Whether you like Chris Brown or not, it's safe to say that the boy's got moves. Whether he's doing Michael Jackson's moonwalk onstage or pulling off an a very complex toe spin in a music video, he's very smooth on his feet.

Maybe it's just us, but this city reminds us a lot of the dreamscape Parisian city from Cristopher Nolan's mind heist movie "Inception," aside from the whole city folding back over itself thing and whatnot.

Lady Gaga's famous hair bow may seem extremely complex and difficult to achieve without a football team of hairstylists and assistants ready to fix every stray hair, but, as you'll see in this video, it actually takes less than ten minutes for you to do it yourself.
This step by step video tutorial will show you how to download Pandora Music for free! It's easier than you think. This tutorial focuses on Orbit Downloader, which you'll have to download to get the music. It's a little complex, but once you get it installed, you'll be able to have all the music you want.

If you just got a new Android mobile phone, then chances are, the first thing you're going to want to set up is your email account, so you have instant access to your emails all the time, everywhere and anywhere. Setting up your specific email account or accounts is actually not hard. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up an email account on an Android cell phone.
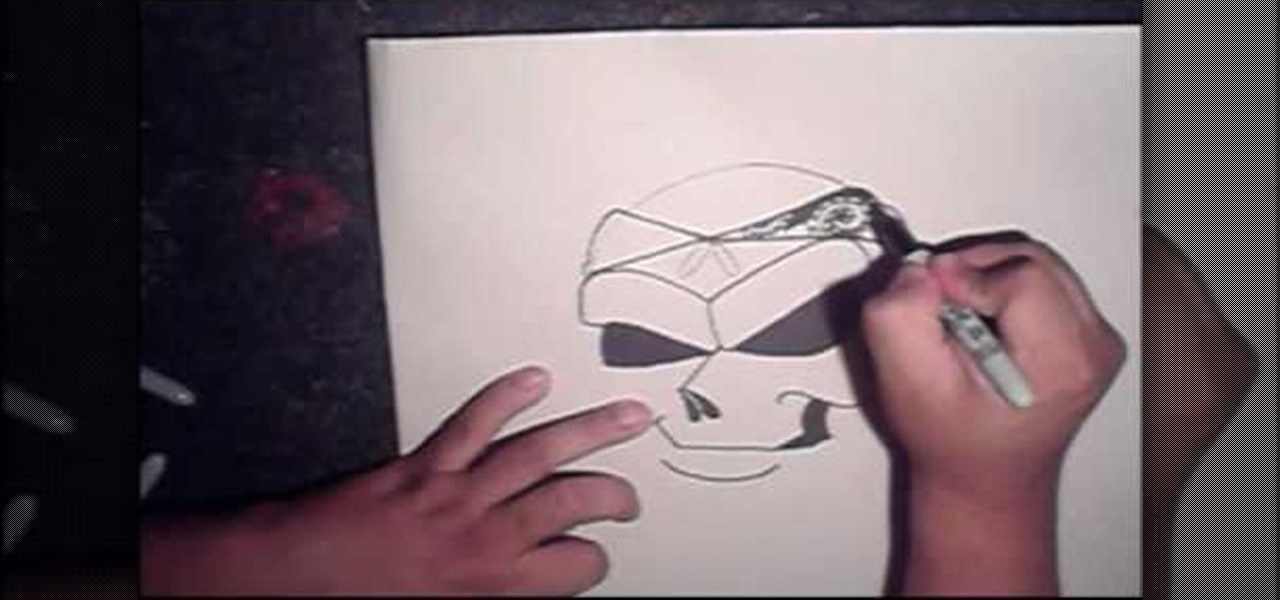
A pretty cool graffiti character is a skull. It is intimidating and complex to draw. Skulls have been popular tattoos and tags for decades and are a perfect symbol for anarchy.

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

For all you Facebook-addicts out there (or anybody else that needs to access blocked websites anywhere they want), this is a video that you will want to watch. In just a minute and thirty seconds, any ordinary person can learn how you can access any website they want anywhere they want, bypassing any blocks and firewalls that the network administrator has put up to stop users from getting to their desired website without using complex computer commands or other complicated methods.

Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.

Own a BlackBerry Curve 8330? Need a custom ringtone? Best Buy has answers. The Best Buy Mobile team explains how to set custom ringtones for contacts in your address book on the BlackBerry Curve 8330. There are many different ringtones to choose from and you may set a different one for each one of your contacts.

Fed up with traditional origami? Well, learn how to fold some three-dimensional origami! This origami video tutorial will teach you how to origami a 3D fox. Traditional Japanese origami is the art of paper folding, but 3D origami is a little more complex, a little more challenging... a little more interesting. See how to model and fold a 3D fox with these origami instructions.

This how-to video shows the basic technique for compounding Double Coin Knots. This video a starting point for learning complex compound knots and the techniques used to create them. Follow along with the step-by-step instructions in this video survival training tutorial and learn how to tie compound double coin knots.

This origami lily fits perfectly atop several models of origami stems. The origami lily is a fairly complex origami endeavor, but these visual guidelines will allow you to complete come of the more difficult folds. Watch this video origami tutorial and learn how to use the Japanese art of paper folding to make a paper lily.

This tutorial demonstrates how to finish your quilt that has irregular edges using a facing instead of binding. Review this quilting instructional video to quilt a complex border finish. The facing method allows you to avoid mitering every corner.

This wavy shell crochet pattern uses three colors to make the design look complex and random. Actually it's quite simple. There are only two rows in this wavy shell crochet pattern. One row alternates between a few standard stitches and half pinwheel shape. The second row is completely plain. Try out this crochet project to achieve satisfying results.

Changing patterns is easy once you get the simple basic stitch idea in your mind. With consistency, you can complete a large blanket without trouble. Watch this instructional crochet video for some advice on how to count out stitches with a complex crochet pattern.

Follow this simple yet clear example to make your own origami flower shaped box. The step by step process will allow you to complete some of the more difficult folds that go into creating this tulip shaped container. Unlike other origami containers, this tulip cup is neither boxy nor overly complex.

Modular origami, as opposed to traditional origami, requires the use of multiple sheets of paper for more complex projects. Learn how to use the Japanese art of modular origami to fold this stellated dodecahedron. Start watching and start folding origami!

Romeo's and Rubinstein's Revenge juggling patterns are suggested pre-requisites for learning how to do the Sandbox Shuffle, but with a little bit of practice, anyone can learn how to do this complex pattern. Watch this video juggling tutorial and learn how to execute the Sandbox Shuffle juggling pattern.

This how to video covers a rather complex blues technique which involves moving around the piano or keyboard smoothly and swiftly. This lesson is designed for the advanced pianist.

To control more complex or improbable shape changes in Macromedia Flash, you can use shape hints. Shape hints identify points that should correspond in starting and ending shapes. This video tutorial teaches you how to use shape hints to make a cool 3D effect.

The more you use Keynote and the more complex your presentations become, you are going to need to become more organized. This tutorial shows you how to organize your slides in Keynote and keep your work flow smooth.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

This is such a pretty card and so quick to make, it is really ornate with the layers of the frame making the corners look even more complex. It is a really easy card to make and the pink n' black combination just make it all even better.. Step 1: Now Watch the Tutorial

