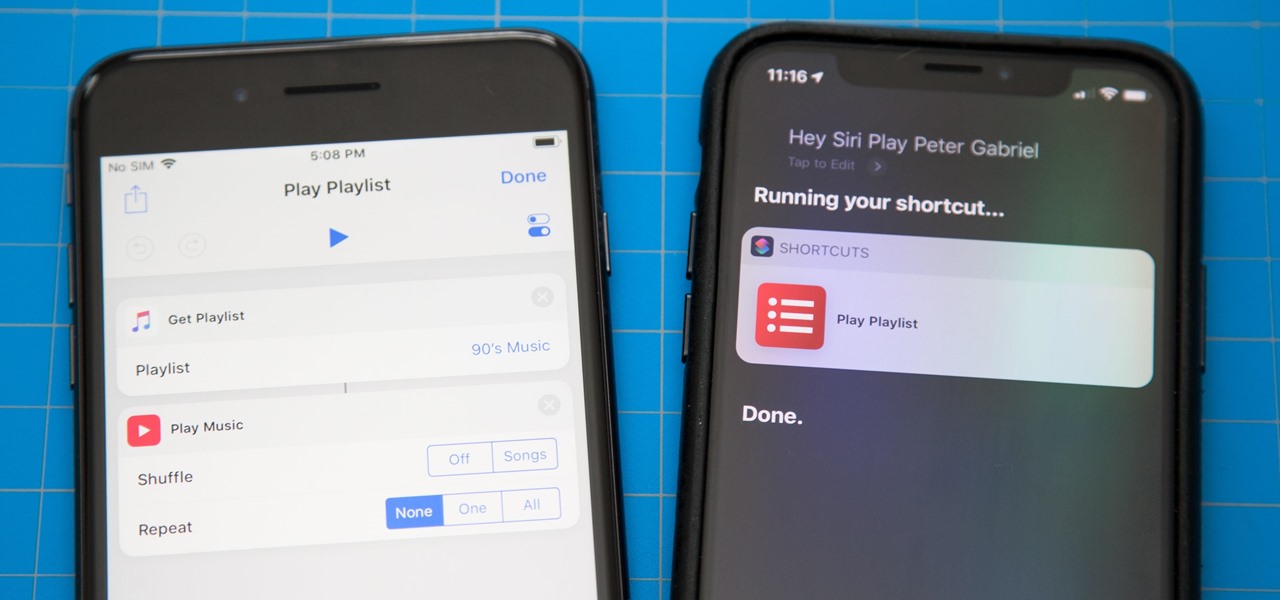
One of the most exciting additions to iOS 12 for iPhones is called Shortcuts, a tool integrated with Siri to help you get things done faster. While there are a few recommended shortcuts available to you in Siri's settings in iOS 12, the Shortcuts app brings the functionality of Workflow to Siri so you can build your own custom actions or select from the gallery of available shortcuts.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Update: Google's new Pixel models have been released! Check out our full guides on the Pixel 3 and Pixel 3 XL to see all the details, but we'll leave the rumor roundup intact below for posterity.

After testing a series of Android 8.0 builds, Essential hit the reset button and jumped to Android 8.1 Oreo. The beta program didn't last long, as Essential has now released the official 8.1 update to the masses. The features from the 8.0 betas are all still there, plus a few goodies specific to the updated version. We'll highlight the standouts here.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

Apple's newest mobile operating system, iOS 8, is out for the general public, and we've got a rundown on the best new features you can use on your iPad, iPhone, and iPod touch. While there's not a huge visual change as there was from iOS 6 to iOS 7, there's still plenty of cool new features in iOS 8 to be excited about.

We see Steampunk props all the time and wonder where the maker found all their pieces. In fact, for some people it's almost like a game to examine each prop and see if they can name all of the original parts.