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

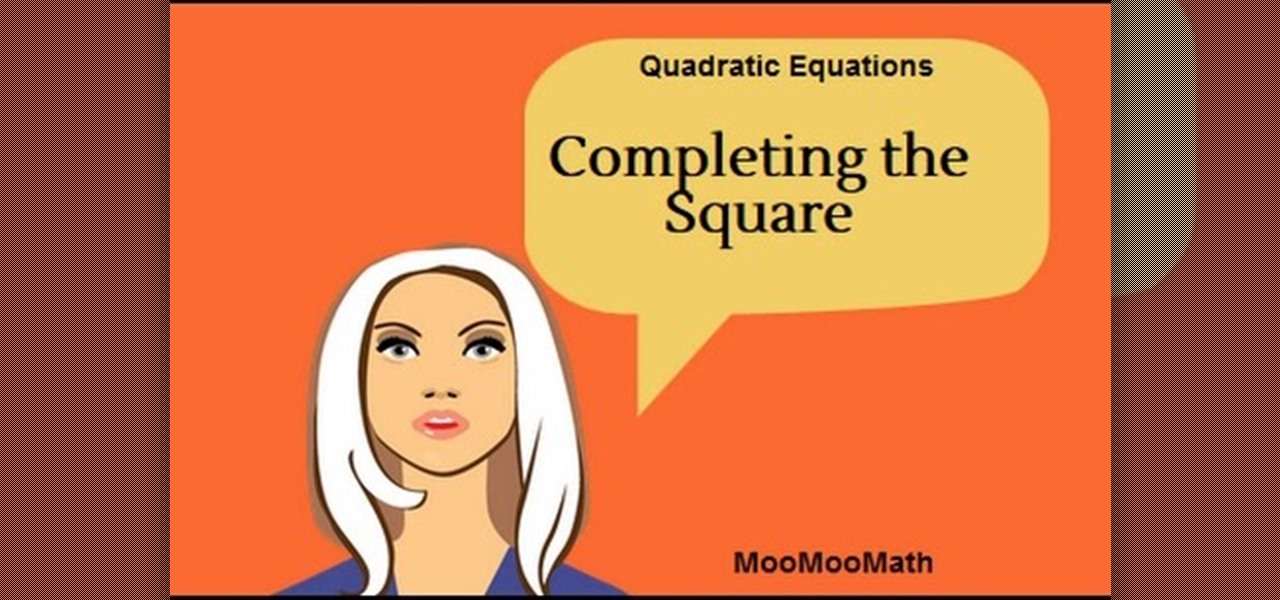
How to use "we half it,we square,we add it to both sides" when using the complete the square" This method can help make a complex Math problem a little bit easier.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

I've often marvelled at the complex worlds people come up with on Minecraft. I particularly enjoy looking at maps with skyscrapers and modern structures in modern cities. If you're one of those people too, check out this sneak peek for a tour of a world-class city containing replicas of buildings including the Trump Tower, BMO and one of my favourites: The Bellagio Hotel! The world has been made on the XBOX 360 by a very creative user with the gamertag: TH3 3ND 0F TiM3.

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

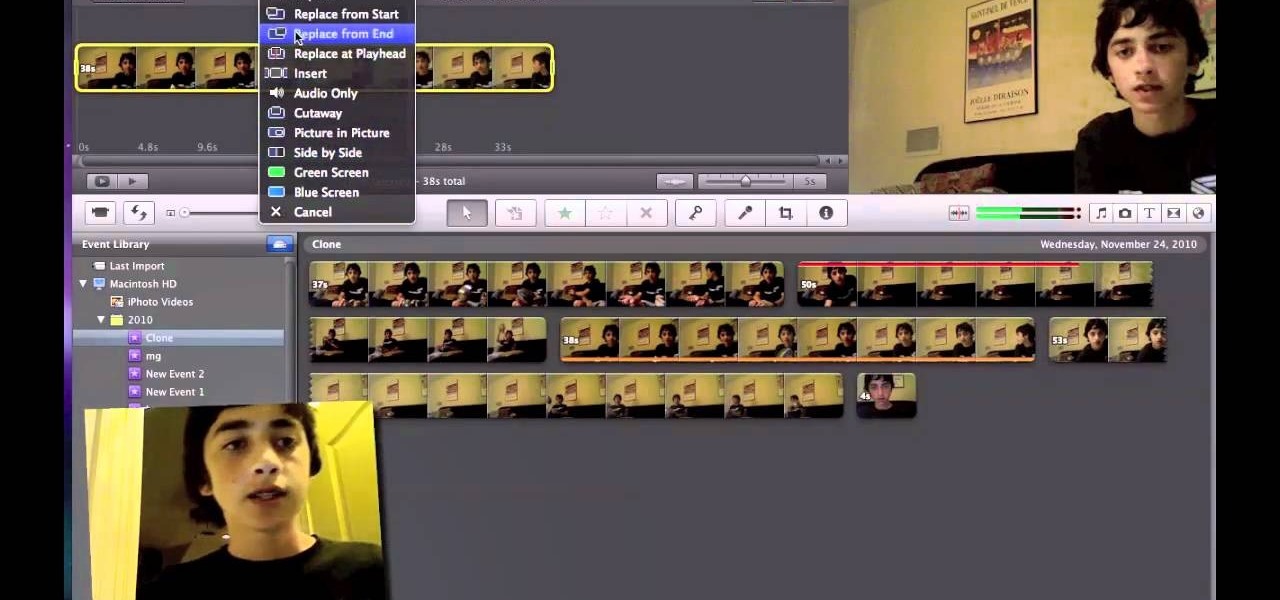
Are you an iMovie user looking to double down on yourself? Well, if so, watch this video and see how to clone yourself, quickly and easily. I mean, who wouldn't want to make two of themselves? It could be so helpful for so many situations! Though cloning may be far in the future, we can still clone ourselves in Videos. Apple's new iMovies, have changed from being small easy video processors to a more complex higher quality Video editing software. This video will use the Green Screen Function ...