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

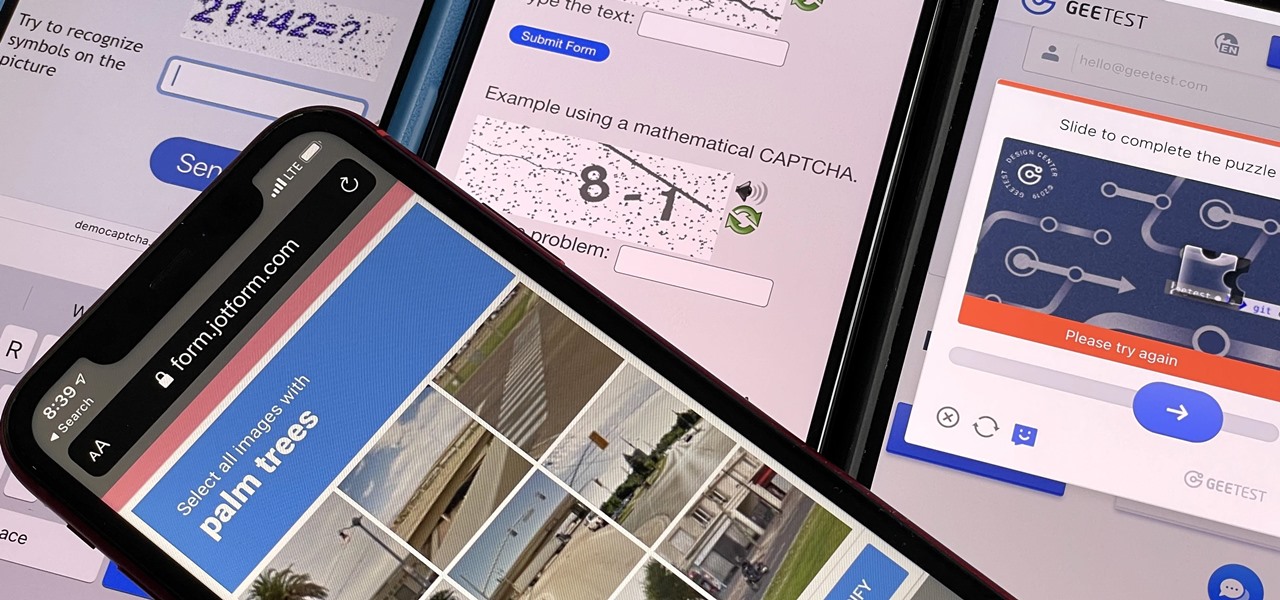
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

If you rely on Apple Maps to get around over other navigation apps, there's a lot you can do. Look Around lets you tour cities up close, restaurant reservations make dining less frustrating, and 3D view gives a new perspective of a neighborhood. While there are many more where that came from, iOS 14.5 just added six new features and changes you need to know about.

If you need to share something online but don't want your personal information attached to the file, use an anonymous file hosting site. By uploading files anonymously, you keep your IP address safe and won't need to create any kind of account that could provide further logging. You can do this in a web browser, but it's much easier to do using a shortcut on your iPhone.

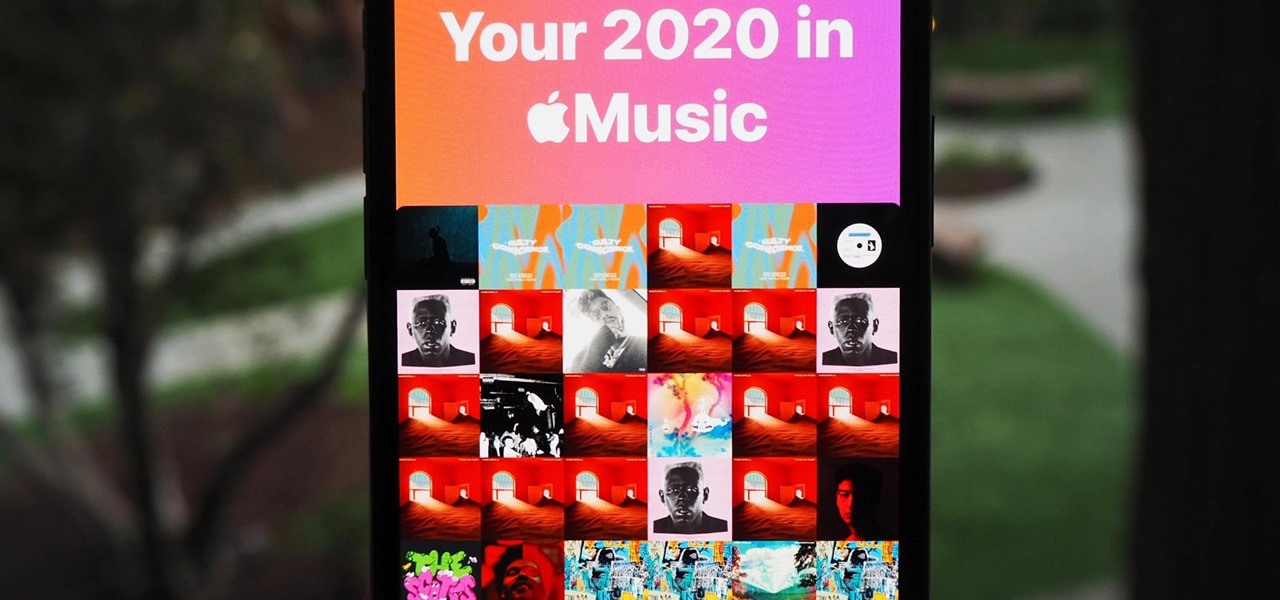
At the end of every year, Spotify analyzes your listening habits for the last 12 months and creates a colorful graphic showcasing your favorite artists, albums, artists, and more. Apple Music does have its own version called Replay, but it's just not very good.

We've wanted them for years, and Apple has finally made widgets accessible on the home screen in iOS 14. These are not the same widgets found in past versions of iOS. They're more data-rich, more colorful, and more versatile. And best of all, both the home screen and Today View get access to them.

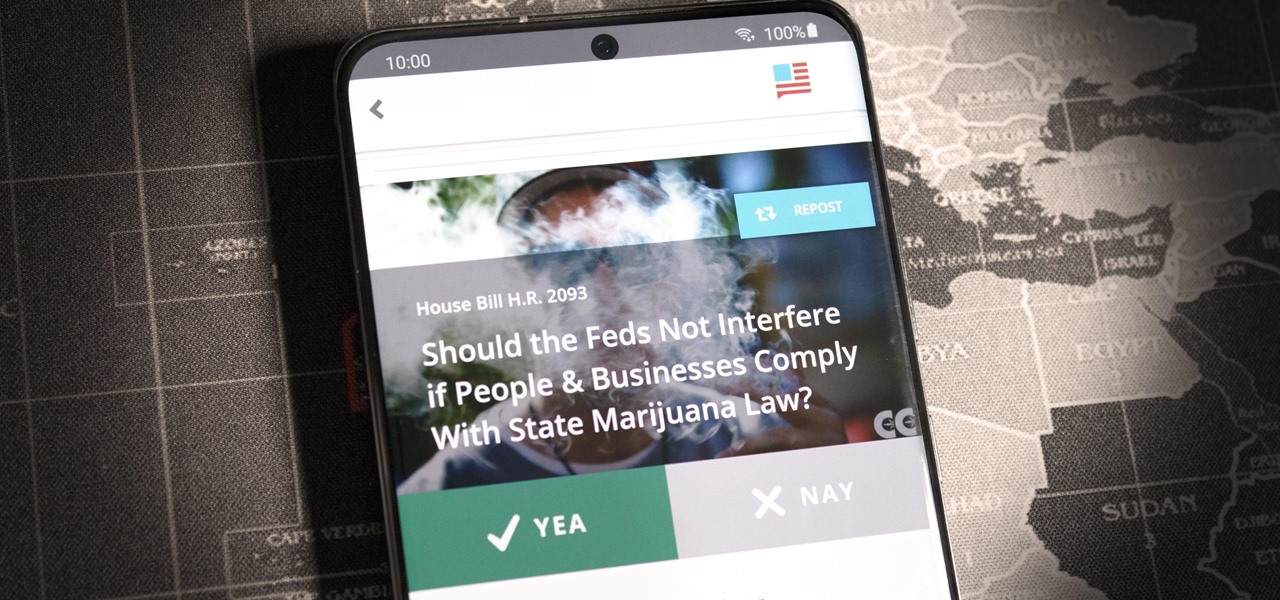
If you live in the US, it's your civic duty to understand our governing bodies and the political system that puts them in place. It doesn't matter what your age is, knowing who to vote for is as important as voting at all. That starts with policing your own representatives to help decide whether or not we should re-elect them.

Samsung's stock Galaxy Themes system leaves much to be desired with its restrictive and expensive theme packs. Back in the day, the gold standard for Android theming was CyanogenMod Theme Engine. And while it no longer exists, a successor has emerged to fill the void.

Home screen widgets might not be a new concept in the Android world, but for iPhones, they're downright revolutionary. A new iOS 14 feature allows you to place small, medium, and large-sized widgets of your favorite apps on the home screen, to see important information without needing to long-press an app's icon, swipe to the Today View, or launch an app directly. Even better — you can stack them!