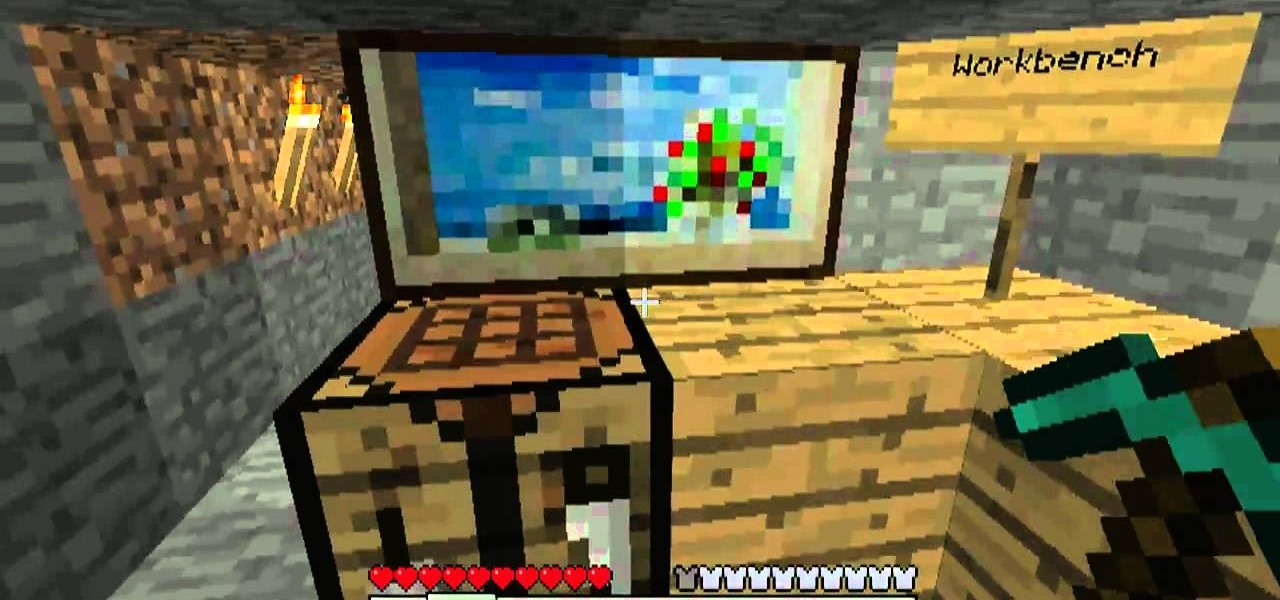
A big part of the fun in Minecraft is figuring out all of the different things that you can craft and how to craft them. Sometimes you just want to make the damn thing though, and to that end this video will show you how to make many of the game's better and more complex to craft blocks. You'll learn how to craft the following blocks: